Abstract
Today, advancements in science and technology have spurred the rapid evolution of systems like electronic banking, demanding precise, swift, and secure identification of individuals based on their distinct traits. Among these traits, fingerprints stand out as a dependable means of identification, finding application in realms such as crime investigation and national border control due to their simplicity and heightened security. The qualities inherent in fingerprint-based identification have led to its widespread adoption over other identification methods. This article proposes a hybrid biometric system that integrates the Gabor filter and scale-invariant feature transform features and then uses support vector machine and K-nearest neighbors as classifiers, aiming to notably enhance authentication systems by mitigating issues seen in single-method biometric systems. Also, principal component analysis is used to reduce dimensions and eliminate redundancy. In this article, the famous database FVC2004 is used. Test results highlight the considerable reliability and accuracy of the proposed combined approach compared to systems reliant on a singular biometric method.
1 Introduction
Maintaining the security of confidential information and personal information as well as the ability to securely access them is of particular importance, so defining appropriate solutions for this purpose is very necessary and essential. One of these reliable solutions is the use of physiological features and characteristics, which are called biometrics and have a higher level of reliability and security [1]. In biometric systems, the vital and behavioral characteristics of people are used to recognize their identity. Several vital and behavioral features have been presented for use in biometric-based identification systems. Among the biometrics, fingerprint has been more accepted, for this reason, working on fingerprint images and their proper and optimal processing has been the priority of the activities of specialists in this matter [2,3]. Biometric systems based on fingerprints have important features such as high security, cheapness of fingerprint-taking tools, small size, and ease of working with them. Every person’s fingerprint does not change under the influence of mental and emotional events. These characteristics have caused fingerprint-based identification systems to be used more than other identification systems [4]. The use of fingerprints for identification is based on the prominent lines of the first joint of the fingers. Fingertip lines include ridges and depressions, each of these ridges is called a vein, and the empty space between two veins is called a groove. The veins and grooves have a regular structure and a special shape that makes them unique [5]. The quality, transformation, angle, and position of an input fingerprint image are important factors that affect the recognition efficiency in the automatic fingerprint identification system. In general, biometric systems perform identity recognition in two ways: verification or identification. In this thesis, the identification of fingerprints with high accuracy for different fingerprint changes (movement, rotation, extreme changes, pinch, punch) is discussed [6]. In this way, fingerprint identification is done by extracting fingerprint features from fingerprints and comparing these features with the information already collected in the system. In this research, fingerprint identification by extracting features from the fingerprint areas, in this stage the features the Gabor filter, is used hand in hand with scale-invariant feature transform (SIFT) which is used too. Then the features are combined together and selected of suitable features from them. Also, we used principal component analysis (PCA) to minimize dimensions and eliminate redundancy. In second step the support vector machine (SVM) and KNN classification are used, then merge them together and selection of suitable result from them. In this article, the famous database FVC2004 is used. Figure 1 shows the different stages of the work are fully explained.

Block diagram human identification using fingerprint images system.
2 Literature review
Several studies have been performed on fingerprints in comparison to all other biological characteristics of humans. Compared to other biometric characteristics of humans, fingerprint has advantages that make it unique. The investigation of this issue has been done because nowadays fingerprint recognition has become a necessity. One of the largest identification systems based on fingerprints is the integrated automated fingerprint identification system (IAFIS), which has been used by the police force in the United States since 1999. The IAFIS system currently stores the fingerprint information of more than 60 million people along with the statistical information related to the traces left in the crime scenes and identification with 10 fingerprints to identify the accused in the cases and statistical control in the background.
In 2008, the United States Federal Police began upgrading IAFIS to New Generation Identification systems. In addition to fingerprints, these systems can support other features like palm print, iris, and face [7].
Shen et al. used the Gabor filter for the images of hands and FKP. Hamming distance was utilized to match characteristics where the obtained accuracy was 89.20% [8].
The method of feature extraction based on the texture characteristics of knuckle wrinkling images has been investigated and evaluated in terms of efficiency and accuracy [9].
Yin et al. suggested a feature extraction method under the name of weighted linear embedding. This method simultaneously uses local and non-local information in the form of Gaussian weighting [10].
Zhang et al. presented a new method for extracting different features from ROI images using Gabor filters. In this method, the direction domain information of each pixel is used using Gabor filters [11].
Kang et al. [12], on the other hand, presented a new multi-quality biometric system based on non-tangential spectrum of fingerprints, which is claimed to extract three features of fingerprints, knuckles, of finger plates instead of extracting only one feature based on the limitations of single biometrics. The database tested in this method was taken by the authors.
Peralta et al. [13] proposed a minutiae extraction method that improves the efficiency of the fingerprint matching algorithm. In this method, the test results have been compared on the FVC database and a database taken by the authors, which are claimed to have high diagnostic accuracy.
In a series of methods, the adaptation of a part of fingerprints was used as a new idea in identifying people’s personality. For example, Lee et al. describe a partial matching method of fingerprinting using minutia features [14].
Khusnuliawati et al. [15] compared SIFT with LEBP for feature extraction using LVQ classifier for the matching process.
Hu et al. [16] used a multi-scale uniform local binary pattern block to extract local texture features, followed by a block-based (2D)2PCA method to preserve local information of finger tissue images.
In 2017 [17], a Gabor filter was used to extract the texture of the finger vein because the Gabor filters can be designed to capture the local orientation and frequency information of the finger vein image Gabor filters with specific directions were used, with image enhanced to exclude undesirable communities changed them. Subsequently, a post-processing function of morphological top-hat operation was applied to the extracted tissues to further improve the tissue shapes.
In 2018 [18], a new finger muscle dataset was utilized that included videos of muscle structures around the finger. In addition, the performance of different feature extraction algorithms such as maximum curvature, principal curvature, and Gabor filters was compared.
In 2020, Kovač and Marák [19] proposed a passive object recognition system that faithfully combines fingerprints and finger tissue images. For finger tissues, the first of five different steps is performed to perform feature extraction using SIFT and SURF algorithms, while the second is used to detect scale- and rotation-invariant points.
3 General principles in fingerprint recognition systems
Determining the identity of people using fingerprints is widely used compared to other biometric methods of identification. The ridges and depressions in the skin of the fingertip are called fingerprints. The primary factor driving the widespread and common utilization of fingerprints for identification is their inherent uniqueness and permanence throughout an individual’s life [20].
The fingerprint, among the oldest and most recognized biometric identification methods for individuals, has significantly evolved in recent years. Current methods have replaced traditional stamps and paper with specialized scanners capable of swiftly verifying and comparing fingerprints against recorded samples. The fingerprint, among the oldest and most recognized biometric identification methods for individuals, has significantly evolved in recent years. Current methods have replaced traditional stamps and paper with specialized scanners capable of swiftly verifying and comparing fingerprints against recorded samples. This method is considered one of the most common methods of identity recognition. So that he is used as one of the safe and fast methods even in employee attendance systems. Fingerprint identification methods ensure consistent and dependable recognition of identity, leading to their utilization across diverse applications. However, fingerprint identification systems encounter several practical challenges. The elasticity of the skin can cause distortions in the shape and positioning of fingerprints each time they are captured. Besides high reliability and immediate processing, automatic fingerprint identification systems necessitate essential factors for effective operation [21].
To tackle these issues, the essence of forks from fingerprint images should be extracted and matching with the different fingerprints should be investigated. There are standard methods for manual matching of fingerprints, but the manual method of matching fingerprints is difficult and time-consuming and does not have the necessary performance. Of course, since databases have millions of fingerprints, it is practically impossible to match fingerprints manually. To automate the matching, a method for image or coding of fingerprints must be defined. This image expression must have the following conditions: The ability to distinguish each fingerprint at different levels of resolution, simple calculations, the ability to be used in automatic matching algorithms, stability and not changing with noise and damage, being efficient, and showing images in a compressed format. If the image is saved raw, a lot of memory is required and the system will not have the necessary performance.
In structural methods, the features’ fingerprints should be firstly extracted from the image and those images are labeled with the matching features, and the matching process is done using these features. So far, 18 features have been identified for fingerprints, the two most important features of which are the end of the ridge and bifurcation of the ridge, which are called Minutiae. The y, x plane and the angles of their protrusions represent the minutia information. Minutiae topological structure is a distinct fingerprint that remains constant with time. Therefore, minutia’s topological structure can be matched to facilitate fingerprint detection. A reasonably high-quality fingerprint has approximately 70–80 minotas; in detailed images, this number naturally drops to 20–30 characteristics; however, fingerprint matching can still be accomplished with this amount.
