Abstract
To solve the problem that most computer network security assessment systems cannot comprehensively analyze data, this article proposes a research method for computer network confidentiality information security system based on the Bayesian classification algorithm. This research takes the computer network security secret-related information security as the core, cleverly uses the EBCA back-propagation model, and comprehensively uses nonlinear functions to propose a computer network secret-related information security application system considering EBCA, which effectively solves the complex cross-linking relationship. The effectiveness of the method is verified by simulation experiments. Simulation experiments show that when the network performance is in the optimal state, the slope is 1, the intercept is 0, and the fitting degree is 1. The method proposed in this article is especially suitable for the nonlinear characteristics of computer network security and can accurately, comprehensively, and systematically reflect the security operation status of network security and confidential information. Then, through the simulation test, it is found that the method in this study can effectively meet the error requirements of equipment integrity and equipment normal rate.
1 Introduction
In information network security, experts often use blocking and detection models to improve network security, but they each have their pros and cons. For blocking, the traditional method is to establish a protection domain, every person entering the system must be authenticated and authorized, and at the same time, information in the protection domain is prevented from leaking to the outside. Using this method to achieve computer and network security introduces several limitations: First, it is impossible to build a completely safe system; second, it contradicts the current open trend [1]. The main research of computer artificial intelligence (AI) network secret-related information security system, as a whole, gives the ability to acquire, understand, and predict network security elements from entities in the network and accordingly generate strategies to deal with threats in network security, in order to realize the cooperative work and information fusion of various security entities in heterogeneous and generalized networks, building a seamless network security system provides a new idea [2]. The rationality and authenticity of the results of the computer network confidential information security system are very critical; it has a far-reaching impact on the formulation of security policies because the formulation and implementation of security policies mainly depend on the credibility of the assessment. Generally, it starts from the bottom-level decision-making indicators and conducts credibility evaluation layer by layer until the highest level, to obtain an overall network confidential information security system [3,4]. As with any form of communication, compressed data communication can only work if both the sender and receiver of the information understand the encoding mechanism. For example, an article is only meaningful if the recipient knows that the article needs to be interpreted in English characters. Similarly, compressed data can only be understood if the receiver knows the encoding method. Some compression algorithms take advantage of this feature by encrypting data during the compression process, such as with a password, to ensure that only the authorized party can access the data correctly. Artificial Intelligence (AI) is a new technical science that studies and develops theories, methods, techniques, and application systems for simulating, extending, and expanding human intelligence.
AI is a branch of computer science; it seeks to understand the essence of intelligence and produce a new intelligent machine that responds in a similar way to human intelligence. Research in this area includes robotics, language recognition, image recognition, natural language processing, and expert systems. Since the birth of AI, the theory and technology have become more and more mature, and the field of application is also expanding; it is conceivable that the technological products brought by AI in the future will be the “container” of human intelligence. AI can simulate the information process of human consciousness and thinking. AI is not human intelligence, but it can think like human beings and may surpass human intelligence. Computer artificial intelligence network security is crucial to air traffic security and classified information security. In the national industry, the civil aviation industry is a very important information industry, and it is related not only to the country’s airspace security and classified information security but also to the country’s economic security and classified information security; at the same time, it is also related to social security and confidential information security [5]. From this, it is shown to be a very important project to strengthen national network security and the defense strategy of classified information security. By adopting network security and classified information security, we can effectively understand the overall situation of national space network information; as a result, many security incidents can be prevented. In the construction of a computer network confidential information security application system, the most used method is the Bayesian classification algorithm, and many scholars at home and abroad have used this method to obtain a great research breakthrough [6]. From the perspective of importance, the computer network classified information security application system is compared with the national power network, the application field of Bayesian Classification Algorithms (BCA) is wider, and many mature technical achievements have also been made. However, it should also be noted that at this stage, the research on the computer network confidential information security application system considering BCA is still in the early stage, in particular, the correlation of each target attribute, the proportion of which is shown as a nonlinear relationship that has reached at least half; it is difficult to reflect this relationship conventionally. Especially for some problems, the source of which is not clear, and some contradictions often appear in the process of analysis, there will even be a phenomenon of disorganization [7]. In the author’s research, combined with relevant professional theoretical knowledge, the security types of computer network classified information are divided into three levels, and the relationship of each level structure is shown in Figure 1. Taking into account the situation discussed above, this research focuses on the security of confidential information in computer network security, selects the EBCA backpropagation model reasonably, and gives full play to the characteristics of nonlinear functions according to the specific characteristics of the model, which accurately reflects the computer network security. Various complex relationships are contained in the network, thus contributing to a comprehensive and accurate analysis of the security of the network and classified information.
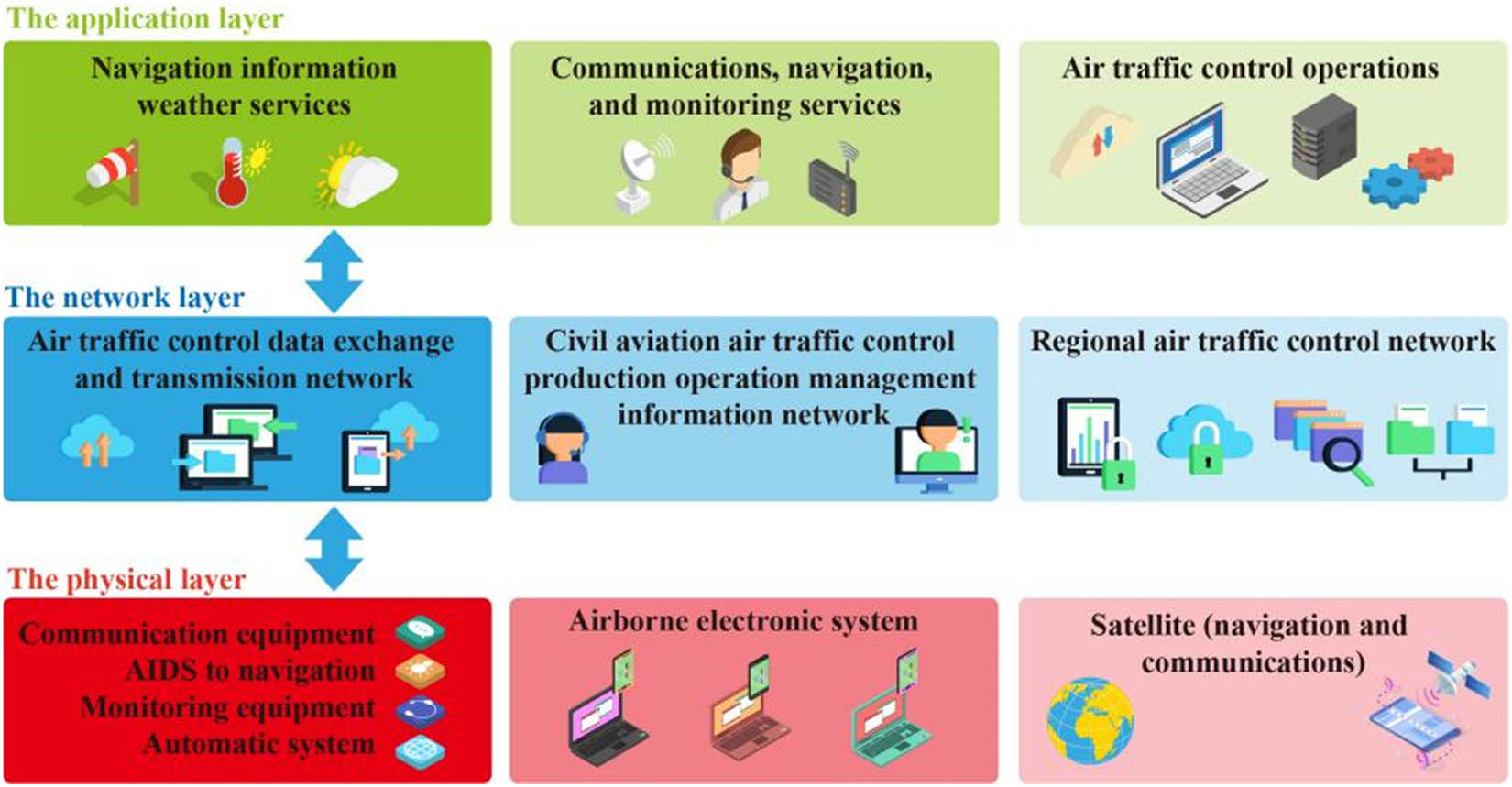
The layer structure of a computer network.
