Abstract
In recent years, tourist attractions have become increasingly popular vacation destinations, leading to a gradual emergence of the tourism market and an improvement in the regulatory systems of scenic spots. However, these attractions frequently experience various abnormal behaviors (ABs). The existing abnormal behavior detection (ABD) algorithms are hindered by interference from the scenic area background, resulting in poor identification of ABs. The study proposed a background model constructed by an optimized Gaussian mixture model based on the background subtraction method to eliminate the background interference. Based on this model, an ABD method was established using action data based on spatio-temporal block detection and motion foreground effect map features. Experiments were conducted to train the video clips and action databases to establish the ABD model. In the study, algorithms were tested using computers, and different scenic spots were set up to validate tourists. Three scenic spot scenes with different time and environmental conditions were set up to detect tourist ABD, and the results were compared with different existing anomaly detection algorithms. Research has shown that the area under the receiver operation characteristic curve in outdoor scenes a and c is significantly larger than that in indoor scene b, with areas under the curves of 96.55 and 97.40%, respectively. In two outdoor research scenarios b and c, the area under the curve and equal error rate of the research algorithm (RA) are 88.14, 18.24, 98.12, and 7.55%, respectively, which are significantly better than the two compared algorithms. Although they are 97.31 and 6.29% in scenario a, slightly lower than the 95.18 and 12.69% of the compared algorithms, the expected time is very close to the ideal value, and overall, they have good performance. In addition, the average recognition accuracy of the RA (93.24%) is higher than that of the comparative algorithm (89.32%). The proposed ABD method has shown certain efficiency and accuracy in identifying ABs. It can provide effective decision-making support for scenic area management and has reference significance for improving the safety management quality of scenic area monitoring. By monitoring the AB of tourists, scenic area management personnel can take timely measures to ensure the safety of tourists and the order of the scenic area. In addition, the results of this study not only provide a new approach and method for detecting AB of scenic spot tourists, but also provide valuable reference significance and theoretical contributions in fields such as video surveillance, behavior analysis, and artificial intelligence.
1 Introduction
The challenges faced by tourist attraction managers are multifaceted, covering not only the daily trivialities of scenic area operations, but also in-depth considerations for tourist safety, environmental protection, and service quality improvement. During the peak tourism season, tourists exhibit various behaviors within the scenic area, including some abnormal behaviors (ABs) such as littering, damaging public facilities, and climbing without permission. These behaviors not only affect the environment of scenic spots, but may also pose a threat to the safety of tourists themselves. Therefore, management personnel need to develop effective environmental protection measures to reduce the damage of tourist activities to the environment. At the same time, they need to strengthen environmental protection publicity, improve tourists’ environmental awareness, enhance tourist satisfaction, and improve service quality and service. Among the potential consequences of undiscovered ABs, AB often comes with certain safety hazards, such as tourists climbing or wading in water without authorization within the scenic area. Second, the AB of some tourists can cause irreversible damage to the scenic area environment, affecting the overall image of the scenic area and the tourist experience. Finally, some serious ABs, such as theft and fighting, not only cause physical and mental harm to tourists, but also have a negative impact on the image and social security of the scenic area, damaging its reputation and image. In order to detect the AB of tourists, object anomaly detection algorithms have been proposed, but existing object detection and recognition algorithms are affected by background interference, resulting in poor recognition performance in video surveillance [1,2]. The high-efficiency and high-precision abnormal behavior detection (ABD) method has reference significance for improving the quality of monitoring and safety management in scenic spots. In order to deal with background interference and improve target recognition ability, a detection target description method combining background subtraction method (BSM) optimized Gaussian model with spatial block detection and motion foreground drawing features is proposed. By monitoring surveillance videos in the area, specific ABs can be identified and warned in real time. However, in practical applications, there may be challenges: in scenic areas, occlusion between tourists and scenic facilities may cause some or all of the target tourists’ bodies to be hidden, making it difficult to identify ABs. Second, the complexity of the scenic area environment makes it difficult to accurately update the background model. Lighting conditions may also cause changes in the brightness and contrast of the image. Then, there are various behaviors of tourists in the scenic area, and some ABs may manifest as complex action sequences. In response to these challenges, research can consider adopting more advanced deep learning algorithms to improve the accuracy and real-time performance of ABD. The research structure of this article is as follows: The first section introduces the background, significance, and prospects of AB recognition and detection in tourist attractions. Then, the second part focuses on establishing a background model based on optimized hybrid Gaussian model (GM) and designing the ABD method. The latter is also the focus and innovation of this study. The third part introduces the experimental verification using the model and method developed in the second part, and analyzes the experimental results. The fourth part summarizes the experimental results, discusses the shortcomings and limitations of the design, and outlines the future development direction
2 Related works
In tourism settings, implementing machine learning techniques and behavior recognition technology to identify AB can enhance the supervision system of scenic areas, reduce manpower expenditure, and enhance accuracy and real-time monitoring. Numerous researchers have provided their own research and perspectives regarding this topic. Arisoy and Kayabol proposed an algorithm for hyperspectral image anomaly detection based on nonparametric Bayesian background estimation. They used the Gaussian mixture model (GMM) for estimating parameters and model order of the proposed method for anomaly detection. It is shown that the detection performance of the method outperformed other methods on real hyperspectral datasets [3]. Dongling et al. proposed a GM-based adaptive update template defect enhancement algorithm. It has been demonstrated that the accurate localization of flaws was attained, effectively enhancing contrast and removing noise effects [4]. Cai and other researchers presented a shared state space model employing two recurrent neural networks to extract the background information and the temporal properties of the target sequence by adding a shared background information component to the state space model. The information that was retrieved was included in the state space model as linear Gaussian components, and a Kalman filter was used to perform the inference procedure. The model log-likelihood was used to optimize the model. Tests showed that the model beats the most advanced techniques and is able to retrieve the common information hidden in the data [5]. An artificial intelligence and sequence minimization (SMO) algorithm optimization model-based sports combined training behavior recognition model was proposed by Jiang and Tsai. The model lowers the false recognition rate and increases the recognition rate of sports movements, according to test results [6].
Preventing injuries, fatalities, and property damage requires identifying and eliminating ABs that pose a concern to public safety. The goal of numerous research projects has been to create intelligent video surveillance systems that can automatically identify unusual activity by identifying human behaviors. These investigations, however, have concentrated on identifying predetermined activities that are directly associated with the target’s AB, which could result in incorrect or missed detection of these acts. A method for identifying anomalous behaviors was put out by Kim et al. using sequence analysis of the identified action components to infer behavioral intent, and deep learning-based identification of non-semantic-level human action components segregated in a few-second timeframe. Through the analysis of real event data, it was determined that intent can be evaluated with accuracy using various action sequence elements. This opens up new avenues for monitoring ABs and getting insight into their intent, ultimately enhancing the capabilities of intelligent surveillance systems [7]. A technique for identifying unusual access behaviors in university civics catechism classrooms was presented by Hong et al. The outcomes demonstrated that the technique may successfully identify unusual access behavior [8]. Wu and Cheng focused on detecting AB of indoor people using a new in-room effective ABD framework to achieve detection of AB of indoor people. Fuzzy C-mean clustering was used to detect outliers in the data samples. Experimental studies showed that the detection framework has good practical application value [9]. Aiming at the problem of low performance of crowd ABD due to complex background and occlusion, Song and Sheng proposed a single-image crowd counting and ABD method based on multi-scale Generative adversarial network (GAN). An embedded GAN module with multi-branch generator and region discriminator was first designed for initial generation of crowd density map. Then, the proposed multi-scale GAN module was added to obtain crowd motion trajectories using synthetic optical flow feature descriptors to achieve AB classification. The technique can considerably increase the robustness and accuracy of crowd counting and ABD in real complicated scenarios, according to simulation studies [10].
In order to improve the performance of motion detection, Zheng et al. proposed a Gaussian modeling algorithm to repair holes and fractures caused by traditional frame difference methods. The proposed algorithm uses an improved three frame difference method and sets a threshold to predict the results used to obtain the accuracy of moving object detection. The experimental results show that the algorithm can suppress the generation and rupture of holes, reduce noise, and quickly and accurately detect motion [11]. The traditional theory of motion target detection has drawbacks such as clustering, background updating, inaccurate detection results, and low anti-interference performance. Hu and Xu used background subtraction to automatically capture the basketball shooting trajectory, improving the accuracy and efficiency of motion target detection. The results show that compared with the inter frame subtraction method (88%) and the optimal flow method (85%), the background subtraction method has better accuracy, with an accuracy rate of over 90%, and has good robustness when considering variable speed and non-rigid objects [12]. The AB of the abnormal population has significant variability, as well as significant ambiguity and uncertainty in video content. Li et al. proposed a new probabilistic framework called Variational ABD (VABD). The experimental results show that VABD is superior to state-of-the-art algorithms in detecting abnormal crowd behavior. Without increasing data, the area under the curve (AUC) of VABD on the IITB corridor reached 72.24%, which is nearly 5% higher than the state-of-the-art methods [13]. IITB Carrier is a large-scale surveillance dataset containing 4.83566 frames of video data, provided free of charge for research purposes, particularly for evaluating existing technologies for anomaly activity detection tasks.
In summary, researchers have examined data recognition and algorithm classification for AB recognition and detection. However, more in-depth work is needed to enhance the GMM, eliminate background interference, and improve the efficiency of AB recognition. The study suggests an optimized GMM which utilizes BSM and K-means clustering to establish a background model. Additionally, it merges the spatial time block detection and motion of ABD recognition method of the foreground effect map to detect AB among scenic tourists. The outcome of this research would provide a technical foundation for the safety monitoring and management of scenic spots.
