Abstract
Internet of Things (IoT) and more new technologies have brought great convenience to daily life, but they have also raised more data security and privacy protection. To ensure the security of IoT data and user privacy in various scenarios, the federated learning (FL) method is optimized based on function encryption and blockchain. At the same time, using the decentralized function to encrypt the privacy of the training model, the learning model can provide more secure and reliable services, aiming to solve the problem of large difference in the quality of computing nodes and data privacy leakage in the current FL. The experimental results show that the model accuracy of the optimized system reaches 93%, which is significantly higher than 90% of the traditional centralized model. In addition, the improved approach effectively reduced the risk of data breaches by 1.5%, increased the resistance to attacks by 90%, and increased the user trust by 85%. The average response time of the optimized system is between 5 and 100 milliseconds. When the data dimension is less than 32 and the size of the data terminal group is less than 10, the terminal traffic of the improved FL data protection system is less than that of the other two systems. When the data terminal group was 50, the calculated communication traffic was 19,008 bits, which was an acceptable range for improving the data protection system of FL. Experimental results demonstrate that the improved method can improve the accuracy of the learning model and ensure the efficiency of data processing while protecting user privacy in data sharing.
1 Introduction
Affected by big data, edge computing, cloud computing, and other technologies, various artificial intelligence (AI) technologies are integrated into all aspects of human life. As a new computing architecture, edge computing has the ability to process and store data near the source of data generation, and its potential applications are extensive and far-reaching. First, in intelligent transportation systems, edge computing can process sensor data from vehicles and infrastructure in real time to optimize traffic flow and safety conditions. Second, in the field of intelligent manufacturing, edge computing can support real-time monitoring and fault diagnosis of equipment, improve production efficiency, and reduce maintenance costs. In addition, edge computing also shows great potential in the medical field, through the instant analysis of patient data, to provide faster response and personalized medical services. At the same time, in the Internet of Things (IoT) environment, edge computing can effectively reduce latency, enhance data privacy protection, and improve user experience. With the development of 5G networks, edge computing will play an increasingly important role in many fields such as smart home, environmental monitoring, and intelligent security. In short, many technologies such as smart transportation, smart healthcare, and smart homes are closely related to IoT technologies [1]. Thanks to the development of information collection and statistical tools, IoT data collection is no longer limited to a predetermined collection scope, but is automatically collected [2]. As the most fundamental element of the IoT, data information security has become one of the research focuses for professionals. In the collection and transmission of data, users’ device data faces the risk of being maliciously collected without consent. Therefore, the leakage of privacy data may have an impact on public and national security [3]. In the data storage, distributed cloud storage can effectively solve the centralization problem of centralized cloud storage, but it also increases the targeted attacks [4]. When data leaks or is lost, it can cause serious losses to its owners. Regarding the security issues of the IoT, many domestic and foreign experts have made improvements to its protection technology.
Federated learning (FL) is a fundamental AI technology designed to enable efficient machine learning while ensuring information security and data privacy during big data exchange. Deng et al. built a new framework that integrated three main components: learning quality estimation, quality awareness incentive mechanism, and automatic weighted model aggregation. The aim was to address issues such as large differences in computing node quality and data privacy leakage in FL, to achieve efficient FL. The framework had good effectiveness in real-world datasets and learning tasks [5]. Polap and Woźniak. used FL and considered parallelism to implement various classifiers, in order to improve efficiency and reduce training time, while being able to quickly implement given solutions to meet actual market demands. Experiments showed that even in small databases, this technology could serve as a very useful implementation method [6]. Geng et al. designed a fault diagnosis algorithm on the basis of FL method, which improved the quality of the training model by optimizing the weighting strategy of the model and the model aggregation strategy. The algorithm reduced the average training iterations by 52.5% and improved the average fault classification accuracy by about 8.6% [7]. Li et al. designed an improved FL strategy to overcome the convergence difficulties and high data quality issues of traditional FL. This method learned a globally shared model by aggregating local training generators with the maximum mean difference. Experimental results showed that this method made significant progress in achieving the highest initial score and generating high-quality instances [8]. Rashid et al. built a FL method to detect unnecessary intrusions by jointly training local IoT device data to ensure privacy and security. The accuracy of the proposed intrusion detection model was 92.49%, which proved the effectiveness and reliability [9].
IoT data security and privacy protection refer to the protection and security measures for data in IoT systems to prevent data leakage, tampering, and malicious attacks, while also protecting user privacy. Shahid et al. discussed data privacy protection issues related to a subset of the IoT in the healthcare field, including possible points and causes of data breaches, as well as how to improve the compliance of IoT devices with medical data privacy and protection regulations. Suggestions were proposed to enhance the security and privacy of IoT implementation [10]. Yu et al. proposed three new memory neural network models to improve the security of medical data in the IoT. The model exhibited complex dynamic behavior, including coexisting attractors, multi-vortex attractors, and grid multi-vortex attractors. The results indicated that the distribution of ciphertext histograms was uniform, the correlation between adjacent pixels was almost zero, and the information entropy reached 7.9977 [11]. Ren et al. built a privacy-preserving intelligent crowd-sourcing scheme on the basis of reinforcement learning, which considered data volume, data quality, and cost to optimize the system’s utility, to address the security issues of data-based applications in the IoT. Simulation experiments showed that this method was effective [12]. Rupa et al. proposed a homomorphic encryption technique on the basis of matrix transformation to protect the security of cloud data. This technology shifted, rotated, and transposed the binary conversion values of each character in plaintext, using symmetric cryptography for encryption and decryption. The research results indicated that this algorithm was more powerful than existing methods, which could resist various attacks. Attackers could not easily predict plaintext through statistical analysis [13]. Li et al. proposed a protection and reward data-sharing scheme based on blockchain, which utilized non-repudiation ring signatures and Monero to achieve anonymous transactions. The permission technology for smart contract execution was used to ensure flexible access control for multiple shares. The results showed that the scheme had efficient and practical performance, which could prevent malicious cloud servers from establishing databases of user behavior profiles [14]. Issa et al. proposed a blockchain-based federated learning method to address the privacy and security issues of deep learning algorithms in Internet of Things systems, aiming to enhance the security and privacy protection of the systems, and discussed the challenges and risks of future research [15]. Ioannou et al. proposed an energy-efficient IDS to enhance network security in response to security risks in the medical Internet of Things (MIoT). The experimental results show that the enhanced random forest algorithm achieves 99.98% accuracy in attack classification, while the single-class support vector machine achieves 99.7% accuracy in anomaly detection. In addition, the introduced joint learning method effectively updates the entire system model and achieves efficient attack identification through the iot system and Raspberry Pi MIoT gateway, while reducing resource utilization and energy consumption [16]. Li et al. proposed a novel joint learning framework to address the challenges of device heterogeneity, non-independent uniformly distributed data (non-IID), and communication overhead. The framework utilizes efficient model aggregation techniques and communication optimization updates to reduce bandwidth consumption and ensure data privacy and security. Extensive testing shows that the framework outperforms existing learning algorithms in connection speed, resource utilization, and model performance, achieving a 15% increase in model accuracy and a 40% reduction in communication overhead. The scalability and adaptability of the framework under changing network conditions and customer availability have been demonstrated through the validation in smart city traffic prediction and medical iot case studies [17].
To sum up, most of the current research focuses on a single technology or algorithm and lacks the integration of methods across domains, for example, relatively few studies combine joint learning with edge computing or blockchain, which limits its ability to be applied to more complex scenarios; there have been studies focusing on device heterogeneity and non-independent homodistributed data, but there is still a lack of effective solutions to handle the converged needs of different types of devices and data sources, which can lead to performance bottlenecks. Therefore, the study proposes an improved federal learning system for iot data security and privacy protection. The originality of this method lies in the use of multi-task learning and local batch normalization layer to effectively process non-IID data, so that the model can adapt to different data characteristics in a large range, and improve the generalization ability and robustness of the model. The proposed method adds adaptive client selection mechanism to optimize resource scheduling and communication efficiency, and the integrated data protection privacy policy strengthens the security of the system to ensure that the service quality is improved without affecting the security of user data.
2 Methods and materials
2.1 FL method based on Bayesian differential privacy (DP) mechanism and blockchain
Effective data protection is the main optimization objective in the training and prediction process of FL. During the training phase, privacy data protection can be achieved by encrypting the parameters of the learning model [18]. Malicious attacks will adjust the aggregation weights of FL models to change the proportion of local models, causing user models to be reconstructed. In order to prevent such attacks, the study utilizes Bayesian DP mechanism to accurately represent the privacy loss during the learning iteration stage, so that the model information uploaded by IoT users can be minimized as much as possible, thereby improving the accuracy. The schematic diagram of DP is displayed in Figure 1.
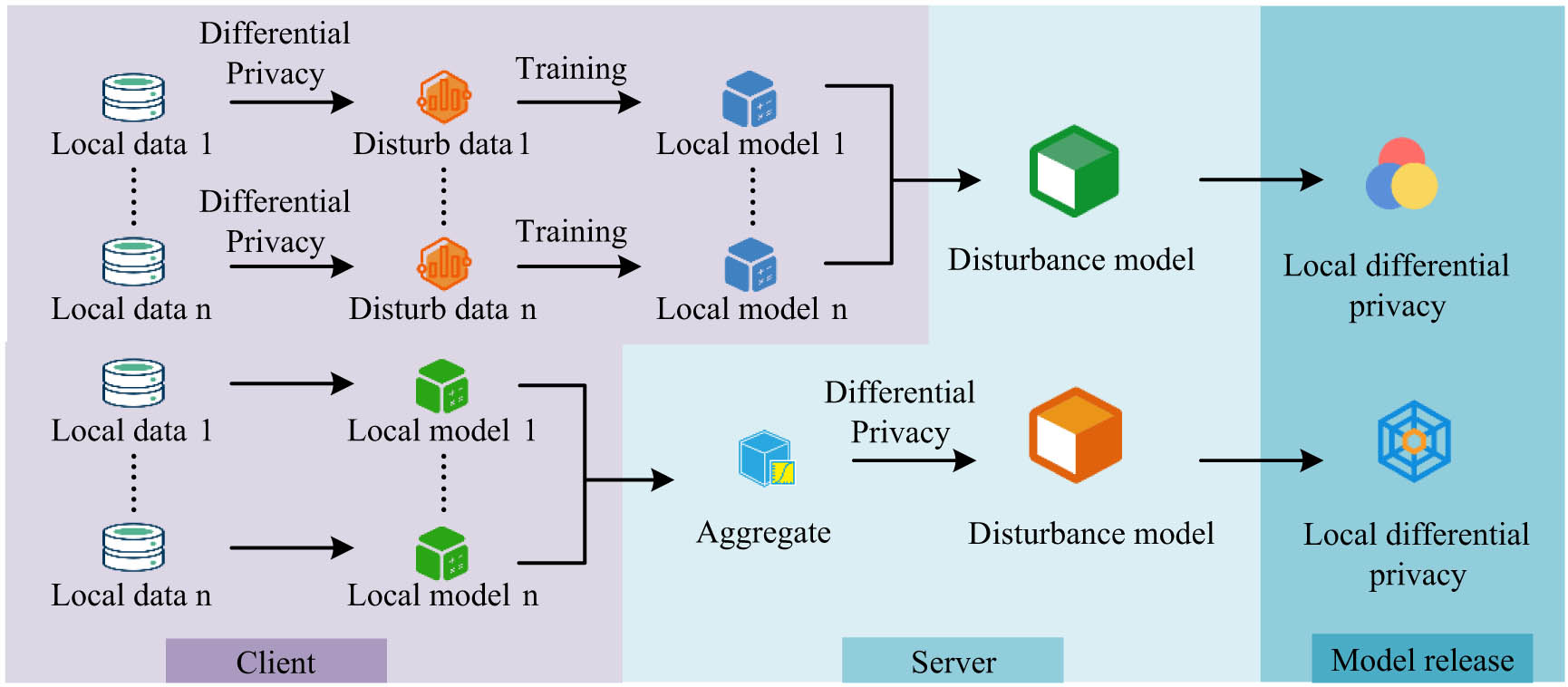
Schematic diagram of DP.