2 Literature review
In recent years, computer artificial intelligence network secrets have become a research hotspot in the field of network security, many scholars have put forward many theories and methods and established effective evaluation models and methods, such as Bayesian network, fuzzy reasoning, game theory, graph model, etc. [8] Using network security and classified information security can effectively understand the overall situation of national space network information so that many security accidents can be prevented before they occur. The research results from comprehensive security assessments and large-scale networks proposed a security situation hierarchical index evaluation model and 25 candidate indicators, and established an evaluation index system; the candidate indicators are organically organized and further abstracted [9]. In the network security situation assessment based on Hidden Markov Model, a method is proposed to obtain the improved observation sequence and transition matrix in a random way, which can effectively characterize the security of the network [10]. The authors proposed a security situation prediction method based on Radial Basis Function (RBF) neural network, which can achieve a more accurate prediction effect in an environment with a small neural network node scale and is very suitable for security situation prediction in a large-scale network environment. A framework was established without modularization technology to integrate network attack detection technology, and the basic idea is “defense in depth.” However, this method can only detect limited attacks and cannot really evaluate network security [11]. A security evaluation model was proposed based on the Back Propagation (BP) neural network; on this basis, the RBF network is used to predict the current security situation, and the genetic algorithm is used to optimize the network parameters, and it can more accurately predict the security situation [12]. The authors proposed to extract effective threats from a large amount of security alarm information, identify the method of the current state, and propose a network real-time dynamic threat identification and quantitative assessment method based on spatiotemporal correlation analysis [13]. The author and others proposed a reasoning process based on expert experience and opinion fusion and implemented a network security situation assessment method based on DS (Dempster Shafer) evidence fusion reasoning; it is verified by the vulnerability index experiment, and the two can confirm each other. Aiming at the problem of network security situation assessment, the author compared and analyzed a variety of existing situation assessment methods, an evaluation method based on a neural network is proposed, and a security situation evaluation method based on BP neural network is designed [14]. From the perspective of importance, compared with the national power network, the computer network classified information security application system has a wider application field and has also formed many relatively mature technical achievements. However, it should also be noted that the research on the computer network classified information security application system considering EBCA is still in the early stage, especially the correlation of each target attribute, which is represented by a nonlinear relationship. The proportion has reached at least half. It is difficult to reflect this relationship by conventional methods; especially for some problems, the source of which is unclear, and some contradictions and even incoherence often appear in the process of analysis.
Based on this research, the author proposes research on computer network confidential information security systems based on the Bayesian classification algorithm. Focusing on the security of confidential information of computer network security, the BCA back-propagation model is reasonably selected, and according to the specific characteristics of the model, the characteristics of nonlinear functions are fully utilized, and it accurately reflects all kinds of complex relationships contained in the computer network, thus contributing to a comprehensive and accurate analysis of the security of the network and classified information.
3 Research methods
3.1 System of AI in computer network confidential information security application
The computer network information security system consists of six parts, they are communication satellite system, ground air traffic control (ATC) system, space navigation system, information service system, airborne electronic system, and plane communication network system. In the author’s research, combined with relevant professional theoretical knowledge, the security types of computer network confidential information are divided into three levels [15].
The bottom layer is the physical layer, also known as the CNS layer of the new navigation system. In this layer, it is usually composed of infrastructures, such as space satellite systems, navigation systems, and ground communication systems.
The middle layer is mainly composed of the network layer. This layer is usually called the data transmission layer. This layer is basically composed of transmission facilities, including the regional ATC backbone network, the ATC bureau network, and the management information network.
The highest layer is the application layer, also known as the air traffic management layer, which mainly includes a variety of services, for example, aeronautical information business, communication and navigation business, meteorological business, information network business, etc. When designing a computer network confidential information security application system, it is necessary to take the above three-layer structure as the core content, and implement guarantee processing for each layer; for example, intrusion detection, data encryption, and setting up effective firewalls can be accomplished according to different technical methods [16].
3.2 Bayesian classification algorithm model
Bayesian classification algorithm model (Extended Bayesian Classification Algorithms, EBCA) is a typical classification model based on statistical methods. Bayes’ theorem is the most important formula in Bayesian theory and the theoretical basis of Bayesian learning methods; it skillfully links the prior probability of the event with the posterior probability and uses the prior information and sample data information to determine the posterior probability of the event. Let U = {A 1, A 2, …, A n , C} be a finite set of discrete random variables, where A 1, A 2, …, A n are attribute variables; the value range of class variable C is {c 1, c 2, …, c i }, and a i is the value of attribute A i . The probability that an instance x i = (a 1, a 2, …, a n ) (bold letters denote a vector) belongs to class cj can be expressed by Bayes’ theorem as Eq. (1):
where a is the regularization factor, P(c i ) is the prior probability of class c j , P(c j |a 1,a 2,…,a n ) is the posterior probability of class cj, the prior probability is independent of the training sample data, while the posterior probability reflects the influence of the sample data on the class cj. According to the chain rule of probability, Eq. (1) can be expressed as Eq. (2):
The goal of the classification task given the training data set D{x 1,x 2,…,x n } is to perform analysis on the data set D and determine a mapping function f:(A 1,A 2,…,A n ) → C, so that an instance x i (a 1,a 2,…,a a ) of any unknown class can be marked with an appropriate class label C. According to the Bayesian maximum, a posteriori criterion, given an instance x i (a 1,a 2,…,a a ), the Bayesian classifier selects the class C* that maximizes the posterior probability P(c j a 1,a 2,…,a n ) as the class label for this instance. Therefore, the key to the Bayesian classification model is how to calculate P(a i ,a 1,a 2,…,a i−1, c j ).
