Abstract
As surveillance cameras have proliferated in usage, their widespread deployment has raised privacy concerns. We introduce an inventive strategy to safeguard privacy in surveillance videos to address these concerns. This article designs a secure system for detecting and encrypting regions of interest (ROIs) that depict multiple individuals within video footage. The suggested system is composed of three phases, with the initial phase incorporating an object detection model to efficiently detect individuals in video frames with the You Only Look Once version 7 architecture. The second stage encrypts ROIs with our unique algorithm, which represents a novel technique derived from combining triple DNA with the modification of the 5D Lorenz chaotic map using fuzzy triangular numbers, which are utilized in key generation. The reverse of this process is a decryption that obtains the original video. The third stage combines all encrypted ROIs from the reconstructed video frames to be securely stored as encrypted video in the cloud. Evaluation results show that the utmost value of the unified averaged changed intensity and the number of changing pixel rate stand at 33.8000 and 99.8934%, respectively, with encryption and decryption speeds up to 7.06 and 6.72 s, respectively.
1 Introduction
In recent years, there has been a surge of interest in object encryption, largely spurred by an escalating transfer of videos over networks. Ensuring the security of these videos is imperative to thwart unauthorized access and to safeguard sensitive information, which has prompted significant research efforts in academic and practical domains. Video surveillance systems that are frequently deployed in high-security environments have been pivotal in driving the evolution of object detection methods for encryption [1].
Surveillance video encryption offers a promising approach to enhancing the privacy and security of video recordings. Two strategies exist for applying encryption techniques to surveillance videos: encrypting the complete video and selectively encrypting solely the regions of interest (ROIs) containing confidential data. Encrypting the entire video [2], as previously discussed, may not always be warranted, especially in the case of public areas where the data is not considered sensitive. Comprehensive encryption can also require substantial computational resources and time. Consequently, a more efficient approach involves encrypting only the ROIs, while leaving non-ROI regions unencrypted [3] to optimize the production of protected surveillance videos.
DNA cryptography suggests an interesting potential for enhancing object encryption in surveillance videos transmitted over networks. With its computational power and the intricate dynamics rooted in chaos theory, the approach can be a valuable resource in the field of cryptography. Specifically, DNA cryptography can produce pseudo-random sequences to serve as encryption keys. This encryption process encompasses the two key steps of scrambling and diffusion. In scrambling, pixel positions across video frames are adjusted based on the encryption key, while diffusion alters pixel values. These two operations work synergistically to generate a novel encoded structure that differs from the original video [4].
In this article, we introduce a novel video encryption approach that combines triple DNA with the modification of the 5D Lorenz chaotic map using fuzzy triangular numbers. The incorporation elevates the level of security and improves video encryption effectiveness by harnessing high diffusion achieved through a scrambling operation and the incorporation of DNA coding within the chaotic system. The noteworthy outcomes of this research include:
Presents a fresh surveillance video. An encryption and decryption scheme is proposed, aiming for reduced time and memory requirements alongside heightened efficiency. The design emphasizes enhanced security, ensuring reduced correlation coefficients among neighboring pixels in the encrypted video.
Proposes a novel method to perform video encryption that combines a triple DNA and anew 5D Lorenzo chaotic system. These methods are compared with recent approaches as baselines.
Generates an exceptionally sensitive key for encrypting and decrypting videos through the proposed 5D Lorenzo map system with fuzzy number, which are utilized in keys generation. This system presents additional benefits compared to a basic chaotic system, including a broader parameter space, increased randomization, and a multitude of chaotic sequences.
The keys generated by the modified 5D Lorenzo map pass all 15 tests in the National Institute of Standards and Technology (NIST) statistical test suite. These produced keys are then utilized for video encryption. The resulting encrypted video undergoes a security analysis using methods such as histogram analysis, correlation, and information entropy.
The remainder of the article consists of sections covering the literature review, theoretical background, research method, experiment process, and results and discussion, followed by our summary and conclusions.
2 Literature review
In their 2018 work, Zhang et al. proposed using DNA sequences for privacy protection in surveillance videos, specifically focusing on safeguarding RoI within the videos. Instead of encrypting the entire video, they advocate for only the areas containing sensitive information. This is a more efficient approach to reduce computational costs and meet real-time video transmission requirements. While conventional cryptographic technologies like AES and RSA are commonly used for privacy protection, they may not be well-suited to the specific needs of surveillance videos. Hence, researchers have explored alternative methods, including the unique approach of utilizing DNA sequences for video encryption, which has shown effectiveness beyond traditional cryptographic technologies in this context [5].
In 2020, Shao proposed an image encryption algorithm for torsional components of generators based on a complex chaotic model. This method involves extracting the RGB torsional vibration component of the image for discrete cosine transform transformation; it is then rotated and fused to complete the initial encryption of the image information. In order to further enhance the security of image information, the image information complex, chaotic encryption model is constructed according to the coding result, so as to eliminate the strong correlation between the adjacent pixels. Particle swarm optimization is used to co-ordinate and optimize the parameters of the compound chaotic encryption model to improve the encryption performance of the model. Experimental results show that the pixel has low correlation, high security, and strong ability to resist attacks after encrypting with this algorithm [6].
In a study published in 2020, Darwich et al. suggested using cloud storage for storing videos intended for specific audiences. Cloud computing, known for its processing power, extensive storage capacity, and fast computation speed, has gained popularity among various entities. However, it also raises security concerns, including confidentiality, data integrity, and availability. Ensuring authentication and authorization for data access is crucial, given that cloud storage comprises distributed supercomputers worldwide [7].
3 Theoretical background
3.1 You Only Look Once version 7 (YOLOv7) algorithm
The latest advancement in architecture for object detection is YOLOv7, which is within the You Only Look Once series. Anticipated to establish itself as the industry norm for object detection [8,9]. YOLOv7 architecture consists of three main components, as shown in Figure 1.
Backbone: A convolutional neural network generates image features.
Neck: An assemblage of neural network layers that blends and integrates features before forwarding them to the subsequent stage for prediction.
Head: Utilizes features from the bottleneck to generate prediction outputs.
![Figure 1
YOLOv7 architecture [10].](/document/doi/10.1515/eng-2024-0051/asset/graphic/j_eng-2024-0051_fig_001.jpg)
YOLOv7 architecture [10].
3.2 Fuzzy numbers
In this section, we provide some introductory information on fuzzy numbers, although there are slight variations in the definitions of fuzzy numbers. In this work, we define a fuzzy number as a function f: X → [0, 1], where X is a set within the real numbers (ℝ), with the following characteristics:
It is a regular fuzzy set, implying the existence of at least one x ∈ X such that f (x) = 1.
The function f is piecewise continuous.
It is worth noting that in certain studies, fuzzy numbers are defined with a unique x₀, such that f (x₀) = 1. However, the fuzzy numbers under consideration in this context are defined as f: [0, 1] → [0, 1] and take on a triangular form:
In this context, z denotes the peak of the triangular fuzzy number. Figure 2 provides examples for different values of z [11,12].
![Figure 2
Illustrations of fuzzy trigonometric numbers for z = 0, 0.3, 0.5, 1 [11].](/document/doi/10.1515/eng-2024-0051/asset/graphic/j_eng-2024-0051_fig_002.jpg)
Illustrations of fuzzy trigonometric numbers for z = 0, 0.3, 0.5, 1 [11].
3.3 Lorenz chaotic mapping
Chaotic maps play a significant role in the study of dynamic nonlinear systems. The Lorenz mapping is a typical example of chaotic mapping in chaotic systems, and it is described by the system’s dynamic equations:
Incorporated into the mapping are system parameters, commonly assigned values of 10, 28, and 8/3. Should these values remain unchanged, the system undergoes collapse once the criterion of 24.74 is satisfied. The Lorenz system produces chaotic sequences characterized by a more intricate system structure compared to low-dimensional ones. This complexity allows for the generation of chaotic sequences involving either a single variable or multiple variables, showcasing a high degree of flexibility in sequence design [13].
3.4 DNA encoding
Understanding DNA sequences is indispensable in fundamental biological research and practical applications across various fields such as diagnostic, forensic, biotechnological, and biological systematics. A DNA sequence consists of four different nucleic acids: thymine (T), adenine (A), guanine (G), and cytosine (C). These nucleic acids adhere to specific base pairing rules, where purine adenine (A) consistently pairs with pyrimidine thymine (T), and pyrimidine cytosine (C) consistently pairs with purine guanine (G) [14]. This complementary base pairing is illustrated in the basic structure of DNA depicted in Figure 3 [15].
![Figure 3
A simple DNA structure [13].](/document/doi/10.1515/eng-2024-0051/asset/graphic/j_eng-2024-0051_fig_003.jpg)
A simple DNA structure [13].
The connections between these bases are referred to as the Watson–Crick base pairing rules, named in honor of the scientists who uncovered their structural basis. Analogous to the complementary nature of 0 and 1 in the binary system, 01 and 10 can also be observed to be complementary, just as 00 and 11 are. Table 1 presents the rules for decoding and coding mapping in the specific context of a DNA series employed within this research. Conversely, Table 2 illustrates the XOR procedure applied to DNA arrangements to conform to the Watson–Crick base pairing rules [15].