The structure of DP mainly consists of two parts, namely, local DP and centralized DP. The former achieves data protection by adding noise to the local training data to interfere with the data. The latter involves adding noise to the model after aggregation to reduce data disturbance. DP can prevent specific records in the dataset from being represented by the output of the function and has a relatively effective defense effect against inference attacks [19].
where
where
Bayesian DP takes into account the distribution characteristics of random samples on the basis of classical DP. The server generates a master public key based on the random number
where
where
Bayesian DP can prevent malicious attacks from querying accurate output results by adding noise to model parameters, thereby resisting malicious attacks during the prediction process and strengthening privacy protection during the prediction stage [20,21]. When model aggregation is completed through FL, services are prone to single failure points and are vulnerable to malicious attacks. To address this, the FL method is combined with blockchain to achieve secure aggregation based on blockchain. The aggregation process of the model based on function encryption is shown in Figure 2.
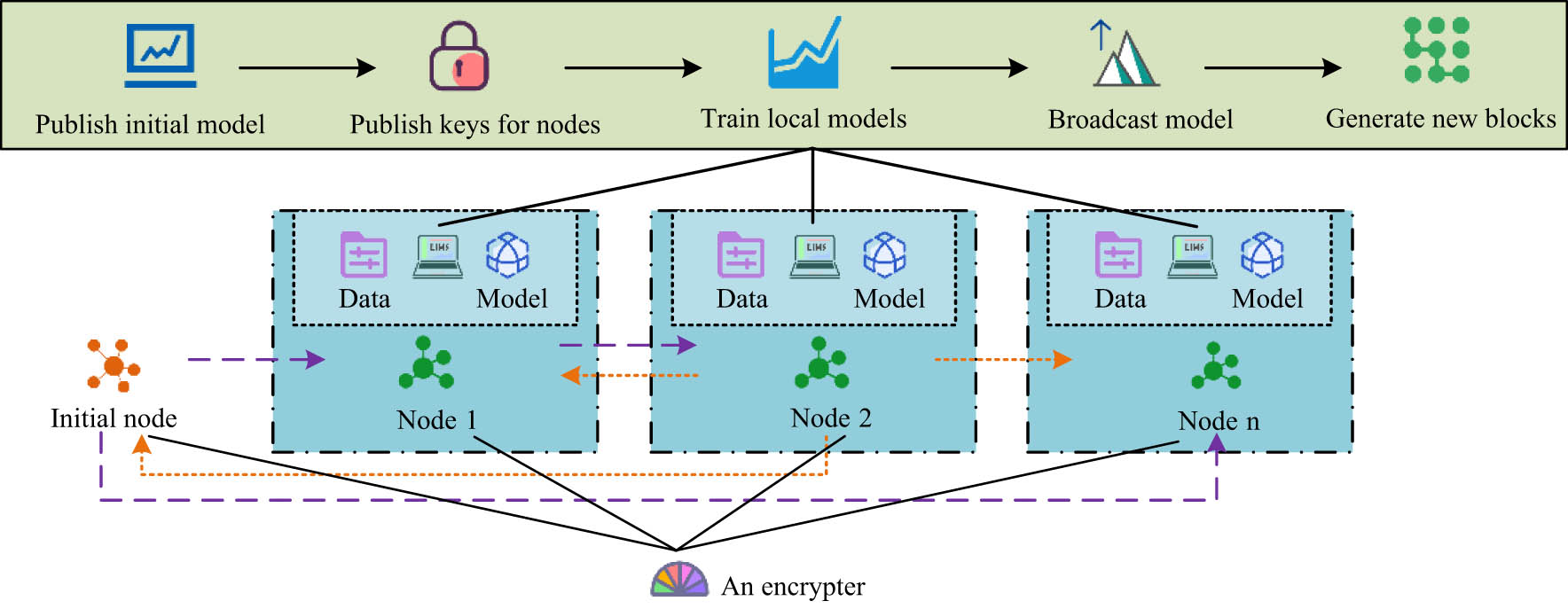
Model aggregation process based on function encryption.
In the process of model aggregation, distributed ledgers are mainly used to record the model parameters during training and aggregation. The training accuracy is improved by tracking and analyzing the training progress. At the same time, the model parameters are encrypted using a function encryption aggregation method to ensure that participants obtain the corresponding aggregated model results and cannot obtain the model results of other participants, effectively improving data security. In blockchain-based FL methods, in order to accurately select participants and improve the quality of uploaded model parameters, the fine-grained collaborative access control strategy is incorporated into the FL method. The main process is shown in Figure 3.
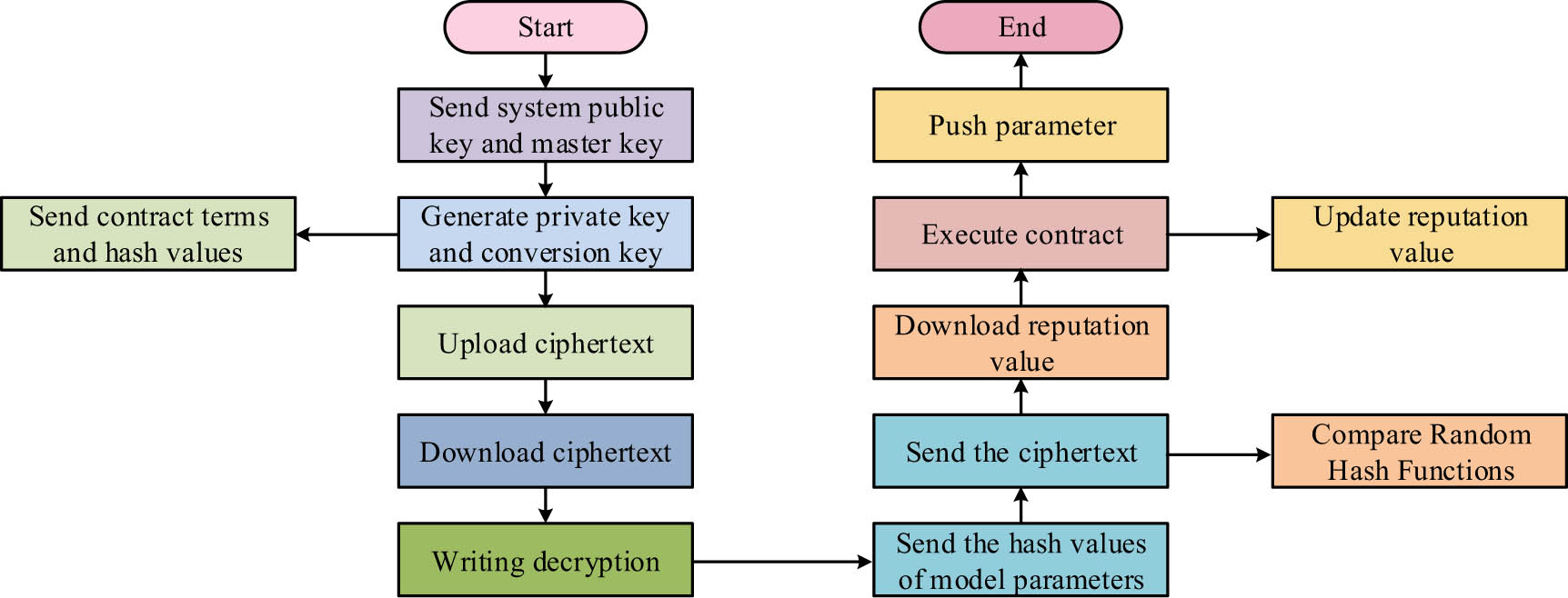
Fine-grained collaborative access control process.
In collaborative access control, the initialization algorithm is implemented by a trusted authentication center sending the system public key and master key to the task publisher and data holder. After the authentication center completes the initialization settings, output the common parameters and select two multiplication loop groups
where
2.2 Data security protection based on improved FL
After the blockchain securely aggregates the training process, the distributed ledger is used to record the model parameters during the training and aggregation process. To make the data sharing in the displacement network more secure and reliable, the privacy data-sharing dimensions of end users can be selectively processed. The combination of functional encryption and blockchain in the research achieves the dual goals of data privacy protection and security aggregation. Functional encryption allows data to be calculated while maintaining encryption, so that user data can still participate in model training even if it is not fully decrypted, thus improving the intensity of privacy protection. At the same time, BT enhances the security and trust of the system by providing an immutable distributed ledger, ensuring transparency of model parameters and training logs. When the edge node uploads its local model parameters to the data aggregation center, the blockchain records this process, avoiding the risk of data tampering or incorrect manipulation. Based on fog computing architecture, users can create their own data protection groups to ensure that their data and choices are not leaked. The dimension-selectable data-sharing schemes are mainly divided into five components: initialization, information aggregation, information mixing, and result analysis. The main framework of the data security-sharing scheme for dimension selectable is shown in Figure 4.
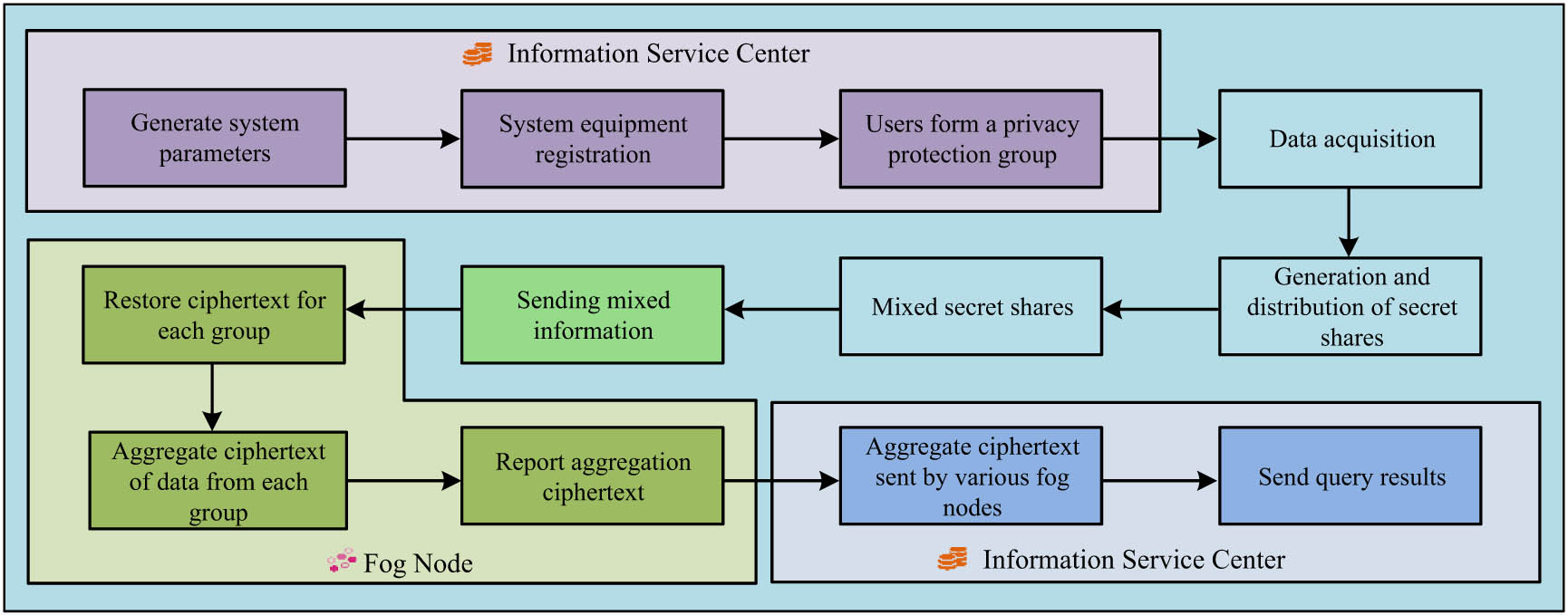
Dimension selectable data-sharing scheme process.
In the registration stage of data sharing, the registration operation is completed by the information service center. After initialization, when the user sends a query request, the information service center will send an information collection command to the fog node. The data terminal will generate a selection vector
where
When the data information is successfully received by the data terminal, the decryption process of ciphertext
In the process of encrypting different users and servers using keys, the incentive mechanism based on DP is added to improve user participation in FL. The principle of the incentive mechanism based on function encryption is displayed in Figure 5.