Currently, the difference between different Bayesian classification models is that they approach P(a i ,a 1,a 2,…,a i−1, c j ) in different ways. In the naive Bayes classifier, all attribute variables are assumed to be mutually class conditionally independent, each node A is only associated with class node C; therefore, the abbreviation of P(a i ,a 1,a 2,…,a i−1, c j ) in formula (2) is P(a i |c j ). Compared with other classification methods, the biggest feature of the Naive Bayes classification algorithm is that it does not need to search, simply count how often each attribute value occurs in the training example, the probability estimation value of each attribute can be estimated, so the efficiency of the naive Bayesian classification algorithm is particularly high [17,18].
3.3 Computer network confidential information security
In this study, a computer network confidential information security application system is designed considering the extended Bayesian classification algorithm. There is a correspondence between the three-layer computer network structure discussed above and the Extended Bayesian classification algorithm, as follows: (i) The CNS layer belongs to the physical layer, which is usually composed of sensor devices, corresponding to the extended Bayesian classification algorithm is the input layer, where the input vector is X(x 1,x 2,…,x i,…,x n )T. x i stands for the processed output signal of the sensor device. (ii) The network layer corresponds to the transport layer. This layer contains a network system with a complex structure, the hidden layer corresponds to the extended Bayesian classification algorithm, and the output vector in this layer is Y(y 1,y 2,…,y i,…,x m ) T . Y j refers to the corresponding computer network. (iii) The application layer corresponds to the output layer, which contains a lot of final business data, in the extended Bayesian classification algorithm is the output layer, in this layer. The output vector is O(o 1,o 2,…,o k,…,o l ) T . o k refers to those computer networks that have been processed in a certain way.
The BCA security system is a system with multiple input and single output characteristics. In the study, the extended Bayesian classification algorithm is used to construct a new construction of ATC information security and confidential information security, with BCA as the basic core, obtaining new security of confidential information security [19,20]. If there is a difference between the network input value and the expected output result, it will cause the problem of output error, which can be expressed as E. Eq. (3) can be obtained according to the following formula:
After extending the above expression to the hidden layer, the following expression (4) can be obtained:
After extending the above expression to the output layer, the following expression (5) can be obtained:
According to the above formula, it can be found that the network input error is affected by the weights w jk and v ij of different layers; therefore, in order to obtain different error E values, it is required to adjust the weights reasonably. Very obvious, the purpose of adjusting the weights is to keep the error decreasing. In other words, it is a changing relationship that makes the error gradient decrease and the weight adjustment amount positively correlated, specifically, formula (6) can be obtained by the following expression:
In the above expression, the negative sign represents the process of decreasing the gradient, h is a constant, corresponding to a specific scale coefficient, which is in the range of 0–1, the BCA algorithm can be used to calculate the change of the error gradient [21]. Using the same method, the first error signal is also processed according to the same rules, and the process of weight adjustment is completed by using the formula (6), which can also be rewritten as the following formula (7):
To sum up, based on formula (7), the signals
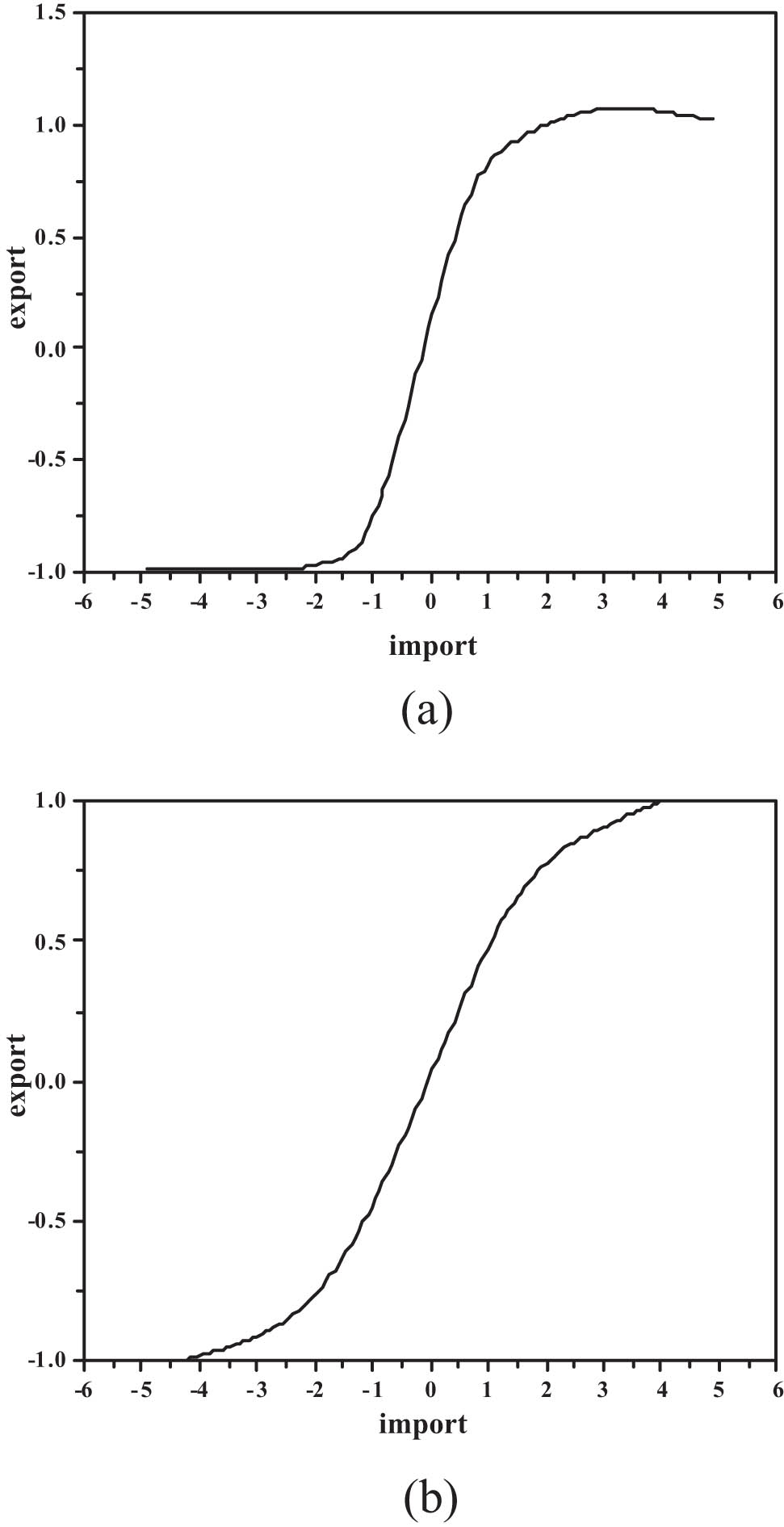
Curve distribution diagram of the tangent function (a) and logarithmic function (b).