The majority of fingerprint recognition systems are structured using the minutiae-based system. These two features are shown in Figure 2. Fingerprint recognition can be based on matching the topological structure of minutiae. Most fingerprint recognition systems have a minutiae-based structure. In these systems, there are three basic stages for diagnosis, which are: pre-processing, extraction of minutiae, and adaptation of minutiae [22].

Some common minutiae patterns in fingerprints.
The first step is to focus on leveling the image quality. The second step, extracting image and the last stage is used for comparison. Regarding the adaptation, there are various methods, among which the following can be mentioned: matching the set of points, graph matching, and isomorphism of two sub-graphs.
Of course, the matching process requires complex calculations for the following reasons: Usually, the fingerprint quality is low. The database of fingerprints is large, and structurally damaged images require powerful matching algorithms.
In the fingerprint recognition systems available in the market, which use these two features (the end of the protrusion and bifurcation of the protrusion), due to the large database and the noise of the images, one-to-one matching is practically difficult, and therefore, a series of matching images are lost. The preparation and then the final adaptation are done by experts.
4 The proposed method of human identification using fingerprint images
In identification systems, the input images are compared with the other images stored in the database. Various reasons, such as noise or the absence of all unique points in the image range, make it difficult to determine an absolute class for all images. One of the complex steps is to improve the image quality and extract details to calculate the direction of the ridge lines of the fingerprint. The existing algorithms are usually known for complex and time-consuming calculations and are performed by software. While the image processing in fingerprint is one of the physical characteristics of this technology. In this research, we found out the effective features, we found out the method of obtaining the optimal matching score which helps to improve low-quality images.
The biometric system is a pattern recognition system that learns fingerprint images utilizing the extracted features from an image. The feature extraction feature is turned into vector arrays and stored in the database.
In this article, the initial focus is on outlining the biometric system. Among various identification methods, those utilizing physiological or behavioral traits offer heightened reliability and security. Fingerprint identification, a prime example, stands out as the most prevalent and reliable method due to its simplicity and exceptional accuracy. People heavily rely on biometric technology, and the proposed approach involves identifying individuals through fingerprint images. Considering the frequent occurrence of incomplete fingerprint images, there’s a necessity to gather more information. The significance of extracting a composite feature lies in determining whether a segment of the fingerprint image is unique to the individual or not. These features are derived by utilizing minutia points and employing skeletal image data. In this method, the Gabor filter and SIFT and their combination were used to reduce noise, and by image processing, data features with more accuracy were extracted. Also, PCA is used to reduce dimensions and eliminate redundancy. Then SVM and K-nearest neighbours (K_NN) classifications are used, matching their results and choosing the best result between them. To check the effectiveness of the proposed method as well as to check the accuracy of fingerprint recognition, the FVC2004 database, each of which contains 91 fingerprints (8 samples of fingerprints from 11 different people), has been used. To evaluate the proposed method, 15 tests were conducted, each time a sample of a fingerprint image was taken. In each stage of implementation, 24 fingerprint samples were examined from the database according to the test steps.
The general scheme of the proposed method is shown in Figure 3.

The proposed method.
4.1 Extraction and selection features
The proposed features in this thesis are Gabor filter and SIFT algorithm.
4.1.1 Gabor filter
The grooves and veins in the fingerprint images follow a specific extension locally and are placed next to each other at a certain frequency. This information is reflected in the direction and frequency of images. To use this data it requires image processing tools rather than machine vision in order to use the fingerprint images properly.
The analysis of the texture of the images will be explained and the analysis of the lines of veins and grooves will be discussed as well.
Gabor function is known as a useful tool in image processing and machine vision, especially in the field of methods based on texture analysis [23]. In 1946, Gabor presented the one-dimensional Gabor function, and then these functions were used in many applications, and the set of two-dimensional filters was first presented by Dogman in 1980. A Gabor filter based on the two-dimensional image domain is defined according to the following formula:
which in the formula No. (1) x
0 and y
0 express the desired location in the image and (v
0,u
0) also the modulus that has the frequency
In these relations, the extension of the Gabor filter and T also shows the alternating function of the C-shaped sine plane. As it is seen, the middle frequency of the filter is found by the sine wave whereas, the filter bandwidth is determined by the Gaussian function. Gabor filters can present an optimal array of signals in two time and frequency domains simultaneously. The fingerprints with the help of Gabor filter banks is based on the assumption that the grooves and streaks of a they create a sine wave pattern. If the angle chosen for the filter is equal to or close to the direction of most of the streaks in the desired area, they will be strengthened, otherwise, they will weaken or make the streaks lighter. In this case, the streaks in the fingerprint image can be strengthened or weakened by appropriate settings of Gabor filter parameters, which is shown in the following formula:
In this relation, O(x,y) and f(x,y) show the frequency and extension of the fingerprint lines at their desired point, respectively. To adapt the filter in a stretch to the structure of the lines in the image, the bandwidth of the filter should be adjusted.
4.1.2 SIFT
The SIFT algorithm was invented by David Lowe in 1999 [25]. SIFT is a method for detecting and extracting key feature points from images that can be used for applications such as matching between images, object identification, 3D reconstruction of scenes, etc. SIFT features are extracted from all images within the database. Subsequently, when presented with a new image, its extracted features are compared against those of all images in the database. The face within the database exhibiting the highest correlation points is identified as the closest match and utilized to isolate the new face. A feature is deemed a match to another feature if its distance falls below a specific fraction compared to the distance of the subsequent closest feature. This challenge arises from the possibility of numerous closely situated features in the event of incorrect matching, stemming from the extensive dimensions of the features. Conversely, in cases of accurate matching, it’s improbable to encounter a feature closely situated to others due to its distinctiveness [26]. Figure 4 shows the general block diagram of the SIFT algorithm.

SIFT algorithm.
4.1.3 PCA
Due to the high dimensions of the feature space, PCA has been used to reduce the dimensions. This work improves classification accuracy [27,28]. In this method, new coordinate axes are defined for the data in such a way that the first axis is placed in the direction where the variance of the data is maximum. The second axis is also perpendicular to the first axis and in the direction of maximum variance. In the same way, other axes are also defined. First, a data matrix X is created by the detail coefficients and another matrix by the approximation coefficients of the fourth level, each with dimensions of 200 × N. N is the number of beats of all arrhythmias [29]. Then, the average of each column is calculated and subtracted from the signal. Suppose Y is the covariance matrix of X, and A is the matrix of eigenvectors and B is the matrix of eigenvalues calculated from the covariance matrix of Y, and we denote each member of A by ϕ and each member of B by λ, then the matrix of principal components P includes the eigenvectors corresponding to m The specific value is larger.
Finally, by multiplying the matrix of the main components in the matrix of coefficients whose average is reduced, the feature matrix C is obtained. The first components are selected as features from both depicted matrices. Therefore, 24 components together for each Image form the input feature vector of the classification system.
Figure 5 is shown for two-dimensional data for PCA.

Data distribution in PCA algorithm.
4.2 Classifications
The proposed classifications are SVM and K_NN training classifications.
4.2.1 SVM
This classifier searches for an optimal hyperplane to separate two sets; so that the distance of the closest data becomes the largest possible value. SVM is a supervised classification system; that is, it should be trained by labeled data first [30]. If the data is scattered in such a way that linear separation is not possible, SVM writes the data to a higher dimensional space where linear separation by a hyperplane is possible. Due to the problems of working in high dimensions, a kernel function is used, so there is no need to map data to high dimensions. One of the most common kernels is the radial basis function kernel. SVM is also extended for multi-class separation. The most common multi-class SVM methods are one vs all and one vs one. In these methods, first, several binary classifications are created, and then, their results are combined. For this purpose, using fingerprint images in the database, a training dataset and a test dataset have been prepared. First, with the help of training data, the classifier was trained and then the performance was evaluated by experimental data [31]. Due to the fact that in fingerprints, the patterns of veins and grooves are different, their image matrix is also different from each other. Therefore, according to the image matrix of a fingerprint, it can be distinguished from similar fingerprints. In this method, to avoid comparing two contradictory samples, which is pointless, fingerprints are arbitrarily classified based on existing methods, and SVM is used to detect each class [32]. To better understand the issue, Figure 6 shows data sets divided into two groups, where the best hypersurface is chosen to separate them using the SVM method.

SVM classification.