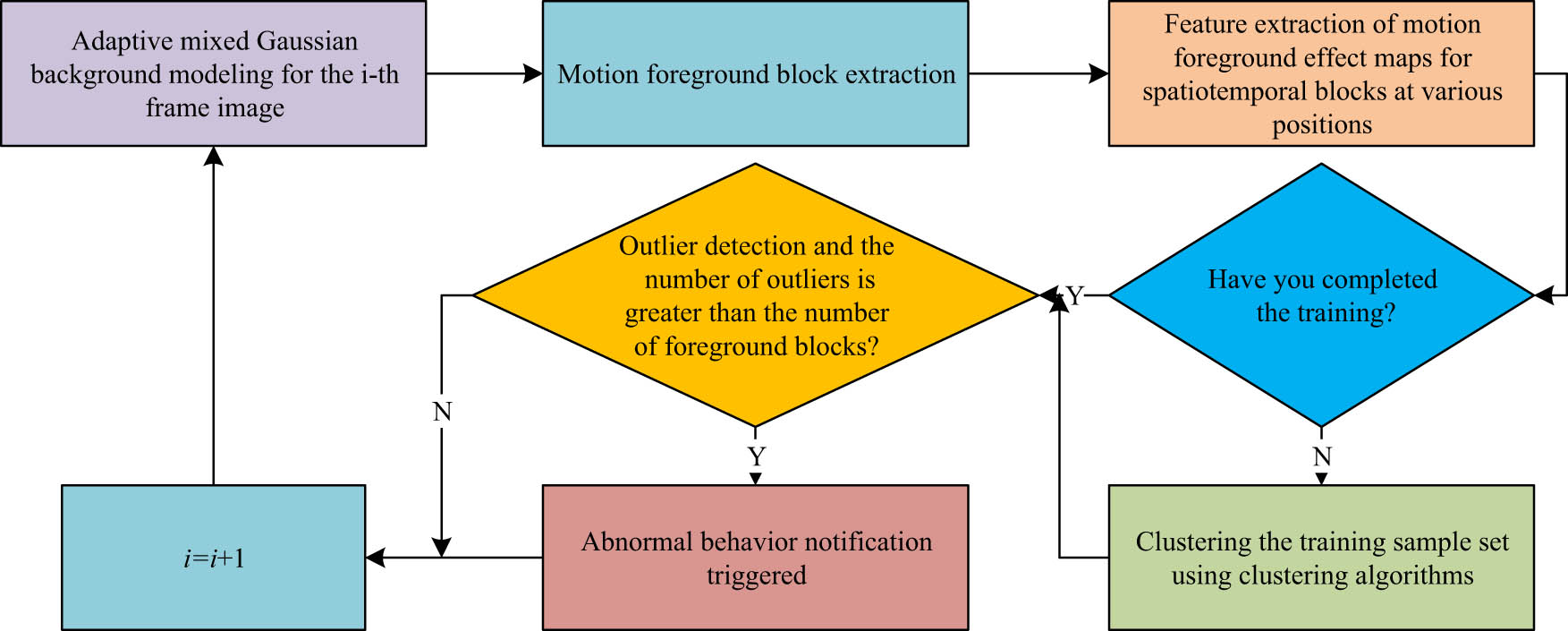
3 Background model and ABD method based on optimized Gaussian model
Efficient and controllable ABD methods can improve the efficiency of scenic area supervision and promote safety management. Identifying ABs of tourists through video surveillance is the main way of safety management in current scenic spots, which can directly reflect the behavior of tourists in scenic spots [14]. The research constructs a background model based on optimized GM to solve the interference of scenic background on the algorithm of identifying ABs, to improve the accuracy and efficiency of identification, and designs a new ABD method combining the spatial time block and motion effect feature map.
3.1 Hybrid Gaussian background model based on K-means clustering optimization
In recent years, with the increasing number of stampede incidents among tourists in scenic areas, large-scale crowd behavior analysis has become a research hotspot in the field of video surveillance. The existing anomaly detection algorithms have poor recognition performance due to the interference of scenic background. The dynamic changes and complexity of the scenic environment, such as weather changes, light and shadow changes, and changes in pedestrian flow, may make it difficult to accurately update the background model. For example, the dynamic process of tourists gathering and dispersing, or the continuous changes in natural elements such as trees and water surfaces, may interfere with the background model. Lighting conditions are a very important influencing factor in the environment of scenic spots. The lighting conditions vary greatly at different times, seasons, and weather conditions, which may lead to changes in the brightness and contrast of images, thereby affecting the accuracy of anomaly detection. Therefore, based on the background subtraction method, a background model optimized by GMM is proposed to eliminate background interference. As a commonly used motion target detection method, BSM is an inter-frame differencing method that utilizes a background model to update the background image, which is obtained by differencing the background image from the main object, with the advantage of being sensitive to the background and speeding up the computation. Figure 1 displays the BSM schematic diagram.
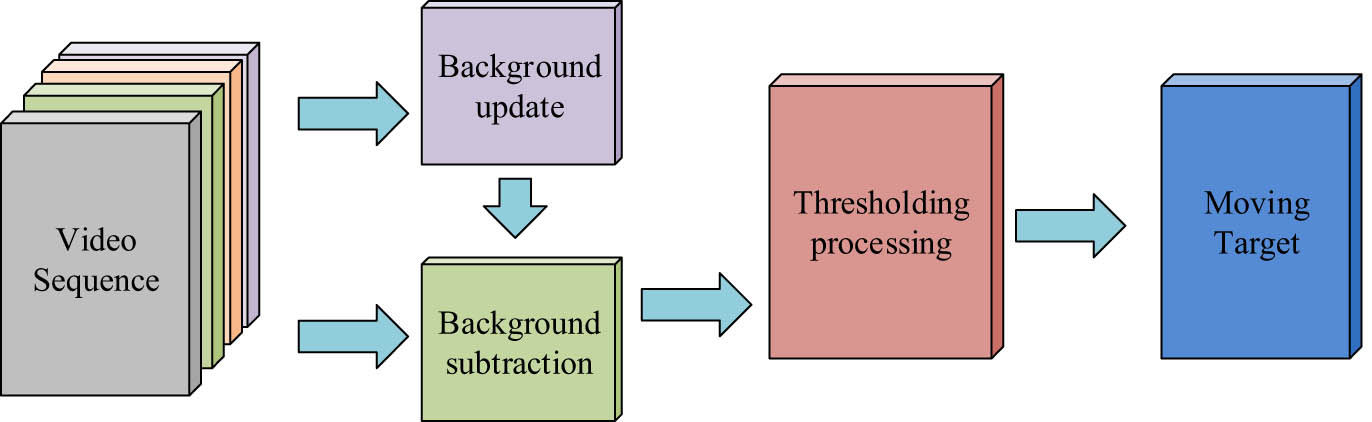
Schematic diagram of BSM.
The image is binarized according to BSM as in equation (1).
where
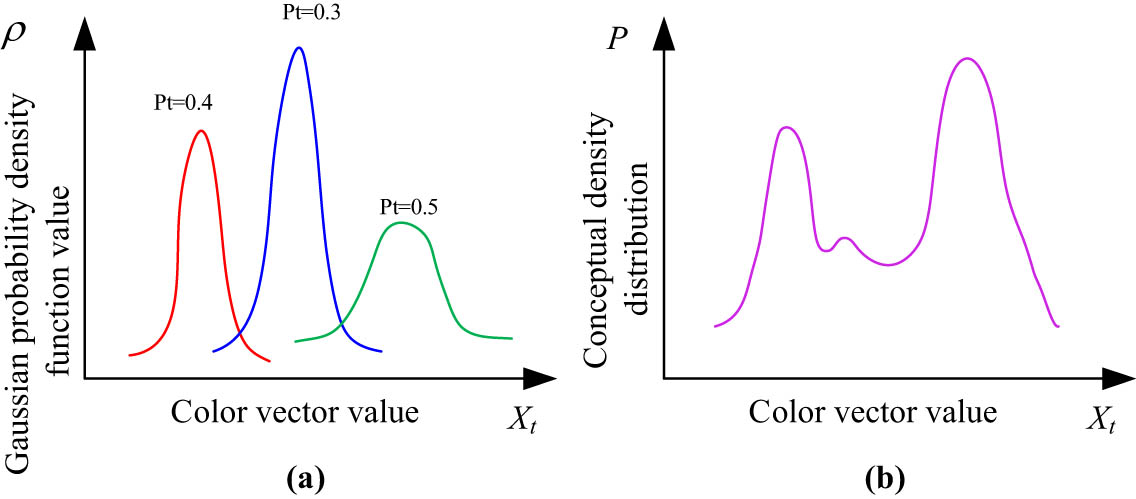
The unimodal GM and hybrid multimodal GM distribution curves. (a) Single Gaussian model distribution curve and (b) multimodal Gaussian model distribution curve.
In Figure 2, the single Gaussian distribution model curve disperses with different parameters and cannot fit well with the pixel distribution model. The mixed Gaussian distribution model combines the properties of a single Gaussian distribution model and has robust and real-time detection effects. Due to the complexity of the background in scenic areas and the uneven grayscale distribution, the study used mixed Gaussian for background modeling. The hybrid GM is modeled as in equation (2).