The sigmoid function has its own unique characteristics; this function has the characteristic of a nonlinear amplification factor, an input signal; it can be amplified from negative infinity to positive infinity and controls the output result within the range of −1 to 1. The actual amplification factor usually depends on the input signal, and when the input signal is at a larger value, the amplification factor will be reduced; when the input signal is small, a large amplification factor will be obtained [22,23]. Therefore, the clever use of the sigmoid activation function can effectively optimize and approximate the nonlinear input/output relationship.
4 Discussion of results
The author mainly uses computer artificial intelligence network data to carry out the simulation and testing process. When selecting such operational data, its source has strict requirements, and the data used here are taken from the duty records of ATC units in various regions of China’s civil aviation. These operating record data are the sample data of the author’s research, and these data are used in the research of BCA security-related information security. The ultimate purpose of building a computer network confidential information security application system is to ensure that each computer network facility in the system can operate normally [24]. Usually, two indicators can be selected to measure the operating status of computer network equipment, namely, the normal rate and the intact rate of equipment operation. The following content will analyze the specific calculation methods of the above two indicators.
1) When calculating the operating normal rate of the equipment, it can be carried out according to the following formula:
Equipment operating normal rate = (Planned operating time (hours) − Abnormal operating time (hours)) / Planned operating time (hours) × 100%
Among them, the planned running time refers to the total time that the system is in normal operation (here refers to the total number of hours included), the cumulative period can be divided into the following three categories: Monthly, quarterly, and annual terms; Uptime is the amount of time the system is not functioning properly (here, the total number of hours included).
2) The formula for calculating the equipment integrity rate is as follows:
Equipment integrity rate = (Total number of equipment − Total number of faulty equipment) / total number of equipment × 100%
Among them, the total number of equipment refers to the total number of equipment within the scope of the equipment shelf life, and the total number of faulty equipment refers to the total number of pieces of equipment that have failed during the equipment shelf life.
According to the classification of equipment, the objects selected in this study are some very commonly used equipment; at the same time, Z here also divides these protection objects into security and classified information security levels. Selection of basic operation sample data Wireless communication equipment, wired communication equipment, navigation equipment, monitoring equipment and ATC automation equipment, the devices discussed earlier are typical representatives in computer networks, and can accurately, effectively, and comprehensively reflect the security status of security and classified information. According to the recorded data extracted by these devices, the operating status of the computer network can be fully, accurately, and effectively reflected; based on these data, the reliability, rationality, and completeness of network security can also be effectively analyzed [25,26]. Security and classification of classified information security levels. In our current research, the confidential information of the computer network confidential information security application system is secured, according to certain rules; it is divided into five levels, the first level is very safe and confidential information security, the second level is relatively safe and classified information security, the third level is security and classified information security, the fourth level is dangerous, and the fifth level is very dangerous. The range represented by each level refers to the actual output value of the network. The specific grades and their corresponding values are listed in Table 1.
Classification of security and classified information security levels
| Active safety level | Network output value |
|---|---|
| A | 0.75–1 |
| B | 0.60–0.75 |
| C | 0.50–0.60 |
| D | 0.35–0.50 |
| E | 0.00–0.35 |
Based on the content discussed above, the author takes the extended Bayesian classification algorithm as the core, the computer network classified information security application is systematically simulated under certain conditions; at the same time, it has been professionally tested with relevant data. The computer network confidential information security application system with the extended Bayesian classification algorithm as the core, in the whole system, contains many subsystems, including not only the WAN but also some local area networks; at the same time, in the design of the hidden layer, the content is also relatively complex. In the design of BCA, due to the influence of the number of information in the hidden layer, it will also have a serious impact on the performance of network testing. Taking into account the actual computer network and taking the actual computer network as the criterion, 10 actual devices are selected and used as analysis factors. The specific parameter settings are shown in Table 2:
Results of training parameter settings
| Parameter type | Remaining parameters |
|---|---|
| Minimum training error goal | 0.01 |
| Maximum training steps epochs | 1,000 |
| Show | 15 |
| Remaining parameters | Default value |
Among them, the minimum training error of 0.01 is affected by two factors, including the minimum error of equipment integrity and the minimum error of equipment normal rate. The data used in this article come from the actual operation data of 12 groups of computer networks. After a large number of experimental tests and analysis of the obtained results, it can be seen that the optimal network performance can be obtained when the hidden layer contains 25 pieces of information. Therefore, a total of 12 groups of data were selected as test pairs in this experiment. At the same time, these data are used as actual analysis samples. The test results of each sample are shown in Table 3.
Training samples
| Evaluation index | VHF system | Satellite system | DVOR system | DME system | Internal call system | ILS system | ADS system | SSR system | GPS system | Flight information | Flight plan | Surveillance system |
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1 | 0.99 | 1.0 | 0.97 | 0.92 | 1.0 | 0.98 | 1.0 | 0.95 | 0.99 | 0.97 | 1.0 | 1.0 |
| 2 | 0.81 | 0.83 | 0.84 | 0.76 | 0.85 | 0.84 | 0.82 | 0.83 | 0.87 | 0.83 | 0.82 | 0.86 |
| 3 | 0.71 | 0.75 | 0.68 | 0.61 | 0.69 | 0.68 | 0.75 | 0.71 | 0.72 | 0.68 | 0.73 | 0.67 |
| 4 | 0.62 | 0.64 | 0.55 | 0.43 | 0.52 | 0.71 | 0.69 | 0.65 | 0.64 | 0.52 | 0.58 | 0.58 |
| 5 | 0.89 | 0.93 | 0.91 | 0.86 | 0.89 | 0.88 | 0.95 | 0.93 | 0.90 | 0.91 | 0.93 | 0.92 |
| 6 | 0.79 | 0.83 | 0.80 | 0.81 | 0.78 | 0.85 | 0.83 | 0.82 | 0.84 | 0.83 | 0.81 | 0.87 |
| 7 | 0.77 | 0.75 | 0.73 | 0.71 | 0.72 | 0.78 | 0.75 | 0.73 | 0.72 | 0.67 | 0.68 | 0.66 |
| 8 | 0.51 | 0.62 | 0.55 | 0.42 | 0.54 | 0.71 | 0.64 | 0.59 | 0.65 | 0.45 | 0.51 | 0.49 |
| 9 | 0.92 | 0.91 | 1.00 | 0.92 | 0.92 | 0.93 | 0.9o | 0.93 | 0.9o | 1.00 | 0.91 | 0.89 |
| 10 | 0.86 | 0.88 | 0.85 | 0.76 | 0.83 | 0.85 | 0.83 | 0.82 | 0.81 | 0.87 | 0.82 | 0.84 |
| 11 | 0.78 | 0.76 | 0.74 | 0.61 | 0.75 | 0.74 | 0.77 | 0.72 | 0.75 | 0.71 | 0.73 | 0.73 |
| 12 | 0.67 | 0.65 | 0.62 | 0.45 | 0.53 | 0.69 | 0.59 | 0.63 | 0.63 | 0.53 | 0.59 | 0.45 |
Among them, the minimum training error of 0.01 is affected by two factors, including the minimum error of equipment integrity and the minimum error of equipment normal rate. The data used by the author come from the actual operation data of 10 groups of computer networks. After a large number of experimental tests and analysis of the obtained results, it can be seen that when the hidden layer contains 20 pieces of information, get the best network performance. Therefore, a total of 10 groups of data are selected as the test objects in this experiment, and these data are used as the actual analysis samples.