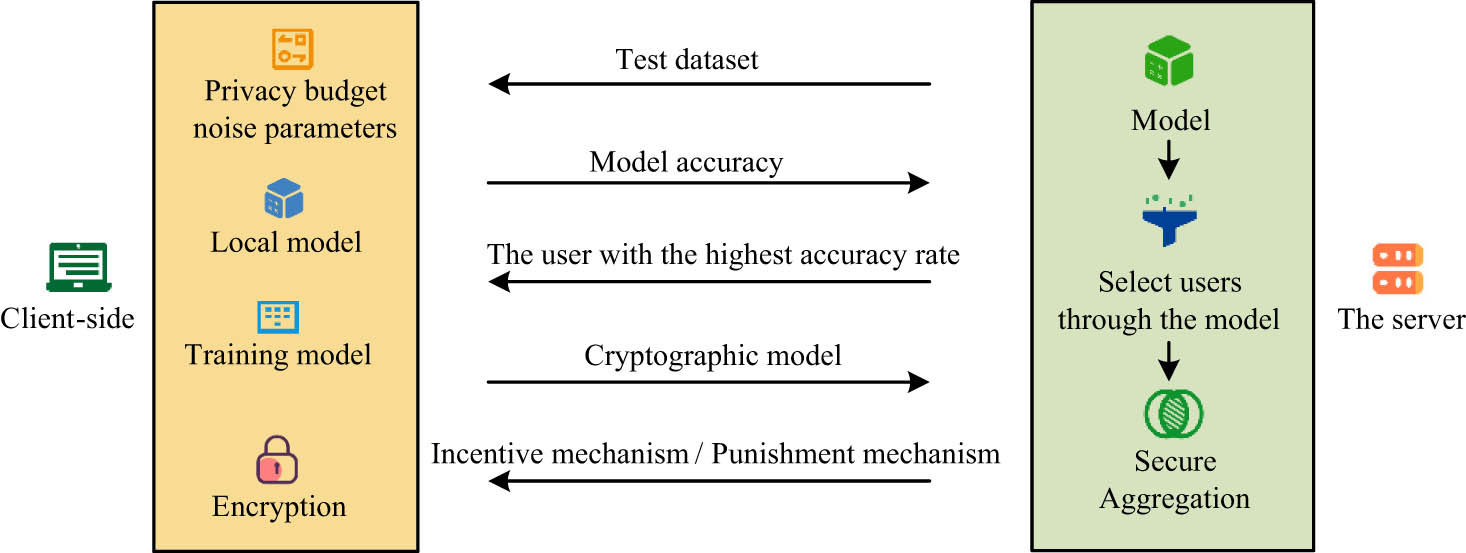
Incentive mechanism process.
When the server releases the initial model to the user, the user side needs to choose the corresponding privacy budget based on their own needs and privacy characteristics. Privacy budget is a crucial parameter for measuring privacy protection performance, which represents the privacy loss generated during training. When confirming the identity of the sender and the legality of the sent content, the system sums up the secret share information and uses symmetric keys and encryption algorithms to complete the encryption process. The encryption process of ciphertext
After encrypting the ciphertext
When the fog node obtains the relevant information of the group, it can be expressed as the corresponding group ciphertext aggregation vector. Then, the group aggregation vector is aggregated again. The re-aggregation result V of the group aggregation ciphertext related to the fog node can be expressed by Eq. (14):
The fog node takes the symmetric key between the data server and the information service center to encrypt the data, and sends the encrypted information to the information service center in the form of
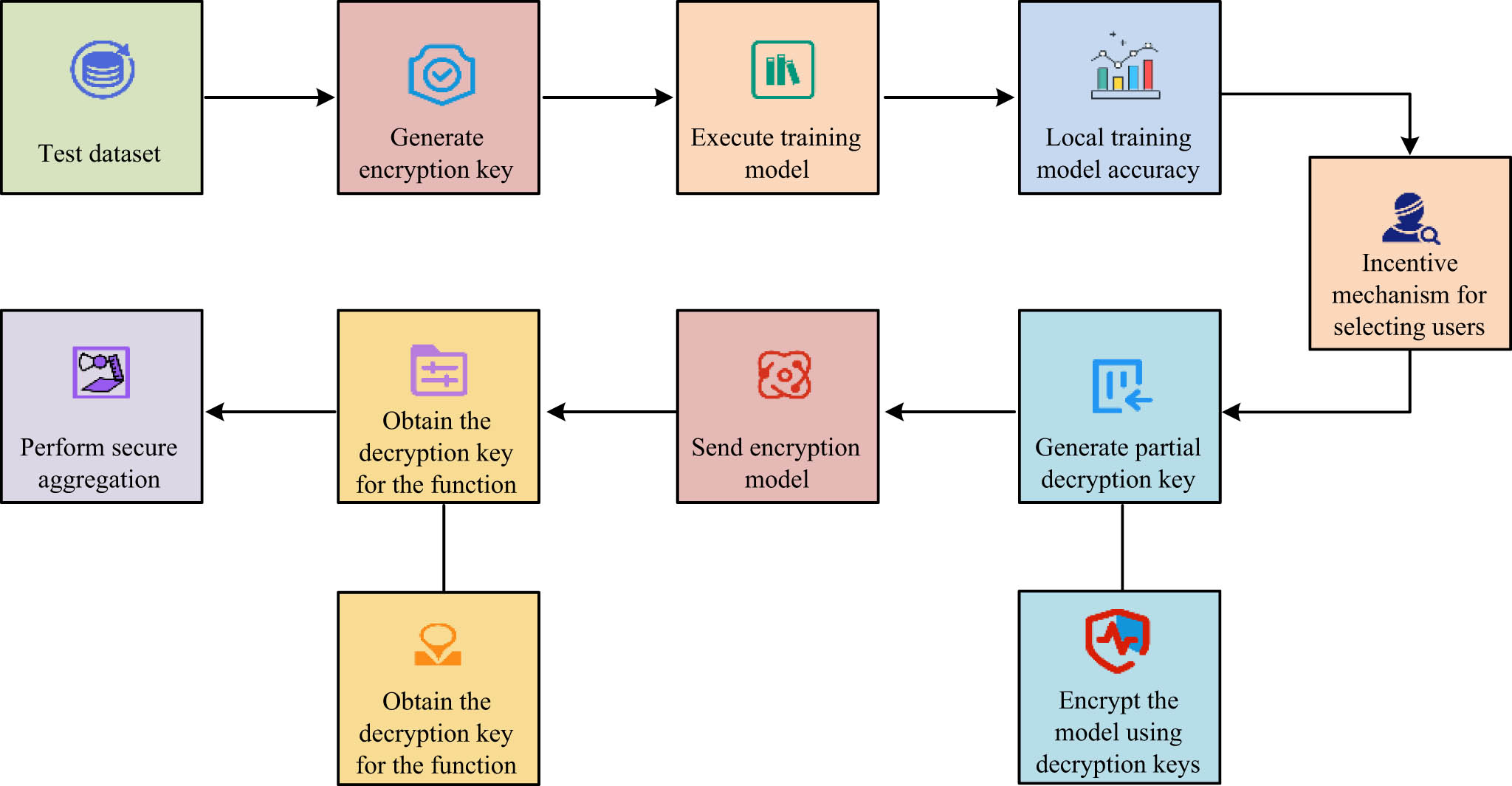
Learning method for decentralized function encryption.
Before conducting local training, the server is responsible for sending the public key and test dataset to each user. The selected user needs to encrypt the local model and send the data information to the server. After receiving the corresponding information in the information service center, the symmetric key is used to encrypt the information and send it to the data center. The encryption process can be expressed as Eq. (15):
When the data center receives the ciphertext, it can complete the aggregation operation on the ciphertext and then send the aggregated ciphertext to the user. At this point, the user can obtain information through the private key and decryption algorithm. The decentralized function is mainly reflected in the distributed management of data processing, storage, and decision making, which enhances the security and resilience of the system by eliminating the dependence on a single central server. In a decentralized architecture, data is processed and stored by multiple edge nodes that operate independently of each other and are able to collaborate without central control. This design not only improves data privacy and reduces the risk of data breaches, but also ensures data transparency and immutability through distributed ledger technology such as blockchain. In addition, decentralized smart contracts can automatically enforce the terms of the agreement, enabling the trust relationship between participants to be further enhanced, reducing operational costs and time delays. As a result, these innovative decentralized capabilities provide more secure, efficient, and flexible solutions for applications across multiple domains. When implementing an improved FL approach, potential scalability challenges include the allocation of computing resources, network bandwidth constraints, and the increase in the number of participating devices, which can lead to increased training times and reduced system performance. In order to solve these problems, a hierarchical FL architecture can be adopted to divide the participating nodes into different levels to optimize data transmission and utilization of computing resources. At the same time, a dynamic resource allocation mechanism can be introduced to automatically adjust resource allocation according to real-time demand. In addition, using edge computing to move part of the data processing and model training to edge nodes close to the data source can effectively reduce the burden on the core network, thereby improving the scalability and response speed of the overall system. The proposed method can be represented by a flow chart, as shown in Figure 7.
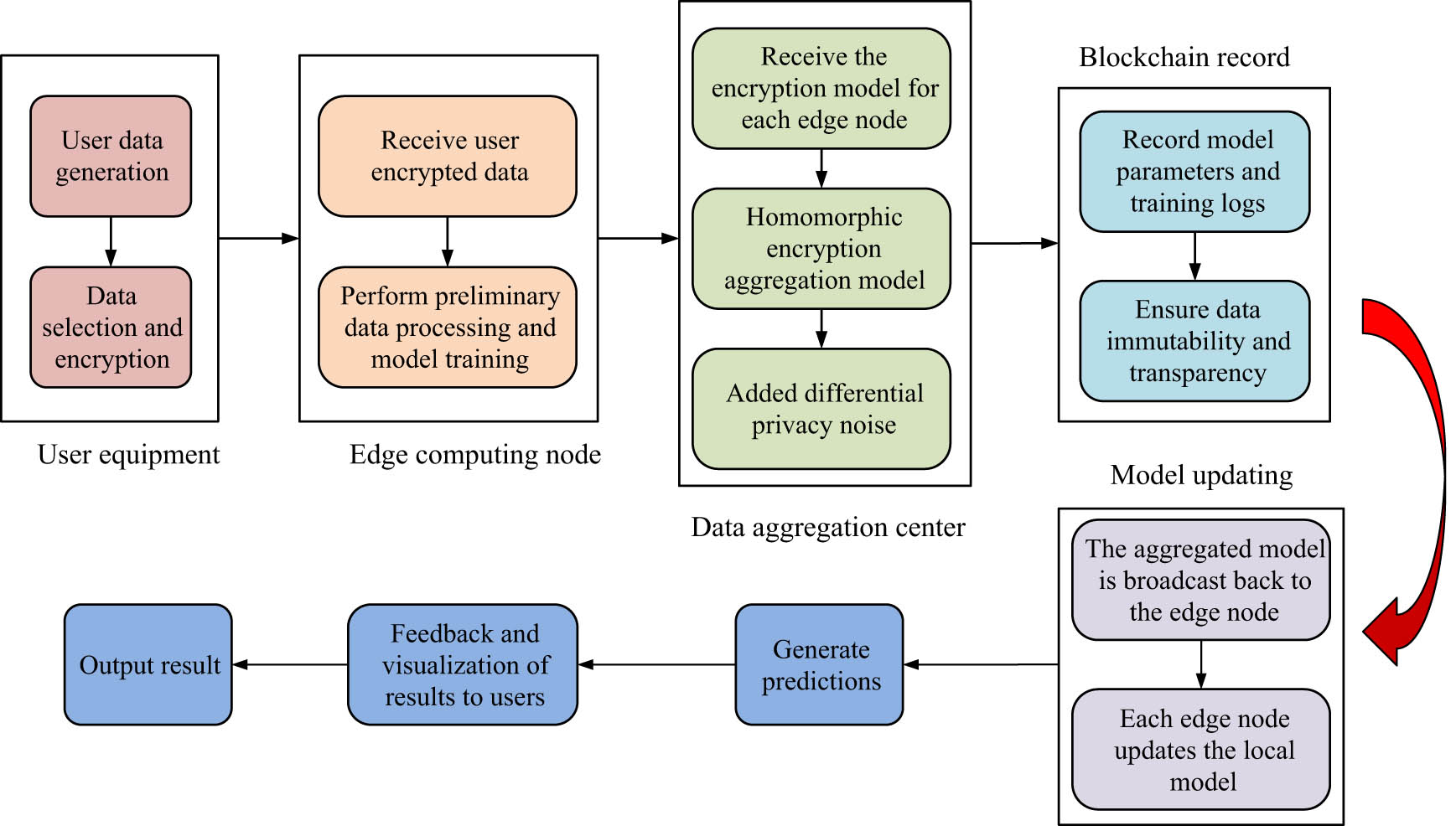
Flowchart of iot data protection based on improved FL technology.