4.2.2 K_NN
One of the most widely used and simple classifiers is the nearest neighbor classifier or K_NN [33,34]. This classifier is independent of probability density estimation and can classify new data separately. In this method, deciding which category a new sample should be placed in is done by examining a number (k) of the most similar samples or neighbors. Among this sample, the number of samples for each class is counted, and the new sample is assigned to the class to which more neighbors belong, most of the neighbors are placed in class X and are attributed [35]. To better understand the topic, the distribution of K_NN is depicted in Figure 7.
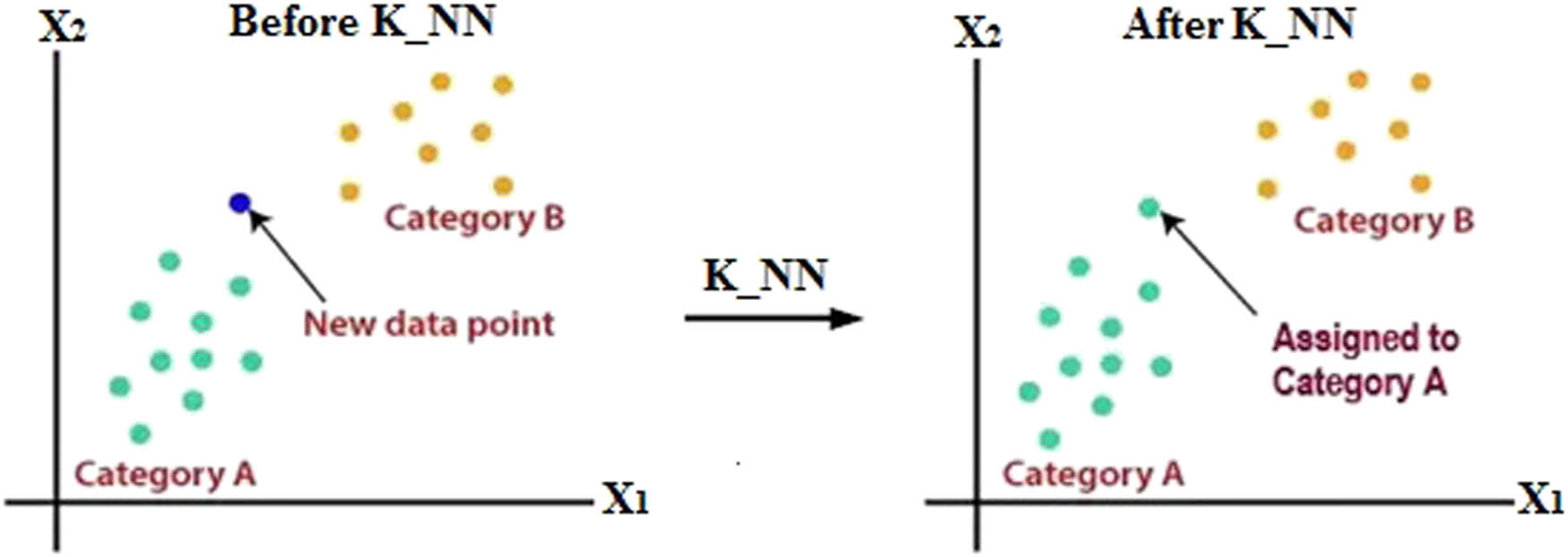
K_NN classification.
5 Evaluation of results
In this article, we have gained the characteristics of the features by Gabor filter and SIFT algorithm. For the simulation, the FVC2004 dataset was used. To assess the proposed system and after extracting properties Gabor filter and SIFT were combined, along with the PCA algorithm which was used to reduce unimportant features, then SVM and K_NN classifications were used, matching their results and choosing the best result between them.
It was noticed that the best results of the SVM classification were gained by combining the Gabor filter and SIFT, with a precision of 99.6% and the execution time of 6.4 s, as shown in Figure 8.

The results with classification (SVM) without using the PCA algorithm.
Moreover, when the PCA algorithm was used, to suppress unimportant features, which led to improving the results and increasing accuracy and speed in implementation, the SVM classification showed the best performance. It was given by compounding the Gabor filter and SIFT with PCA with a precision of 100% and the execution time of 3.4 s, as shown in Figure 9; the other results are shown in Figures 9 and 10.

The results with classification (SVM) with using the PCA algorithm.

The results with classification (K_NN) without using the PCA algorithm.
Also, the best results for the K_NN classification were obtained by fusing the Gabor filter and SIFT, with a precision of 99.3% and a runtime execution time of 6.3 s, as shown in Figure 10; the other results are shown in the same figure.
On the other hand, the best results of the K_NN classification were obtained by mixing the Gabor filter and SIFT with PCA with a precision of 100% while the execution time was 3.8 s, as shown in Figure 11; the remaining results are shown in Figures 10 and 11. Tables 1 and 2 show the results of the algorithm in detail.

The results with classification (K_NN) with using the PCA algorithm.
The results with classification (SVM)
| PCA | Without using the PCA | With using the PCA | ||||
|---|---|---|---|---|---|---|
| Features | Gabor | SIFT | Gabor + SIFT | Gabor | SIFT | Gabor + SIFT |
| Accu. %. | 98.9 | 99.2 | 99.6 | 99.7 | 99.6 | 100 |
| Time sec. | 5.1 | 5.4 | 6.4 | 3.6 | 2.7 | 3.4 |
The results with classification (K_NN)
| PCA | Without using the PCA | With using the PCA | ||||
|---|---|---|---|---|---|---|
| Features | Gabor | SIFT | Gabor + SIFT | Gabor | SIFT | Gabor + SIFT |
| Accu. %. | 98.8 | 98.3 | 99.3 | 99.4 | 99.7 | 100 |
| Time sec. | 5.4 | 5.7 | 6.3 | 3.8 | 3.2 | 3.8 |
6 Conclusion
Today’s biometric systems prioritize safeguarding users’ data security and privacy. There is a significant focus on securing biometric patterns to prevent theft during transmission. Biometric technology stands as a pivotal force steering the world toward a safer and more favorable state. This technology amplifies security measures, enhances speed and convenience, cuts down costs, fosters confidence in electronic commerce, builds trust, and brings about numerous other benefits. Recent years have witnessed heightened growth and advancement in biometric technologies due to escalating security concerns, resulting in accelerated progress across all facets of biometric research. This growth is not only related to the increase in security considerations, but it is also affected by considerations related to the privacy of users, in the field of confidential and safe use of personal information of people that are stored in virtual cases or transmitted through the Internet. In this article, the biometric system is described first. Among identification systems, systems that use physiological or behavioral characteristics of people have more reliability and security level, an example of which is fingerprint identification, which is the most common and widely used method of identification due to its simplicity and high accuracy. The proposed approach is to identify people using fingerprint images where take into consideration that in many cases there is an incomplete image of fingerprints, there is a need to extract more knowledge. In our proposed method, the Gabor filter and SIFT algorithm were combined and used to reduce the noise as an image processing tool; data features with more accuracy were extracted. Also, PCA was used to reduce dimensions and eliminate redundancy. Then SVM and K_NN classifiers were used comparing their results and choosing the best result between them based on the performance in terms of executing time the accuracy. As it can be seen based on the results shown in the figures above, the successful performance of the proposed algorithm, plus the use of the PCA algorithm, had a clear impact on the results in terms of improving accuracy and the execution of run time. Also, it was noticeable that the SVM classification proved its efficiency over the K_NN classification.
-
Funding information: Authors state no funding involved.
-
Author contributions: All authors have accepted responsibility for the entire content of this manuscript and consented to its submission to the journal, reviewed all the results and approved the final version of the manuscript. MJAD and HJSA conceived the study and were in charge of overall direction and planning. MJAD designed and performed the experiments, derived the models, and analyzed the data. MJAD wrote the manuscript in consultation with HJSA and MAAD. HJSA devised the project, the main conceptual ideas, and proof outline. MAAD worked out almost all of the technical details and performed the numerical calculations for the suggested experiment, verifed the numerical results of the HJSA by an independent implementation. MAAD performed the analysis.
-
Conflict of interest: Authors state no conflict of interest.
-
Data availability statement: The most datasets generated and/or analysed in this study are comprised in this submitted manuscript. The other datasets are available on reasonable request from the corresponding author with the attached information.