In order to verify the performance of the network model, this study selects MATLAB as the software system for simulation testing; during the research period, the network is initialized, and the function Trainlm is used to process the whole system. The target value is set to be equal to 0.01, after three steps of training, and the training result obtained is equal to 0.00114378, thereby reducing the error rate to the design error range; Figure 3 shows the actual corresponding error rate.
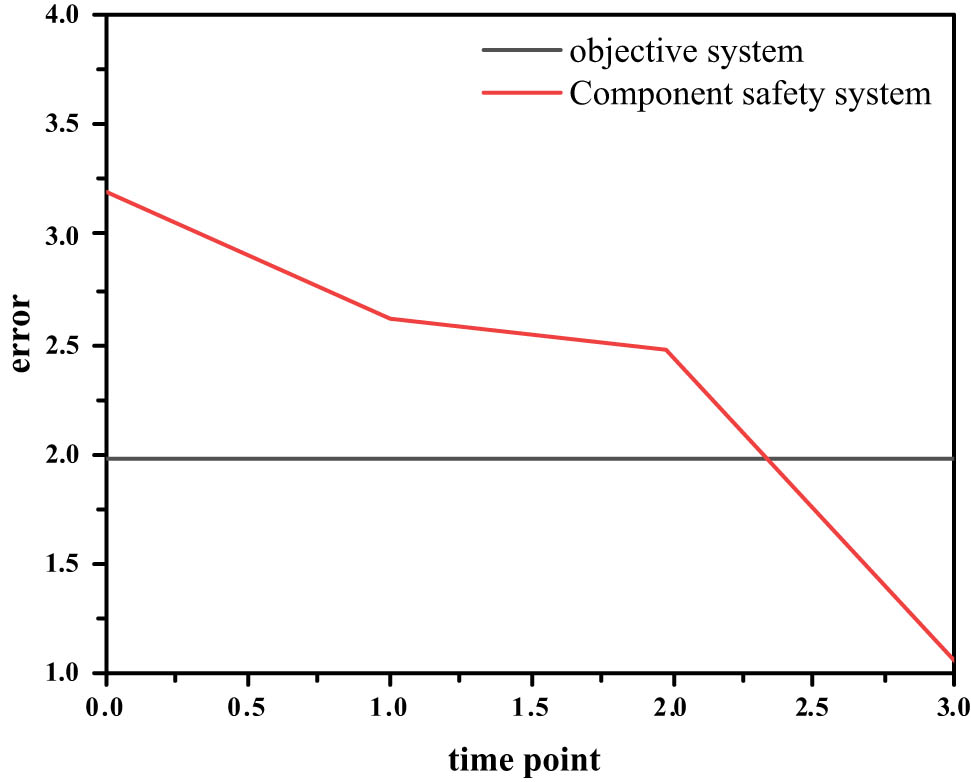
Computer network error rate.
In order to verify the network performance obtained by the training method, this experiment selects the training results as the research object, and on this basis, the relevant simulation test and analysis process were carried out. The postreg function is used to perform nonlinear regression analysis on each data, so as to obtain the result with a better approximation effect; under the condition of fitting degree R = 0.999, the calculation results shown in Figure 4 can be obtained:
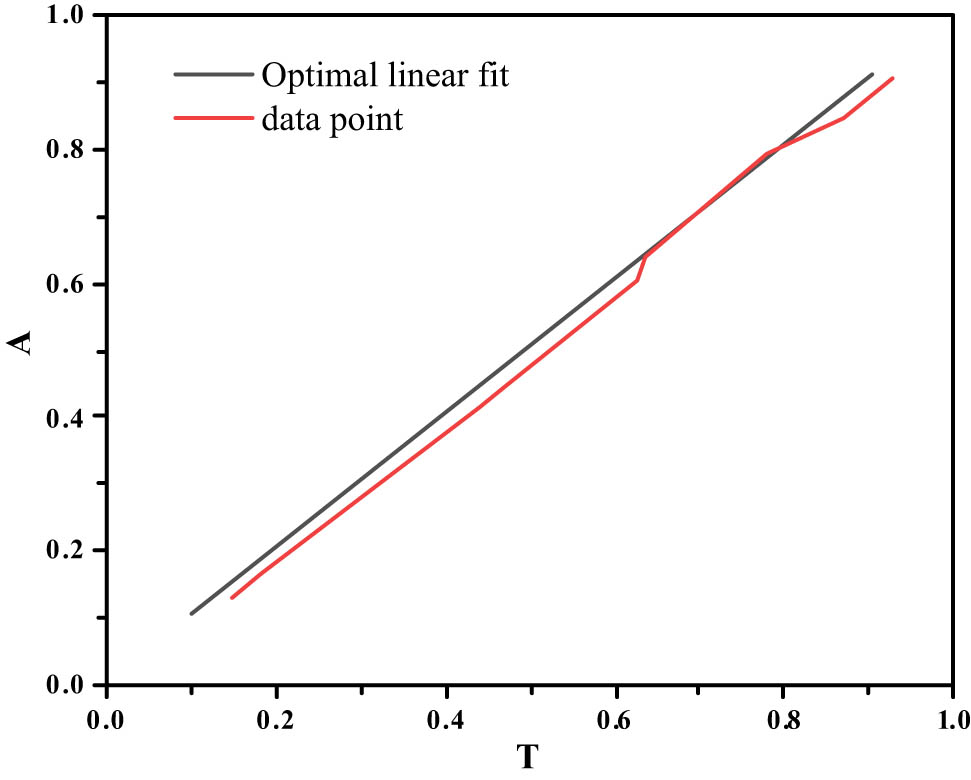
Fitting curve obtained by using nonlinear regression method to process the data of computer network security system.
The author completes the linear regression analysis by simulating the output vector and the target vector and uses the correlation coefficient as the analysis basis. When the network performance is in the optimal state, the slope is equal to 1, the intercept is equal to 0, and the fit is equal to 1.