where
where
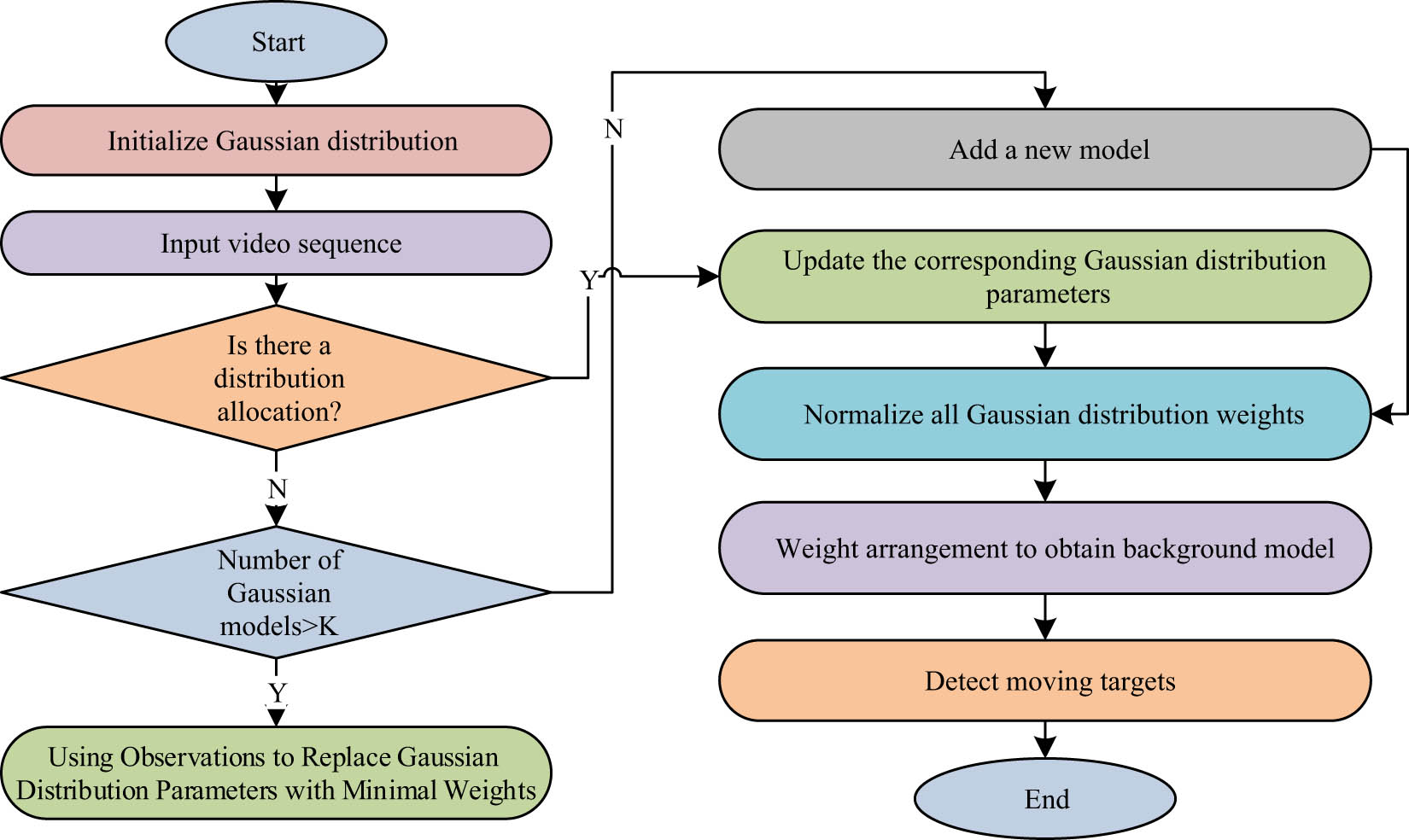
Algorithm flowchart of mixed Gaussian model.
3.2 Optimization of GMM based on K-means clustering
In Gaussian background model, background training of Gaussian background model is required, but human objects are almost always present in many videos and human targets have a great impact on the training of the model, so the study proposes an online K-means clustering algorithm for initialization of GM. This method is able to cluster the image sequence pixel gray values, update the correlation coefficient in the clusters, and construct the GD clustering number, thus improving the speed of the algorithm. The specific optimization process is as follows, first, at the moment
where
where
If the brightness value does not satisfy equation (6), it means that the pixel point does not belong to all the classes set, and a new class needs to be added. Additionally, the new class parameter’s starting value is shown in equation (7).
where
After completing the clustering for each pixel brightness value in the training sequence
where
3.3 AB recognition of tourists in tourist attractions combined with background models
Tourist attraction is a kind of regional place mainly for tourism and related activities, usually for tourists to visit and tour, vacation, fitness, etc. in their leisure time, but also with related facilities and provide corresponding tourism services in an independent management area [18]. AB refers to an unusual action that occurs in a normal position at a normal moment in a certain scenario, or an action that occurs in a non-normal position at a non-normal moment. The behavior is usually emitted by human beings, including some violent nature behaviors, which usually occur under the condition of more than two people and the action occurs fast, and some other nonviolent nature behaviors, which are usually initiated by one person and the action occurs over a longer period of time. Due to the abovementioned reasons, ABs need to be identified and monitored to provide safety technical support for tourist attraction managers [19]. The study proposes a background model based AB recognition method, and further designs the ABD method by optimizing the background model established by hybrid GM. Deep learning algorithms are excellent algorithms in the field of machine learning, which have significant development prospects in the field of image recognition and speech recognition, and can be used for recognizing pedestrians’ ABD, but there may be false detection in a certain frame or multi-frame images, and it may lead to ineffective tracking of the target on the scene with high crowd density, etc. The study proposes a detection target description method combining spatial block detection and motion foreground effect map features based on the background model established based on optimized GM, which is applied to detect tourist crowd ABD.
3.3.1 Description of detection objects in scenic area monitoring
In order to characterize the detected objects in scenic surveillance so as to locate the anomalous objects, the study is carried out in two phases, i.e., global anomaly detection and partial ABD. First, the video frames are viewed as a whole, and only the image frames of the anomalous objects are detected. Then, the video frame is segmented into equal blocks of airtime and the corresponding features are extracted separately to detect the anomaly object. The video frame is split up into several spatial blocks of the same size, using the space-time block as the detection object. Subsequently, the motion foreground effect map feature extraction is executed to derive the feature extraction frame flow, as illustrated in Figure 4.
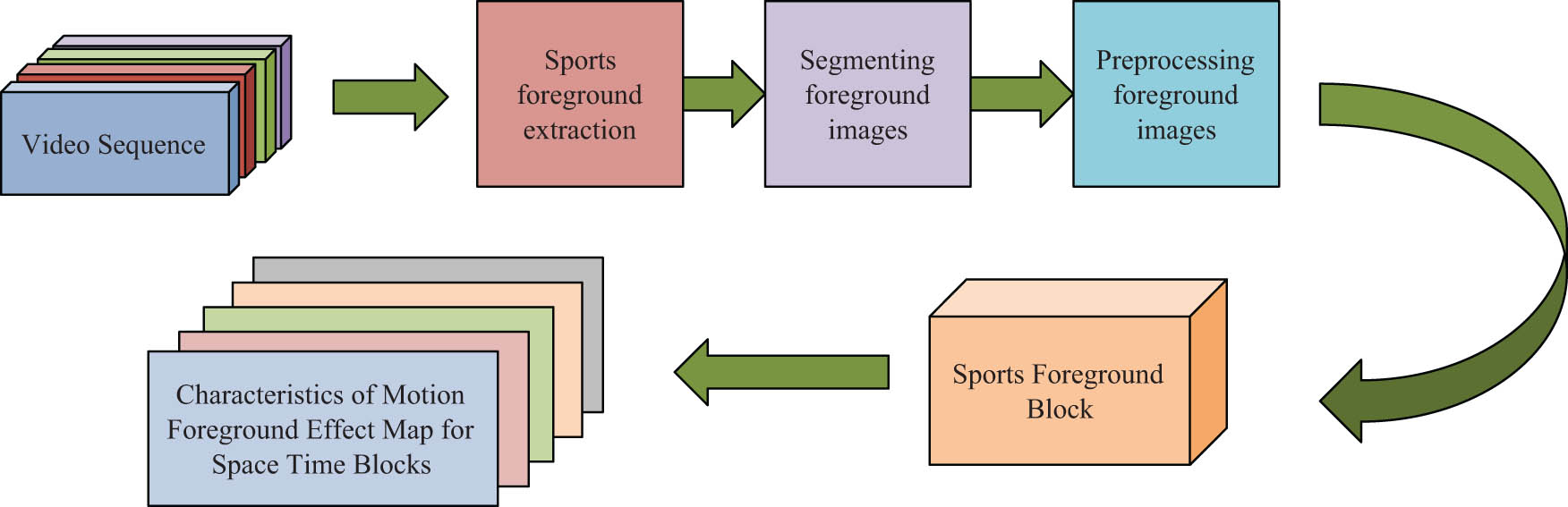
Block diagram of feature extraction for sports foreground effect maps.
The motion foreground block is obtained by first extracting the background region using the optimized hybrid GM, then obtaining the spatial block and foreground image, preprocessing the two to obtain the effect weight vectors, and finally averaging the effect weight vectors to obtain the feature description. The most effective way to analyze AB is to analyze the motion information of moving pedestrians, and generally AB will show a rapid change in the motion information [20]. The background model established by the study based on the optimization GM excludes the influence and interference brought by the scenic background on the motion foreground information, so the study focuses on the tourists’ abnormal motion information here. In the extraction stage of the motion foreground block, the null partition model is set, and the conditions for the selection of the motion foreground block are as in equation (10).
where
where
where the angle between the vector from the foreground block to the spatial block and the OF of
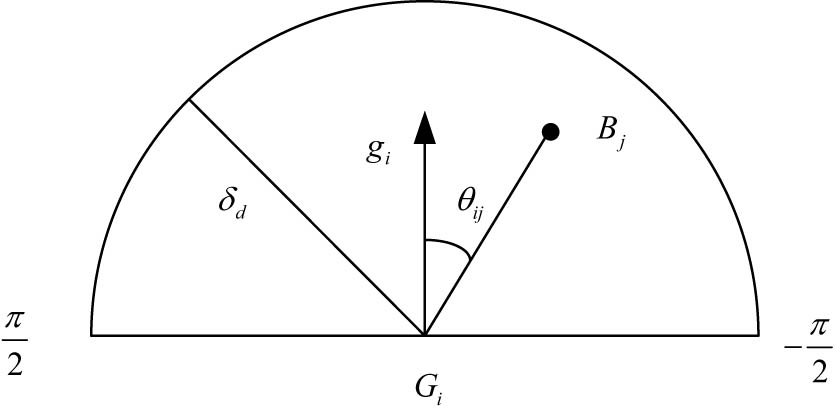
Motion model diagram of foreground block.
The effect weights of the motion foreground blocks on the spatial blocks are calculated as in equation (13).
where
where in order to make the extracted features have a high and strong differentiation, the motion direction
where
3.3.2 ABD based on motion foreground rendering features
On the basis of the above calculation of the features of the foreground effect map of crowd motion, the resulting features are clustered, and the specific process is shown in Figure 6.
Flow chart for ABD based on motion foreground effect map features.
The study used an improved clustering algorithm with optimized clustering centers for its clustering, first, the mutual distances between all the samples in the sample set were calculated, and the sample point with the largest distance was selected as the clustering center [23,24,25]. Once the optimal clustering category has been identified, the collection of clustering centers is obtained by extracting the set of feature samples of all airtime blocks using the trained clustering model. After counting the number of abnormal airtime blocks, the AB is found by measuring the distance between the feature samples of the detected airtime blocks and the features of the motion foreground effect map.