References
[1] Palma D, Pier Luca M. Biometric-based human recognition systems: an overview. Recent Adv Biomet. 2022;27:1–21.10.5772/intechopen.101686Suche in Google Scholar
[2] Dujaili, Mohammed Jawad AI. Survey on facial expressions recognition: databases, features and classification schemes. Multimed Tools Appl. 2024;83(3):7457–78.10.1007/s11042-023-15139-wSuche in Google Scholar
[3] Aman K, Rani R, Nigam A. A comprehensive survey and deep learning-based approach for human recognition using ear biometric. Vis Comput. 2022;38(7):2383–416.10.1007/s00371-021-02119-0Suche in Google Scholar PubMed PubMed Central
[4] Althabhawee AFY, Alwawi BKOC. Fingerprint recognition based on collected images using deep learning technology. IAES Int J Artif Intell. 2022;11(1):81.10.11591/ijai.v11.i1.pp81-88Suche in Google Scholar
[5] Kumar A, Zhou Y. Human identification using finger images. IEEE Trans Image Proc. 2011;21(4):2228–44.10.1109/TIP.2011.2171697Suche in Google Scholar PubMed
[6] Chanukya PS, Thivakaran TK. Multimodal biometric cryptosystem for human authentication using fingerprint and ear. Multimed Tools Appl. 2020;79:659–73.10.1007/s11042-019-08123-wSuche in Google Scholar
[7] Jain AK, Ross AA, Nandakumar K. Introduce on to Biometric. New York: Springer; 2011.10.1007/978-0-387-77326-1Suche in Google Scholar
[8] Shen L, Bai L, Ji ZH. Hand-based biometrics fusing palm and finger-knuckle-print. Proc IEEE Int Workhsop Emerg Tech Chall (ETCHB). 2010;1:123129.10.1109/ETCHB.2010.5559284Suche in Google Scholar
[9] Usha K, Ezhilarasan M. Personal recognition using finger knuckle shape oriented features and texture analysis. J King Saud UnivComput Inf Sci. 2016;28(4):416–31.10.1016/j.jksuci.2015.02.004Suche in Google Scholar
[10] Yin J, Zhou J, Zh J. Weighted linear embedding and its application to finger-knucckleprint and palmprint recognition. International Workshop on Emerging Techniques and Challenges for Hand-Based Biometrics. Istanbul, Turkey: IEEE; 2010. p. 1–4.10.1109/ETCHB.2010.5559291Suche in Google Scholar
[11] Zhang L, Zhang D, Zhu H. Online finger-knuckle-print verification for personal authentication. Patt Recognit. 2010;43:2560–71.10.1016/j.patcog.2010.01.020Suche in Google Scholar
[12] Kang W, Chen X, Wu Q. The biometric recognition on contactless multi-spectrum finger images. Inf Phys Technol. 2015;68:19–27.10.1016/j.infrared.2014.10.007Suche in Google Scholar
[13] Peralta D, Galar M, Triguero I, Miguel-Hurtado O, Benitez JM, Herrera F. Minutiae filtering to improve both efficacy and efficiency of fingerprint matching algorithms. Eng Appl Artif Intell. 2014;32:37–53.10.1016/j.engappai.2014.02.016Suche in Google Scholar
[14] Lee W, Cho S, Choi H, Kim J. Partial fingerprint matching using minutiae and ridge shape features for small fingerprint scanners. Expert Syst Appl. 2017 Nov;87:183–98.10.1016/j.eswa.2017.06.019Suche in Google Scholar
[15] Khusnuliawati H, Fatichah C, Soelaiman R. A comparative study of finger vein recognition by using learning vector quantization. Iptek J Proc Ser. 2017;3(2):136–42.10.12962/j23546026.y2017i2.2311Suche in Google Scholar
[16] Hu N, Ma H, Zhan T. Finger vein biometric verification using block multi-scale uniform local binary pattern features and block two-directional two-dimension principal component analysis. Optik. 2020;208:163664.Suche in Google Scholar
[17] Babu GS, Bobby ND, Bennet MA, Shalini B, Srilakshmi K. Multistage feature extraction of finger vein patterns using gabor filters. Iioab J. 2017;8:84–91.Suche in Google Scholar
[18] Prommegger B, Kauba C, Uhl A. Multi-perspective finger-vein biometrics. In: Proceedings of the 2018 IEEE 9th International Conference on Biometrics Theory, Applications and Systems (BTAS). Redondo Beach, CA, USA; October 2018. p. 22–5.10.1109/BTAS.2018.8698558Suche in Google Scholar
[19] Kovač I, Marák P. Openfinger: Towards a combination of discriminative power of fingerprints and finger vein patterns in multimodal biometric system. Tatra Mt Math Publ. 2020;77:109–38.10.2478/tmmp-2020-0012Suche in Google Scholar
[20] Smith M, Miller S. The ethical application of biometric facial recognition technology. Ai Soc. 2022;37(1):167–75.10.1007/s00146-021-01199-9Suche in Google Scholar PubMed PubMed Central
[21] Li L, Mu X, Li S, Peng H. A review of face recognition technology. IEEE Access. 2020;8:139110–20.10.1109/ACCESS.2020.3011028Suche in Google Scholar
[22] Abdul Cader M, Jahan A, Banks J, Chandran V. Fingerprint systems: sensors, image acquisition, interoperability and challenges. Sensors. 2023;23(14):6591.10.3390/s23146591Suche in Google Scholar PubMed PubMed Central
[23] Kovač I, Marák P. Finger vein recognition: utilization of adaptive gabor filters in the enhancement stage combined with sift/surf-based feature extraction. Signal Image Video Proc. 2023;17(3):635–41.10.1007/s11760-022-02270-8Suche in Google Scholar
[24] Ding S, Bian W, Liao H, Sun T, Xue Y. Combining Gabor filtering and classification dictionaries learning for fingerprint enhancement. Iet Biometrics. 2017;6(6):438–47.10.1049/iet-bmt.2016.0161Suche in Google Scholar
[25] Lowe DG. Object recognition from local scale-invariant features. Proceedings of the Seventh IEEE International Conference on Computer Vision. vol. 2, IEEE; 1999.10.1109/ICCV.1999.790410Suche in Google Scholar
[26] Hardika K, Fatichah C, Soelaiman R. Multi-feature fusion using SIFT and LEBP for finger vein recognition. Telkomnika. 2017;15(1):478–85.10.12928/telkomnika.v15i1.4443Suche in Google Scholar
[27] Al-Dujaili MJ, Ebrahimi-Moghadam A. Speech emotion recognition: a comprehensive survey. Wirel Pers Commun. 2023;129(4):2525–61.10.1007/s11277-023-10244-3Suche in Google Scholar
[28] Beng TS, Rosdi BA. Finger-vein identification using pattern map and principal component analysis. 2011 IEEE International Conference on Signal and Image Processing Applications. IEEE; 2011.10.1109/ICSIPA.2011.6144093Suche in Google Scholar
[29] Hu N, Hui M, Zhan T. Finger vein biometric verification using block multi-scale uniform local binary pattern features and block two-directional two-dimension principal component analysis. Optik. 2020;208:163664.10.1016/j.ijleo.2019.163664Suche in Google Scholar
[30] Al-Dujaili MJ, Ahily HJ. A new hybrid model to predict human age estimation from face images based on supervised machine learning algorithms. Cybernet Inf Technol. 2023;23(2):20–33.10.2478/cait-2023-0011Suche in Google Scholar
[31] Kapoor K, Rani S, Kumar M, Chopra V, Brar GS. Hybrid local phase quantization and grey wolf optimization based SVM for finger vein recognition. Multimed Tools Appl. 2021;80:15233–71.10.1007/s11042-021-10548-1Suche in Google Scholar
[32] Zhang X, Wang W. Finger vein recognition method based on GLCM-HOG and SVM. 2020 IEEE 3rd International Conference on Information Systems and Computer Aided Education (ICISCAE). IEEE; 2020.10.1109/ICISCAE51034.2020.9236798Suche in Google Scholar
[33] Al Dujaili MJ, Ebrahimi-Moghadam A. Automatic speech emotion recognition based on hybrid features with ANN, LDA and K_NN classifiers. Multimed Tools Appl. 2023;82(27):42783–801.10.1007/s11042-023-15413-xSuche in Google Scholar
[34] Al-Dulaimi MA, Al-Nima RR, Sharba MR. Encrypting communication transmission messages by utilizing multi-layer perception neural network. Informatica. 2021:32(4):21–39.Suche in Google Scholar
[35] Khanam R, Ramsha K, Rajeev R. Analysis of finger vein feature extraction and recognition using DA and KNN methods. 2019 Amity international conference on artificial intelligence (AICAI). IEEE; 2019.10.1109/AICAI.2019.8701253Suche in Google Scholar
© 2024 the author(s), published by De Gruyter
This work is licensed under the Creative Commons Attribution 4.0 International License.