Rules for mapping the encoding and decoding of DNA
| Rule 1 | Rule 2 | Rule 3 | Rule 4 | Rule 5 | Rule 6 | Rule 7 | Rule 8 | |
|---|---|---|---|---|---|---|---|---|
| A | 00 | 00 | 11 | 11 | 10 | 01 | 10 | 01 |
| T | 11 | 11 | 00 | 00 | 01 | 10 | 01 | 10 |
| C | 10 | 01 | 10 | 01 | 00 | 00 | 11 | 11 |
| G | 01 | 10 | 01 | 10 | 11 | 11 | 00 | 00 |
XOR operations for the DNA sequence pairing rules
| XOR | A | T | C | G |
| A | A | T | C | G |
| T | T | A | G | C |
| C | C | G | A | T |
| G | G | C | T | A |
4 Research method
In this section, the provided approach is outlined, elucidating each sequential step. The initial stage employs YOLOv7 to process the video surveillance, identifying the ROIs within every frame. After pinpointing each ROI, they undergo encryption to secure the sensitive data they encapsulate using a new 5D Lorenzo chaotic system. In the next stage, the coded ROIs are seamlessly reintegrated back to their original positions within the frames of the video. Finally, the encrypted video is uploaded to the cloud for storage and subsequent access. A visual overview of the entire process is illustrated in Figure 4.
![Figure 4
The general framework of the proposed method to detect and encrypt ROIs [16].](/document/doi/10.1515/eng-2024-0051/asset/graphic/j_eng-2024-0051_fig_004.jpg)
The general framework of the proposed method to detect and encrypt ROIs [16].
4.1 Object detection process
The proposed approach presents an effective strategy to minimize the processing time necessary for object detection in videos by utilizing YOLOv7 and incorporating the “remove duplicate frames” method. This method leverages zero difference approaches (ZDAs) to detect and remove frames that contain identical content, thereby eliminating those frames with a difference of zero. After implementing ZDA, the proposed method continues with the YOLOv7 algorithm, resulting in object detection denoted by bounding boxes around the identified objects.
4.2 Encryption process
The suggested video encryption scheme is outlined in a step-by-step manner in Figure 5.
![Figure 5
A workflow visualization for the general steps of the encryption process [16].](/document/doi/10.1515/eng-2024-0051/asset/graphic/j_eng-2024-0051_fig_005.jpg)
A workflow visualization for the general steps of the encryption process [16].
4.2.1 ROIs scrambling algorithm
To enhance the security of the encryption technique, image scrambling operations are employed to disrupt the correlation between adjacent pixels. Specifically, the scrambling process is applied to an ROI denoted as I, with dimensions (M × N). In this context, M denotes the height, and N denotes the width of the ROI. Algorithm 1 outlines the procedure for creating a scrambled ROI, denoted as I′, by utilizing a chaotic key (k) that serves as an arbitrary matrix.
Algorithm 1: The Scrambling Pixels Algorithm
Input: I (i, j), ROI of video with dimension (M × N), scrambling key (k).
Output: I′ (i, j), the scrambled ROI.
Begin:
Step 1: Generate chaotic sequence K with a random function. The sequence length is K0 = M × N.
Step 2: Transform the digital ROI matrix I, with dimensions M × N, into a one-dimensional sequence P with a length of M × N. P = (p(1), p(2), …, p(MN)).
Step 3: Organize the chaotic sequence K in ascending order to derive the index sequence B. Consequently, the size of B, along with its updated index sequences, becomes 1 × MN.
Step 4: Shuffle the array P based on the index sequence B to generate a new array Q, where Q(i) = P(B(i)), for i = 1, 2, 3, …, M × N.
Step 5: Transform the one-dimensional array Q into an ROI matrix I′ with dimensions M × N.
Step 6: Repeat steps 2 through 5 until all ROIs across all video frames are scrambled.
End.
4.2.2 ROIs video triple DNA encoding
The subsequent phase involves the application of 3DNA coding to the permutation outcome obtained in the preceding step. The RGB-scrambled ROI is divided into its three constituent parts: R (red), G (green), and B (blue). Each component is individually converted into binary numbers, where each pair of bits is mapped to any of the DNA symbols: A, C, G, or T, following the randomly selected rules listed in Table 1. This transformation adheres to rules (1, 5, 7) outlined in Table 1, yielding the three encoding elements of Rc, Gc, and Bc. Following, the second round of Rc, Gc, and Bc components is encoded based on rules (2, 3, 6). This step produces three additional encoding components: Rcc, Gcc, and Bcc.
In another subsequent phase, a third round of Rcc, Gcc, and Bcc components are encoded based on rules (3, 4, 8). This step generates three more encoding components of Rccc, Gccc, and Bccc. Finally, these three encoding components are combined to create a unified ROI representing the encoded ROI.
4.2.3 Generating keys through a new 5D Lorenzo chaotic system
A novel 5D chaotic system with fuzzy numbers incorporating differential dynamic equations has been introduced to explore chaotic properties and produce a series of numerical output sequences. Figure 6 displays the chaotic attractors in each plane of the 5D Lorenz chaotic map.
In the chaos parameter set, b, r, s, u, and dt are involved, while x, y, z, k, and p constitute the starting conditions for the chaotic map. The recently introduced 5D chaotic system was implemented and evaluated, and the Lyapunov exponents for both the initial conditions and parameters were computed. At maximum Lyapunov values (x = 2.1, y = 0.5, z = 1.1, k = 1.1, and p = 0.1) and system parameter (b = 0.01, r = 0.5, s = 0.95, u = 1.1, and dt = 0.01), ƒz denotes the fuzzy triangular function described above, centered at z. The proposed 5D chaotic system demonstrates Lyapunov values indicative of super chaos, featuring five values that are positive. The chaos keys generated (K1, K2, …, K5) from all proposed systems successfully undergo statistical tests conducted by the NIST before being effectively employed in video encryption. Figure 6 displays the chaotic attractors in each plane of the 5D Lorenz chaotic map.
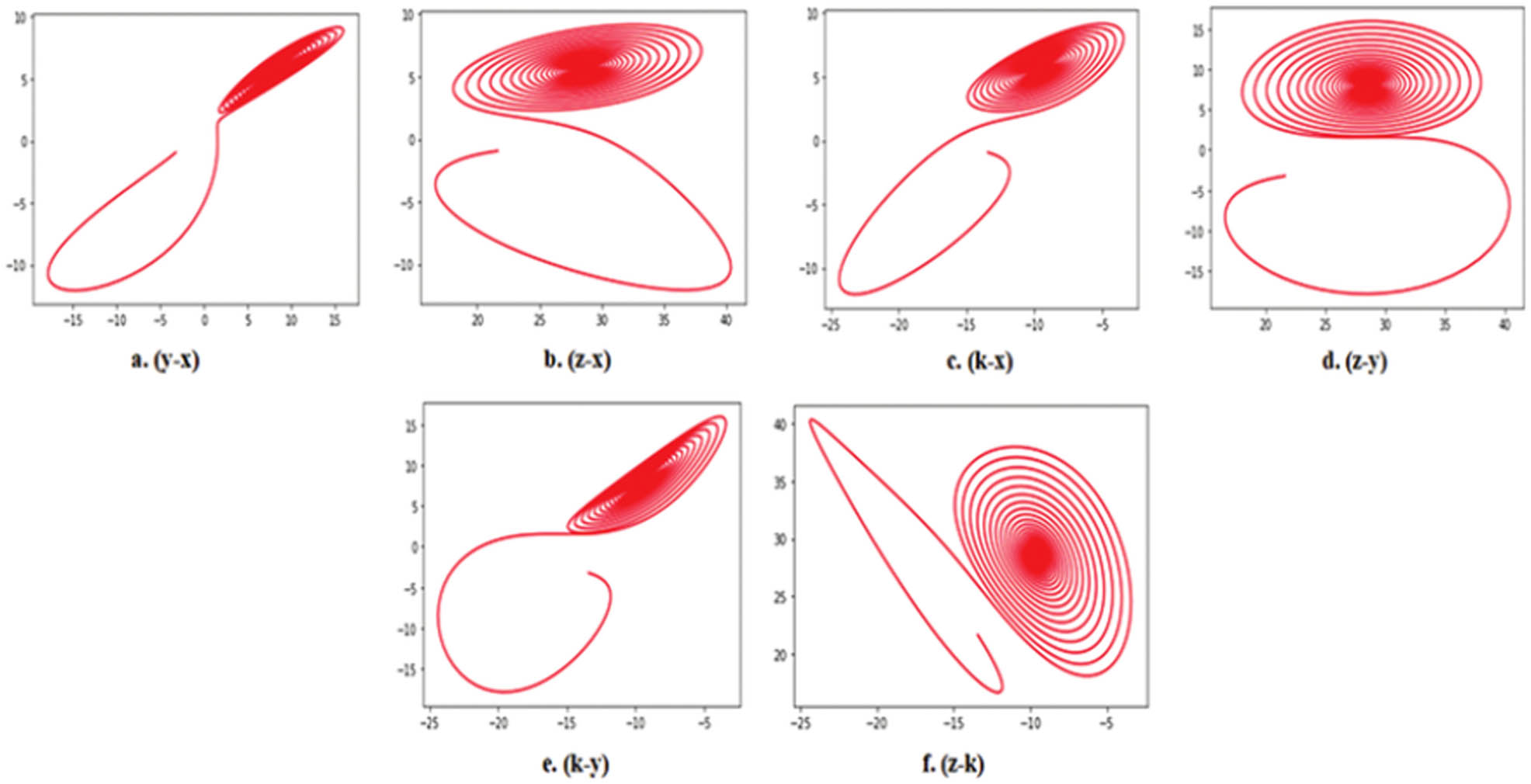
Chaotic attractors found in every plane of the 5D Lorenz chaotic map onto different spaces (a) y-x , (b) z-x, (c) k-x, (d) z-y, (e) k-y, and (f) z-k.