4 Validation experiment of ABD method for tourists in scenic spots
An experiment is conducted here to verify the feasibility and benefits of the research-proposed tourists’ ABD method, which is based on the background model design of optimized GM. It also provides technical support for the management of people’s safety and order in scenic areas. The experiment also analyzes the corresponding design parameters and experimental data results.
4.1 Experimental parameters and process design
The background model constructed based on optimized GMMs and subsequent anomaly detection methods need to consider multiple factors: in terms of computational efficiency, GMM training usually involves a lot of iterations and parameter optimization. By optimizing the algorithm and selecting appropriate initial parameters, training time can be significantly reduced. The optimized GMM and related anomaly detection algorithms should have high computational efficiency. For large-scale datasets or high concurrency scenarios, parallel computing techniques can be used to accelerate processing speed. In terms of resource requirements, in order to train and optimize the GMM model and perform real-time anomaly detection, it is necessary to have certain computing resources to support the required computing load and ensure the stability and reliability of the system. Computers were used in the studies to run the algorithm tests and confirm that the backdrop model created by the optimization GM and the ABD approach for scenic tourists was effective. The computer is configured for Windows, and the CPU is configured for CoreTM i7-6400, 12.4 GHZ. The experiments are mainly carried out on the MATLAB 2016 platform, and different scenic spots are set up for the verification of tourist ABD. The data selected for the experiment come from the surveillance video clips of a tourist attraction and the behavioral database provided by a hospital, and the video clips include ten surveillance videos. After preprocessing, the data set the actual specific frame numbers of the anomalous frames in the video, as shown in Table 1. This dataset includes ten video segments covering three scenarios (two outdoor and one indoor, set as a, b, and c, where a and c are outdoor), with a total frame rate of 7,670 and a video frame resolution of 320 × 240. The video frames where the crowd starts to scatter and run are called abnormal frames, and all of these frames are labeled as abnormal frames. The comparison algorithms selected for the study are the existing Histograms of oriented optical flow (HOF), Histogram of maximal optical flow projection (HMOFP), and the corresponding metrics are selected as AUC and Equal error rate (EER).
The actual number of abnormal frames in the video
| Scene | Video clips | Start frame count | Abnormal start frames | Abnormal end frames | End Frames |
|---|---|---|---|---|---|
| Scene a | 1 | 1 | 429 | 605 | 648 |
| 2 | 659 | 1,354 | 1,497 | 1,508 | |
| 3 | 1,594 | 1,657 | 1,988 | 2,183 | |
| Scene b | 4 | 2,247 | 2,597 | 2,642 | 2,719 |
| 5 | 2,813 | 3,018 | 3,294 | 3,514 | |
| 6 | 3,597 | 3,829 | 3,994 | 4,192 | |
| Scene c | 7 | 4,208 | 4,771 | 5,001 | 5,142 |
| 8 | 5,268 | 5,499 | 5,641 | 5,681 | |
| 9 | 5,920 | 6,154 | 6,288 | 6,905 | |
| 10 | 6,993 | 7,294 | 7,730 | 7,649 |
The study conducts experiments on the detection and recognition effect of the ABD method based on different behavioral actions of tourists. Based on different types of behaviors set in the behavioral database, such as running, jumping, squatting, falling, wandering, etc., the proposed algorithm is used to conduct behavioral detection of the study, and the related recognition accuracy is recorded.
4.2 ABD data measurement and analysis
The experiment verifies the RA’s detection performance in three scenarios and displays the corresponding receiver operation characteristic (ROC) curves, depicted in Figure 7(a). Additionally, the values for the AUC and EER indices are shown in Figure 7(b). In Figure 7(a), the area under the ROC curve in scenarios a and c is significantly larger than in scenario b, corresponding to the AUC of 96.55 and 97.40% in Figure 7(b), respectively. It can be seen that the detection performance in scene a and scene c is better, while the detection performance in scene b is relatively weak, indicating that the research method has better outdoor anomaly detection performance.
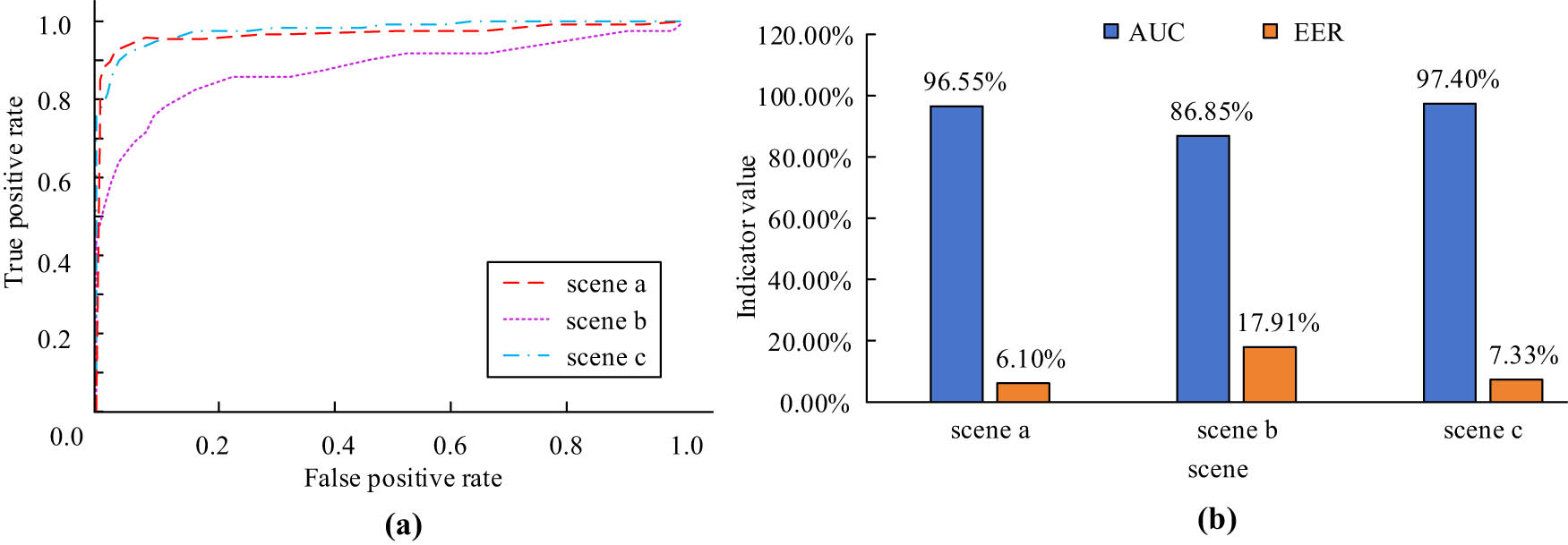
ROC curve, AUC, and EER index values of the proposed algorithm in three different scenarios. (a) ROC curves for in three scenarios of UMN dataset and (b) the AUC and EET indicator values of the proposed algorithm in three scenarios.
Table 2 displays the results of a study conducted to further validate the efficacy of the designed ABD method and examine the impact of various algorithms in various scenarios with varying performance indicators. The indicators were compared with RAs were AUC and EER. The AUC and EER of RA in scenarios b and c are 88.14, 18.24, 98.12, and 7.55%, respectively, which are obviously better than the two algorithms in comparison, although in scenario a, it is 97.31 and 6.29%, which is slightly inferior to the HMOFP algorithm’s 95.18 and 12.69%, but it is expected to be very close to the ideal value, and overall has a good performance.
Performance indicators of different algorithms in different scenarios
| Scene | Evaluating indicator | RAs (%) | HMOFP (%) | HOF (%) |
|---|---|---|---|---|
| Scene a | AUC | 97.31 | 98.14 | 95.18 |
| EER | 6.29 | 6.49 | 12.69 | |
| Scene b | AUC | 88.14 | 85.19 | 81.57 |
| EER | 18.24 | 25.36 | 27.43 | |
| Scene c | AUC | 98.12 | 97.45 | 96.09 |
| EER | 7.55 | 7.38 | 7.70 |
In the experiment, walking is set as normal behavior and others are AB, such as running, bending to walk, and falling. The corresponding data actions are collected for training to obtain the corresponding model. The backgrounds of the three traveling scenes are segmented for recognition and extraction to build the corresponding background models. In addition, the RA and Song proposed a single image crowd counting and ABD method based on multi-scale GAN networks (compared with Algorithm 1), Wu and the team proposed a new indoor effective ABD framework (compared with Algorithm 2), and Jiang et al. proposed an optimized model based on SMO algorithm and an artificial intelligence motion combination training behavior recognition model (compared with Algorithm 3) for recognition accuracy comparison, as shown in Figure 8. It can be seen that the recognition accuracy of algorithms 1, 2, and 3 is generally lower than that of the RA, with an average recognition accuracy of 89.32, 89.80, 88.23, and 93.27%, respectively. When identifying hovering actions, the accuracy of the RA and the comparison algorithm are 87.69, 84.02, 81.47, and 80.16%, respectively. This is because hovering actions are no different from normal actions, except for the length of action repetition. It can be seen that the algorithm proposed this time has good accuracy in identifying abnormal actions of tourists.