Artikel in diesem Heft
- Regular Articles
- Methodology of automated quality management
- Influence of vibratory conveyor design parameters on the trough motion and the self-synchronization of inertial vibrators
- Application of finite element method in industrial design, example of an electric motorcycle design project
- Correlative evaluation of the corrosion resilience and passivation properties of zinc and aluminum alloys in neutral chloride and acid-chloride solutions
- Will COVID “encourage” B2B and data exchange engineering in logistic firms?
- Influence of unsupported sleepers on flange climb derailment of two freight wagons
- A hybrid detection algorithm for 5G OTFS waveform for 64 and 256 QAM with Rayleigh and Rician channels
- Effect of short heat treatment on mechanical properties and shape memory properties of Cu–Al–Ni shape memory alloy
- Exploring the potential of ammonia and hydrogen as alternative fuels for transportation
- Impact of insulation on energy consumption and CO2 emissions in high-rise commercial buildings at various climate zones
- Advanced autopilot design with extremum-seeking control for aircraft control
- Adaptive multidimensional trust-based recommendation model for peer to peer applications
- Effects of CFRP sheets on the flexural behavior of high-strength concrete beam
- Enhancing urban sustainability through industrial synergy: A multidisciplinary framework for integrating sustainable industrial practices within urban settings – The case of Hamadan industrial city
- Advanced vibrant controller results of an energetic framework structure
- Application of the Taguchi method and RSM for process parameter optimization in AWSJ machining of CFRP composite-based orthopedic implants
- Improved correlation of soil modulus with SPT N values
- Technologies for high-temperature batch annealing of grain-oriented electrical steel: An overview
- Assessing the need for the adoption of digitalization in Indian small and medium enterprises
- A non-ideal hybridization issue for vertical TFET-based dielectric-modulated biosensor
- Optimizing data retrieval for enhanced data integrity verification in cloud environments
- Performance analysis of nonlinear crosstalk of WDM systems using modulation schemes criteria
- Nonlinear finite-element analysis of RC beams with various opening near supports
- Thermal analysis of Fe3O4–Cu/water over a cone: a fractional Maxwell model
- Radial–axial runner blade design using the coordinate slice technique
- Theoretical and experimental comparison between straight and curved continuous box girders
- Effect of the reinforcement ratio on the mechanical behaviour of textile-reinforced concrete composite: Experiment and numerical modeling
- Experimental and numerical investigation on composite beam–column joint connection behavior using different types of connection schemes
- Enhanced performance and robustness in anti-lock brake systems using barrier function-based integral sliding mode control
- Evaluation of the creep strength of samples produced by fused deposition modeling
- A combined feedforward-feedback controller design for nonlinear systems
- Effect of adjacent structures on footing settlement for different multi-building arrangements
- Analyzing the impact of curved tracks on wheel flange thickness reduction in railway systems
- Review Articles
- Mechanical and smart properties of cement nanocomposites containing nanomaterials: A brief review
- Applications of nanotechnology and nanoproduction techniques
- Relationship between indoor environmental quality and guests’ comfort and satisfaction at green hotels: A comprehensive review
- Communication
- Techniques to mitigate the admission of radon inside buildings
- Erratum
- Erratum to “Effect of short heat treatment on mechanical properties and shape memory properties of Cu–Al–Ni shape memory alloy”
- Special Issue: AESMT-3 - Part II
- Integrated fuzzy logic and multicriteria decision model methods for selecting suitable sites for wastewater treatment plant: A case study in the center of Basrah, Iraq
- Physical and mechanical response of porous metals composites with nano-natural additives
- Special Issue: AESMT-4 - Part II
- New recycling method of lubricant oil and the effect on the viscosity and viscous shear as an environmentally friendly
- Identify the effect of Fe2O3 nanoparticles on mechanical and microstructural characteristics of aluminum matrix composite produced by powder metallurgy technique
- Static behavior of piled raft foundation in clay
- Ultra-low-power CMOS ring oscillator with minimum power consumption of 2.9 pW using low-voltage biasing technique
- Using ANN for well type identifying and increasing production from Sa’di formation of Halfaya oil field – Iraq
- Optimizing the performance of concrete tiles using nano-papyrus and carbon fibers
- Special Issue: AESMT-5 - Part II
- Comparative the effect of distribution transformer coil shape on electromagnetic forces and their distribution using the FEM
- The complex of Weyl module in free characteristic in the event of a partition (7,5,3)
- Restrained captive domination number
- Experimental study of improving hot mix asphalt reinforced with carbon fibers
- Asphalt binder modified with recycled tyre rubber
- Thermal performance of radiant floor cooling with phase change material for energy-efficient buildings
- Surveying the prediction of risks in cryptocurrency investments using recurrent neural networks
- A deep reinforcement learning framework to modify LQR for an active vibration control applied to 2D building models
- Evaluation of mechanically stabilized earth retaining walls for different soil–structure interaction methods: A review
- Assessment of heat transfer in a triangular duct with different configurations of ribs using computational fluid dynamics
- Sulfate removal from wastewater by using waste material as an adsorbent
- Experimental investigation on strengthening lap joints subjected to bending in glulam timber beams using CFRP sheets
- A study of the vibrations of a rotor bearing suspended by a hybrid spring system of shape memory alloys
- Stability analysis of Hub dam under rapid drawdown
- Developing ANFIS-FMEA model for assessment and prioritization of potential trouble factors in Iraqi building projects
- Numerical and experimental comparison study of piled raft foundation
- Effect of asphalt modified with waste engine oil on the durability properties of hot asphalt mixtures with reclaimed asphalt pavement
- Hydraulic model for flood inundation in Diyala River Basin using HEC-RAS, PMP, and neural network
- Numerical study on discharge capacity of piano key side weir with various ratios of the crest length to the width
- The optimal allocation of thyristor-controlled series compensators for enhancement HVAC transmission lines Iraqi super grid by using seeker optimization algorithm
- Numerical and experimental study of the impact on aerodynamic characteristics of the NACA0012 airfoil
- Effect of nano-TiO2 on physical and rheological properties of asphalt cement
- Performance evolution of novel palm leaf powder used for enhancing hot mix asphalt
- Performance analysis, evaluation, and improvement of selected unsignalized intersection using SIDRA software – Case study
- Flexural behavior of RC beams externally reinforced with CFRP composites using various strategies
- Influence of fiber types on the properties of the artificial cold-bonded lightweight aggregates
- Experimental investigation of RC beams strengthened with externally bonded BFRP composites
- Generalized RKM methods for solving fifth-order quasi-linear fractional partial differential equation
- An experimental and numerical study investigating sediment transport position in the bed of sewer pipes in Karbala
- Role of individual component failure in the performance of a 1-out-of-3 cold standby system: A Markov model approach
- Implementation for the cases (5, 4) and (5, 4)/(2, 0)
- Center group actions and related concepts
- Experimental investigation of the effect of horizontal construction joints on the behavior of deep beams
- Deletion of a vertex in even sum domination
- Deep learning techniques in concrete powder mix designing
- Effect of loading type in concrete deep beam with strut reinforcement
- Studying the effect of using CFRP warping on strength of husk rice concrete columns
- Parametric analysis of the influence of climatic factors on the formation of traditional buildings in the city of Al Najaf
- Suitability location for landfill using a fuzzy-GIS model: A case study in Hillah, Iraq
- Hybrid approach for cost estimation of sustainable building projects using artificial neural networks
- Assessment of indirect tensile stress and tensile–strength ratio and creep compliance in HMA mixes with micro-silica and PMB
- Density functional theory to study stopping power of proton in water, lung, bladder, and intestine
- A review of single flow, flow boiling, and coating microchannel studies
- Effect of GFRP bar length on the flexural behavior of hybrid concrete beams strengthened with NSM bars
- Exploring the impact of parameters on flow boiling heat transfer in microchannels and coated microtubes: A comprehensive review
- Crumb rubber modification for enhanced rutting resistance in asphalt mixtures
- Special Issue: AESMT-6
- Design of a new sorting colors system based on PLC, TIA portal, and factory I/O programs
- Forecasting empirical formula for suspended sediment load prediction at upstream of Al-Kufa barrage, Kufa City, Iraq
- Optimization and characterization of sustainable geopolymer mortars based on palygorskite clay, water glass, and sodium hydroxide
- Sediment transport modelling upstream of Al Kufa Barrage
- Study of energy loss, range, and stopping time for proton in germanium and copper materials
- Effect of internal and external recycle ratios on the nutrient removal efficiency of anaerobic/anoxic/oxic (VIP) wastewater treatment plant
- Enhancing structural behaviour of polypropylene fibre concrete columns longitudinally reinforced with fibreglass bars
- Sustainable road paving: Enhancing concrete paver blocks with zeolite-enhanced cement
- Evaluation of the operational performance of Karbala waste water treatment plant under variable flow using GPS-X model