At present, with the increasing value of data information, hackers have become a profession. They invade specific computers and servers in various ways, steal users’ data information, and cause users to suffer serious economic losses. With the rapid development of information technology, the forms of hacking also show obvious diversification characteristics. Therefore, we should strengthen the defense technology of hacking and adopt diversified defense methods to realize the security of computer network data and information. (i) The self-adaptability of the computer firewall should be improved, and the firewall can automatically adjust its own protection level according to the change of the security situation in the Internet environment. (ii) The hacker intrusion detection software should be installed to monitor the behavior of illegally entering the computer, obtain the IP address of the intruder in time, and report the information to the network security information center. (iii) If the intrusion continues and the computer has the risk of data and information being stolen, the computer security system will automatically cut off the network connection or adjust the firewall level to the highest level to prevent intrusion packets from entering the computer.
5 Conclusion
This article proposes research on the computer network confidential information security system based on the Bayesian classification algorithm and gives an attempt scheme for computer artificial intelligence network confidential information security management. It fully considers the fusion of multi-information sources and multi-level heterogeneous information. Dynamically generate the current network security status, which accurately reflects the current network security status. By comprehensively utilizing the functions of nonlinear functions, a BCA-based computer network confidential information security application system is proposed, which effectively solves the complex cross-linking relationship. At the same time, the effectiveness of the model is verified by simulation experiments. It provides theoretical support for the design and implementation of BCA-based computer network confidential information security application system. It can accurately comprehensively, and systematically reflect the security operation status of network security and classified information. Then, through the simulation test, it is found that the method in this study can effectively meet the error requirements of equipment integrity and equipment normal rate.
-
Funding information: The author states no funding involved.
-
Author contributions: Author has accepted responsibility for the entire content of this manuscript and approved its submission.
-
Conflict of interest: Author states no conflict of interest.
References
[1] Gundersen K, Alendal G, Oleynik A, Blaser N. Binary time series classification with bayesian convolutional neural networks when monitoring for marine gas discharges. Algorithms. 2020;13(6):145–9.10.3390/a13060145Suche in Google Scholar
[2] Gaye B, Zhang D, Wulamu A. Improvement of support vector machine algorithm in big data background. Math Probl Eng. 2021;2021(1):1–9.10.1155/2021/5594899Suche in Google Scholar
[3] Lopes P. Bayesian step least mean squares algorithm for gaussian signals. IET Signal Proc. 2020;14(8):506–12.10.1049/iet-spr.2020.0058Suche in Google Scholar
[4] Sunl Z. A decision-making method based on bayesian optimization algorithm for small modular reactor. Kerntechnik. 2020;85(2):109–21.10.1515/kern-2020-850208Suche in Google Scholar
[5] Armero C, García-Donato G, Jiménez-Puerto J, Pardo-Gordó S, Bernabeu J. Bayesian classification for dating archaeological sites via projectile points. SORT. 2021;45(1):33–46.Suche in Google Scholar
[6] Fang S, Zhang Z, Wang Z, Pan H, Du T. Principal slip zone determination in the wenchuan earthquake fault scientific drilling project-hole 1: Considering the bayesian discriminant function. Acta Geophys. 2020;68(8):1–13.10.1007/s11600-020-00496-zSuche in Google Scholar
[7] Ewais A, Samara DA. Adaptive moocs based on intended learning outcomes using nave bayesian technique. Int J Emerg Technol Learn. 2020;15(4):4–7.10.3991/ijet.v15i04.11420Suche in Google Scholar
[8] Angadi UB, Rai A, Uma G. Mbferns: Classification and extraction of actionable knowledge using multi-branch ferns-based naive bayesian classifier. Soft Comput. 2021;25(6):1–13.10.1007/s00500-021-05759-5Suche in Google Scholar
[9] Lee J, Cardille JA, Coe MT. Agricultural expansion in mato grosso from 1986–2000: A bayesian time series approach to tracking past land cover change. Remote Sens. 2020;12(4):688–92.10.3390/rs12040688Suche in Google Scholar
[10] Gavade AB, Rajpurohit VS. A hybrid optimization-based deep belief neural network for the classification of vegetation area in multi-spectral satellite image. Int J Knowl-Based Intell Eng Syst. 2021;24(4):363–79.10.3233/KES-170376Suche in Google Scholar
[11] Liang J, Li M, Jing Z, Pan H. Multi-target joint detection; tracking and classification based on marginal glmb filter and belief function theory. Sensors. 2020;20(15):4235–9.10.3390/s20154235Suche in Google Scholar PubMed PubMed Central
[12] Chen J, Du L, Guo Y. Label constrained convolutional factor analysis for classification with limited training samples. Inf Sci. 2021;544(6):372–94.10.1016/j.ins.2020.08.048Suche in Google Scholar
[13] Gao J, Liu J, Guo S, Zhang Q, Wang X. A data mining method using deep learning for anomaly detection in cloud computing environment. Math Probl Eng. 2020;2020(1):1–11.10.1155/2020/6343705Suche in Google Scholar
[14] Kim SH, Dong IK. Traffic-aware backscatter communications in wireless-powered heterogeneous networks. IEEE Trans Mob Comput. 2020;19(7):1731–44.10.1109/VTCFall.2018.8690915Suche in Google Scholar
[15] Xiao X, Xu M, Jin J, Wang Y, Jung TP, Ming D. Discriminative canonical pattern matching for single-trial classification of erp components. IEEE Trans Biomed Eng. 2020;67(8):2266–75.10.1109/TBME.2019.2958641Suche in Google Scholar PubMed
[16] Wang L, Chen P, Chen S, Sun M. A novel approach to fully representing the diversity in conditional dependencies for learning bayesian network classifier. Intell Data Anal. 2021;25(1):35–55.10.3233/IDA-194959Suche in Google Scholar
[17] Waleed M, Um TW, Khan A, Khan U. Automatic detection system of olive trees using improved k-means algorithm. Remote Sens. 2020;12(5):760–5.10.3390/rs12050760Suche in Google Scholar
[18] Suh SM, Park Y, Ko KM, Yang SM, Kim SH. Weighted mask R-CNN for improving adjacent boundary segmentation. J Sens. 2021;11:1–8.10.1155/2021/8872947Suche in Google Scholar
[19] Xiao Y, Pan W, Guo X, Bi S, Lin S. Fault diagnosis of traction transformer based on bayesian network. Energies. 2020;13(18):4966–70.10.3390/en13184966Suche in Google Scholar
[20] Chen L, Zhan P, Cao L, Li X. Discrimination and correlation analysis of multiview sar images with application to target recognition. Sci Program. 2021;2021(6):1–9.10.1155/2021/6646388Suche in Google Scholar
[21] Silva AP, Vieira MN, Barbosa AV. Forensic speaker comparison using evidence interval in full bayesian significance test. Math Probl Eng. 2020;2020(1):1–9.10.1155/2020/2914942Suche in Google Scholar
[22] Gil-Begue S, Bielza C, Larraaga P. Multi-dimensional bayesian network classifiers: A survey. Artif Intell Rev. 2021;54(1):519–59.10.1007/s10462-020-09858-xSuche in Google Scholar
[23] Wang C, Sun H, Zhao R, Cao X. Research on bearing fault diagnosis method based on an adaptive anti-noise network under long time series. Sensors. 2020;20(24):7031–6.10.3390/s20247031Suche in Google Scholar PubMed PubMed Central
[24] Ramchoun H, Ettaouil M. New prior distribution for bayesian neural network and learning via hamiltonian monte carlo. Evol Syst. 2020;11(4):661–71.10.1007/s12530-019-09288-3Suche in Google Scholar
[25] Burr T, Favalli A, Lombardi M, Stinnett J. Application of the approximate bayesian computation algorithm to gamma-ray spectroscopy. Algorithms. 2020;13(10):265–8.10.3390/a13100265Suche in Google Scholar
[26] Ke H, Chen D, Shi B, Zhang J, Li X. Improving brain e-health services via high-performance eeg classification with grouping bayesian optimization. IEEE Trans Serv Comput. 2020;13(4):696–708.10.1109/TSC.2019.2962673Suche in Google Scholar
© 2022 Hao Wu, published by De Gruyter
This work is licensed under the Creative Commons Attribution 4.0 International License.