In Figure 7, the proposed research architecture flow chart can be broken down into several key components and steps, each of which plays an important role in the overall process. First, the user device is the starting point for data generation, and the user generates data through various sensors or devices and chooses what needs to be shared for encryption to ensure privacy protection. The data is then transmitted to edge computing nodes, which receive the user’s encrypted data and do the initial data processing and model training locally, reducing dependence on the core network. The processed encryption models are then sent to a data aggregation center, which receives encryption models from multiple edge nodes, aggregates them using homomorphic encryption techniques, and adds DP noise to further enhance data security and privacy protection. Then, the data aggregation is recorded through the blockchain, ensuring transparency and immutability of the model parameters and training logs, which guarantees the integrity of the data. Then, the aggregated model is broadcast back to each edge node. In the model update stage, each edge node updates the local model according to the newly obtained model, so as to maintain the continuity of learning. Finally, the results feedback section generates predictive results and feeds those results back to the user, while providing relevant data visualization to ensure that the user can intuitively understand and use the information. This flowchart provides a complete description of the application architecture of an improved FL approach in an iot environment that promotes data privacy protection and computational efficiency.
The research method is also scalable and can be integrated with other security protocols, such as homomorphic encryption. Through homomorphic encryption, the user’s data can be calculated in the encrypted state, which means that the data can still participate in the model training without being decrypted, thus further enhancing the security and privacy protection of the data. In addition, combining homomorphic encryption with FL ensures that specific user data is not accessible to different parties even during data transmission and processing, thus meeting increasingly stringent data protection regulations and increasing user trust in the system.
3 Results
3.1 Performance testing of improved FL method
To verify the performance of the improved FL data protection system, the experiment sets the number of users to 20, 30, and 40, respectively. The accuracy of models with different privacy budget ranges is analyzed, as illustrated in Figure 8.
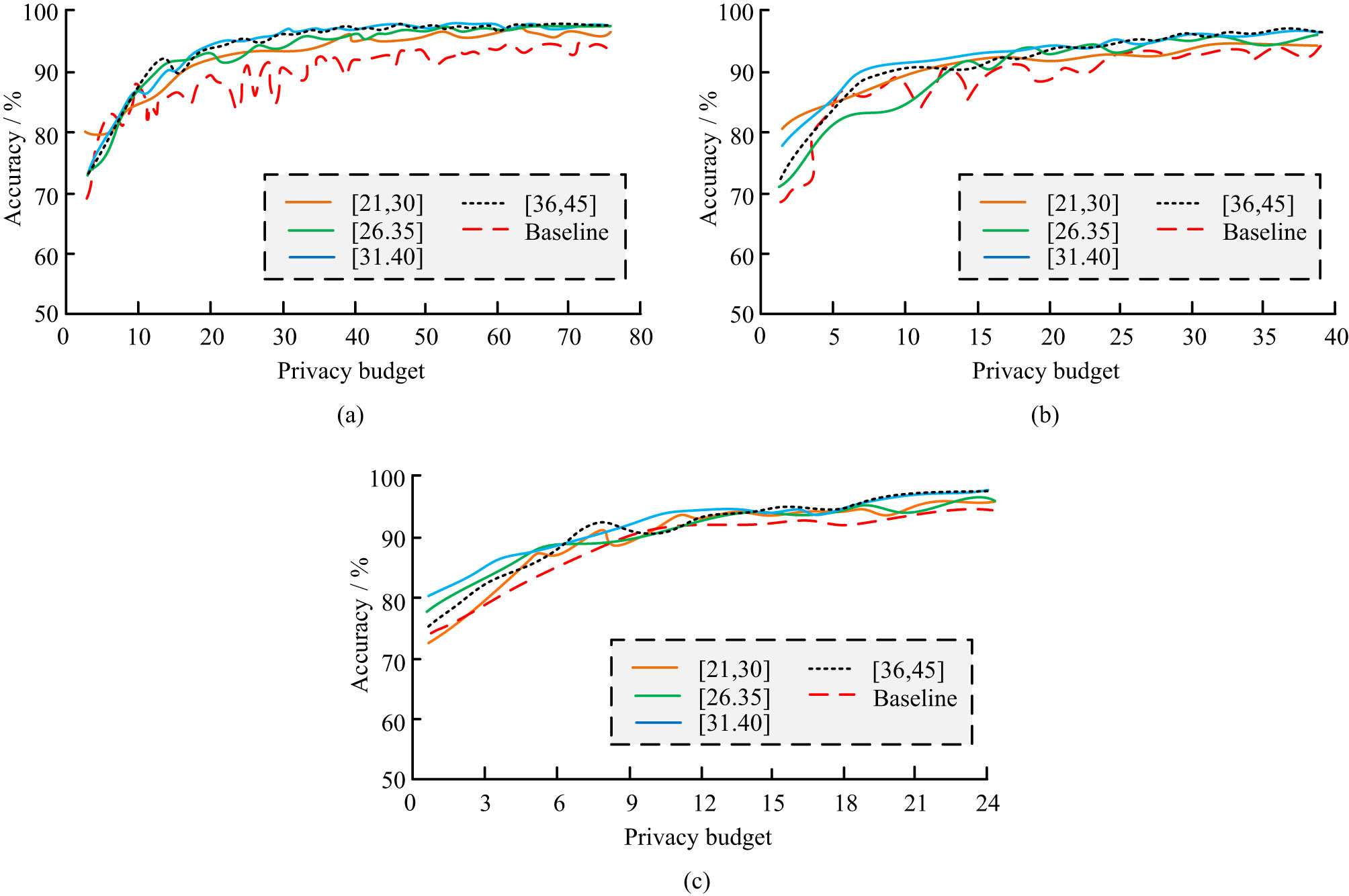
Model accuracy for different privacy budget ranges. (a) Number of users: 20. (b) Number of users: 30. (c) Number of users: 50.
In Figure 8(a), when the user was 20, the accuracy was basically higher than the baseline level. The accuracy of the model was about 98.04%. In Figure 8(b), the range of user budget values had a relatively small impact on accuracy when the user was 30. The accuracy within each range was higher than the limit level. In Figure 8(c), when the user increased to 40, the accuracy outweighed the baseline value when the privacy budget was small. According to the DP theory, a smaller privacy budget indicates more secure data privacy, but a reduction in privacy budget can affect the accuracy of the global model. When the user increased and the privacy budget decreased, the accuracy of the global model significantly decreased. The improved method proposed in the study allows users to randomly select their privacy budget, thus proving that the incentive mechanism can effectively improve the privacy protection performance of the model. In addition, the study sets the number of users to 40 and tests its accuracy by changing the values of the noise parameters. The accuracy under various noise parameters with privacy budgets of 35, 40, and 45 is shown in Figure 9.
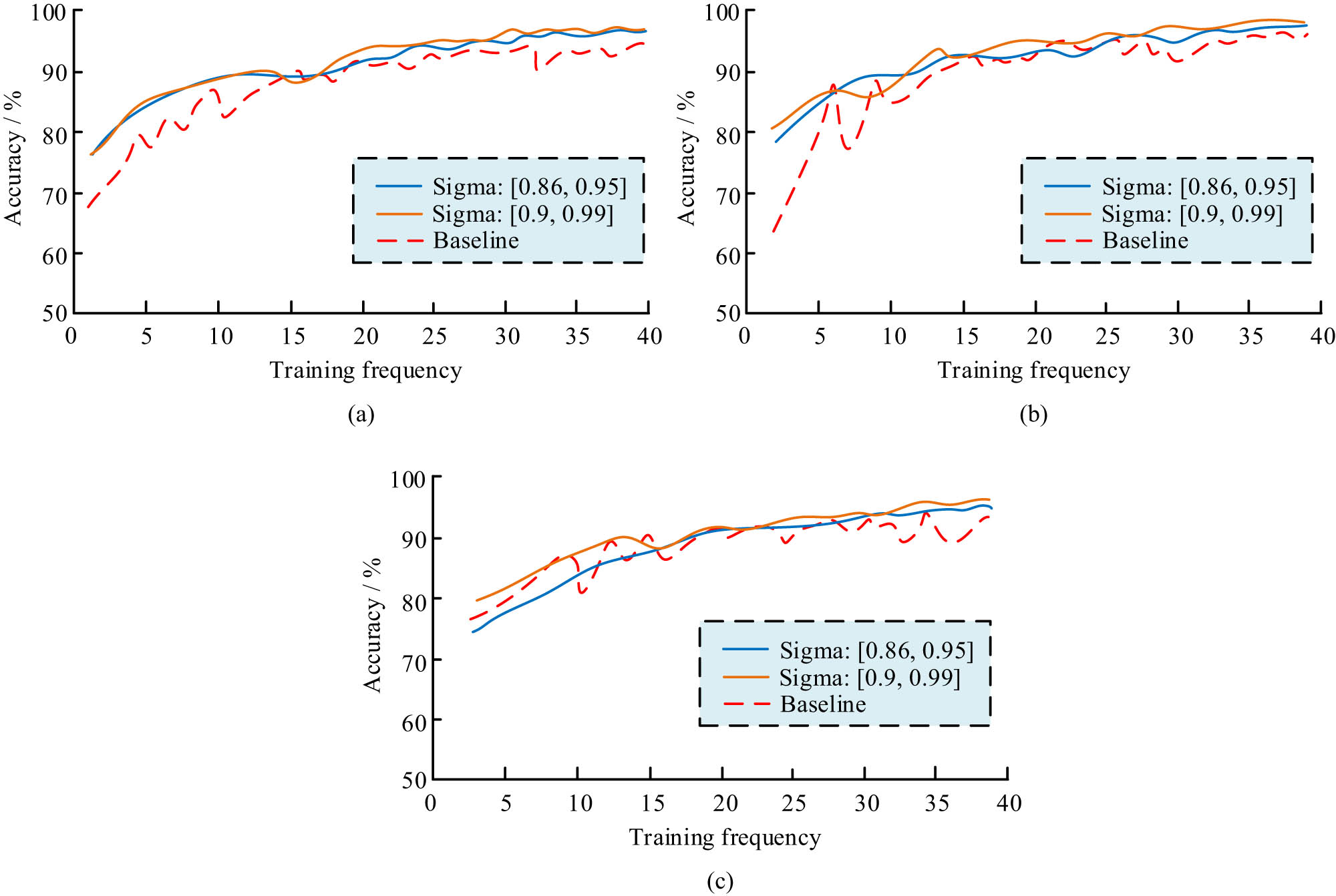
Model accuracy under different noise parameters. (a) Privacy budget 35. (b) Privacy budget 40. (c) Privacy budget 45.
In Figure 9(a), as the iteration increased to 40, the accuracy reached 96.98% for noise parameter values ranging from 0.86 to 0.95 and 0.9 to 0.99. At this point, the baseline value was 94.31%. In Figure 9(b), when the number of iterations reached 40, the baseline value was 1.76% lower in accuracy than the other two cases. In Figure 9(c), when the privacy budget value was 45, the final model accuracy exceeded the baseline value. Users generally choose smaller noise parameters to ensure the quality. The proposed incentive mechanism can support users to choose smaller noise parameters, thereby improving the performance. To further assess the performance of the proposed data protection system, the experiment first tests the time cost of each stage. Option 1, which requires confirmation of the signer, and Option 2, which requires open anonymity of the signer, are compared with the blockchain-based FL protection strategy proposed in the study. The time cost of the three schemes is shown in Figure 10.