- Design and simulation of photonic crystal fiber for highly sensitive chemical sensing applications
- Optimization and design of a new column sequencing for crude oil distillation at Basrah refinery
- Inductive 3D numerical modelling of the tibia bone using MRI to examine von Mises stress and overall deformation
- An image encryption method based on modified elliptic curve Diffie-Hellman key exchange protocol and Hill Cipher
- Experimental investigation of generating superheated steam using a parabolic dish with a cylindrical cavity receiver: A case study
- Effect of surface roughness on the interface behavior of clayey soils
- Investigated of the optical properties for SiO2 by using Lorentz model
- Measurements of induced vibrations due to steel pipe pile driving in Al-Fao soil: Effect of partial end closure
- Experimental and numerical studies of ballistic resistance of hybrid sandwich composite body armor
- Evaluation of clay layer presence on shallow foundation settlement in dry sand under an earthquake
- Optimal design of mechanical performances of asphalt mixtures comprising nano-clay additives
- Advancing seismic performance: Isolators, TMDs, and multi-level strategies in reinforced concrete buildings
- Predicted evaporation in Basrah using artificial neural networks
- Energy management system for a small town to enhance quality of life
- Numerical study on entropy minimization in pipes with helical airfoil and CuO nanoparticle integration
- Equations and methodologies of inlet drainage system discharge coefficients: A review
- Thermal buckling analysis for hybrid and composite laminated plate by using new displacement function
- Investigation into the mechanical and thermal properties of lightweight mortar using commercial beads or recycled expanded polystyrene
- Experimental and theoretical analysis of single-jet column and concrete column using double-jet grouting technique applied at Al-Rashdia site
- The impact of incorporating waste materials on the mechanical and physical characteristics of tile adhesive materials
- Seismic resilience: Innovations in structural engineering for earthquake-prone areas
- Automatic human identification using fingerprint images based on Gabor filter and SIFT features fusion
- Performance of GRKM-method for solving classes of ordinary and partial differential equations of sixth-orders
- Visible light-boosted photodegradation activity of Ag–AgVO3/Zn0.5Mn0.5Fe2O4 supported heterojunctions for effective degradation of organic contaminates
- Production of sustainable concrete with treated cement kiln dust and iron slag waste aggregate
- Key effects on the structural behavior of fiber-reinforced lightweight concrete-ribbed slabs: A review
- A comparative analysis of the energy dissipation efficiency of various piano key weir types
- Special Issue: Transport 2022 - Part II
- Variability in road surface temperature in urban road network – A case study making use of mobile measurements
- Special Issue: BCEE5-2023
- Evaluation of reclaimed asphalt mixtures rejuvenated with waste engine oil to resist rutting deformation
- Assessment of potential resistance to moisture damage and fatigue cracks of asphalt mixture modified with ground granulated blast furnace slag
- Investigating seismic response in adjacent structures: A study on the impact of buildings’ orientation and distance considering soil–structure interaction
- Improvement of porosity of mortar using polyethylene glycol pre-polymer-impregnated mortar
- Three-dimensional analysis of steel beam-column bolted connections
- Assessment of agricultural drought in Iraq employing Landsat and MODIS imagery
- Performance evaluation of grouted porous asphalt concrete
- Optimization of local modified metakaolin-based geopolymer concrete by Taguchi method
- Effect of waste tire products on some characteristics of roller-compacted concrete
- Studying the lateral displacement of retaining wall supporting sandy soil under dynamic loads
- Seismic performance evaluation of concrete buttress dram (Dynamic linear analysis)
- Behavior of soil reinforced with micropiles
- Possibility of production high strength lightweight concrete containing organic waste aggregate and recycled steel fibers
- An investigation of self-sensing and mechanical properties of smart engineered cementitious composites reinforced with functional materials
- Forecasting changes in precipitation and temperatures of a regional watershed in Northern Iraq using LARS-WG model
- Experimental investigation of dynamic soil properties for modeling energy-absorbing layers
- Numerical investigation of the effect of longitudinal steel reinforcement ratio on the ductility of concrete beams
- An experimental study on the tensile properties of reinforced asphalt pavement
- Self-sensing behavior of hot asphalt mixture with steel fiber-based additive
- Behavior of ultra-high-performance concrete deep beams reinforced by basalt fibers
- Optimizing asphalt binder performance with various PET types
- Investigation of the hydraulic characteristics and homogeneity of the microstructure of the air voids in the sustainable rigid pavement
- Enhanced biogas production from municipal solid waste via digestion with cow manure: A case study
- Special Issue: AESMT-7 - Part I
- Preparation and investigation of cobalt nanoparticles by laser ablation: Structure, linear, and nonlinear optical properties
- Seismic analysis of RC building with plan irregularity in Baghdad/Iraq to obtain the optimal behavior
- The effect of urban environment on large-scale path loss model’s main parameters for mmWave 5G mobile network in Iraq
- Formatting a questionnaire for the quality control of river bank roads
- Vibration suppression of smart composite beam using model predictive controller
- Machine learning-based compressive strength estimation in nanomaterial-modified lightweight concrete
- In-depth analysis of critical factors affecting Iraqi construction projects performance
- Behavior of container berth structure under the influence of environmental and operational loads
- Energy absorption and impact response of ballistic resistance laminate
- Effect of water-absorbent polymer balls in internal curing on punching shear behavior of bubble slabs
- Effect of surface roughness on interface shear strength parameters of sandy soils
- Evaluating the interaction for embedded H-steel section in normal concrete under monotonic and repeated loads
- Estimation of the settlement of pile head using ANN and multivariate linear regression based on the results of load transfer method
- Enhancing communication: Deep learning for Arabic sign language translation
- A review of recent studies of both heat pipe and evaporative cooling in passive heat recovery
- Effect of nano-silica on the mechanical properties of LWC
- An experimental study of some mechanical properties and absorption for polymer-modified cement mortar modified with superplasticizer
- Digital beamforming enhancement with LSTM-based deep learning for millimeter wave transmission
- Developing an efficient planning process for heritage buildings maintenance in Iraq
- Design and optimization of two-stage controller for three-phase multi-converter/multi-machine electric vehicle
- Evaluation of microstructure and mechanical properties of Al1050/Al2O3/Gr composite processed by forming operation ECAP
- Calculations of mass stopping power and range of protons in organic compounds (CH3OH, CH2O, and CO2) at energy range of 0.01–1,000 MeV
- Investigation of in vitro behavior of composite coating hydroxyapatite-nano silver on 316L stainless steel substrate by electrophoretic technic for biomedical tools
- A review: Enhancing tribological properties of journal bearings composite materials
- Improvements in the randomness and security of digital currency using the photon sponge hash function through Maiorana–McFarland S-box replacement
- Design a new scheme for image security using a deep learning technique of hierarchical parameters
- Special Issue: ICES 2023
- Comparative geotechnical analysis for ultimate bearing capacity of precast concrete piles using cone resistance measurements
- Visualizing sustainable rainwater harvesting: A case study of Karbala Province
- Geogrid reinforcement for improving bearing capacity and stability of square foundations
- Evaluation of the effluent concentrations of Karbala wastewater treatment plant using reliability analysis
- Adsorbent made with inexpensive, local resources
- Effect of drain pipes on seepage and slope stability through a zoned earth dam
- Sediment accumulation in an 8 inch sewer pipe for a sample of various particles obtained from the streets of Karbala city, Iraq
- Special Issue: IETAS 2024 - Part I
- Analyzing the impact of transfer learning on explanation accuracy in deep learning-based ECG recognition systems
- Effect of scale factor on the dynamic response of frame foundations
- Improving multi-object detection and tracking with deep learning, DeepSORT, and frame cancellation techniques
- The impact of using prestressed CFRP bars on the development of flexural strength
- Assessment of surface hardness and impact strength of denture base resins reinforced with silver–titanium dioxide and silver–zirconium dioxide nanoparticles: In vitro study
- A data augmentation approach to enhance breast cancer detection using generative adversarial and artificial neural networks
- Modification of the 5D Lorenz chaotic map with fuzzy numbers for video encryption in cloud computing
- Special Issue: 51st KKBN - Part I
- Evaluation of static bending caused damage of glass-fiber composite structure using terahertz inspection
Artikel in diesem Heft
- Regular Articles
- Methodology of automated quality management
- Influence of vibratory conveyor design parameters on the trough motion and the self-synchronization of inertial vibrators
- Application of finite element method in industrial design, example of an electric motorcycle design project
- Correlative evaluation of the corrosion resilience and passivation properties of zinc and aluminum alloys in neutral chloride and acid-chloride solutions
- Will COVID “encourage” B2B and data exchange engineering in logistic firms?