Artikel in diesem Heft
- Research Articles
- Fractal approach to the fluidity of a cement mortar
- Novel results on conformable Bessel functions
- The role of relaxation and retardation phenomenon of Oldroyd-B fluid flow through Stehfest’s and Tzou’s algorithms
- Damage identification of wind turbine blades based on dynamic characteristics
- Improving nonlinear behavior and tensile and compressive strengths of sustainable lightweight concrete using waste glass powder, nanosilica, and recycled polypropylene fiber
- Two-point nonlocal nonlinear fractional boundary value problem with Caputo derivative: Analysis and numerical solution
- Construction of optical solitons of Radhakrishnan–Kundu–Lakshmanan equation in birefringent fibers
- Dynamics and simulations of discretized Caputo-conformable fractional-order Lotka–Volterra models
- Research on facial expression recognition based on an improved fusion algorithm
- N-dimensional quintic B-spline functions for solving n-dimensional partial differential equations
- Solution of two-dimensional fractional diffusion equation by a novel hybrid D(TQ) method
- Investigation of three-dimensional hybrid nanofluid flow affected by nonuniform MHD over exponential stretching/shrinking plate
- Solution for a rotational pendulum system by the Rach–Adomian–Meyers decomposition method
- Study on the technical parameters model of the functional components of cone crushers
- Using Krasnoselskii's theorem to investigate the Cauchy and neutral fractional q-integro-differential equation via numerical technique
- Smear character recognition method of side-end power meter based on PCA image enhancement
- Significance of adding titanium dioxide nanoparticles to an existing distilled water conveying aluminum oxide and zinc oxide nanoparticles: Scrutinization of chemical reactive ternary-hybrid nanofluid due to bioconvection on a convectively heated surface
- An analytical approach for Shehu transform on fractional coupled 1D, 2D and 3D Burgers’ equations
- Exploration of the dynamics of hyperbolic tangent fluid through a tapered asymmetric porous channel
- Bond behavior of recycled coarse aggregate concrete with rebar after freeze–thaw cycles: Finite element nonlinear analysis
- Edge detection using nonlinear structure tensor
- Synchronizing a synchronverter to an unbalanced power grid using sequence component decomposition
- Distinguishability criteria of conformable hybrid linear systems
- A new computational investigation to the new exact solutions of (3 + 1)-dimensional WKdV equations via two novel procedures arising in shallow water magnetohydrodynamics
- A passive verses active exposure of mathematical smoking model: A role for optimal and dynamical control
- A new analytical method to simulate the mutual impact of space-time memory indices embedded in (1 + 2)-physical models
- Exploration of peristaltic pumping of Casson fluid flow through a porous peripheral layer in a channel
- Investigation of optimized ELM using Invasive Weed-optimization and Cuckoo-Search optimization
- Analytical analysis for non-homogeneous two-layer functionally graded material
- Investigation of critical load of structures using modified energy method in nonlinear-geometry solid mechanics problems
- Thermal and multi-boiling analysis of a rectangular porous fin: A spectral approach
- The path planning of collision avoidance for an unmanned ship navigating in waterways based on an artificial neural network
- Shear bond and compressive strength of clay stabilised with lime/cement jet grouting and deep mixing: A case of Norvik, Nynäshamn
- Communication
- Results for the heat transfer of a fin with exponential-law temperature-dependent thermal conductivity and power-law temperature-dependent heat transfer coefficients
- Special Issue: Recent trends and emergence of technology in nonlinear engineering and its applications - Part I
- Research on fault detection and identification methods of nonlinear dynamic process based on ICA
- Multi-objective optimization design of steel structure building energy consumption simulation based on genetic algorithm
- Study on modal parameter identification of engineering structures based on nonlinear characteristics
- On-line monitoring of steel ball stamping by mechatronics cold heading equipment based on PVDF polymer sensing material
- Vibration signal acquisition and computer simulation detection of mechanical equipment failure
- Development of a CPU-GPU heterogeneous platform based on a nonlinear parallel algorithm
- A GA-BP neural network for nonlinear time-series forecasting and its application in cigarette sales forecast
- Analysis of radiation effects of semiconductor devices based on numerical simulation Fermi–Dirac
- Design of motion-assisted training control system based on nonlinear mechanics
- Nonlinear discrete system model of tobacco supply chain information
- Performance degradation detection method of aeroengine fuel metering device
- Research on contour feature extraction method of multiple sports images based on nonlinear mechanics
- Design and implementation of Internet-of-Things software monitoring and early warning system based on nonlinear technology
- Application of nonlinear adaptive technology in GPS positioning trajectory of ship navigation
- Real-time control of laboratory information system based on nonlinear programming
- Software engineering defect detection and classification system based on artificial intelligence
- Vibration signal collection and analysis of mechanical equipment failure based on computer simulation detection
- Fractal analysis of retinal vasculature in relation with retinal diseases – an machine learning approach
- Application of programmable logic control in the nonlinear machine automation control using numerical control technology
- Application of nonlinear recursion equation in network security risk detection
- Study on mechanical maintenance method of ballasted track of high-speed railway based on nonlinear discrete element theory
- Optimal control and nonlinear numerical simulation analysis of tunnel rock deformation parameters
- Nonlinear reliability of urban rail transit network connectivity based on computer aided design and topology
- Optimization of target acquisition and sorting for object-finding multi-manipulator based on open MV vision
- Nonlinear numerical simulation of dynamic response of pile site and pile foundation under earthquake
- Research on stability of hydraulic system based on nonlinear PID control
- Design and simulation of vehicle vibration test based on virtual reality technology
- Nonlinear parameter optimization method for high-resolution monitoring of marine environment
- Mobile app for COVID-19 patient education – Development process using the analysis, design, development, implementation, and evaluation models
- Internet of Things-based smart vehicles design of bio-inspired algorithms using artificial intelligence charging system
- Construction vibration risk assessment of engineering projects based on nonlinear feature algorithm
- Application of third-order nonlinear optical materials in complex crystalline chemical reactions of borates
- Evaluation of LoRa nodes for long-range communication
- Secret information security system in computer network based on Bayesian classification and nonlinear algorithm
- Experimental and simulation research on the difference in motion technology levels based on nonlinear characteristics
- Research on computer 3D image encryption processing based on the nonlinear algorithm
- Outage probability for a multiuser NOMA-based network using energy harvesting relays