4.2.4 ROIs video encryption
The set of five chaotic sequences generated by equations (5)–(9) within the proposed method. These sequences are then converted into five vectors, identified as key1, key2, key3, key4, and key5. The creation of these vectors depends on the 5D chaotic Lorenz map, characterized by specific parameters and starting conditions. Each vector has a dimensionality corresponding to the original image (h × w). During this phase, the encoded ROI that is split into even and odd arrays is organized into the R, G, and B components. The pixels in the even array of the ROI with key1, key3, and key5 undergo the DNA-XOR procedure, as outlined in Table 2, to obtain the even ROI encryption. Conversely, the pixels in the odd array of the ROI with key2, key5, and key4 undergo the DNA-XOR operation to obtain the odd ROI encryption. Combining these two 2D arrays from the XOR operations yields the encrypted ROI.
In summary, this process ensures ROI encryption by utilizing chaotic sequences and performing XOR operations, as shown in Equations (10)–(15).
4.2.5 Decryption process
For decryption, the original ROIs from the encrypted surveillance video are recovered by reversing the encryption steps. This entails identifying the positions of the encrypted ROIs and the keys employed in the encryption process, as depicted in Figure 7. In other words, the decryption stage retraces the stages of the encryption phase by following the opposite order. Figure 8 illustrates a visual representation of the suggested object decryption method.
![Figure 7
Overview of the basic stages involved in the decryption procedure [16].](/document/doi/10.1515/eng-2024-0051/asset/graphic/j_eng-2024-0051_fig_007.jpg)
Overview of the basic stages involved in the decryption procedure [16].
![Figure 8
A workflow visualization for the general steps of the decryption process [16].](/document/doi/10.1515/eng-2024-0051/asset/graphic/j_eng-2024-0051_fig_008.jpg)
A workflow visualization for the general steps of the decryption process [16].
4.3 Uploading encrypted video to the cloud
The cloud upload of videos is important for organizations today because of its efficiency and cost-effectiveness. For uploading videos to the cloud, an organization must establish an end-to-end system that ensures the safety and security of videos [17,18]. The software for such a system should be easy to use and maintain as it is expected to be used by multiple individuals who may not be tech-savvy and require user-friendly interfaces. This proposed work utilizes the OneDrive cloud as the interface tool for managing encrypted videos, as illustrated in Figure 9.
Screenshot of uploaded encrypted videos in the OneDrive cloud.
5 Experimental process
This section provides details about the experimental setup for evaluating the performance of the proposed image encryption algorithms. The experiments were performed using Python 3.10 on a computer with an 8th Gen Core i7 CPU operating at 2.20 GHz and 8 GB of memory. The surveillance videos in Figure 10 are used as tested videos from [16], that includes the original, objects detected, encrypted, and decrypted versions. The findings outlined demonstrate that all encrypted videos appear utterly distorted, suggesting the efficiency of the proposed method.
![Figure 10
Sample output of the experimental process to test encrypting and decrypting ROIs in videos with the proposed method [16].](/document/doi/10.1515/eng-2024-0051/asset/graphic/j_eng-2024-0051_fig_010.jpg)
Sample output of the experimental process to test encrypting and decrypting ROIs in videos with the proposed method [16].
6 Results and discussion
In this section, we evaluate the efficiency of the proposed encryption algorithm with a variety of tests, including analyzing the key space entropy and conducting an analysis of differential attacks, histogram examination, evaluation of video quality, correlation analysis, and time assessment. The tests are further explained in the following.
6.1 Analysis of key space and sensitivity
The key space metric is essential for evaluating encryption systems as it measures the system’s susceptibility to minimal alterations in the secret key used for encryption and decryption. As depicted in Figure 11, the proposed approach exhibits a high level of sensitivity, making it highly responsive to even the most minor changes in the secret key [19].
![Figure 11
Illustration of how the encryption process is affected by variations in the secret key parameter. (a) Original of house frame. (b) Encrypted of house frame. (c) Decrypted of house frame by r = 1.19. (d) Decrypted of house frame by r = 1.12000001 [16].](/document/doi/10.1515/eng-2024-0051/asset/graphic/j_eng-2024-0051_fig_011.jpg)
Illustration of how the encryption process is affected by variations in the secret key parameter. (a) Original of house frame. (b) Encrypted of house frame. (c) Decrypted of house frame by r = 1.19. (d) Decrypted of house frame by r = 1.12000001 [16].
6.2 Entropy
In the context of this study, entropy quantifies the amount of information contained within a dataset and can show the distribution of grayscale pixel values in the ROIs of the video frames. Entropy is a constant positive value, and a higher value indicates that a variable contains a greater amount of information such that
where p(s i ) denotes the probability of grayscale s i , and n represents the total count of grayscale pixels. In this experiment, a house test video is utilized, and Table 3 lists the calculated entropy for the initial and encrypted ROIs representing the individuals on the left, middle, and right appearing in frame number 100 of the test video. These results imply that the information entropy of the encrypted ROIs is near 8, demonstrating the system’s ability to withstand attacks [20].
Calculated entropy of the ROIs in the initial and corresponding encrypted video frames
| Video object | Left ROI | Middle ROI | Right ROI |
|---|---|---|---|
| Original ROI | 7.8600 | 7.7322 | 7.6532 |
| Encrypted ROI | 7.9967 | 7.9948 | 7.9902 |
| Decrypted ROI | 7.8525 | 7.7271 | 7.6532 |
6.3 Differential attack analysis
The unified averaged changed intensity (UACI) and the number of changing pixel rate (NPCR) are metrics capable of identifying factors associated with differential attacks and highlighting crucial image information. The equations for each metric are defined in the following:
where H and W denote the columns and rows for ROI, in each case, and D is approximated by
where C 1(i, j) and C 2(i, j) depict pixel values within the ciphered ROIs, and L indicates the quantity of gray levels. Then, the UACI is expressed as
Table 4 lists the calculated metric values after a series of ROIs for the same left, middle, and right elements in video frame 100, which were tested using the suggested system [21]. The results of NPCR and UCAI are relatively good, so the reconstructed ROIs seem plausibly similar to the original pixel distributions compared to other methods.
6.4 Histogram analysis
For an encryption algorithm to be considered effective, the histograms of the encrypted video frames are anticipated to exhibit uniformity. Figure 12 displays the pixel value histograms per color channel for both the original and encrypted ROIs. The results indicate that the suggested algorithm has the potential to thwart statistical attacks [25].
![Figure 12
Histogram comparison analysis for the (a) original and encrypted left ROI of the test video frame, (b) original and encrypted middle ROI, and (c) original and encrypted right ROI [16].](/document/doi/10.1515/eng-2024-0051/asset/graphic/j_eng-2024-0051_fig_012.jpg)
Histogram comparison analysis for the (a) original and encrypted left ROI of the test video frame, (b) original and encrypted middle ROI, and (c) original and encrypted right ROI [16].
6.5 Video quality
A standard requirement for the ROIs of video frame encryption methods is that the encrypted ROIs deviate significantly from the initial ROIs. The two criteria of the PSNR and MSE can compare the original and encrypted ROIs generated by the proposed algorithm. These metrics are defined as [26]
Values for our test frame are calculated in Table 5, with the results for MSE and PSNR being relatively good.
6.6 Correlation coefficient
The correlation coefficient gauges the linear relationship in terms of range and trend between two random variables. The correlation coefficient approaches 1 when two variables, x and y, are closely linked, while a value near 0 indicates that these variables are considered unrelated. Equation (22) can be employed for calculating the correlation coefficient as follows:
These coefficients are calculated for our test video frames in Table 6, which indicates a range for the original ROIs between 0.9689 and 0.9313 and the range for the encrypted ROIs between −0.0184 and −0.0296. The correlation coefficients between the initial and encrypted ROIs are different, as illustrated in Figure 13, which suggests a robust algorithm [27].
Correlation coefficients calculated on the test video frame between the original and corresponding encrypted ROIs
| Video name | Left ROI | Middle ROI | Right ROI |
|---|---|---|---|
| Original ROIs | 0.9313 | 0.9689 | 0.9513 |
| Encrypted ROIs | −0.0184 | −0.0296 | −0.0261 |
![Figure 13
Correlation analysis of the ROIs in both the original frames and their corresponding encrypted frames in the test video indicates a notable distinction in the pixel value distributions [16].](/document/doi/10.1515/eng-2024-0051/asset/graphic/j_eng-2024-0051_fig_013.jpg)
Correlation analysis of the ROIs in both the original frames and their corresponding encrypted frames in the test video indicates a notable distinction in the pixel value distributions [16].
6.7 Time analysis
The assessment criterion involves the duration it takes for the cryptographic strategy to execute the encryption and decryption algorithms for any video. Our experiment shows a slight difference between encryption and decryption times. As a result, encrypting the frames with our proposed approach takes longer than decrypting them, as compared in Table 7 with existing ROI encryption methods. However, our method requires a shorter overall time for execution in comparison to existing approaches.
Average encryption and decryption times
| Video name | Max ROIs per frame | Time of encryption (s) | Time of decryption (s) |
|---|---|---|---|
| House | 3 | 10.16 | 9.15 |
| Airport | 4 | 9.71 | 9.11 |
| Company | 5 | 7.06 | 6.72 |
| Street | 14 | 11.95 | 10.99 |
| Reception | 2 | 10.2 | 10.1 |
| Office | 5 | 8.76 | 8.02 |
| [28] | 12 | 34.28 | — |
| [28] | 3 | 42.88 | — |
| [28] | 1 | 50.61 | — |
| [29] | Color (512 × 512) | 4.60.58 | — |
| [29] | Color (256 × 256) | 3.61.75 | — |
| [30] | Color (512 × 512) | 14.81.19 | — |
6.8 NIST analyses
The NIST outlined guidelines for ensuring data security that includes fifteen tests designed to assess the randomness and strength of encryption algorithms. Table 8 provides benchmarked performance data for our proposed system with these tests, indicating a successful evaluation for each. We compare our results with those from random number generators proposed in [31], as shown in Table 9.