- Influence of unsupported sleepers on flange climb derailment of two freight wagons
- A hybrid detection algorithm for 5G OTFS waveform for 64 and 256 QAM with Rayleigh and Rician channels
- Effect of short heat treatment on mechanical properties and shape memory properties of Cu–Al–Ni shape memory alloy
- Exploring the potential of ammonia and hydrogen as alternative fuels for transportation
- Impact of insulation on energy consumption and CO2 emissions in high-rise commercial buildings at various climate zones
- Advanced autopilot design with extremum-seeking control for aircraft control
- Adaptive multidimensional trust-based recommendation model for peer to peer applications
- Effects of CFRP sheets on the flexural behavior of high-strength concrete beam
- Enhancing urban sustainability through industrial synergy: A multidisciplinary framework for integrating sustainable industrial practices within urban settings – The case of Hamadan industrial city
- Advanced vibrant controller results of an energetic framework structure
- Application of the Taguchi method and RSM for process parameter optimization in AWSJ machining of CFRP composite-based orthopedic implants
- Improved correlation of soil modulus with SPT N values
- Technologies for high-temperature batch annealing of grain-oriented electrical steel: An overview
- Assessing the need for the adoption of digitalization in Indian small and medium enterprises
- A non-ideal hybridization issue for vertical TFET-based dielectric-modulated biosensor
- Optimizing data retrieval for enhanced data integrity verification in cloud environments
- Performance analysis of nonlinear crosstalk of WDM systems using modulation schemes criteria
- Nonlinear finite-element analysis of RC beams with various opening near supports
- Thermal analysis of Fe3O4–Cu/water over a cone: a fractional Maxwell model
- Radial–axial runner blade design using the coordinate slice technique
- Theoretical and experimental comparison between straight and curved continuous box girders
- Effect of the reinforcement ratio on the mechanical behaviour of textile-reinforced concrete composite: Experiment and numerical modeling
- Experimental and numerical investigation on composite beam–column joint connection behavior using different types of connection schemes
- Enhanced performance and robustness in anti-lock brake systems using barrier function-based integral sliding mode control
- Evaluation of the creep strength of samples produced by fused deposition modeling
- A combined feedforward-feedback controller design for nonlinear systems
- Effect of adjacent structures on footing settlement for different multi-building arrangements
- Analyzing the impact of curved tracks on wheel flange thickness reduction in railway systems
- Review Articles
- Mechanical and smart properties of cement nanocomposites containing nanomaterials: A brief review
- Applications of nanotechnology and nanoproduction techniques
- Relationship between indoor environmental quality and guests’ comfort and satisfaction at green hotels: A comprehensive review
- Communication
- Techniques to mitigate the admission of radon inside buildings
- Erratum
- Erratum to “Effect of short heat treatment on mechanical properties and shape memory properties of Cu–Al–Ni shape memory alloy”
- Special Issue: AESMT-3 - Part II
- Integrated fuzzy logic and multicriteria decision model methods for selecting suitable sites for wastewater treatment plant: A case study in the center of Basrah, Iraq
- Physical and mechanical response of porous metals composites with nano-natural additives
- Special Issue: AESMT-4 - Part II
- New recycling method of lubricant oil and the effect on the viscosity and viscous shear as an environmentally friendly
- Identify the effect of Fe2O3 nanoparticles on mechanical and microstructural characteristics of aluminum matrix composite produced by powder metallurgy technique
- Static behavior of piled raft foundation in clay
- Ultra-low-power CMOS ring oscillator with minimum power consumption of 2.9 pW using low-voltage biasing technique
- Using ANN for well type identifying and increasing production from Sa’di formation of Halfaya oil field – Iraq
- Optimizing the performance of concrete tiles using nano-papyrus and carbon fibers
- Special Issue: AESMT-5 - Part II
- Comparative the effect of distribution transformer coil shape on electromagnetic forces and their distribution using the FEM
- The complex of Weyl module in free characteristic in the event of a partition (7,5,3)
- Restrained captive domination number
- Experimental study of improving hot mix asphalt reinforced with carbon fibers
- Asphalt binder modified with recycled tyre rubber
- Thermal performance of radiant floor cooling with phase change material for energy-efficient buildings
- Surveying the prediction of risks in cryptocurrency investments using recurrent neural networks
- A deep reinforcement learning framework to modify LQR for an active vibration control applied to 2D building models
- Evaluation of mechanically stabilized earth retaining walls for different soil–structure interaction methods: A review
- Assessment of heat transfer in a triangular duct with different configurations of ribs using computational fluid dynamics
- Sulfate removal from wastewater by using waste material as an adsorbent
- Experimental investigation on strengthening lap joints subjected to bending in glulam timber beams using CFRP sheets
- A study of the vibrations of a rotor bearing suspended by a hybrid spring system of shape memory alloys
- Stability analysis of Hub dam under rapid drawdown
- Developing ANFIS-FMEA model for assessment and prioritization of potential trouble factors in Iraqi building projects
- Numerical and experimental comparison study of piled raft foundation
- Effect of asphalt modified with waste engine oil on the durability properties of hot asphalt mixtures with reclaimed asphalt pavement
- Hydraulic model for flood inundation in Diyala River Basin using HEC-RAS, PMP, and neural network
- Numerical study on discharge capacity of piano key side weir with various ratios of the crest length to the width
- The optimal allocation of thyristor-controlled series compensators for enhancement HVAC transmission lines Iraqi super grid by using seeker optimization algorithm
- Numerical and experimental study of the impact on aerodynamic characteristics of the NACA0012 airfoil
- Effect of nano-TiO2 on physical and rheological properties of asphalt cement
- Performance evolution of novel palm leaf powder used for enhancing hot mix asphalt
- Performance analysis, evaluation, and improvement of selected unsignalized intersection using SIDRA software – Case study
- Flexural behavior of RC beams externally reinforced with CFRP composites using various strategies
- Influence of fiber types on the properties of the artificial cold-bonded lightweight aggregates
- Experimental investigation of RC beams strengthened with externally bonded BFRP composites
- Generalized RKM methods for solving fifth-order quasi-linear fractional partial differential equation
- An experimental and numerical study investigating sediment transport position in the bed of sewer pipes in Karbala
- Role of individual component failure in the performance of a 1-out-of-3 cold standby system: A Markov model approach
- Implementation for the cases (5, 4) and (5, 4)/(2, 0)
- Center group actions and related concepts
- Experimental investigation of the effect of horizontal construction joints on the behavior of deep beams
- Deletion of a vertex in even sum domination
- Deep learning techniques in concrete powder mix designing
- Effect of loading type in concrete deep beam with strut reinforcement
- Studying the effect of using CFRP warping on strength of husk rice concrete columns
- Parametric analysis of the influence of climatic factors on the formation of traditional buildings in the city of Al Najaf
- Suitability location for landfill using a fuzzy-GIS model: A case study in Hillah, Iraq
- Hybrid approach for cost estimation of sustainable building projects using artificial neural networks
- Assessment of indirect tensile stress and tensile–strength ratio and creep compliance in HMA mixes with micro-silica and PMB
- Density functional theory to study stopping power of proton in water, lung, bladder, and intestine
- A review of single flow, flow boiling, and coating microchannel studies
- Effect of GFRP bar length on the flexural behavior of hybrid concrete beams strengthened with NSM bars
- Exploring the impact of parameters on flow boiling heat transfer in microchannels and coated microtubes: A comprehensive review
- Crumb rubber modification for enhanced rutting resistance in asphalt mixtures
- Special Issue: AESMT-6
- Design of a new sorting colors system based on PLC, TIA portal, and factory I/O programs
- Forecasting empirical formula for suspended sediment load prediction at upstream of Al-Kufa barrage, Kufa City, Iraq
- Optimization and characterization of sustainable geopolymer mortars based on palygorskite clay, water glass, and sodium hydroxide
- Sediment transport modelling upstream of Al Kufa Barrage
- Study of energy loss, range, and stopping time for proton in germanium and copper materials
- Effect of internal and external recycle ratios on the nutrient removal efficiency of anaerobic/anoxic/oxic (VIP) wastewater treatment plant
- Enhancing structural behaviour of polypropylene fibre concrete columns longitudinally reinforced with fibreglass bars
- Sustainable road paving: Enhancing concrete paver blocks with zeolite-enhanced cement
- Evaluation of the operational performance of Karbala waste water treatment plant under variable flow using GPS-X model