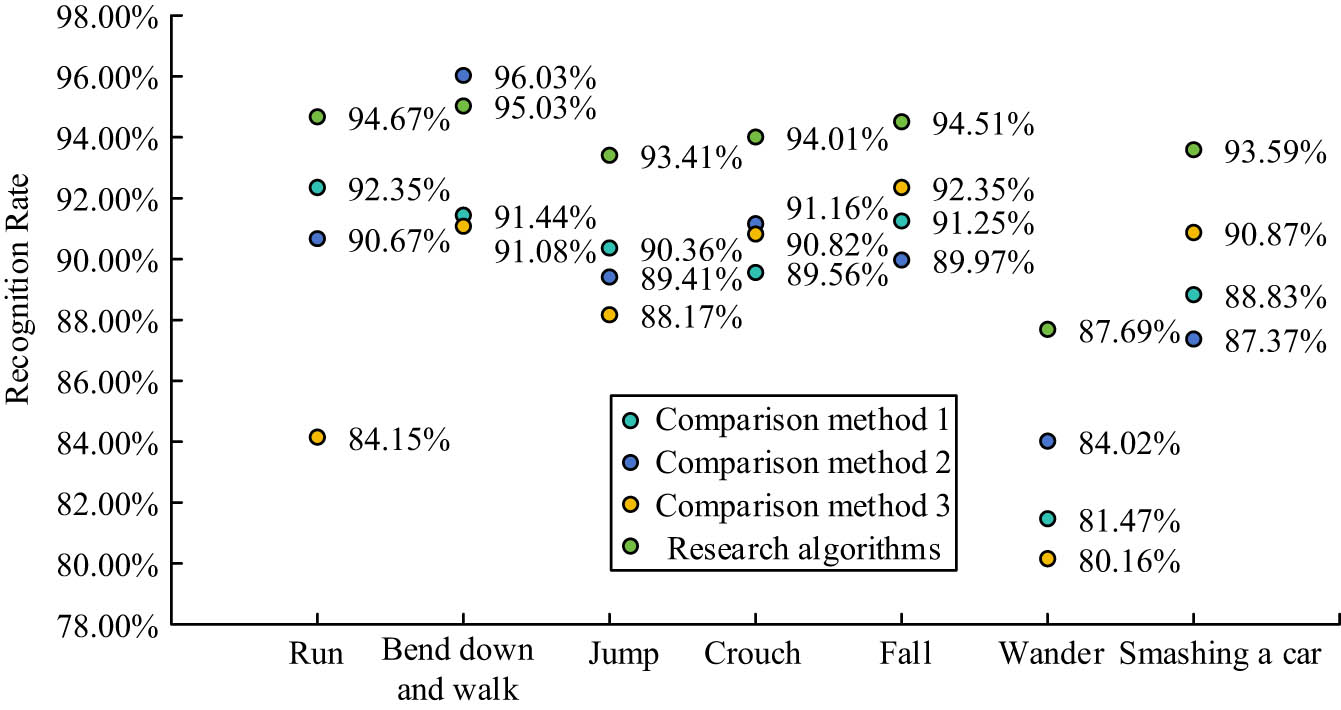
AB identification results.
As shown in Figure 9, in order to visually analyze the different features between AB and normal behavior, the study plotted the feature histograms of the two actions under different mode operators, and the normal behavior study selected the walking action, and AB selected the bending action. The target area contained in the image is relatively large compared to the background area, and there is a certain difference in grayscale between the background area and the target area. The peak in the histogram in Figure 9 is not obvious, indicating that the operator’s influence on the reflection of the histogram is not deep. Figure 9(a) and (b) show the histograms of the features of the stooping action under the two modes, and the stooping action shows flatter fluctuations. Figure 9(c) and (d) shows the histogram of the features of the walking action in the two modes, and the performance of the histogram of the features of the walking action fluctuates significantly.
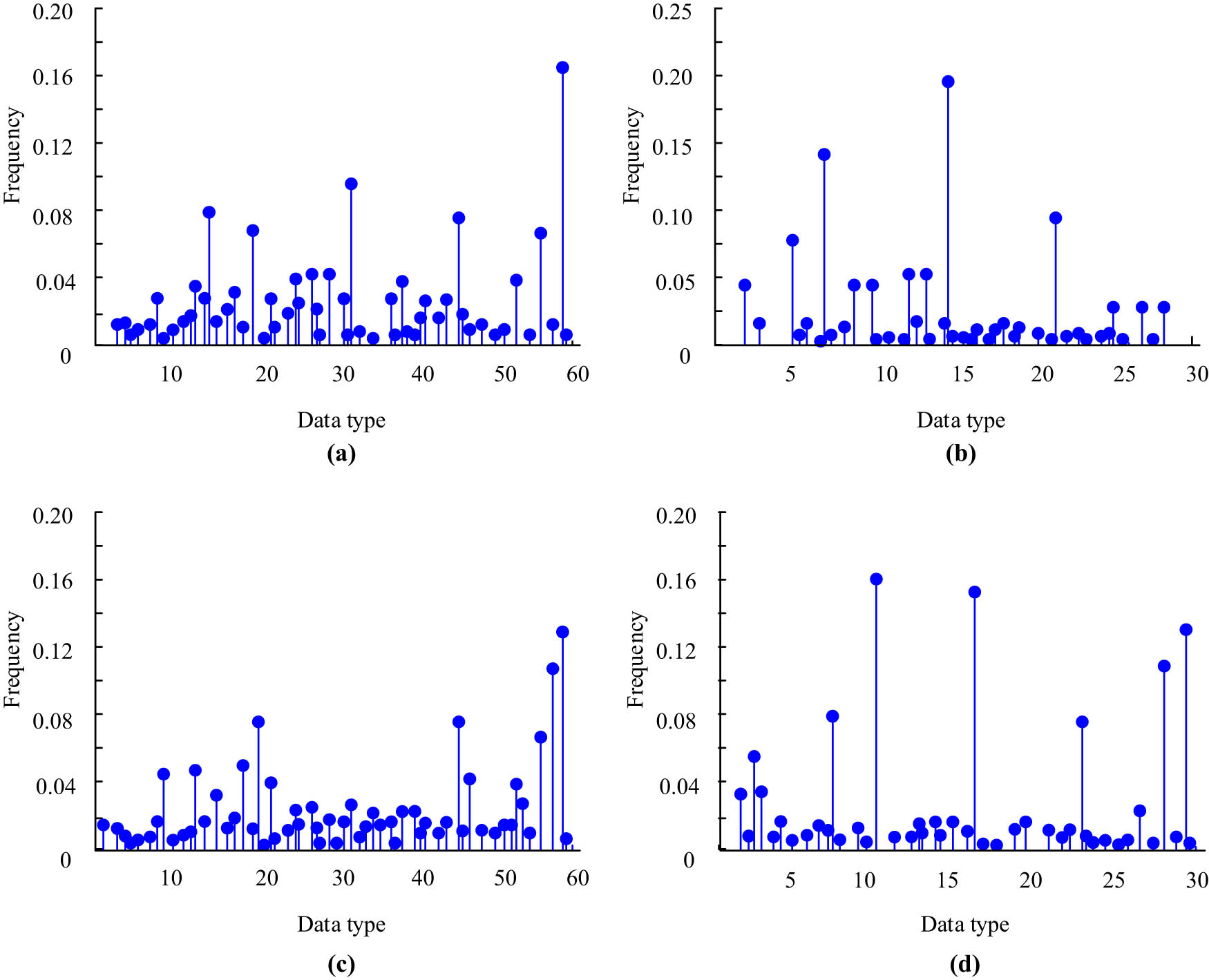
Characteristic histograms of two actions under different mode operators. Histogram of bending behavior in (a) Mode 1 and (b) Mode 2. Histogram of walking behavior in (c) Mode 1 and (d) Mode 2.
Figure 10 shows the aspect ratios of the minimum outer rectangular box obtained by morphological analysis after GMM segmentation of their motion foreground maps for normal walking and running actions under the color model. In Figure 10(a), the change in the aspect ratio of the rectangular box is more balanced and regular in the case of normal walking, and in Figure 10(b), the aspect ratio of the rectangular box in the case of running is a faster change with a short duration.
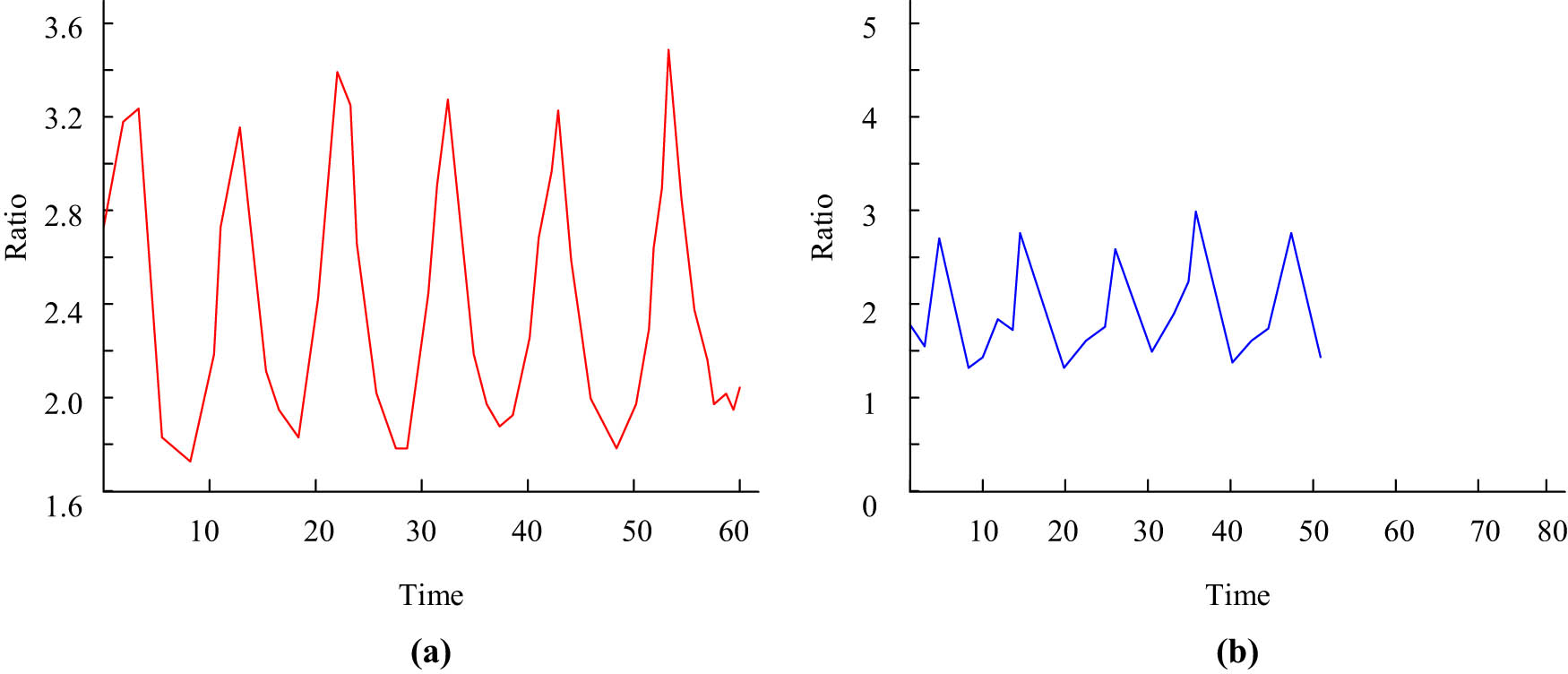
The aspect ratio of the minimum bounding rectangle in the foreground image of normal walking and running movements. (a) Normal walking and (b) running movements.