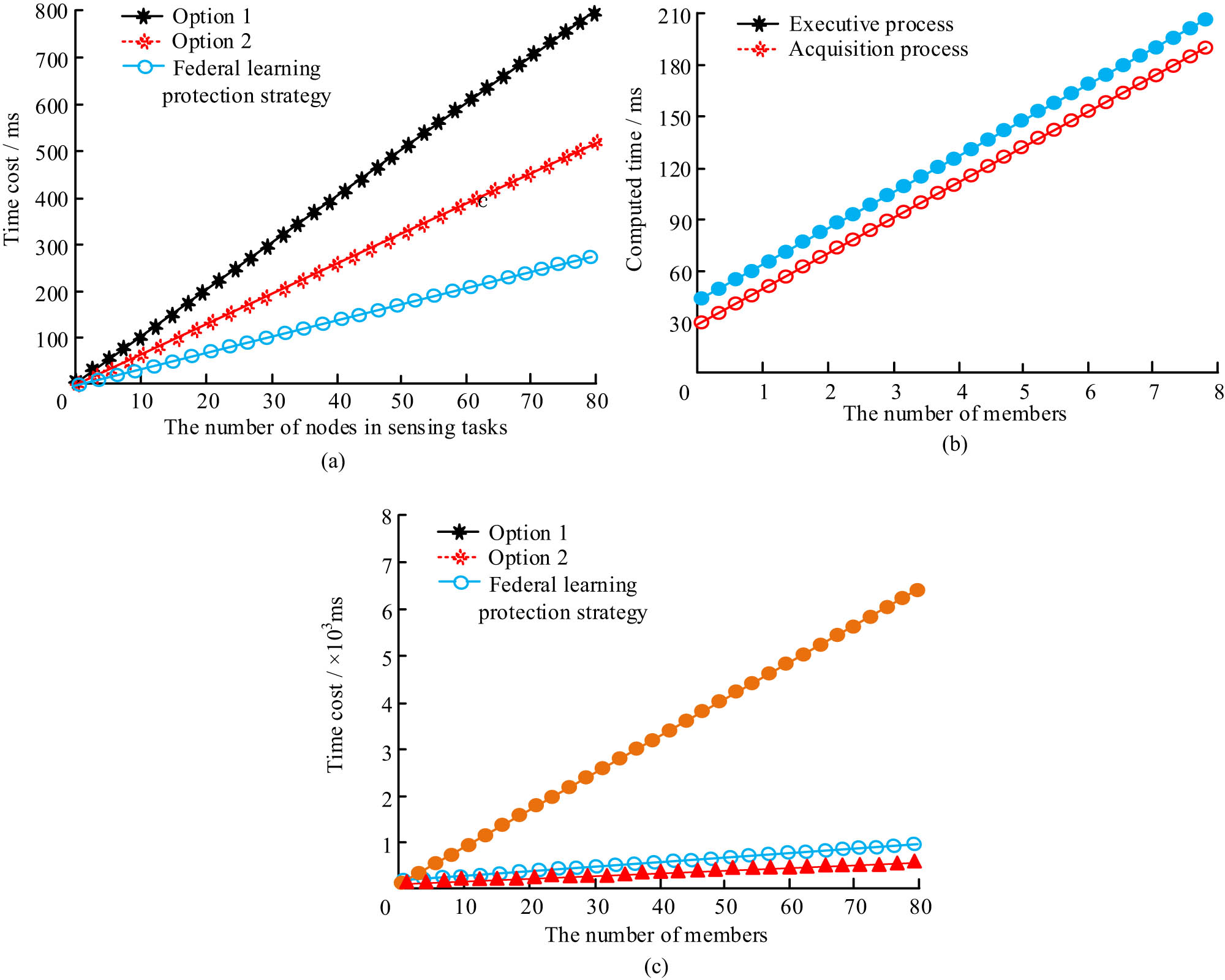
Time cost of each strategy. (a) Aggregation stage. (b) A nonymous license execution phase and acquisition phase. (c) Ring signature group.
From Figure 10(a), during the aggregation process and aggregation verification process, the blockchain-based FL protection strategy had a lower time cost than the other two strategies due to the lack of additional computational costs for signatures. When the number of nodes in the sensing task was 70, the time cost of the blockchain-based FL protection strategy was 260 ms, while the time costs of strategy 1 and strategy 2 were 720 ms and 450 ms, respectively. In the anonymous license execution and data acquisition process in Figure 10(b), as the number of members in the ring signature group increased, the time cost also increased. When the number of members in the ring signature increased to 80, the time cost of the execution phase was 210 ms, while the time cost of the data acquisition phase was 210 ms. In Figure 10(c), the time cost of strategy 1 was much higher than that of the blockchain-based FL protection strategy and strategy 2. The average time consumption of FL protection strategy was 200 ms less than that of strategy 2.
3.2 IoT data security protection experiment
In order to test the ciphertext and key storage performance during the encryption and decryption process of the model, data protection system 1 based on hybrid cloud platform and data protection system 2 based on single support vector machine are selected for comparison with the improved FL data protection system. The storage overhead and user response of the three systems are shown in Figure 11.
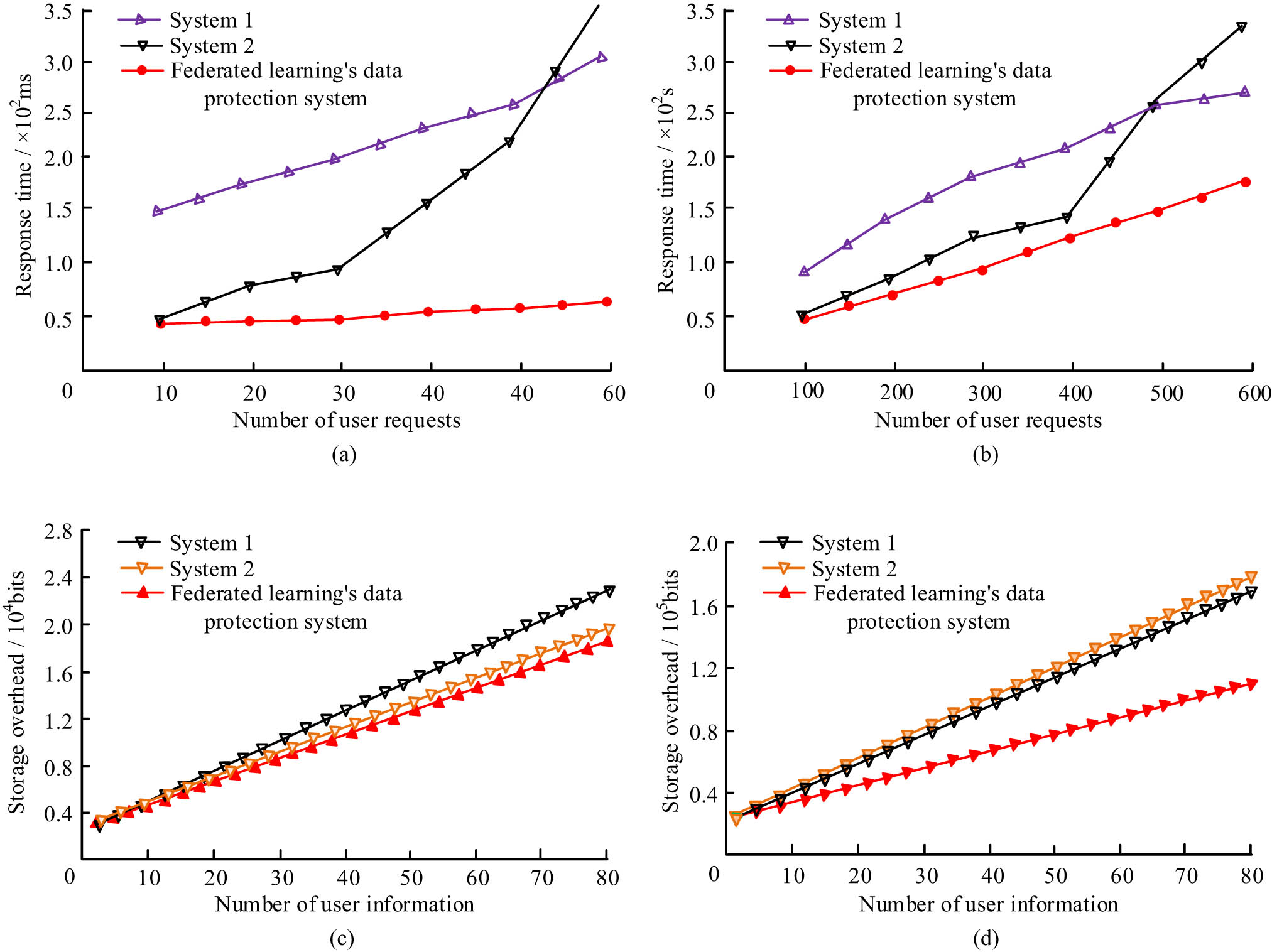
Storage overhead and user response of three systems. (a) Small scale con currency. (b) Large scale concurrency. (c) Cryptocurrency storage overhead. (c) Cryptocurrency storage overhead. (d) Key storage overhead.
In Figure 11(a), when the user request scale was small, the response time of the improved FL data protection system proposed in the study was relatively stable, fluctuating around 0.5 × 102 ms, with a maximum response time of only 0.65 × 102 ms. In Figure 11(b), when the user request was 500, the response time of the improved FL data protection system was about 1.4 × 102 ms, while the response times of system 1 and system 2 were both 2.6 × 102 ms. In Figure 11(c), when storing ciphertext, the storage length of system 1 was 1.8 × 104 bits when the number of user information was 60. The storage lengths of system 2 and the FL were relatively close, both less than 1.5 × 104 bits. In Figure 11(d), when the number of user information was 70, the key storage lengths of system 1, system 2, and the FL data protection system were 1.73 × 105 bits, 1.65 × 105 bits, and 1.06 × 105 bits, respectively. Regarding the response of IoT data access, experiments are conducted on a data protection system based on a hybrid cloud platform and an improved FL system. The comparison of response time between the two systems is displayed in Figure 12.
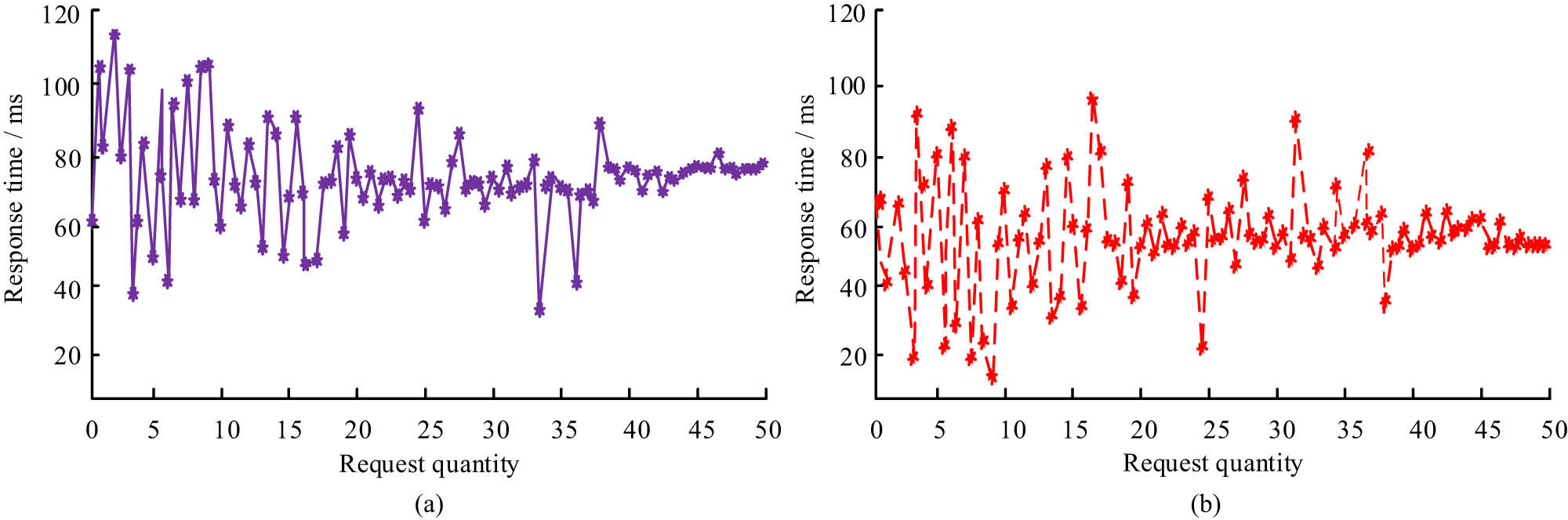
Response status of each system. (a) Multi state maintenance IoT data security system and (b) improving the IoT data security system for federated learning.