Artikel in diesem Heft
- Research Articles
- Fractal approach to the fluidity of a cement mortar
- Novel results on conformable Bessel functions
- The role of relaxation and retardation phenomenon of Oldroyd-B fluid flow through Stehfest’s and Tzou’s algorithms
- Damage identification of wind turbine blades based on dynamic characteristics
- Improving nonlinear behavior and tensile and compressive strengths of sustainable lightweight concrete using waste glass powder, nanosilica, and recycled polypropylene fiber
- Two-point nonlocal nonlinear fractional boundary value problem with Caputo derivative: Analysis and numerical solution
- Construction of optical solitons of Radhakrishnan–Kundu–Lakshmanan equation in birefringent fibers
- Dynamics and simulations of discretized Caputo-conformable fractional-order Lotka–Volterra models
- Research on facial expression recognition based on an improved fusion algorithm
- N-dimensional quintic B-spline functions for solving n-dimensional partial differential equations
- Solution of two-dimensional fractional diffusion equation by a novel hybrid D(TQ) method
- Investigation of three-dimensional hybrid nanofluid flow affected by nonuniform MHD over exponential stretching/shrinking plate
- Solution for a rotational pendulum system by the Rach–Adomian–Meyers decomposition method
- Study on the technical parameters model of the functional components of cone crushers
- Using Krasnoselskii's theorem to investigate the Cauchy and neutral fractional q-integro-differential equation via numerical technique
- Smear character recognition method of side-end power meter based on PCA image enhancement
- Significance of adding titanium dioxide nanoparticles to an existing distilled water conveying aluminum oxide and zinc oxide nanoparticles: Scrutinization of chemical reactive ternary-hybrid nanofluid due to bioconvection on a convectively heated surface
- An analytical approach for Shehu transform on fractional coupled 1D, 2D and 3D Burgers’ equations
- Exploration of the dynamics of hyperbolic tangent fluid through a tapered asymmetric porous channel
- Bond behavior of recycled coarse aggregate concrete with rebar after freeze–thaw cycles: Finite element nonlinear analysis
- Edge detection using nonlinear structure tensor
- Synchronizing a synchronverter to an unbalanced power grid using sequence component decomposition
- Distinguishability criteria of conformable hybrid linear systems
- A new computational investigation to the new exact solutions of (3 + 1)-dimensional WKdV equations via two novel procedures arising in shallow water magnetohydrodynamics
- A passive verses active exposure of mathematical smoking model: A role for optimal and dynamical control
- A new analytical method to simulate the mutual impact of space-time memory indices embedded in (1 + 2)-physical models
- Exploration of peristaltic pumping of Casson fluid flow through a porous peripheral layer in a channel
- Investigation of optimized ELM using Invasive Weed-optimization and Cuckoo-Search optimization
- Analytical analysis for non-homogeneous two-layer functionally graded material
- Investigation of critical load of structures using modified energy method in nonlinear-geometry solid mechanics problems
- Thermal and multi-boiling analysis of a rectangular porous fin: A spectral approach
- The path planning of collision avoidance for an unmanned ship navigating in waterways based on an artificial neural network
- Shear bond and compressive strength of clay stabilised with lime/cement jet grouting and deep mixing: A case of Norvik, Nynäshamn
- Communication
- Results for the heat transfer of a fin with exponential-law temperature-dependent thermal conductivity and power-law temperature-dependent heat transfer coefficients
- Special Issue: Recent trends and emergence of technology in nonlinear engineering and its applications - Part I
- Research on fault detection and identification methods of nonlinear dynamic process based on ICA
- Multi-objective optimization design of steel structure building energy consumption simulation based on genetic algorithm
- Study on modal parameter identification of engineering structures based on nonlinear characteristics
- On-line monitoring of steel ball stamping by mechatronics cold heading equipment based on PVDF polymer sensing material
- Vibration signal acquisition and computer simulation detection of mechanical equipment failure
- Development of a CPU-GPU heterogeneous platform based on a nonlinear parallel algorithm
- A GA-BP neural network for nonlinear time-series forecasting and its application in cigarette sales forecast
- Analysis of radiation effects of semiconductor devices based on numerical simulation Fermi–Dirac
- Design of motion-assisted training control system based on nonlinear mechanics
- Nonlinear discrete system model of tobacco supply chain information
- Performance degradation detection method of aeroengine fuel metering device
- Research on contour feature extraction method of multiple sports images based on nonlinear mechanics
- Design and implementation of Internet-of-Things software monitoring and early warning system based on nonlinear technology
- Application of nonlinear adaptive technology in GPS positioning trajectory of ship navigation
- Real-time control of laboratory information system based on nonlinear programming
- Software engineering defect detection and classification system based on artificial intelligence
- Vibration signal collection and analysis of mechanical equipment failure based on computer simulation detection
- Fractal analysis of retinal vasculature in relation with retinal diseases – an machine learning approach
- Application of programmable logic control in the nonlinear machine automation control using numerical control technology
- Application of nonlinear recursion equation in network security risk detection
- Study on mechanical maintenance method of ballasted track of high-speed railway based on nonlinear discrete element theory
- Optimal control and nonlinear numerical simulation analysis of tunnel rock deformation parameters
- Nonlinear reliability of urban rail transit network connectivity based on computer aided design and topology
- Optimization of target acquisition and sorting for object-finding multi-manipulator based on open MV vision
- Nonlinear numerical simulation of dynamic response of pile site and pile foundation under earthquake
- Research on stability of hydraulic system based on nonlinear PID control
- Design and simulation of vehicle vibration test based on virtual reality technology
- Nonlinear parameter optimization method for high-resolution monitoring of marine environment
- Mobile app for COVID-19 patient education – Development process using the analysis, design, development, implementation, and evaluation models
- Internet of Things-based smart vehicles design of bio-inspired algorithms using artificial intelligence charging system
- Construction vibration risk assessment of engineering projects based on nonlinear feature algorithm
- Application of third-order nonlinear optical materials in complex crystalline chemical reactions of borates
- Evaluation of LoRa nodes for long-range communication
- Secret information security system in computer network based on Bayesian classification and nonlinear algorithm
- Experimental and simulation research on the difference in motion technology levels based on nonlinear characteristics
- Research on computer 3D image encryption processing based on the nonlinear algorithm
- Outage probability for a multiuser NOMA-based network using energy harvesting relays