NIST assessment test results of dynamic random key1,… key5
| ID | NIST test | P_value of key1 | P_value of key2 | P_value of key3 | P_value of key4 | P_value of key5 | P_value >0.01 |
|---|---|---|---|---|---|---|---|
| 1 | Frequency | 0.8596 | 0.8734 | 0.4398 | 0.8495 | 0.5489 | Pass |
| 2 | Frequency within a block | 0.8596 | 0.7834 | 0.7645 | 0.2384 | 0.5478 | Pass |
| 3 | Runs | 0.3781 | 0.7638 | 0.7643 | 0.6378 | 0.4578 | Pass |
| 4 | Longest run of ones | 0.8354 | 0.8384 | 0.7839 | 0.7864 | 0.5784 | Pass |
| 5 | Rank | 0.4765 | 0.6384 | 0.1274 | 0.489 | 0.5478 | Pass |
| 6 | Spectral | 0.3303 | 0.3789 | 0.8634 | 0.6749 | 0.5478 | Pass |
| 7 | Non-overlapping T.M. | 0.9999 | 0.4873 | 0.3672 | 0.9749 | 0.9840 | Pass |
| 8 | Overlapping T.M. | 0.9432 | 0.2174 | 0.7523 | 0.6738 | 0.5494 | Pass |
| 9 | Maurer’s universal | 0.6548 | 0.4837 | 0.9734 | 0.5498 | 0.4873 | Pass |
| 10 | Linear complexity | 0.5678 | 0.9483 | 0.3456 | 0.8495 | 0.1298 | Pass |
| 11 | Serial | 0.4989 | 0.5647 | 0.8673 | 0.8493 | 0.8459 | Pass |
| 12 | Approximate entropy | 1.0000 | 0.7483 | 0.2371 | 0.9293 | 0.5489 | Pass |
| 13 | Cumulative sums | 0.9492 | 0.9743 | 0.8943 | 0.1278 | 0.4563 | Pass |
| 14 | Random excursions | 0.4584 | 0.8743 | 0.7485 | 0.6478 | 0.9743 | Pass |
| 15 | Random excursions variant | 0.2327 | 0.7489 | 0.8438 | 0.8493 | 0.8493 | Pass |
NIST assessment test results of static random key in [31]
| ID | NIST test | P_value | P_value >0.01 |
|---|---|---|---|
| 1 | Frequency | 0.3291 | Pass |
| 2 | Frequency within a block | 0.1792 | Pass |
| 3 | Runs | 0.0887 | Pass |
| 4 | Longest run of ones | 0.0620 | Pass |
| 5 | Rank | 0.0283 | Pass |
| 6 | Spectral | 0.0000 | Fail |
| 7 | Non-overlapping T.M | 0.9986 | Pass |
| 8 | Overlapping T.M. | 0.7500 | Pass |
| 9 | Universal | 0.8847 | Pass |
| 10 | Linear complexity | 0.1760 | Pass |
| 11 | Serial | 0.3040 | Pass |
| 12 | Approximate entropy | 0.3114 | Pass |
| 13 | Cumulative sums | 0.2869 | Pass |
| 14 | Random excursions | 0.1276 | Pass |
| 15 | Random excursions variant | 0.2624 | Pass |
6.9 Energy consumption analysis
The selective encryption algorithm is faster than the full encryption algorithm since it encrypts the partial data instead of the total video clip [32]. Contrary to popular belief, our experiments show that the energy overhead of selective video encryption is insignificant compared to the energy consumed for full video encryption. In terms of energy, the selective algorithm consumes about 40% of relative energy. energy analysis on the video encryption algorithms as summarized in Table 10.
7 Conclusions
In this work, the 5D Lorenz map underwent modification by incorporating triangular fuzzy numbers, resulting in a newly modified 5D Lorenz map that demonstrates a broad spectrum of chaos-related phenomena across different parameter settings. It was illustrated that the altered 5D Lorenz map achieves an elevated Lyapunov exponent in comparison to the original Lorenz map. The 5D Lorenzo map is employed in the generation of keys, which are then used to encrypt ROIs symbolizing individuals. The identification of these (ROIs) through YOLOv7, indicating effective object detection, streamlines the process of identifying pertinent areas within surveillance videos. After this, triple DNA encoding is applied, resulting in the encoded ROI. This triple-encoded ROI is further fortified through encryption using a chaotic 5D Lorenzo map to enhance video security during transmission. The decryption process reverses the encryption operation. Finally, the encrypted video is uploaded to the cloud for persistent storage. A simulation experiment is conducted to assess the effectiveness of the proposed approach with an evaluation of various metrics, like entropy and the analysis of differential attacks, analysis of histograms, assessment of sensitivity, exploration of key space, and evaluation of video quality. The experimental findings suggest the algorithm’s robust security performance and ability to effectively withstand various threats.
-
Funding information: The authors state no funding involved.
-
Author contributions: All authors have accepted responsibility for the entire content of this manuscript and consented to its submission to the journal, reviewed all the results and approved the final version of the manuscript. MAAK conceived of the presented idea. AHA developed the theory, performed the computations, and verified the analytical methods. ATA helped supervise the project. All authors discussed the results and contributed to the final manuscript.
-
Conflicts of interest: Authors state no conflict of interest.
-
Data availability statement: Most datasets generated and analyzed in this study are comprised in this submitted manuscript. The other datasets are available on reasonable request from the corresponding author with the attached information.
References
[1] Zuxuan W, Ting Y, Yanwei F, Yu-Gang J. Deep learning for video classification and captioning. In Frontiers of multimedia research. New York; Vol. 2. 2017 Feb. p. 3–29.10.1145/3122865.3122867Suche in Google Scholar
[2] Xiaodong L, Haoyang Y, Hongyu Z, Xin J, Hongbo S, Jing L. Video encryption based on hyperchaotic system. Multimed Tools Appl. 2022 Jun;79:23995–4011.10.1007/s11042-020-09200-1Suche in Google Scholar
[3] Shifa A, Asghar MN, Fleury M, Kanwal N, Ansari MS, Lee B, et al. MuLViS: Multi-level encryption based security system for surveillance videos. IEEE Access. 2020;8:177131–55.10.1109/ACCESS.2020.3024926Suche in Google Scholar
[4] Alem F, Yu C, Sencun Z. Lightweight frame scrambling mechanisms for end‐to‐end privacy in edge smart surveillance. IET Smart Cities. 2022;4(1):17–35.10.1049/smc2.12019Suche in Google Scholar
[5] Zhang X, Seo SH, Wang C. A lightweight encryption method for privacy protection in surveillance videos. IEEE Access. 2018 Apr;6:18074–87.10.1109/ACCESS.2018.2820724Suche in Google Scholar
[6] Shao Y. Image encryption algorithm for torsional components of generator based on compound chaotic model. Therm Sci. 2020;24(3 Part A):1473–80.10.2298/TSCI190717078SSuche in Google Scholar
[7] Darwich M, Ismail Y, Darwich T, Bayoumi M. Cost-efficient storage for on-demand video streaming on cloud. In 2020 IEEE 6th World Forum on Internet of Things (WF-IoT). IEEE; 2020 Jun. p. 1–4.10.1109/WF-IoT48130.2020.9221374Suche in Google Scholar
[8] Jiang K, Xie T, Yan R, Wen X, Li D, Jiang H, et al. An attention mechanism-improved YOLOv7 object detection algorithm for hemp duck count estimation. Agriculture. 2020;12(10):1–18.10.3390/agriculture12101659Suche in Google Scholar
[9] Muhammad H, Hussain A, Muhammad M, Richard H, Tariq A. Domain feature mapping with YOLOv7 for automated edge-based pallet racking inspections. Sensors. 2022;22(18):1–13.10.3390/s22186927Suche in Google Scholar PubMed PubMed Central
[10] Chien YW, Alexey B, Hong YM. YOLOv7: Trainable bag-of-freebies sets new state-of-the-art for real-time object detectors. arXiv Prepr. arXiv2207.02696. 2022 Jul;1–15.Suche in Google Scholar
[11] Lazaros M, Christos V, Sajad J, Jesus M, Jacques K, Karthike YR, et al. Modification of the Logistic Map Using Fuzzy Numbers with Application to Pseudorandom Number Generation and Image Encryption. Entropy. 2020 April;1:20.Suche in Google Scholar
[12] Lefta FA, Hamdan AN. Integrated fuzzy logic and multicriteria decision model methods for selecting suitable sites for wastewater treatment plant: A case study in the center of Basrah, Iraq. Open Eng. 2024;14:1–21.10.1515/eng-2022-0439Suche in Google Scholar
[13] Rawia AM, Maisa’a AA, Ashwak A. A novel lightweight image encryption scheme. Comput Mater Continua. 2023;75:1–17.10.32604/cmc.2023.036861Suche in Google Scholar
[14] He JH. Mysterious pi and a possible link to DNA sequencing. Int J Nonlinear Sci Numer Simul. 2004 Sep;5(3):263–74.10.1515/IJNSNS.2004.5.3.263Suche in Google Scholar
[15] Wei W, Dongming P, Honggang W, Hamid S, Hsiao H. Energy -constrained quality optimization for secure image transmission in wireless sensor networks. Adv Multimed. 2007;2027:1–10.Suche in Google Scholar
[16] https://www.shutterstock.com/royalty-free/people-videos.Suche in Google Scholar
[17] Emre E, Santiago O. Multimedia storage in the cloud using Amazon web services: implications for online education. arXiv Prepr. arXiv1608.07085. 2016;1–16.Suche in Google Scholar
[18] Sergei V, Yuriy A, Daniil T. Templet Web: the use of volunteer computing approach in PaaS-style cloud. Open Eng. 2018;8:1–7.10.1515/eng-2018-0007Suche in Google Scholar
[19] Xiaoqiang Z, Zhiwei L, Xiaochang Y. Design of artificial intelligence image encryption algorithm based on hyperchaos. Ain Shams Eng J. 2023;14(3):1–8.10.1016/j.asej.2022.101891Suche in Google Scholar
[20] Huda G, Maisa’a A. Comparison of three proposal methods in steganography encryption secret message using PVD and MapReduce. IRAQI J Comput Commun Control Syst Eng. 2021;21(2):1–17.Suche in Google Scholar
[21] Yousef A, Arslan M, Jawa A. A lightweight image encryption algorithm based on chaotic map and random substitution. Entropy. 2022;24(10):1–25.10.3390/e24101344Suche in Google Scholar PubMed PubMed Central
[22] Hui L, Jianwen Z, Linquan H, Yifan L. A lightweight image encryption algorithm based on message passing and chaotic map. Secur Commun Netw. 2020;2020:1–12.10.1155/2020/7151836Suche in Google Scholar
[23] Azhaar K, Alaa K. A new image encryption algorithm based on multi chaotic system. Iraqi J Sci. 2022;63(1):324–37.10.24996/ijs.2022.63.1.31Suche in Google Scholar
[24] Manish G, Kamlesh K, Piyush K. Session key based fast, secure and lightweight image encryption algorithm. Multimed Tools Appl. 2020;80(7):10391–416.10.1007/s11042-020-10116-zSuche in Google Scholar
[25] Simin D, Guodong Y. IWT and RSA based asymmetric image encryption algorithm. Alex Eng J. 2023;66:979–91.10.1016/j.aej.2022.10.066Suche in Google Scholar
[26] Sally A, Maisa’a A. An improved method for combine (LSB and MSB) based on color image RGB. Eng Technol J. 2021;39(1B):231–42.10.30684/etj.v39i1B.1574Suche in Google Scholar
[27] Gao S, Wu R, Wang X, Wang J, Li Q, Wang C, et al. A 3D model encryption scheme based on a cascaded chaotic system. Signal Process. 2023;202:108745.10.1016/j.sigpro.2022.108745Suche in Google Scholar
[28] Khalid M, Mohamed A, Hanaa M, Mostafa M, Nabil A. Privacy protection in surveillance videos using block scrambling-based encryption and DCNN-based face detection. IEEE Access. 2022;10:106750–69.10.1109/ACCESS.2022.3211657Suche in Google Scholar
[29] Shuting C, Linqing H, Xuesong C, Xiaoming X. A symmetric plaintext-related color image encryption system based on bit permutation. Entropy. 2018;20(4):282.10.3390/e20040282Suche in Google Scholar PubMed PubMed Central