In addition, in order to compare the performance with the most advanced ABD technology, the experiment will iterate the RA with the latest ABD algorithm to obtain the convergence curve and obtain the accuracy of ABD, as shown in Figure 11. It can be seen that the convergence curve of the algorithm proposed in the study is stable, and finally stabilizes with the ABD algorithm at an objective function of around 2.51. The ABD algorithm has a fast convergence speed and a faster decrease in the objective function. Based on the accuracy, the proposed algorithm and ABD algorithm are 0.92 and 0.88, respectively, indicating a higher ABD accuracy of the RA.
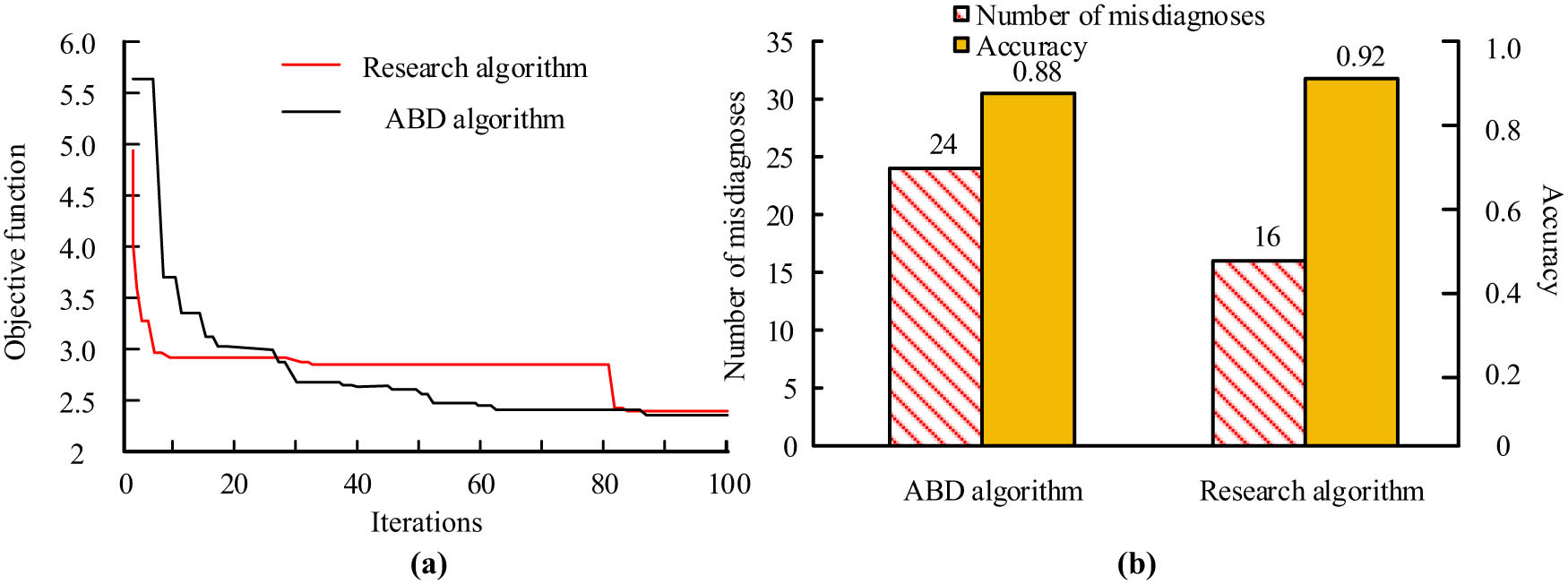
Comparison of convergence speed and accuracy with the latest ABD technology. (a) Iterative convergence curve and (b) tourist ABD accuracy.
5 Discussion
Using a combination of motion foreground effect map features and spatial block detection, the ABD method developed in this research, and based on the background model of optimized GM, a certain level of superiority in recognition efficiency and accuracy has been demonstrated through experiments. It can also offer a reference value for the regulation of AB for tourists in scenic spots. However, there is still insufficient research on the detection of AB in indoor and shadow experiments. Shadows can undergo significant changes with changes in light, and it is necessary to propose methods to eliminate these effects in future research to further improve the effectiveness of object segmentation. The study used background subtraction to construct and optimize a Gaussian model, which solves the problem of being easily affected by background interference in video surveillance detection and recognition. Combining spatiotemporal block detection and motion foreground effect map features, a detection target description method was developed to solve the problem of tourist ABD. In practical applications, researching algorithms can effectively ensure recognition efficiency and accuracy. The method proposed in the study has advantages in scalability or adaptability. In terms of scalability, the study can be applied to various application fields related to video surveillance, such as traffic safety monitoring, public management monitoring, etc. After optimization, the GMM can handle large-scale datasets and is easy to integrate with distributed computing frameworks. By distributing data on multiple nodes for parallel processing, it can significantly improve computational efficiency while maintaining the scalability of the model. In terms of adaptability, the research background model can be dynamically updated and adjusted based on real-time data to adapt to environmental changes. In ABD, the mixed Gaussian model can detect different outliers, and due to its elasticity, it can adapt to different types and quantities of outliers. Further improving the performance factors of anomaly detection methods based on optimized GMMs is an important research direction. The following is an in-depth analysis of these factors and improvement areas: complex GMMs require more computing resources and may face low training efficiency on large-scale datasets. A small dataset may lead to overfitting of the model, while insufficient data diversity may affect the model’s ability to identify AB. In addition, improper parameter initialization may lead to slow model convergence or trapping in local optima. Effective selection and extraction of target features can capture key behavioral information and improve the accuracy of anomaly detection. Potential areas for further improvement in research methods include structural optimization, parameter selection optimization, feature selection optimization, computational efficiency, and resource optimization, as well as effective integration with other model algorithms, all of which can further improve algorithm performance.
In addition, the research results can also be widely applied in fields such as public safety, smart homes and security systems, and traffic monitoring and management. By installing surveillance cameras and applying the aforementioned technologies, it is possible to monitor personnel behavior in real-time, detect suspicious or dangerous behavior in a timely manner, and ensure public order and personnel safety. In the home environment, intelligent security systems monitor the behavior of family members through cameras, which is of great significance for ensuring family safety. In the field of transportation, ABD can be used for traffic monitoring and management, real-time monitoring of vehicle driving trajectory and speed, identification of abnormal driving behaviors such as speeding, reversing, and changing lanes without lights, and real-time intervention and punishment through traffic management systems to improve road traffic safety levels.
During the research process, the privacy protection of tourist video information was allowed, and the use of monitoring technology was transparent and fair. When deploying monitoring technology, there were no restrictions or infringements on individual rights and freedoms. Monitoring technology has sufficient security. The processing and deployment of monitoring technology takes into account its impact and responsibility on society.
6 Conclusion
In tourist destinations, the trend is to recognize and provide timely warnings to the staff on the appearance of tourist ABs. However, real-time surveillance video used for manual AB recognition consumes a large amount of public resources and is ineffective. Furthermore, the diversity of application scenarios affects the accuracy of behavior recognition due to the variation in scenic spot backgrounds. To enhance the accuracy of AB recognition, this study presents an ABD approach that utilizes an optimized GM background model. The method merges motion foreground effect map features with spatial block detection. Experiments were conducted to validate the findings. The results indicated that the aspect ratio of the rectangular frame was more balanced and regular during normal walking, whereas during running, the aspect ratio changed more quickly and for a shorter duration. These findings enable the detection of abnormal movements. In scenes b and c, RA showed significantly better performance than the two compared algorithms with AUC and EER values of 88.14, 18.24, 98.12, and 7.55%. However, in scene a, its performance yielded a slightly inferior result with AUC and EER values of 97.31 and 6.29%, respectively, compared to the 95.18 and 12.69% achieved by the HMOFP algorithm. Nonetheless, it was anticipated to be very close to the optimal value and maintained good overall performance. The findings of the experiment show how extremely successful the ABD strategy suggested in the study is in terms of both performance and detection. With the booming development of the tourism industry, the safety and comfortable experience of tourists have become the core elements of tourism area management. The study proposes a background model based on optimized GMM and subsequent ABD methods, which are of great significance in strengthening the safety and management of tourist areas. Through efficient and accurate ABD, strong technical support is provided for the safety management of tourist areas, which not only improves management efficiency and safety, but also enhances tourist satisfaction and loyalty, laying a solid foundation for the sustainable development of tourist areas. Therefore, the tourism area management department should attach great importance to and actively apply this advanced technology to continuously improve the level of safety management and service quality. Although the experimental dataset used by the research institute is a publicly available and authoritative set of ABD videos with relatively simple scenes, actual monitoring videos have the characteristics of variable lighting and complex monitoring content, so more in-depth research is needed. And this study only found relatively common basic ABs. In practical applications, the accuracy of ABD may vary with changes in scenic area’s weather, brightness, etc., and may be unstable. Therefore, in subsequent research, the following suggestions were proposed: considering the variable application environment of the algorithm, the possible interference of back and forth motion in the background, and the influence of weather changes, Gaussian mixture background modeling method should be used to construct the background model in the motion detection process. During the detection process, different experiments were conducted for different environments, and several important parameters in the Gaussian model were adjusted to determine the empirical values of important parameters in different environments. A self-adaptive model update rate was studied for the update problem of GMMs in typical algorithms, which significantly improved the modeling speed and reflected the real background image in a more timely manner. This improved the efficiency of the entire model learning and system stability, and eliminated the shadows generated by moving targets to a certain extent. Based on the improved algorithm’s motion target detection results, motion target tracking is carried out using the Kalman filter prediction method. Under the premise of effectively detecting motion targets, it can quickly and accurately track targets in simple and more complex environments.
-
Funding information: The research is supported by Science and Technology Department of Shaanxi Province Study on Protection and Tourism Utilization of Yan’an Red Industrial Heritage under digital technology (2022GY-346); Yan’an University Special project on “Research and Interpretation of the Spirit of the 20th National Congress of the Communist Party of China” (2022YDZX20).