In Figure 12(a), the average response time of the data protection system based on single class support vector machine remained between 30 ms and 115 ms overall. When the number of requests was less than 20, the response time fluctuated greatly. As the number of visits gradually increased to 30, the system’s response time gradually stabilized, fluctuating around 75 ms. In Figure 12(b), the response time of the improved FL data protection system also varied greatly when the request was small. When the request was less than 20, the average response time fluctuated between 5 ms and 100 ms. When the request visit was 9, the average response time reached the minimum value of 5 ms. When the visit was 16, the average response time reached the maximum value. As the request increases, the request failures also increase, resulting in a decrease in the average response time. To further verify the performance of the data security protection system, the study evaluates the overall performance by comparing the communication traffic. The communication traffic of data terminals and fog nodes is shown in Figure 13.
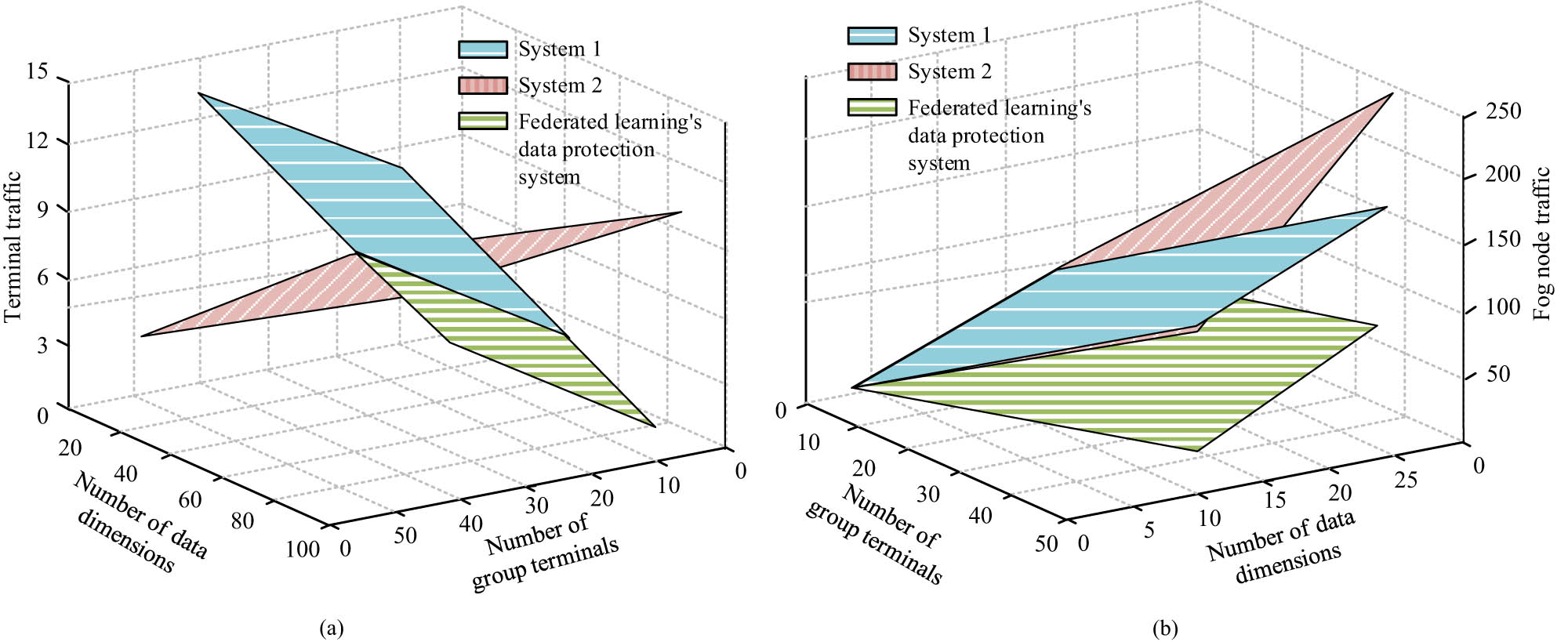
Comparison of communication traffic between data terminals and fog nodes. (a) Comparison of terminal communication traffic and (b) comparison of fog node traffic.
In Figure 13(a), when the data dimension was less than 32 and the data terminal group was less than 10, the terminal communication traffic of the improved FL data protection system was smaller than the other two systems. When the number of data terminal groups increased to 10 or more, the terminal communication traffic of the improved FL data protection system was greater than that of system 1 and system 2. Since the number of groups set in the experiment was not greater than 50, when the number of groups was exactly 50, the calculated communication traffic was 19,008 bits, which was within the acceptable range of the improved FL data protection system. In Figure 13(b), when the data dimension was less than 31, the fog nodes of system 1 and system 2 collected 3,328 pieces of data from each terminal and sent them to the data analysis module. The improved FL data protection system, due to the symmetric encryption, had a much smaller communication burden on fog nodes compared with system 1 and system 2. Therefore, the improved FL data protection system, after adopting symmetric encryption methods, has better computational efficiency for its data terminals and fog nodes than the other two systems. The communication traffic is slightly higher than other systems due to secret distribution within the group, but still within an acceptable range and will not affect the communication quality. The research further analyzes the security analysis and vulnerability assessment of the proposed method, and the results are shown in Table 1.
Comparison of security analysis and vulnerability assessment results
| Evaluation index | Improved FL methods | Traditional centralized model | Evaluation index | Improved FL methods | Traditional centralized model |
|---|---|---|---|---|---|
| Data breach risk | 0.015 | 0.100 | Compliance | 0.95 | 0.70 |
| Anti-aggression | 0.90 | 0.60 | User trust | 0.85 | 0.50 |
| Encryption efficiency | 0.70 | 0.95 | Overall system reliability | 0.80 | 0.60 |
Table 1 shows how the improved FL approach compares to the traditional centralized model in terms of security analysis and vulnerability assessment. By comparing the risk of data breach, the risk of the improved FL method is only 1.5%, which is significantly lower than the traditional model of 10%, indicating that it has a clear advantage in data security. In terms of resistance to aggression, the improved FL method has a 90 percent ability to resist external attacks, which is significantly higher than the traditional model’s 60 percent. Although the traditional model is more efficient (95%), the improved FL method still maintains the level of 70%. In terms of compliance, the improved method surpassed the traditional model’s compliance rate of 70% with 95%, showing its superiority in privacy protection and laws and regulations. In terms of user trust, the improved FL method scored 85%, which is also much higher than the traditional model’s 50%. Finally, the overall system reliability shows that the improved method (80%) is superior to the traditional method (60%), which emphasizes the security and reliability advantages of the improved FL method in many aspects.
According to the aforementioned experimental results, the research method has high feasibility for deployment and evaluation in the real world. The experimental results show that the method has excellent performance in response time, model accuracy, and privacy protection, which lays a solid foundation for practical application. Second, by implementing small-scale pilot projects, their effectiveness can be gradually verified in real environments, reducing risks in full deployment. In addition, with the development of new technologies such as 5G, the combination of edge computing and FL can meet the real-time data processing needs and enhance the adaptability of application scenarios. At the same time, in the face of the growing demand for data privacy protection, this method can effectively ensure the security of user information, improve legal compliance, and increase user acceptance. Finally, cooperation with related industries will promote the organic integration of technology and practical needs, which will promote the wide application of the method in intelligent transportation, medical, and intelligent manufacturing.
4 Discussion and conclusion
The IoT, together with emerging industries such as cloud computing, blockchain, AI, and virtual reality, is driving the development of the digital economy and digital society. In order to provide more reliable protection for user privacy in IoT data collection and sharing, privacy-preserving data aggregation technology was explored. Then, the FL method was improved based on function encryption and blockchain. At the same time, decentralized functions were used to encrypt the privacy of the training model, and a DP incentive mechanism was added to improve user participation and model accuracy. The experimental results showed that when storing ciphertext, the storage length of system 1 was 1.8 × 104 bits when the number of user information was 60. The storage length of system 2 and the FL was relatively close, both less than 1.5 × 104 bits. The average response time of the data protection system on the basis of single-class support vector machine remained between 30 and 115 ms. When the number of request accesses was less than 20, the average response time of the improved FL data protection system fluctuated between 5 and 100 ms. The proposed improved FL method can effectively enhance the security of IoT data and achieve reliable protection of user information. Moreover, this method also has application potential in many specific fields. In smart agriculture, decentralized FL enables secure co-construction and analysis of sensor data to optimize crop growing conditions and increase yields. Second, in smart city management, the technology can integrate traffic flow and environmental monitoring data in real time, assist decision makers to effectively plan resources, and improve urban operation efficiency. In addition, in the field of healthcare, decentralized solutions can guarantee the privacy of patient data while supporting cross-institutional data sharing, enabling more accurate diagnosis and health management. However, the improved FL aggregation scheme proposed in the study requires encrypting various parameters in the model. Encrypting and decrypting a large number of parameters will significantly increase the computational cost of the model, affecting the multi round iteration process. Future research will further enhance the repetitive encryption and decryption process to improve the aggregation efficiency.
-
Funding information: The author states no funding involved.
-
Author contributions: Gang Wang: conceptualization, data curation, formal analysis, funding acquisition, investigation, methodology, project administration, resources, software, supervision, validation, visualization, writing – original draft, writing – review and editing. The author has accepted responsibility for the entire content of this manuscript and approved its submission.
-
Conflict of interest: The author states no conflict of interest.
-
Data availability statement: The datasets generated during and/or analyzed during the current study are available from the corresponding author on reasonable request.
References
[1] Sadhu PK, Yanambaka VP, Abdelgawad A. Internet of things: security and solutions survey. Sensors. 2022;22(19):7433–83.10.3390/s22197433Search in Google Scholar PubMed PubMed Central
[2] Ahmad MT, Astuti SI. Conceptual design impacts in new normal era: the use of artificial intelligence (ai) and internet of things (iot) (Case studies: class room and restaurant). Acta Inform Malaysia. 2022;6(2):39–42. 10.26480/aim.02.2022.39.42.Search in Google Scholar
[3] Zhang K, Tian J, Xiao H, Zhao Y, Zhao W, Chen J. A numerical splitting and adaptive privacy budget-allocation-based LDP mechanism for privacy preservation in blockchain-powered IoT. IEEE Internet Things J. 2022;10(8):6733–41.10.1109/JIOT.2022.3145845Search in Google Scholar
[4] Al-Turjman F, Zahmatkesh H, Shahroze R. An overview of security and privacy in smart cities’ IoT communications. Trans Emerg Telecommun Technol. 2022;33(3):3677–96.10.1002/ett.3677Search in Google Scholar
[5] Deng Y, Lyu F, Ren J, Chen YC, Yang P, Zhou Y, et al. Improving federated learning with quality-aware user incentive and auto-weighted model aggregation. IEEE Trans Parallel Distrib Syst. 2022;33(12):4515–29.10.1109/TPDS.2022.3195207Search in Google Scholar
[6] Polap D, Woźniak M. A hybridization of distributed policy and heuristic augmentation for improving federated learning approach. Neural Network. 2022;146:130–40.10.1016/j.neunet.2021.11.018Search in Google Scholar PubMed
[7] Geng DQ, He HW, Lan XC, Liu C. Bearing fault diagnosis based on improved federated learning algorithm. Computing. 2022;104:1–19.10.1007/s00607-021-01019-4Search in Google Scholar
[8] Li W, Chen J, Wang Z, Shen Z, Ma C, Cui X. Ifl-gan: Improved federated learning generative adversarial network with maximum mean discrepancy model aggregation. IEEE Trans Neural Network Learn Syst. 2022;34(12):10502–15.10.1109/TNNLS.2022.3167482Search in Google Scholar PubMed
[9] Rashid MM, Khan SU, Eusufzai F, Redwan MA, Sabuj SR, Elsharief M. A federated learning-based approach for improving intrusion detection in industrial internet of things networks. Network. 2023;3(1):158–79.10.3390/network3010008Search in Google Scholar
[10] Shahid J, Ahmad R, Kiani AK, Ahmad T, Saeed S, Almuhaideb AM. Data protection and privacy of the internet of healthcare things (IoHTs). Appl Sci. 2022;12(4):1927–48.10.3390/app12041927Search in Google Scholar
[11] Yu F, Shen H, Yu Q, Kong X, Sharma PK, Cai S. Privacy protection of medical data based on multi-scroll memristive Hopfield neural network. IEEE Trans Network Sci Eng. 2022;10(2):845–58.10.1109/TNSE.2022.3223930Search in Google Scholar
[12] Ren Y, Liu W, Liu A, Wang T, Li A. A privacy-protected intelligent crowdsourcing application of IoT based on the reinforcement learning. Future Gener Comput Syst. 2022;127:56–69.10.1016/j.future.2021.09.003Search in Google Scholar
[13] Rupa C, Greeshmanth P, Shah MA. Novel secure data protection scheme using Martino homomorphic encryption. J Cloud Comput. 2023;12:47–58.10.1186/s13677-023-00425-7Search in Google Scholar
[14] Li T, Wang H, He D, Yu J. Blockchain-based privacy-preserving and rewarding private data sharing for IoT. IEEE Internet Things J. 2022;9(16):15138–49.10.1109/JIOT.2022.3147925Search in Google Scholar
[15] Issa W, Moustafa N, Turnbull B, Sohrabi N, Tari Z. Blockchain-based federated learning for securing internet of things: A comprehensive survey. ACM Comput Surv. 2023;55(9):1–43.10.1145/3560816Search in Google Scholar
[16] Ioannou I, Nagaradjane P, Angin P, Balasubramanian P, Kavitha KJ, Murugan P, et al. GEMLIDS-MIOT: a green effective machine learning intrusion detection system based on Federated Learning for Medical IoT network security hardening. Comput Commun. 2024;218:209–39.10.1016/j.comcom.2024.02.023Search in Google Scholar
[17] Li H, Zhou S, Yuan B, Zhang M. Optimizing intelligent edge computing resource scheduling based on federated learning. J Knowl Learn Sci Technol. 2024;3(3):235–60.10.60087/jklst.vol3.n3.p.235-260Search in Google Scholar
[18] Qahtan S, Sharif KY, Zaidan AA, AlSattar HA, Albahri OS, Zaidan BB, et al. Novel multi security and privacy benchmarking framework for blockchain-based IoT healthcare industry 4.0 systems. IEEE Trans Ind Inform. 2022;18(9):6415–23.10.1109/TII.2022.3143619Search in Google Scholar
[19] Chen Y, Sun J, Yang Y, Li T, Niu X, Zhou H. PSSPR: a source location privacy protection scheme based on sector phantom routing in WSNs. Int J Intell Syst. 2022;37(2):1204–21.10.1002/int.22666Search in Google Scholar
[20] Mehdi G, Hooman H, Liu S, Peyman P, Arif R. Data mining techniques for web mining: a survey. Artif Intell Appl. 2022;1(1):3–10.10.47852/bonviewAIA2202290Search in Google Scholar
[21] Damanik HA. Securing data network for growing business vpn architectures cellular network connectivity. Acta Inform Malaysia. 2022;6(1):1–6. 10.26480/aim.01.2022.01.06.Search in Google Scholar
© 2025 the author(s), published by De Gruyter
This work is licensed under the Creative Commons Attribution 4.0 International License.