[30] Xiaolin W, Bin Z, Yutong H, Yamei R. A novel color image encryption scheme using rectangular transform-enhanced chaotic tent maps. IEEE Access. 2017;5:6429–36.Suche in Google Scholar
[31] Chih H, Guo H, Jie S, Jun J, Kuang H. Novel design of cryptosystems for video/audio streaming via dynamic synchronized chaos-based random keys. Multimed Syst. 2022;28(5):1793–808.10.1007/s00530-022-00950-6Suche in Google Scholar PubMed PubMed Central
[32] Lee K, Dutt N, Venkatasubramanian N. An experimental study on energy consumption of video encryption for mobile handheld devices. In 2005 IEEE International Conference on Multimedia and Expo. IEEE; 2005 Jul. p. 1424–7.Suche in Google Scholar
© 2024 the author(s), published by De Gruyter
This work is licensed under the Creative Commons Attribution 4.0 International License.
Artikel in diesem Heft
- Regular Articles
- Methodology of automated quality management
- Influence of vibratory conveyor design parameters on the trough motion and the self-synchronization of inertial vibrators
- Application of finite element method in industrial design, example of an electric motorcycle design project
- Correlative evaluation of the corrosion resilience and passivation properties of zinc and aluminum alloys in neutral chloride and acid-chloride solutions
- Will COVID “encourage” B2B and data exchange engineering in logistic firms?
- Influence of unsupported sleepers on flange climb derailment of two freight wagons
- A hybrid detection algorithm for 5G OTFS waveform for 64 and 256 QAM with Rayleigh and Rician channels
- Effect of short heat treatment on mechanical properties and shape memory properties of Cu–Al–Ni shape memory alloy
- Exploring the potential of ammonia and hydrogen as alternative fuels for transportation
- Impact of insulation on energy consumption and CO2 emissions in high-rise commercial buildings at various climate zones
- Advanced autopilot design with extremum-seeking control for aircraft control
- Adaptive multidimensional trust-based recommendation model for peer to peer applications
- Effects of CFRP sheets on the flexural behavior of high-strength concrete beam
- Enhancing urban sustainability through industrial synergy: A multidisciplinary framework for integrating sustainable industrial practices within urban settings – The case of Hamadan industrial city
- Advanced vibrant controller results of an energetic framework structure
- Application of the Taguchi method and RSM for process parameter optimization in AWSJ machining of CFRP composite-based orthopedic implants
- Improved correlation of soil modulus with SPT N values
- Technologies for high-temperature batch annealing of grain-oriented electrical steel: An overview
- Assessing the need for the adoption of digitalization in Indian small and medium enterprises
- A non-ideal hybridization issue for vertical TFET-based dielectric-modulated biosensor
- Optimizing data retrieval for enhanced data integrity verification in cloud environments
- Performance analysis of nonlinear crosstalk of WDM systems using modulation schemes criteria
- Nonlinear finite-element analysis of RC beams with various opening near supports
- Thermal analysis of Fe3O4–Cu/water over a cone: a fractional Maxwell model
- Radial–axial runner blade design using the coordinate slice technique
- Theoretical and experimental comparison between straight and curved continuous box girders
- Effect of the reinforcement ratio on the mechanical behaviour of textile-reinforced concrete composite: Experiment and numerical modeling
- Experimental and numerical investigation on composite beam–column joint connection behavior using different types of connection schemes
- Enhanced performance and robustness in anti-lock brake systems using barrier function-based integral sliding mode control
- Evaluation of the creep strength of samples produced by fused deposition modeling
- A combined feedforward-feedback controller design for nonlinear systems
- Effect of adjacent structures on footing settlement for different multi-building arrangements
- Analyzing the impact of curved tracks on wheel flange thickness reduction in railway systems
- Review Articles
- Mechanical and smart properties of cement nanocomposites containing nanomaterials: A brief review
- Applications of nanotechnology and nanoproduction techniques
- Relationship between indoor environmental quality and guests’ comfort and satisfaction at green hotels: A comprehensive review
- Communication
- Techniques to mitigate the admission of radon inside buildings
- Erratum
- Erratum to “Effect of short heat treatment on mechanical properties and shape memory properties of Cu–Al–Ni shape memory alloy”
- Special Issue: AESMT-3 - Part II
- Integrated fuzzy logic and multicriteria decision model methods for selecting suitable sites for wastewater treatment plant: A case study in the center of Basrah, Iraq
- Physical and mechanical response of porous metals composites with nano-natural additives
- Special Issue: AESMT-4 - Part II
- New recycling method of lubricant oil and the effect on the viscosity and viscous shear as an environmentally friendly
- Identify the effect of Fe2O3 nanoparticles on mechanical and microstructural characteristics of aluminum matrix composite produced by powder metallurgy technique
- Static behavior of piled raft foundation in clay
- Ultra-low-power CMOS ring oscillator with minimum power consumption of 2.9 pW using low-voltage biasing technique
- Using ANN for well type identifying and increasing production from Sa’di formation of Halfaya oil field – Iraq
- Optimizing the performance of concrete tiles using nano-papyrus and carbon fibers
- Special Issue: AESMT-5 - Part II
- Comparative the effect of distribution transformer coil shape on electromagnetic forces and their distribution using the FEM
- The complex of Weyl module in free characteristic in the event of a partition (7,5,3)
- Restrained captive domination number
- Experimental study of improving hot mix asphalt reinforced with carbon fibers
- Asphalt binder modified with recycled tyre rubber
- Thermal performance of radiant floor cooling with phase change material for energy-efficient buildings
- Surveying the prediction of risks in cryptocurrency investments using recurrent neural networks
- A deep reinforcement learning framework to modify LQR for an active vibration control applied to 2D building models
- Evaluation of mechanically stabilized earth retaining walls for different soil–structure interaction methods: A review
- Assessment of heat transfer in a triangular duct with different configurations of ribs using computational fluid dynamics
- Sulfate removal from wastewater by using waste material as an adsorbent
- Experimental investigation on strengthening lap joints subjected to bending in glulam timber beams using CFRP sheets
- A study of the vibrations of a rotor bearing suspended by a hybrid spring system of shape memory alloys
- Stability analysis of Hub dam under rapid drawdown
- Developing ANFIS-FMEA model for assessment and prioritization of potential trouble factors in Iraqi building projects
- Numerical and experimental comparison study of piled raft foundation
- Effect of asphalt modified with waste engine oil on the durability properties of hot asphalt mixtures with reclaimed asphalt pavement
- Hydraulic model for flood inundation in Diyala River Basin using HEC-RAS, PMP, and neural network
- Numerical study on discharge capacity of piano key side weir with various ratios of the crest length to the width
- The optimal allocation of thyristor-controlled series compensators for enhancement HVAC transmission lines Iraqi super grid by using seeker optimization algorithm
- Numerical and experimental study of the impact on aerodynamic characteristics of the NACA0012 airfoil
- Effect of nano-TiO2 on physical and rheological properties of asphalt cement
- Performance evolution of novel palm leaf powder used for enhancing hot mix asphalt
- Performance analysis, evaluation, and improvement of selected unsignalized intersection using SIDRA software – Case study
- Flexural behavior of RC beams externally reinforced with CFRP composites using various strategies
- Influence of fiber types on the properties of the artificial cold-bonded lightweight aggregates
- Experimental investigation of RC beams strengthened with externally bonded BFRP composites
- Generalized RKM methods for solving fifth-order quasi-linear fractional partial differential equation
- An experimental and numerical study investigating sediment transport position in the bed of sewer pipes in Karbala
- Role of individual component failure in the performance of a 1-out-of-3 cold standby system: A Markov model approach
- Implementation for the cases (5, 4) and (5, 4)/(2, 0)
- Center group actions and related concepts
- Experimental investigation of the effect of horizontal construction joints on the behavior of deep beams
- Deletion of a vertex in even sum domination
- Deep learning techniques in concrete powder mix designing
- Effect of loading type in concrete deep beam with strut reinforcement
- Studying the effect of using CFRP warping on strength of husk rice concrete columns
- Parametric analysis of the influence of climatic factors on the formation of traditional buildings in the city of Al Najaf
- Suitability location for landfill using a fuzzy-GIS model: A case study in Hillah, Iraq
- Hybrid approach for cost estimation of sustainable building projects using artificial neural networks
- Assessment of indirect tensile stress and tensile–strength ratio and creep compliance in HMA mixes with micro-silica and PMB
- Density functional theory to study stopping power of proton in water, lung, bladder, and intestine
- A review of single flow, flow boiling, and coating microchannel studies
- Effect of GFRP bar length on the flexural behavior of hybrid concrete beams strengthened with NSM bars
- Exploring the impact of parameters on flow boiling heat transfer in microchannels and coated microtubes: A comprehensive review
- Crumb rubber modification for enhanced rutting resistance in asphalt mixtures
- Special Issue: AESMT-6
- Design of a new sorting colors system based on PLC, TIA portal, and factory I/O programs
- Forecasting empirical formula for suspended sediment load prediction at upstream of Al-Kufa barrage, Kufa City, Iraq
- Optimization and characterization of sustainable geopolymer mortars based on palygorskite clay, water glass, and sodium hydroxide
- Sediment transport modelling upstream of Al Kufa Barrage
- Study of energy loss, range, and stopping time for proton in germanium and copper materials