-
Author contributions: Xiaohua Liu: conceptualization, methodology, software, investigation, formal analysis, data curation, resources, supervision, writing – original draft, writing – review and editing.
-
Conflict of interest: The author declares that there is no conflict of interest.
-
Data availability statement: Not applicable.
References
[1] Amirabadi MA, Kahaei MH, Nezamalhosseini SA, Chen LR. Optimal power allocation in nonlinear MDM-WDM systems using Gaussian noise model. IET optoelectronics. IET Optoelectron. 2022;16(3):133–48.10.1049/ote2.12064Search in Google Scholar
[2] Yagli GM, Yang D, Srinivasan D. Reconciling solar forecasts: Probabilistic forecasting with homoscedastic Gaussian errors on a geographical hierarchy. Sol Energy. 2020;210:59–67.10.1016/j.solener.2020.06.005Search in Google Scholar
[3] Arisoy S, Kayabol K. Nonparametric Bayesian background estimation for hyperspectral anomaly detection. Digit Signal Process. 2021;111(7):102993.1–13.10.1016/j.dsp.2021.102993Search in Google Scholar
[4] Dongling Y, Xiaohui Z, Jianzhen Z, Nanxing W. An enhancement algorithm based on adaptive updating template with Gaussian model for Si3N4 ceramic bearing roller surface defects detection. Ceram Int. 2022;48(5):6672–80.10.1016/j.ceramint.2021.11.217Search in Google Scholar
[5] Cai R, Lin Z, Chen W, Hao Z. Shared state space model for background information extraction and time series prediction. Neurocomputing. 2021;468(11):85–96.10.1016/j.neucom.2021.10.010Search in Google Scholar
[6] Jiang H, Tsai SB. An empirical study on sports combination training action recognition based on SMO algorithm optimization model and artificial intelligence. Math Probl Eng. 2021;2021(Pt.31):7217383.1–11.10.1155/2021/7217383Search in Google Scholar
[7] Kim S, Hwang S, Hong SH. Identifying shoplifting behaviors and inferring behavior intention based on human action detection and sequence analysis. Adv Eng Inform. 2021;50:101399.1–11.10.1016/j.aei.2021.101399Search in Google Scholar
[8] Hong N, Wang X, Wang Z. Abnormal access behavior detection of ideological and political MOOCs in Colleges and Universities. Mob Inf Syst. 2021;2021(Pt.2):9977736.1–14.10.1155/2021/9977736Search in Google Scholar
[9] Wu C, Cheng Z. A novel detection framework for detecting abnormal human behavior. Math Probl Eng. 2020;2020(Pt.43):6625695.1–9.10.1155/2020/6625695Search in Google Scholar
[10] Song B, Sheng R. Crowd counting and abnormal behavior detection via multiscale GAN network combined with deep optical flow. Math Probl Eng. 2020;(Pt.45):6692257.1–11.10.1155/2020/6692257Search in Google Scholar
[11] Zheng D, Zhang Y, Xiao Z. Deep learning-driven Gaussian modeling and improved motion detection algorithm of the three-frame difference method. Mob Inf Syst. 2021;2021(4):1–7.10.1155/2021/9976623Search in Google Scholar
[12] Hu Y, Xu Y. Study on the automatic basketball shooting system based on the background subtraction method. Sci Program. 2021;2021(Pt.13):2634662.1–9.10.1155/2021/2634662Search in Google Scholar
[13] Li J, Huang Q, Du Y, Zhen X, Chen S, Shao L. Variational abnormal behavior detection with motion consistency. IEEE Trans Image Process. 2022;31:275–86.10.1109/TIP.2021.3130545Search in Google Scholar PubMed
[14] Wang R, Xie F, Zhao J, Zhang B, Sun R, Yang J. Smartphone sensors-based abnormal driving behaviors detection: serial-feature network. IEEE Sens J. 2020;21(14):15719–28.10.1109/JSEN.2020.3036862Search in Google Scholar
[15] Huang T, Fu R, Chen Y. Deep driver behavior detection model based on human brain consolidated learning for shared autonomy systems. Measurement. 2021;179(3):109463.1–18.10.1016/j.measurement.2021.109463Search in Google Scholar
[16] Gu M, Fei J, Sun S. Online anomaly detection with sparse Gaussian processes. Neurocomputing. 2020;403(11):383–99.10.1016/j.neucom.2020.04.077Search in Google Scholar
[17] Zongmin L, Jirui W, Jie L, Pengda L, Kai R. A novel multiple targets detection method for service robots in the indoor complex scenes. Intell Serv Robot. 2023;16(4):453–69.10.1007/s11370-023-00471-9Search in Google Scholar
[18] Qingfeng D, Jinguo LI. A distributed abnormal traffic detection scheme in internet of things environment. Comput Eng. 2022;48(8):152–9.Search in Google Scholar
[19] Hu X, Wang J. Detection algorithm of abnormal behavior in security for IIoT based on random inspection. Int Core J Eng. 2020;6(5):336–43.Search in Google Scholar
[20] Zhang H, Huang L, Wu CQ, Li Z. An effective convolutional neural network based on SMOTE and Gaussian mixture model for intrusion detection in imbalanced dataset. Comput Netw. 2020;177(18):107315.1–10.10.1016/j.comnet.2020.107315Search in Google Scholar
[21] Wang P, Wang P, Fan E. Violence detection and face recognition based on deep learning. Pattern Recognit Lett. 2021;142:20–4.10.1016/j.patrec.2020.11.018Search in Google Scholar
[22] Song JF, Wang SY, Zhao HL. Traffic flow detection at road intersections based on k-means and NURBS trajectory clustering. Math Probl Eng. 2020;2020(2):1383198.1–6.10.1155/2020/1383198Search in Google Scholar
[23] Williams A. Human-centric functional computing as an approach to human-like computation. Artif Intell Appl. 2023;1(2):118–37.10.47852/bonviewAIA2202331Search in Google Scholar
[24] Chen Y, Ashizawa N, Yeo CK, Yanai N, Yean S. Multi-scale self-organizing map assisted deep autoencoding Gaussian mixture model for unsupervised intrusion detection. Knowl Syst. 2021;224:107086.1–11.10.1016/j.knosys.2021.107086Search in Google Scholar
[25] Su Y. Target detection algorithm and data model optimization based on improved Gaussian mixture model. Microprocess Microsyst. 2021;81(Mar):103797.1–7.10.1016/j.micpro.2020.103797Search in Google Scholar
© 2024 the author(s), published by De Gruyter
This work is licensed under the Creative Commons Attribution 4.0 International License.
Articles in the same Issue
- Research Articles
- A study on intelligent translation of English sentences by a semantic feature extractor
- Detecting surface defects of heritage buildings based on deep learning
- Combining bag of visual words-based features with CNN in image classification
- Online addiction analysis and identification of students by applying gd-LSTM algorithm to educational behaviour data
- Improving multilayer perceptron neural network using two enhanced moth-flame optimizers to forecast iron ore prices
- Sentiment analysis model for cryptocurrency tweets using different deep learning techniques
- Periodic analysis of scenic spot passenger flow based on combination neural network prediction model
- Analysis of short-term wind speed variation, trends and prediction: A case study of Tamil Nadu, India
- Cloud computing-based framework for heart disease classification using quantum machine learning approach
- Research on teaching quality evaluation of higher vocational architecture majors based on enterprise platform with spherical fuzzy MAGDM
- Detection of sickle cell disease using deep neural networks and explainable artificial intelligence
- Interval-valued T-spherical fuzzy extended power aggregation operators and their application in multi-criteria decision-making
- Characterization of neighborhood operators based on neighborhood relationships
- Real-time pose estimation and motion tracking for motion performance using deep learning models
- QoS prediction using EMD-BiLSTM for II-IoT-secure communication systems
- A novel framework for single-valued neutrosophic MADM and applications to English-blended teaching quality evaluation
- An intelligent error correction model for English grammar with hybrid attention mechanism and RNN algorithm
- Prediction mechanism of depression tendency among college students under computer intelligent systems
- Research on grammatical error correction algorithm in English translation via deep learning
- Microblog sentiment analysis method using BTCBMA model in Spark big data environment
- Application and research of English composition tangent model based on unsupervised semantic space
- 1D-CNN: Classification of normal delivery and cesarean section types using cardiotocography time-series signals
- Real-time segmentation of short videos under VR technology in dynamic scenes
- Application of emotion recognition technology in psychological counseling for college students
- Classical music recommendation algorithm on art market audience expansion under deep learning
- A robust segmentation method combined with classification algorithms for field-based diagnosis of maize plant phytosanitary state
- Integration effect of artificial intelligence and traditional animation creation technology
- Artificial intelligence-driven education evaluation and scoring: Comparative exploration of machine learning algorithms
- Intelligent multiple-attributes decision support for classroom teaching quality evaluation in dance aesthetic education based on the GRA and information entropy
- A study on the application of multidimensional feature fusion attention mechanism based on sight detection and emotion recognition in online teaching
- Blockchain-enabled intelligent toll management system
- A multi-weapon detection using ensembled learning
- Deep and hand-crafted features based on Weierstrass elliptic function for MRI brain tumor classification
- Design of geometric flower pattern for clothing based on deep learning and interactive genetic algorithm
- Mathematical media art protection and paper-cut animation design under blockchain technology
- Deep reinforcement learning enhances artistic creativity: The case study of program art students integrating computer deep learning
- Transition from machine intelligence to knowledge intelligence: A multi-agent simulation approach to technology transfer
- Research on the TF–IDF algorithm combined with semantics for automatic extraction of keywords from network news texts
- Enhanced Jaya optimization for improving multilayer perceptron neural network in urban air quality prediction
- Design of visual symbol-aided system based on wireless network sensor and embedded system
- Construction of a mental health risk model for college students with long and short-term memory networks and early warning indicators
- Personalized resource recommendation method of student online learning platform based on LSTM and collaborative filtering
- Employment management system for universities based on improved decision tree
- English grammar intelligent error correction technology based on the n-gram language model
- Speech recognition and intelligent translation under multimodal human–computer interaction system
- Enhancing data security using Laplacian of Gaussian and Chacha20 encryption algorithm
- Construction of GCNN-based intelligent recommendation model for answering teachers in online learning system
- Neural network big data fusion in remote sensing image processing technology
- Research on the construction and reform path of online and offline mixed English teaching model in the internet era
- Real-time semantic segmentation based on BiSeNetV2 for wild road
- Online English writing teaching method that enhances teacher–student interaction
- Construction of a painting image classification model based on AI stroke feature extraction
- Big data analysis technology in regional economic market planning and enterprise market value prediction
- Location strategy for logistics distribution centers utilizing improved whale optimization algorithm
- Research on agricultural environmental monitoring Internet of Things based on edge computing and deep learning
- The application of curriculum recommendation algorithm in the driving mechanism of industry–teaching integration in colleges and universities under the background of education reform
- Application of online teaching-based classroom behavior capture and analysis system in student management
- Evaluation of online teaching quality in colleges and universities based on digital monitoring technology
- Face detection method based on improved YOLO-v4 network and attention mechanism
- Study on the current situation and influencing factors of corn import trade in China – based on the trade gravity model
- Research on business English grammar detection system based on LSTM model
- Multi-source auxiliary information tourist attraction and route recommendation algorithm based on graph attention network