- Design and simulation of photonic crystal fiber for highly sensitive chemical sensing applications
- Optimization and design of a new column sequencing for crude oil distillation at Basrah refinery
- Inductive 3D numerical modelling of the tibia bone using MRI to examine von Mises stress and overall deformation
- An image encryption method based on modified elliptic curve Diffie-Hellman key exchange protocol and Hill Cipher
- Experimental investigation of generating superheated steam using a parabolic dish with a cylindrical cavity receiver: A case study
- Effect of surface roughness on the interface behavior of clayey soils
- Investigated of the optical properties for SiO2 by using Lorentz model
- Measurements of induced vibrations due to steel pipe pile driving in Al-Fao soil: Effect of partial end closure
- Experimental and numerical studies of ballistic resistance of hybrid sandwich composite body armor
- Evaluation of clay layer presence on shallow foundation settlement in dry sand under an earthquake
- Optimal design of mechanical performances of asphalt mixtures comprising nano-clay additives
- Advancing seismic performance: Isolators, TMDs, and multi-level strategies in reinforced concrete buildings
- Predicted evaporation in Basrah using artificial neural networks
- Energy management system for a small town to enhance quality of life
- Numerical study on entropy minimization in pipes with helical airfoil and CuO nanoparticle integration
- Equations and methodologies of inlet drainage system discharge coefficients: A review
- Thermal buckling analysis for hybrid and composite laminated plate by using new displacement function
- Investigation into the mechanical and thermal properties of lightweight mortar using commercial beads or recycled expanded polystyrene
- Experimental and theoretical analysis of single-jet column and concrete column using double-jet grouting technique applied at Al-Rashdia site
- The impact of incorporating waste materials on the mechanical and physical characteristics of tile adhesive materials
- Seismic resilience: Innovations in structural engineering for earthquake-prone areas
- Automatic human identification using fingerprint images based on Gabor filter and SIFT features fusion
- Performance of GRKM-method for solving classes of ordinary and partial differential equations of sixth-orders
- Visible light-boosted photodegradation activity of Ag–AgVO3/Zn0.5Mn0.5Fe2O4 supported heterojunctions for effective degradation of organic contaminates
- Production of sustainable concrete with treated cement kiln dust and iron slag waste aggregate
- Key effects on the structural behavior of fiber-reinforced lightweight concrete-ribbed slabs: A review
- A comparative analysis of the energy dissipation efficiency of various piano key weir types
- Special Issue: Transport 2022 - Part II
- Variability in road surface temperature in urban road network – A case study making use of mobile measurements
- Special Issue: BCEE5-2023
- Evaluation of reclaimed asphalt mixtures rejuvenated with waste engine oil to resist rutting deformation
- Assessment of potential resistance to moisture damage and fatigue cracks of asphalt mixture modified with ground granulated blast furnace slag
- Investigating seismic response in adjacent structures: A study on the impact of buildings’ orientation and distance considering soil–structure interaction
- Improvement of porosity of mortar using polyethylene glycol pre-polymer-impregnated mortar
- Three-dimensional analysis of steel beam-column bolted connections
- Assessment of agricultural drought in Iraq employing Landsat and MODIS imagery
- Performance evaluation of grouted porous asphalt concrete
- Optimization of local modified metakaolin-based geopolymer concrete by Taguchi method
- Effect of waste tire products on some characteristics of roller-compacted concrete
- Studying the lateral displacement of retaining wall supporting sandy soil under dynamic loads
- Seismic performance evaluation of concrete buttress dram (Dynamic linear analysis)
- Behavior of soil reinforced with micropiles
- Possibility of production high strength lightweight concrete containing organic waste aggregate and recycled steel fibers
- An investigation of self-sensing and mechanical properties of smart engineered cementitious composites reinforced with functional materials
- Forecasting changes in precipitation and temperatures of a regional watershed in Northern Iraq using LARS-WG model
- Experimental investigation of dynamic soil properties for modeling energy-absorbing layers
- Numerical investigation of the effect of longitudinal steel reinforcement ratio on the ductility of concrete beams
- An experimental study on the tensile properties of reinforced asphalt pavement
- Self-sensing behavior of hot asphalt mixture with steel fiber-based additive
- Behavior of ultra-high-performance concrete deep beams reinforced by basalt fibers
- Optimizing asphalt binder performance with various PET types
- Investigation of the hydraulic characteristics and homogeneity of the microstructure of the air voids in the sustainable rigid pavement
- Enhanced biogas production from municipal solid waste via digestion with cow manure: A case study
- Special Issue: AESMT-7 - Part I
- Preparation and investigation of cobalt nanoparticles by laser ablation: Structure, linear, and nonlinear optical properties
- Seismic analysis of RC building with plan irregularity in Baghdad/Iraq to obtain the optimal behavior
- The effect of urban environment on large-scale path loss model’s main parameters for mmWave 5G mobile network in Iraq
- Formatting a questionnaire for the quality control of river bank roads
- Vibration suppression of smart composite beam using model predictive controller
- Machine learning-based compressive strength estimation in nanomaterial-modified lightweight concrete
- In-depth analysis of critical factors affecting Iraqi construction projects performance
- Behavior of container berth structure under the influence of environmental and operational loads
- Energy absorption and impact response of ballistic resistance laminate
- Effect of water-absorbent polymer balls in internal curing on punching shear behavior of bubble slabs
- Effect of surface roughness on interface shear strength parameters of sandy soils
- Evaluating the interaction for embedded H-steel section in normal concrete under monotonic and repeated loads
- Estimation of the settlement of pile head using ANN and multivariate linear regression based on the results of load transfer method
- Enhancing communication: Deep learning for Arabic sign language translation
- A review of recent studies of both heat pipe and evaporative cooling in passive heat recovery
- Effect of nano-silica on the mechanical properties of LWC
- An experimental study of some mechanical properties and absorption for polymer-modified cement mortar modified with superplasticizer
- Digital beamforming enhancement with LSTM-based deep learning for millimeter wave transmission
- Developing an efficient planning process for heritage buildings maintenance in Iraq
- Design and optimization of two-stage controller for three-phase multi-converter/multi-machine electric vehicle
- Evaluation of microstructure and mechanical properties of Al1050/Al2O3/Gr composite processed by forming operation ECAP
- Calculations of mass stopping power and range of protons in organic compounds (CH3OH, CH2O, and CO2) at energy range of 0.01–1,000 MeV
- Investigation of in vitro behavior of composite coating hydroxyapatite-nano silver on 316L stainless steel substrate by electrophoretic technic for biomedical tools
- A review: Enhancing tribological properties of journal bearings composite materials
- Improvements in the randomness and security of digital currency using the photon sponge hash function through Maiorana–McFarland S-box replacement
- Design a new scheme for image security using a deep learning technique of hierarchical parameters
- Special Issue: ICES 2023
- Comparative geotechnical analysis for ultimate bearing capacity of precast concrete piles using cone resistance measurements
- Visualizing sustainable rainwater harvesting: A case study of Karbala Province
- Geogrid reinforcement for improving bearing capacity and stability of square foundations
- Evaluation of the effluent concentrations of Karbala wastewater treatment plant using reliability analysis
- Adsorbent made with inexpensive, local resources
- Effect of drain pipes on seepage and slope stability through a zoned earth dam
- Sediment accumulation in an 8 inch sewer pipe for a sample of various particles obtained from the streets of Karbala city, Iraq
- Special Issue: IETAS 2024 - Part I
- Analyzing the impact of transfer learning on explanation accuracy in deep learning-based ECG recognition systems
- Effect of scale factor on the dynamic response of frame foundations
- Improving multi-object detection and tracking with deep learning, DeepSORT, and frame cancellation techniques
- The impact of using prestressed CFRP bars on the development of flexural strength
- Assessment of surface hardness and impact strength of denture base resins reinforced with silver–titanium dioxide and silver–zirconium dioxide nanoparticles: In vitro study
- A data augmentation approach to enhance breast cancer detection using generative adversarial and artificial neural networks
- Modification of the 5D Lorenz chaotic map with fuzzy numbers for video encryption in cloud computing
- Special Issue: 51st KKBN - Part I
- Evaluation of static bending caused damage of glass-fiber composite structure using terahertz inspection