- Effect of internal and external recycle ratios on the nutrient removal efficiency of anaerobic/anoxic/oxic (VIP) wastewater treatment plant
- Enhancing structural behaviour of polypropylene fibre concrete columns longitudinally reinforced with fibreglass bars
- Sustainable road paving: Enhancing concrete paver blocks with zeolite-enhanced cement
- Evaluation of the operational performance of Karbala waste water treatment plant under variable flow using GPS-X model
- Design and simulation of photonic crystal fiber for highly sensitive chemical sensing applications
- Optimization and design of a new column sequencing for crude oil distillation at Basrah refinery
- Inductive 3D numerical modelling of the tibia bone using MRI to examine von Mises stress and overall deformation
- An image encryption method based on modified elliptic curve Diffie-Hellman key exchange protocol and Hill Cipher
- Experimental investigation of generating superheated steam using a parabolic dish with a cylindrical cavity receiver: A case study
- Effect of surface roughness on the interface behavior of clayey soils
- Investigated of the optical properties for SiO2 by using Lorentz model
- Measurements of induced vibrations due to steel pipe pile driving in Al-Fao soil: Effect of partial end closure
- Experimental and numerical studies of ballistic resistance of hybrid sandwich composite body armor
- Evaluation of clay layer presence on shallow foundation settlement in dry sand under an earthquake
- Optimal design of mechanical performances of asphalt mixtures comprising nano-clay additives
- Advancing seismic performance: Isolators, TMDs, and multi-level strategies in reinforced concrete buildings
- Predicted evaporation in Basrah using artificial neural networks
- Energy management system for a small town to enhance quality of life
- Numerical study on entropy minimization in pipes with helical airfoil and CuO nanoparticle integration
- Equations and methodologies of inlet drainage system discharge coefficients: A review
- Thermal buckling analysis for hybrid and composite laminated plate by using new displacement function
- Investigation into the mechanical and thermal properties of lightweight mortar using commercial beads or recycled expanded polystyrene
- Experimental and theoretical analysis of single-jet column and concrete column using double-jet grouting technique applied at Al-Rashdia site
- The impact of incorporating waste materials on the mechanical and physical characteristics of tile adhesive materials
- Seismic resilience: Innovations in structural engineering for earthquake-prone areas
- Automatic human identification using fingerprint images based on Gabor filter and SIFT features fusion
- Performance of GRKM-method for solving classes of ordinary and partial differential equations of sixth-orders
- Visible light-boosted photodegradation activity of Ag–AgVO3/Zn0.5Mn0.5Fe2O4 supported heterojunctions for effective degradation of organic contaminates
- Production of sustainable concrete with treated cement kiln dust and iron slag waste aggregate
- Key effects on the structural behavior of fiber-reinforced lightweight concrete-ribbed slabs: A review
- A comparative analysis of the energy dissipation efficiency of various piano key weir types
- Special Issue: Transport 2022 - Part II
- Variability in road surface temperature in urban road network – A case study making use of mobile measurements
- Special Issue: BCEE5-2023
- Evaluation of reclaimed asphalt mixtures rejuvenated with waste engine oil to resist rutting deformation
- Assessment of potential resistance to moisture damage and fatigue cracks of asphalt mixture modified with ground granulated blast furnace slag
- Investigating seismic response in adjacent structures: A study on the impact of buildings’ orientation and distance considering soil–structure interaction
- Improvement of porosity of mortar using polyethylene glycol pre-polymer-impregnated mortar
- Three-dimensional analysis of steel beam-column bolted connections
- Assessment of agricultural drought in Iraq employing Landsat and MODIS imagery
- Performance evaluation of grouted porous asphalt concrete
- Optimization of local modified metakaolin-based geopolymer concrete by Taguchi method
- Effect of waste tire products on some characteristics of roller-compacted concrete
- Studying the lateral displacement of retaining wall supporting sandy soil under dynamic loads
- Seismic performance evaluation of concrete buttress dram (Dynamic linear analysis)
- Behavior of soil reinforced with micropiles
- Possibility of production high strength lightweight concrete containing organic waste aggregate and recycled steel fibers
- An investigation of self-sensing and mechanical properties of smart engineered cementitious composites reinforced with functional materials
- Forecasting changes in precipitation and temperatures of a regional watershed in Northern Iraq using LARS-WG model
- Experimental investigation of dynamic soil properties for modeling energy-absorbing layers
- Numerical investigation of the effect of longitudinal steel reinforcement ratio on the ductility of concrete beams
- An experimental study on the tensile properties of reinforced asphalt pavement
- Self-sensing behavior of hot asphalt mixture with steel fiber-based additive
- Behavior of ultra-high-performance concrete deep beams reinforced by basalt fibers
- Optimizing asphalt binder performance with various PET types
- Investigation of the hydraulic characteristics and homogeneity of the microstructure of the air voids in the sustainable rigid pavement
- Enhanced biogas production from municipal solid waste via digestion with cow manure: A case study
- Special Issue: AESMT-7 - Part I
- Preparation and investigation of cobalt nanoparticles by laser ablation: Structure, linear, and nonlinear optical properties
- Seismic analysis of RC building with plan irregularity in Baghdad/Iraq to obtain the optimal behavior
- The effect of urban environment on large-scale path loss model’s main parameters for mmWave 5G mobile network in Iraq
- Formatting a questionnaire for the quality control of river bank roads
- Vibration suppression of smart composite beam using model predictive controller
- Machine learning-based compressive strength estimation in nanomaterial-modified lightweight concrete
- In-depth analysis of critical factors affecting Iraqi construction projects performance
- Behavior of container berth structure under the influence of environmental and operational loads
- Energy absorption and impact response of ballistic resistance laminate
- Effect of water-absorbent polymer balls in internal curing on punching shear behavior of bubble slabs
- Effect of surface roughness on interface shear strength parameters of sandy soils
- Evaluating the interaction for embedded H-steel section in normal concrete under monotonic and repeated loads
- Estimation of the settlement of pile head using ANN and multivariate linear regression based on the results of load transfer method
- Enhancing communication: Deep learning for Arabic sign language translation
- A review of recent studies of both heat pipe and evaporative cooling in passive heat recovery
- Effect of nano-silica on the mechanical properties of LWC
- An experimental study of some mechanical properties and absorption for polymer-modified cement mortar modified with superplasticizer
- Digital beamforming enhancement with LSTM-based deep learning for millimeter wave transmission
- Developing an efficient planning process for heritage buildings maintenance in Iraq
- Design and optimization of two-stage controller for three-phase multi-converter/multi-machine electric vehicle
- Evaluation of microstructure and mechanical properties of Al1050/Al2O3/Gr composite processed by forming operation ECAP
- Calculations of mass stopping power and range of protons in organic compounds (CH3OH, CH2O, and CO2) at energy range of 0.01–1,000 MeV
- Investigation of in vitro behavior of composite coating hydroxyapatite-nano silver on 316L stainless steel substrate by electrophoretic technic for biomedical tools
- A review: Enhancing tribological properties of journal bearings composite materials
- Improvements in the randomness and security of digital currency using the photon sponge hash function through Maiorana–McFarland S-box replacement
- Design a new scheme for image security using a deep learning technique of hierarchical parameters
- Special Issue: ICES 2023
- Comparative geotechnical analysis for ultimate bearing capacity of precast concrete piles using cone resistance measurements
- Visualizing sustainable rainwater harvesting: A case study of Karbala Province
- Geogrid reinforcement for improving bearing capacity and stability of square foundations
- Evaluation of the effluent concentrations of Karbala wastewater treatment plant using reliability analysis
- Adsorbent made with inexpensive, local resources
- Effect of drain pipes on seepage and slope stability through a zoned earth dam
- Sediment accumulation in an 8 inch sewer pipe for a sample of various particles obtained from the streets of Karbala city, Iraq
- Special Issue: IETAS 2024 - Part I
- Analyzing the impact of transfer learning on explanation accuracy in deep learning-based ECG recognition systems
- Effect of scale factor on the dynamic response of frame foundations
- Improving multi-object detection and tracking with deep learning, DeepSORT, and frame cancellation techniques
- The impact of using prestressed CFRP bars on the development of flexural strength
- Assessment of surface hardness and impact strength of denture base resins reinforced with silver–titanium dioxide and silver–zirconium dioxide nanoparticles: In vitro study
- A data augmentation approach to enhance breast cancer detection using generative adversarial and artificial neural networks
- Modification of the 5D Lorenz chaotic map with fuzzy numbers for video encryption in cloud computing
- Special Issue: 51st KKBN - Part I
- Evaluation of static bending caused damage of glass-fiber composite structure using terahertz inspection
Artikel in diesem Heft
- Regular Articles
- Methodology of automated quality management
- Influence of vibratory conveyor design parameters on the trough motion and the self-synchronization of inertial vibrators
- Application of finite element method in industrial design, example of an electric motorcycle design project
- Correlative evaluation of the corrosion resilience and passivation properties of zinc and aluminum alloys in neutral chloride and acid-chloride solutions
- Will COVID “encourage” B2B and data exchange engineering in logistic firms?