Articles in the same Issue
- Research Articles
- Generalized (ψ,φ)-contraction to investigate Volterra integral inclusions and fractal fractional PDEs in super-metric space with numerical experiments
- Solitons in ultrasound imaging: Exploring applications and enhancements via the Westervelt equation
- Stochastic improved Simpson for solving nonlinear fractional-order systems using product integration rules
- Exploring dynamical features like bifurcation assessment, sensitivity visualization, and solitary wave solutions of the integrable Akbota equation
- Research on surface defect detection method and optimization of paper-plastic composite bag based on improved combined segmentation algorithm
- Impact the sulphur content in Iraqi crude oil on the mechanical properties and corrosion behaviour of carbon steel in various types of API 5L pipelines and ASTM 106 grade B
- Unravelling quiescent optical solitons: An exploration of the complex Ginzburg–Landau equation with nonlinear chromatic dispersion and self-phase modulation
- Perturbation-iteration approach for fractional-order logistic differential equations
- Variational formulations for the Euler and Navier–Stokes systems in fluid mechanics and related models
- Rotor response to unbalanced load and system performance considering variable bearing profile
- DeepFowl: Disease prediction from chicken excreta images using deep learning
- Channel flow of Ellis fluid due to cilia motion
- A case study of fractional-order varicella virus model to nonlinear dynamics strategy for control and prevalence
- Multi-point estimation weldment recognition and estimation of pose with data-driven robotics design
- Analysis of Hall current and nonuniform heating effects on magneto-convection between vertically aligned plates under the influence of electric and magnetic fields
- A comparative study on residual power series method and differential transform method through the time-fractional telegraph equation
- Insights from the nonlinear Schrödinger–Hirota equation with chromatic dispersion: Dynamics in fiber–optic communication
- Mathematical analysis of Jeffrey ferrofluid on stretching surface with the Darcy–Forchheimer model
- Exploring the interaction between lump, stripe and double-stripe, and periodic wave solutions of the Konopelchenko–Dubrovsky–Kaup–Kupershmidt system
- Computational investigation of tuberculosis and HIV/AIDS co-infection in fuzzy environment
- Signature verification by geometry and image processing
- Theoretical and numerical approach for quantifying sensitivity to system parameters of nonlinear systems
- Chaotic behaviors, stability, and solitary wave propagations of M-fractional LWE equation in magneto-electro-elastic circular rod
- Dynamic analysis and optimization of syphilis spread: Simulations, integrating treatment and public health interventions
- Visco-thermoelastic rectangular plate under uniform loading: A study of deflection
- Threshold dynamics and optimal control of an epidemiological smoking model
- Numerical computational model for an unsteady hybrid nanofluid flow in a porous medium past an MHD rotating sheet
- Regression prediction model of fabric brightness based on light and shadow reconstruction of layered images
- Dynamics and prevention of gemini virus infection in red chili crops studied with generalized fractional operator: Analysis and modeling
- Qualitative analysis on existence and stability of nonlinear fractional dynamic equations on time scales
- Fractional-order super-twisting sliding mode active disturbance rejection control for electro-hydraulic position servo systems
- Analytical exploration and parametric insights into optical solitons in magneto-optic waveguides: Advances in nonlinear dynamics for applied sciences
- Bifurcation dynamics and optical soliton structures in the nonlinear Schrödinger–Bopp–Podolsky system
- Review Article
- Haar wavelet collocation method for existence and numerical solutions of fourth-order integro-differential equations with bounded coefficients
- Special Issue: Nonlinear Analysis and Design of Communication Networks for IoT Applications - Part II
- Silicon-based all-optical wavelength converter for on-chip optical interconnection
- Research on a path-tracking control system of unmanned rollers based on an optimization algorithm and real-time feedback
- Analysis of the sports action recognition model based on the LSTM recurrent neural network
- Industrial robot trajectory error compensation based on enhanced transfer convolutional neural networks
- Research on IoT network performance prediction model of power grid warehouse based on nonlinear GA-BP neural network
- Interactive recommendation of social network communication between cities based on GNN and user preferences
- Application of improved P-BEM in time varying channel prediction in 5G high-speed mobile communication system
- Construction of a BIM smart building collaborative design model combining the Internet of Things
- Optimizing malicious website prediction: An advanced XGBoost-based machine learning model
- Economic operation analysis of the power grid combining communication network and distributed optimization algorithm
- Sports video temporal action detection technology based on an improved MSST algorithm
- Internet of things data security and privacy protection based on improved federated learning
- Enterprise power emission reduction technology based on the LSTM–SVM model
- Construction of multi-style face models based on artistic image generation algorithms
- Research and application of interactive digital twin monitoring system for photovoltaic power station based on global perception
- Special Issue: Decision and Control in Nonlinear Systems - Part II
- Animation video frame prediction based on ConvGRU fine-grained synthesis flow
- Application of GGNN inference propagation model for martial art intensity evaluation
- Benefit evaluation of building energy-saving renovation projects based on BWM weighting method
- Deep neural network application in real-time economic dispatch and frequency control of microgrids
- Real-time force/position control of soft growing robots: A data-driven model predictive approach
- Mechanical product design and manufacturing system based on CNN and server optimization algorithm
- Application of finite element analysis in the formal analysis of ancient architectural plaque section
- Research on territorial spatial planning based on data mining and geographic information visualization
- Fault diagnosis of agricultural sprinkler irrigation machinery equipment based on machine vision
- Closure technology of large span steel truss arch bridge with temporarily fixed edge supports
- Intelligent accounting question-answering robot based on a large language model and knowledge graph
- Analysis of manufacturing and retailer blockchain decision based on resource recyclability
- Flexible manufacturing workshop mechanical processing and product scheduling algorithm based on MES
- Exploration of indoor environment perception and design model based on virtual reality technology
- Tennis automatic ball-picking robot based on image object detection and positioning technology
- A new CNN deep learning model for computer-intelligent color matching
- Design of AR-based general computer technology experiment demonstration platform
- Indoor environment monitoring method based on the fusion of audio recognition and video patrol features
- Health condition prediction method of the computer numerical control machine tool parts by ensembling digital twins and improved LSTM networks
- Establishment of a green degree evaluation model for wall materials based on lifecycle
- Quantitative evaluation of college music teaching pronunciation based on nonlinear feature extraction
- Multi-index nonlinear robust virtual synchronous generator control method for microgrid inverters
- Manufacturing engineering production line scheduling management technology integrating availability constraints and heuristic rules
- Analysis of digital intelligent financial audit system based on improved BiLSTM neural network
- Attention community discovery model applied to complex network information analysis
- A neural collaborative filtering recommendation algorithm based on attention mechanism and contrastive learning
- Rehabilitation training method for motor dysfunction based on video stream matching
- Research on façade design for cold-region buildings based on artificial neural networks and parametric modeling techniques
- Intelligent implementation of muscle strain identification algorithm in Mi health exercise induced waist muscle strain
- Optimization design of urban rainwater and flood drainage system based on SWMM
- Improved GA for construction progress and cost management in construction projects
- Evaluation and prediction of SVM parameters in engineering cost based on random forest hybrid optimization
- Museum intelligent warning system based on wireless data module
- Optimization design and research of mechatronics based on torque motor control algorithm
- Special Issue: Nonlinear Engineering’s significance in Materials Science
- Experimental research on the degradation of chemical industrial wastewater by combined hydrodynamic cavitation based on nonlinear dynamic model
- Study on low-cycle fatigue life of nickel-based superalloy GH4586 at various temperatures
- Some results of solutions to neutral stochastic functional operator-differential equations
- Ultrasonic cavitation did not occur in high-pressure CO2 liquid
- Research on the performance of a novel type of cemented filler material for coal mine opening and filling
- Testing of recycled fine aggregate concrete’s mechanical properties using recycled fine aggregate concrete and research on technology for highway construction
- A modified fuzzy TOPSIS approach for the condition assessment of existing bridges
- Nonlinear structural and vibration analysis of straddle monorail pantograph under random excitations
- Achieving high efficiency and stability in blue OLEDs: Role of wide-gap hosts and emitter interactions
- Construction of teaching quality evaluation model of online dance teaching course based on improved PSO-BPNN
- Enhanced electrical conductivity and electromagnetic shielding properties of multi-component polymer/graphite nanocomposites prepared by solid-state shear milling
- Optimization of thermal characteristics of buried composite phase-change energy storage walls based on nonlinear engineering methods
- A higher-performance big data-based movie recommendation system
- Nonlinear impact of minimum wage on labor employment in China
- Nonlinear comprehensive evaluation method based on information entropy and discrimination optimization
- Application of numerical calculation methods in stability analysis of pile foundation under complex foundation conditions
- Research on the contribution of shale gas development and utilization in Sichuan Province to carbon peak based on the PSA process
- Characteristics of tight oil reservoirs and their impact on seepage flow from a nonlinear engineering perspective
- Nonlinear deformation decomposition and mode identification of plane structures via orthogonal theory
- Numerical simulation of damage mechanism in rock with cracks impacted by self-excited pulsed jet based on SPH-FEM coupling method: The perspective of nonlinear engineering and materials science
- Cross-scale modeling and collaborative optimization of ethanol-catalyzed coupling to produce C4 olefins: Nonlinear modeling and collaborative optimization strategies
- Unequal width T-node stress concentration factor analysis of stiffened rectangular steel pipe concrete
- Special Issue: Advances in Nonlinear Dynamics and Control
- Development of a cognitive blood glucose–insulin control strategy design for a nonlinear diabetic patient model
- Big data-based optimized model of building design in the context of rural revitalization
- Multi-UAV assisted air-to-ground data collection for ground sensors with unknown positions
- Design of urban and rural elderly care public areas integrating person-environment fit theory
- Application of lossless signal transmission technology in piano timbre recognition
- Application of improved GA in optimizing rural tourism routes
- Architectural animation generation system based on AL-GAN algorithm
- Advanced sentiment analysis in online shopping: Implementing LSTM models analyzing E-commerce user sentiments
- Intelligent recommendation algorithm for piano tracks based on the CNN model
- Visualization of large-scale user association feature data based on a nonlinear dimensionality reduction method
- Low-carbon economic optimization of microgrid clusters based on an energy interaction operation strategy
- Optimization effect of video data extraction and search based on Faster-RCNN hybrid model on intelligent information systems
- Construction of image segmentation system combining TC and swarm intelligence algorithm
- Particle swarm optimization and fuzzy C-means clustering algorithm for the adhesive layer defect detection
- Optimization of student learning status by instructional intervention decision-making techniques incorporating reinforcement learning
- Fuzzy model-based stabilization control and state estimation of nonlinear systems
- Optimization of distribution network scheduling based on BA and photovoltaic uncertainty
- Tai Chi movement segmentation and recognition on the grounds of multi-sensor data fusion and the DBSCAN algorithm
- Special Issue: Dynamic Engineering and Control Methods for the Nonlinear Systems - Part III
- Generalized numerical RKM method for solving sixth-order fractional partial differential equations