- Influence of unsupported sleepers on flange climb derailment of two freight wagons
- A hybrid detection algorithm for 5G OTFS waveform for 64 and 256 QAM with Rayleigh and Rician channels
- Effect of short heat treatment on mechanical properties and shape memory properties of Cu–Al–Ni shape memory alloy
- Exploring the potential of ammonia and hydrogen as alternative fuels for transportation
- Impact of insulation on energy consumption and CO2 emissions in high-rise commercial buildings at various climate zones
- Advanced autopilot design with extremum-seeking control for aircraft control
- Adaptive multidimensional trust-based recommendation model for peer to peer applications
- Effects of CFRP sheets on the flexural behavior of high-strength concrete beam
- Enhancing urban sustainability through industrial synergy: A multidisciplinary framework for integrating sustainable industrial practices within urban settings – The case of Hamadan industrial city
- Advanced vibrant controller results of an energetic framework structure
- Application of the Taguchi method and RSM for process parameter optimization in AWSJ machining of CFRP composite-based orthopedic implants
- Improved correlation of soil modulus with SPT N values
- Technologies for high-temperature batch annealing of grain-oriented electrical steel: An overview
- Assessing the need for the adoption of digitalization in Indian small and medium enterprises
- A non-ideal hybridization issue for vertical TFET-based dielectric-modulated biosensor
- Optimizing data retrieval for enhanced data integrity verification in cloud environments
- Performance analysis of nonlinear crosstalk of WDM systems using modulation schemes criteria
- Nonlinear finite-element analysis of RC beams with various opening near supports
- Thermal analysis of Fe3O4–Cu/water over a cone: a fractional Maxwell model
- Radial–axial runner blade design using the coordinate slice technique
- Theoretical and experimental comparison between straight and curved continuous box girders
- Effect of the reinforcement ratio on the mechanical behaviour of textile-reinforced concrete composite: Experiment and numerical modeling
- Experimental and numerical investigation on composite beam–column joint connection behavior using different types of connection schemes
- Enhanced performance and robustness in anti-lock brake systems using barrier function-based integral sliding mode control
- Evaluation of the creep strength of samples produced by fused deposition modeling
- A combined feedforward-feedback controller design for nonlinear systems
- Effect of adjacent structures on footing settlement for different multi-building arrangements
- Analyzing the impact of curved tracks on wheel flange thickness reduction in railway systems
- Review Articles
- Mechanical and smart properties of cement nanocomposites containing nanomaterials: A brief review
- Applications of nanotechnology and nanoproduction techniques
- Relationship between indoor environmental quality and guests’ comfort and satisfaction at green hotels: A comprehensive review
- Communication
- Techniques to mitigate the admission of radon inside buildings
- Erratum
- Erratum to “Effect of short heat treatment on mechanical properties and shape memory properties of Cu–Al–Ni shape memory alloy”
- Special Issue: AESMT-3 - Part II
- Integrated fuzzy logic and multicriteria decision model methods for selecting suitable sites for wastewater treatment plant: A case study in the center of Basrah, Iraq
- Physical and mechanical response of porous metals composites with nano-natural additives
- Special Issue: AESMT-4 - Part II
- New recycling method of lubricant oil and the effect on the viscosity and viscous shear as an environmentally friendly
- Identify the effect of Fe2O3 nanoparticles on mechanical and microstructural characteristics of aluminum matrix composite produced by powder metallurgy technique
- Static behavior of piled raft foundation in clay
- Ultra-low-power CMOS ring oscillator with minimum power consumption of 2.9 pW using low-voltage biasing technique
- Using ANN for well type identifying and increasing production from Sa’di formation of Halfaya oil field – Iraq
- Optimizing the performance of concrete tiles using nano-papyrus and carbon fibers
- Special Issue: AESMT-5 - Part II
- Comparative the effect of distribution transformer coil shape on electromagnetic forces and their distribution using the FEM
- The complex of Weyl module in free characteristic in the event of a partition (7,5,3)
- Restrained captive domination number
- Experimental study of improving hot mix asphalt reinforced with carbon fibers
- Asphalt binder modified with recycled tyre rubber
- Thermal performance of radiant floor cooling with phase change material for energy-efficient buildings
- Surveying the prediction of risks in cryptocurrency investments using recurrent neural networks
- A deep reinforcement learning framework to modify LQR for an active vibration control applied to 2D building models
- Evaluation of mechanically stabilized earth retaining walls for different soil–structure interaction methods: A review
- Assessment of heat transfer in a triangular duct with different configurations of ribs using computational fluid dynamics
- Sulfate removal from wastewater by using waste material as an adsorbent
- Experimental investigation on strengthening lap joints subjected to bending in glulam timber beams using CFRP sheets
- A study of the vibrations of a rotor bearing suspended by a hybrid spring system of shape memory alloys
- Stability analysis of Hub dam under rapid drawdown
- Developing ANFIS-FMEA model for assessment and prioritization of potential trouble factors in Iraqi building projects
- Numerical and experimental comparison study of piled raft foundation
- Effect of asphalt modified with waste engine oil on the durability properties of hot asphalt mixtures with reclaimed asphalt pavement
- Hydraulic model for flood inundation in Diyala River Basin using HEC-RAS, PMP, and neural network
- Numerical study on discharge capacity of piano key side weir with various ratios of the crest length to the width
- The optimal allocation of thyristor-controlled series compensators for enhancement HVAC transmission lines Iraqi super grid by using seeker optimization algorithm
- Numerical and experimental study of the impact on aerodynamic characteristics of the NACA0012 airfoil
- Effect of nano-TiO2 on physical and rheological properties of asphalt cement
- Performance evolution of novel palm leaf powder used for enhancing hot mix asphalt
- Performance analysis, evaluation, and improvement of selected unsignalized intersection using SIDRA software – Case study
- Flexural behavior of RC beams externally reinforced with CFRP composites using various strategies
- Influence of fiber types on the properties of the artificial cold-bonded lightweight aggregates
- Experimental investigation of RC beams strengthened with externally bonded BFRP composites
- Generalized RKM methods for solving fifth-order quasi-linear fractional partial differential equation
- An experimental and numerical study investigating sediment transport position in the bed of sewer pipes in Karbala
- Role of individual component failure in the performance of a 1-out-of-3 cold standby system: A Markov model approach
- Implementation for the cases (5, 4) and (5, 4)/(2, 0)
- Center group actions and related concepts
- Experimental investigation of the effect of horizontal construction joints on the behavior of deep beams
- Deletion of a vertex in even sum domination
- Deep learning techniques in concrete powder mix designing
- Effect of loading type in concrete deep beam with strut reinforcement
- Studying the effect of using CFRP warping on strength of husk rice concrete columns
- Parametric analysis of the influence of climatic factors on the formation of traditional buildings in the city of Al Najaf
- Suitability location for landfill using a fuzzy-GIS model: A case study in Hillah, Iraq
- Hybrid approach for cost estimation of sustainable building projects using artificial neural networks
- Assessment of indirect tensile stress and tensile–strength ratio and creep compliance in HMA mixes with micro-silica and PMB
- Density functional theory to study stopping power of proton in water, lung, bladder, and intestine
- A review of single flow, flow boiling, and coating microchannel studies
- Effect of GFRP bar length on the flexural behavior of hybrid concrete beams strengthened with NSM bars
- Exploring the impact of parameters on flow boiling heat transfer in microchannels and coated microtubes: A comprehensive review
- Crumb rubber modification for enhanced rutting resistance in asphalt mixtures
- Special Issue: AESMT-6
- Design of a new sorting colors system based on PLC, TIA portal, and factory I/O programs
- Forecasting empirical formula for suspended sediment load prediction at upstream of Al-Kufa barrage, Kufa City, Iraq
- Optimization and characterization of sustainable geopolymer mortars based on palygorskite clay, water glass, and sodium hydroxide
- Sediment transport modelling upstream of Al Kufa Barrage
- Study of energy loss, range, and stopping time for proton in germanium and copper materials
- Effect of internal and external recycle ratios on the nutrient removal efficiency of anaerobic/anoxic/oxic (VIP) wastewater treatment plant
- Enhancing structural behaviour of polypropylene fibre concrete columns longitudinally reinforced with fibreglass bars
- Sustainable road paving: Enhancing concrete paver blocks with zeolite-enhanced cement
- Evaluation of the operational performance of Karbala waste water treatment plant under variable flow using GPS-X model
- Design and simulation of photonic crystal fiber for highly sensitive chemical sensing applications
- Optimization and design of a new column sequencing for crude oil distillation at Basrah refinery
- Inductive 3D numerical modelling of the tibia bone using MRI to examine von Mises stress and overall deformation
- An image encryption method based on modified elliptic curve Diffie-Hellman key exchange protocol and Hill Cipher
- Experimental investigation of generating superheated steam using a parabolic dish with a cylindrical cavity receiver: A case study
- Effect of surface roughness on the interface behavior of clayey soils
- Investigated of the optical properties for SiO2 by using Lorentz model
- Measurements of induced vibrations due to steel pipe pile driving in Al-Fao soil: Effect of partial end closure
- Experimental and numerical studies of ballistic resistance of hybrid sandwich composite body armor
- Evaluation of clay layer presence on shallow foundation settlement in dry sand under an earthquake
- Optimal design of mechanical performances of asphalt mixtures comprising nano-clay additives
- Advancing seismic performance: Isolators, TMDs, and multi-level strategies in reinforced concrete buildings
- Predicted evaporation in Basrah using artificial neural networks
- Energy management system for a small town to enhance quality of life
- Numerical study on entropy minimization in pipes with helical airfoil and CuO nanoparticle integration
- Equations and methodologies of inlet drainage system discharge coefficients: A review
- Thermal buckling analysis for hybrid and composite laminated plate by using new displacement function
- Investigation into the mechanical and thermal properties of lightweight mortar using commercial beads or recycled expanded polystyrene
- Experimental and theoretical analysis of single-jet column and concrete column using double-jet grouting technique applied at Al-Rashdia site
- The impact of incorporating waste materials on the mechanical and physical characteristics of tile adhesive materials
- Seismic resilience: Innovations in structural engineering for earthquake-prone areas
- Automatic human identification using fingerprint images based on Gabor filter and SIFT features fusion
- Performance of GRKM-method for solving classes of ordinary and partial differential equations of sixth-orders
- Visible light-boosted photodegradation activity of Ag–AgVO3/Zn0.5Mn0.5Fe2O4 supported heterojunctions for effective degradation of organic contaminates
- Production of sustainable concrete with treated cement kiln dust and iron slag waste aggregate
- Key effects on the structural behavior of fiber-reinforced lightweight concrete-ribbed slabs: A review
- A comparative analysis of the energy dissipation efficiency of various piano key weir types
- Special Issue: Transport 2022 - Part II
- Variability in road surface temperature in urban road network – A case study making use of mobile measurements
- Special Issue: BCEE5-2023
- Evaluation of reclaimed asphalt mixtures rejuvenated with waste engine oil to resist rutting deformation
- Assessment of potential resistance to moisture damage and fatigue cracks of asphalt mixture modified with ground granulated blast furnace slag
- Investigating seismic response in adjacent structures: A study on the impact of buildings’ orientation and distance considering soil–structure interaction
- Improvement of porosity of mortar using polyethylene glycol pre-polymer-impregnated mortar
- Three-dimensional analysis of steel beam-column bolted connections
- Assessment of agricultural drought in Iraq employing Landsat and MODIS imagery
- Performance evaluation of grouted porous asphalt concrete
- Optimization of local modified metakaolin-based geopolymer concrete by Taguchi method
- Effect of waste tire products on some characteristics of roller-compacted concrete
- Studying the lateral displacement of retaining wall supporting sandy soil under dynamic loads
- Seismic performance evaluation of concrete buttress dram (Dynamic linear analysis)
- Behavior of soil reinforced with micropiles
- Possibility of production high strength lightweight concrete containing organic waste aggregate and recycled steel fibers
- An investigation of self-sensing and mechanical properties of smart engineered cementitious composites reinforced with functional materials
- Forecasting changes in precipitation and temperatures of a regional watershed in Northern Iraq using LARS-WG model
- Experimental investigation of dynamic soil properties for modeling energy-absorbing layers
- Numerical investigation of the effect of longitudinal steel reinforcement ratio on the ductility of concrete beams
- An experimental study on the tensile properties of reinforced asphalt pavement
- Self-sensing behavior of hot asphalt mixture with steel fiber-based additive
- Behavior of ultra-high-performance concrete deep beams reinforced by basalt fibers
- Optimizing asphalt binder performance with various PET types
- Investigation of the hydraulic characteristics and homogeneity of the microstructure of the air voids in the sustainable rigid pavement
- Enhanced biogas production from municipal solid waste via digestion with cow manure: A case study
- Special Issue: AESMT-7 - Part I
- Preparation and investigation of cobalt nanoparticles by laser ablation: Structure, linear, and nonlinear optical properties
- Seismic analysis of RC building with plan irregularity in Baghdad/Iraq to obtain the optimal behavior
- The effect of urban environment on large-scale path loss model’s main parameters for mmWave 5G mobile network in Iraq
- Formatting a questionnaire for the quality control of river bank roads
- Vibration suppression of smart composite beam using model predictive controller
- Machine learning-based compressive strength estimation in nanomaterial-modified lightweight concrete
- In-depth analysis of critical factors affecting Iraqi construction projects performance
- Behavior of container berth structure under the influence of environmental and operational loads
- Energy absorption and impact response of ballistic resistance laminate
- Effect of water-absorbent polymer balls in internal curing on punching shear behavior of bubble slabs
- Effect of surface roughness on interface shear strength parameters of sandy soils
- Evaluating the interaction for embedded H-steel section in normal concrete under monotonic and repeated loads
- Estimation of the settlement of pile head using ANN and multivariate linear regression based on the results of load transfer method
- Enhancing communication: Deep learning for Arabic sign language translation
- A review of recent studies of both heat pipe and evaporative cooling in passive heat recovery
- Effect of nano-silica on the mechanical properties of LWC
- An experimental study of some mechanical properties and absorption for polymer-modified cement mortar modified with superplasticizer
- Digital beamforming enhancement with LSTM-based deep learning for millimeter wave transmission
- Developing an efficient planning process for heritage buildings maintenance in Iraq
- Design and optimization of two-stage controller for three-phase multi-converter/multi-machine electric vehicle
- Evaluation of microstructure and mechanical properties of Al1050/Al2O3/Gr composite processed by forming operation ECAP
- Calculations of mass stopping power and range of protons in organic compounds (CH3OH, CH2O, and CO2) at energy range of 0.01–1,000 MeV
- Investigation of in vitro behavior of composite coating hydroxyapatite-nano silver on 316L stainless steel substrate by electrophoretic technic for biomedical tools
- A review: Enhancing tribological properties of journal bearings composite materials
- Improvements in the randomness and security of digital currency using the photon sponge hash function through Maiorana–McFarland S-box replacement
- Design a new scheme for image security using a deep learning technique of hierarchical parameters
- Special Issue: ICES 2023
- Comparative geotechnical analysis for ultimate bearing capacity of precast concrete piles using cone resistance measurements
- Visualizing sustainable rainwater harvesting: A case study of Karbala Province
- Geogrid reinforcement for improving bearing capacity and stability of square foundations
- Evaluation of the effluent concentrations of Karbala wastewater treatment plant using reliability analysis
- Adsorbent made with inexpensive, local resources
- Effect of drain pipes on seepage and slope stability through a zoned earth dam
- Sediment accumulation in an 8 inch sewer pipe for a sample of various particles obtained from the streets of Karbala city, Iraq
- Special Issue: IETAS 2024 - Part I
- Analyzing the impact of transfer learning on explanation accuracy in deep learning-based ECG recognition systems
- Effect of scale factor on the dynamic response of frame foundations
- Improving multi-object detection and tracking with deep learning, DeepSORT, and frame cancellation techniques
- The impact of using prestressed CFRP bars on the development of flexural strength
- Assessment of surface hardness and impact strength of denture base resins reinforced with silver–titanium dioxide and silver–zirconium dioxide nanoparticles: In vitro study
- A data augmentation approach to enhance breast cancer detection using generative adversarial and artificial neural networks
- Modification of the 5D Lorenz chaotic map with fuzzy numbers for video encryption in cloud computing
- Special Issue: 51st KKBN - Part I
- Evaluation of static bending caused damage of glass-fiber composite structure using terahertz inspection