Articles in the same Issue
- Research Articles
- Generalized (ψ,φ)-contraction to investigate Volterra integral inclusions and fractal fractional PDEs in super-metric space with numerical experiments
- Solitons in ultrasound imaging: Exploring applications and enhancements via the Westervelt equation
- Stochastic improved Simpson for solving nonlinear fractional-order systems using product integration rules
- Exploring dynamical features like bifurcation assessment, sensitivity visualization, and solitary wave solutions of the integrable Akbota equation
- Research on surface defect detection method and optimization of paper-plastic composite bag based on improved combined segmentation algorithm
- Impact the sulphur content in Iraqi crude oil on the mechanical properties and corrosion behaviour of carbon steel in various types of API 5L pipelines and ASTM 106 grade B
- Unravelling quiescent optical solitons: An exploration of the complex Ginzburg–Landau equation with nonlinear chromatic dispersion and self-phase modulation
- Perturbation-iteration approach for fractional-order logistic differential equations
- Variational formulations for the Euler and Navier–Stokes systems in fluid mechanics and related models
- Rotor response to unbalanced load and system performance considering variable bearing profile
- DeepFowl: Disease prediction from chicken excreta images using deep learning
- Channel flow of Ellis fluid due to cilia motion
- A case study of fractional-order varicella virus model to nonlinear dynamics strategy for control and prevalence
- Multi-point estimation weldment recognition and estimation of pose with data-driven robotics design
- Analysis of Hall current and nonuniform heating effects on magneto-convection between vertically aligned plates under the influence of electric and magnetic fields
- A comparative study on residual power series method and differential transform method through the time-fractional telegraph equation
- Insights from the nonlinear Schrödinger–Hirota equation with chromatic dispersion: Dynamics in fiber–optic communication
- Mathematical analysis of Jeffrey ferrofluid on stretching surface with the Darcy–Forchheimer model
- Exploring the interaction between lump, stripe and double-stripe, and periodic wave solutions of the Konopelchenko–Dubrovsky–Kaup–Kupershmidt system
- Computational investigation of tuberculosis and HIV/AIDS co-infection in fuzzy environment
- Signature verification by geometry and image processing
- Theoretical and numerical approach for quantifying sensitivity to system parameters of nonlinear systems
- Chaotic behaviors, stability, and solitary wave propagations of M-fractional LWE equation in magneto-electro-elastic circular rod
- Dynamic analysis and optimization of syphilis spread: Simulations, integrating treatment and public health interventions
- Visco-thermoelastic rectangular plate under uniform loading: A study of deflection
- Threshold dynamics and optimal control of an epidemiological smoking model
- Numerical computational model for an unsteady hybrid nanofluid flow in a porous medium past an MHD rotating sheet
- Regression prediction model of fabric brightness based on light and shadow reconstruction of layered images
- Dynamics and prevention of gemini virus infection in red chili crops studied with generalized fractional operator: Analysis and modeling
- Qualitative analysis on existence and stability of nonlinear fractional dynamic equations on time scales
- Fractional-order super-twisting sliding mode active disturbance rejection control for electro-hydraulic position servo systems
- Analytical exploration and parametric insights into optical solitons in magneto-optic waveguides: Advances in nonlinear dynamics for applied sciences
- Bifurcation dynamics and optical soliton structures in the nonlinear Schrödinger–Bopp–Podolsky system
- Review Article
- Haar wavelet collocation method for existence and numerical solutions of fourth-order integro-differential equations with bounded coefficients
- Special Issue: Nonlinear Analysis and Design of Communication Networks for IoT Applications - Part II
- Silicon-based all-optical wavelength converter for on-chip optical interconnection
- Research on a path-tracking control system of unmanned rollers based on an optimization algorithm and real-time feedback
- Analysis of the sports action recognition model based on the LSTM recurrent neural network
- Industrial robot trajectory error compensation based on enhanced transfer convolutional neural networks
- Research on IoT network performance prediction model of power grid warehouse based on nonlinear GA-BP neural network
- Interactive recommendation of social network communication between cities based on GNN and user preferences
- Application of improved P-BEM in time varying channel prediction in 5G high-speed mobile communication system
- Construction of a BIM smart building collaborative design model combining the Internet of Things
- Optimizing malicious website prediction: An advanced XGBoost-based machine learning model
- Economic operation analysis of the power grid combining communication network and distributed optimization algorithm
- Sports video temporal action detection technology based on an improved MSST algorithm
- Internet of things data security and privacy protection based on improved federated learning
- Enterprise power emission reduction technology based on the LSTM–SVM model
- Construction of multi-style face models based on artistic image generation algorithms
- Research and application of interactive digital twin monitoring system for photovoltaic power station based on global perception
- Special Issue: Decision and Control in Nonlinear Systems - Part II
- Animation video frame prediction based on ConvGRU fine-grained synthesis flow
- Application of GGNN inference propagation model for martial art intensity evaluation
- Benefit evaluation of building energy-saving renovation projects based on BWM weighting method
- Deep neural network application in real-time economic dispatch and frequency control of microgrids
- Real-time force/position control of soft growing robots: A data-driven model predictive approach
- Mechanical product design and manufacturing system based on CNN and server optimization algorithm
- Application of finite element analysis in the formal analysis of ancient architectural plaque section
- Research on territorial spatial planning based on data mining and geographic information visualization
- Fault diagnosis of agricultural sprinkler irrigation machinery equipment based on machine vision
- Closure technology of large span steel truss arch bridge with temporarily fixed edge supports
- Intelligent accounting question-answering robot based on a large language model and knowledge graph
- Analysis of manufacturing and retailer blockchain decision based on resource recyclability
- Flexible manufacturing workshop mechanical processing and product scheduling algorithm based on MES
- Exploration of indoor environment perception and design model based on virtual reality technology
- Tennis automatic ball-picking robot based on image object detection and positioning technology
- A new CNN deep learning model for computer-intelligent color matching
- Design of AR-based general computer technology experiment demonstration platform
- Indoor environment monitoring method based on the fusion of audio recognition and video patrol features
- Health condition prediction method of the computer numerical control machine tool parts by ensembling digital twins and improved LSTM networks
- Establishment of a green degree evaluation model for wall materials based on lifecycle
- Quantitative evaluation of college music teaching pronunciation based on nonlinear feature extraction
- Multi-index nonlinear robust virtual synchronous generator control method for microgrid inverters
- Manufacturing engineering production line scheduling management technology integrating availability constraints and heuristic rules
- Analysis of digital intelligent financial audit system based on improved BiLSTM neural network
- Attention community discovery model applied to complex network information analysis
- A neural collaborative filtering recommendation algorithm based on attention mechanism and contrastive learning
- Rehabilitation training method for motor dysfunction based on video stream matching
- Research on façade design for cold-region buildings based on artificial neural networks and parametric modeling techniques
- Intelligent implementation of muscle strain identification algorithm in Mi health exercise induced waist muscle strain
- Optimization design of urban rainwater and flood drainage system based on SWMM
- Improved GA for construction progress and cost management in construction projects
- Evaluation and prediction of SVM parameters in engineering cost based on random forest hybrid optimization
- Museum intelligent warning system based on wireless data module
- Optimization design and research of mechatronics based on torque motor control algorithm
- Special Issue: Nonlinear Engineering’s significance in Materials Science
- Experimental research on the degradation of chemical industrial wastewater by combined hydrodynamic cavitation based on nonlinear dynamic model
- Study on low-cycle fatigue life of nickel-based superalloy GH4586 at various temperatures
- Some results of solutions to neutral stochastic functional operator-differential equations
- Ultrasonic cavitation did not occur in high-pressure CO2 liquid
- Research on the performance of a novel type of cemented filler material for coal mine opening and filling
- Testing of recycled fine aggregate concrete’s mechanical properties using recycled fine aggregate concrete and research on technology for highway construction
- A modified fuzzy TOPSIS approach for the condition assessment of existing bridges
- Nonlinear structural and vibration analysis of straddle monorail pantograph under random excitations
- Achieving high efficiency and stability in blue OLEDs: Role of wide-gap hosts and emitter interactions
- Construction of teaching quality evaluation model of online dance teaching course based on improved PSO-BPNN
- Enhanced electrical conductivity and electromagnetic shielding properties of multi-component polymer/graphite nanocomposites prepared by solid-state shear milling
- Optimization of thermal characteristics of buried composite phase-change energy storage walls based on nonlinear engineering methods
- A higher-performance big data-based movie recommendation system
- Nonlinear impact of minimum wage on labor employment in China
- Nonlinear comprehensive evaluation method based on information entropy and discrimination optimization
- Application of numerical calculation methods in stability analysis of pile foundation under complex foundation conditions
- Research on the contribution of shale gas development and utilization in Sichuan Province to carbon peak based on the PSA process
- Characteristics of tight oil reservoirs and their impact on seepage flow from a nonlinear engineering perspective
- Nonlinear deformation decomposition and mode identification of plane structures via orthogonal theory
- Numerical simulation of damage mechanism in rock with cracks impacted by self-excited pulsed jet based on SPH-FEM coupling method: The perspective of nonlinear engineering and materials science
- Cross-scale modeling and collaborative optimization of ethanol-catalyzed coupling to produce C4 olefins: Nonlinear modeling and collaborative optimization strategies
- Unequal width T-node stress concentration factor analysis of stiffened rectangular steel pipe concrete
- Special Issue: Advances in Nonlinear Dynamics and Control
- Development of a cognitive blood glucose–insulin control strategy design for a nonlinear diabetic patient model
- Big data-based optimized model of building design in the context of rural revitalization
- Multi-UAV assisted air-to-ground data collection for ground sensors with unknown positions
- Design of urban and rural elderly care public areas integrating person-environment fit theory
- Application of lossless signal transmission technology in piano timbre recognition
- Application of improved GA in optimizing rural tourism routes
- Architectural animation generation system based on AL-GAN algorithm
- Advanced sentiment analysis in online shopping: Implementing LSTM models analyzing E-commerce user sentiments
- Intelligent recommendation algorithm for piano tracks based on the CNN model
- Visualization of large-scale user association feature data based on a nonlinear dimensionality reduction method
- Low-carbon economic optimization of microgrid clusters based on an energy interaction operation strategy
- Optimization effect of video data extraction and search based on Faster-RCNN hybrid model on intelligent information systems
- Construction of image segmentation system combining TC and swarm intelligence algorithm
- Particle swarm optimization and fuzzy C-means clustering algorithm for the adhesive layer defect detection
- Optimization of student learning status by instructional intervention decision-making techniques incorporating reinforcement learning
- Fuzzy model-based stabilization control and state estimation of nonlinear systems
- Optimization of distribution network scheduling based on BA and photovoltaic uncertainty
- Tai Chi movement segmentation and recognition on the grounds of multi-sensor data fusion and the DBSCAN algorithm
- Special Issue: Dynamic Engineering and Control Methods for the Nonlinear Systems - Part III
- Generalized numerical RKM method for solving sixth-order fractional partial differential equations