- Multi-attribute perceptual fuzzy information decision-making technology in investment risk assessment of green finance Projects
- Research on image compression technology based on improved SPIHT compression algorithm for power grid data
- Optimal design of linear and nonlinear PID controllers for speed control of an electric vehicle
- Traditional landscape painting and art image restoration methods based on structural information guidance
- Traceability and analysis method for measurement laboratory testing data based on intelligent Internet of Things and deep belief network
- A speech-based convolutional neural network for human body posture classification
- The role of the O2O blended teaching model in improving the teaching effectiveness of physical education classes
- Genetic algorithm-assisted fuzzy clustering framework to solve resource-constrained project problems
- Behavior recognition algorithm based on a dual-stream residual convolutional neural network
- Ensemble learning and deep learning-based defect detection in power generation plants
- Optimal design of neural network-based fuzzy predictive control model for recommending educational resources in the context of information technology
- An artificial intelligence-enabled consumables tracking system for medical laboratories
- Utilization of deep learning in ideological and political education
- Detection of abnormal tourist behavior in scenic spots based on optimized Gaussian model for background modeling
- RGB-to-hyperspectral conversion for accessible melanoma detection: A CNN-based approach
- Optimization of the road bump and pothole detection technology using convolutional neural network
- Comparative analysis of impact of classification algorithms on security and performance bug reports
- Cross-dataset micro-expression identification based on facial ROIs contribution quantification
- Demystifying multiple sclerosis diagnosis using interpretable and understandable artificial intelligence
- Unifying optimization forces: Harnessing the fine-structure constant in an electromagnetic-gravity optimization framework
- E-commerce big data processing based on an improved RBF model
- Analysis of youth sports physical health data based on cloud computing and gait awareness
- CCLCap-AE-AVSS: Cycle consistency loss based capsule autoencoders for audio–visual speech synthesis
- An efficient node selection algorithm in the context of IoT-based vehicular ad hoc network for emergency service
- Computer aided diagnoses for detecting the severity of Keratoconus
- Improved rapidly exploring random tree using salp swarm algorithm
- Network security framework for Internet of medical things applications: A survey
- Predicting DoS and DDoS attacks in network security scenarios using a hybrid deep learning model
- Enhancing 5G communication in business networks with an innovative secured narrowband IoT framework
- Quokka swarm optimization: A new nature-inspired metaheuristic optimization algorithm
- Digital forensics architecture for real-time automated evidence collection and centralization: Leveraging security lake and modern data architecture
- Image modeling algorithm for environment design based on augmented and virtual reality technologies
- Enhancing IoT device security: CNN-SVM hybrid approach for real-time detection of DoS and DDoS attacks
- High-resolution image processing and entity recognition algorithm based on artificial intelligence
- Review Articles
- Transformative insights: Image-based breast cancer detection and severity assessment through advanced AI techniques
- Network and cybersecurity applications of defense in adversarial attacks: A state-of-the-art using machine learning and deep learning methods
- Applications of integrating artificial intelligence and big data: A comprehensive analysis
- A systematic review of symbiotic organisms search algorithm for data clustering and predictive analysis
- Modelling Bitcoin networks in terms of anonymity and privacy in the metaverse application within Industry 5.0: Comprehensive taxonomy, unsolved issues and suggested solution
- Systematic literature review on intrusion detection systems: Research trends, algorithms, methods, datasets, and limitations
Articles in the same Issue
- Research Articles
- A study on intelligent translation of English sentences by a semantic feature extractor
- Detecting surface defects of heritage buildings based on deep learning
- Combining bag of visual words-based features with CNN in image classification
- Online addiction analysis and identification of students by applying gd-LSTM algorithm to educational behaviour data
- Improving multilayer perceptron neural network using two enhanced moth-flame optimizers to forecast iron ore prices
- Sentiment analysis model for cryptocurrency tweets using different deep learning techniques
- Periodic analysis of scenic spot passenger flow based on combination neural network prediction model
- Analysis of short-term wind speed variation, trends and prediction: A case study of Tamil Nadu, India
- Cloud computing-based framework for heart disease classification using quantum machine learning approach
- Research on teaching quality evaluation of higher vocational architecture majors based on enterprise platform with spherical fuzzy MAGDM
- Detection of sickle cell disease using deep neural networks and explainable artificial intelligence
- Interval-valued T-spherical fuzzy extended power aggregation operators and their application in multi-criteria decision-making
- Characterization of neighborhood operators based on neighborhood relationships
- Real-time pose estimation and motion tracking for motion performance using deep learning models
- QoS prediction using EMD-BiLSTM for II-IoT-secure communication systems
- A novel framework for single-valued neutrosophic MADM and applications to English-blended teaching quality evaluation
- An intelligent error correction model for English grammar with hybrid attention mechanism and RNN algorithm
- Prediction mechanism of depression tendency among college students under computer intelligent systems
- Research on grammatical error correction algorithm in English translation via deep learning
- Microblog sentiment analysis method using BTCBMA model in Spark big data environment
- Application and research of English composition tangent model based on unsupervised semantic space
- 1D-CNN: Classification of normal delivery and cesarean section types using cardiotocography time-series signals
- Real-time segmentation of short videos under VR technology in dynamic scenes
- Application of emotion recognition technology in psychological counseling for college students
- Classical music recommendation algorithm on art market audience expansion under deep learning
- A robust segmentation method combined with classification algorithms for field-based diagnosis of maize plant phytosanitary state
- Integration effect of artificial intelligence and traditional animation creation technology
- Artificial intelligence-driven education evaluation and scoring: Comparative exploration of machine learning algorithms
- Intelligent multiple-attributes decision support for classroom teaching quality evaluation in dance aesthetic education based on the GRA and information entropy
- A study on the application of multidimensional feature fusion attention mechanism based on sight detection and emotion recognition in online teaching
- Blockchain-enabled intelligent toll management system
- A multi-weapon detection using ensembled learning
- Deep and hand-crafted features based on Weierstrass elliptic function for MRI brain tumor classification
- Design of geometric flower pattern for clothing based on deep learning and interactive genetic algorithm
- Mathematical media art protection and paper-cut animation design under blockchain technology
- Deep reinforcement learning enhances artistic creativity: The case study of program art students integrating computer deep learning
- Transition from machine intelligence to knowledge intelligence: A multi-agent simulation approach to technology transfer
- Research on the TF–IDF algorithm combined with semantics for automatic extraction of keywords from network news texts
- Enhanced Jaya optimization for improving multilayer perceptron neural network in urban air quality prediction
- Design of visual symbol-aided system based on wireless network sensor and embedded system
- Construction of a mental health risk model for college students with long and short-term memory networks and early warning indicators
- Personalized resource recommendation method of student online learning platform based on LSTM and collaborative filtering
- Employment management system for universities based on improved decision tree
- English grammar intelligent error correction technology based on the n-gram language model
- Speech recognition and intelligent translation under multimodal human–computer interaction system
- Enhancing data security using Laplacian of Gaussian and Chacha20 encryption algorithm
- Construction of GCNN-based intelligent recommendation model for answering teachers in online learning system
- Neural network big data fusion in remote sensing image processing technology
- Research on the construction and reform path of online and offline mixed English teaching model in the internet era
- Real-time semantic segmentation based on BiSeNetV2 for wild road
- Online English writing teaching method that enhances teacher–student interaction
- Construction of a painting image classification model based on AI stroke feature extraction
- Big data analysis technology in regional economic market planning and enterprise market value prediction
- Location strategy for logistics distribution centers utilizing improved whale optimization algorithm
- Research on agricultural environmental monitoring Internet of Things based on edge computing and deep learning
- The application of curriculum recommendation algorithm in the driving mechanism of industry–teaching integration in colleges and universities under the background of education reform
- Application of online teaching-based classroom behavior capture and analysis system in student management
- Evaluation of online teaching quality in colleges and universities based on digital monitoring technology
- Face detection method based on improved YOLO-v4 network and attention mechanism
- Study on the current situation and influencing factors of corn import trade in China – based on the trade gravity model
- Research on business English grammar detection system based on LSTM model
- Multi-source auxiliary information tourist attraction and route recommendation algorithm based on graph attention network
- Multi-attribute perceptual fuzzy information decision-making technology in investment risk assessment of green finance Projects
- Research on image compression technology based on improved SPIHT compression algorithm for power grid data
- Optimal design of linear and nonlinear PID controllers for speed control of an electric vehicle
- Traditional landscape painting and art image restoration methods based on structural information guidance
- Traceability and analysis method for measurement laboratory testing data based on intelligent Internet of Things and deep belief network
- A speech-based convolutional neural network for human body posture classification
- The role of the O2O blended teaching model in improving the teaching effectiveness of physical education classes
- Genetic algorithm-assisted fuzzy clustering framework to solve resource-constrained project problems
- Behavior recognition algorithm based on a dual-stream residual convolutional neural network
- Ensemble learning and deep learning-based defect detection in power generation plants
- Optimal design of neural network-based fuzzy predictive control model for recommending educational resources in the context of information technology
- An artificial intelligence-enabled consumables tracking system for medical laboratories
- Utilization of deep learning in ideological and political education
- Detection of abnormal tourist behavior in scenic spots based on optimized Gaussian model for background modeling
- RGB-to-hyperspectral conversion for accessible melanoma detection: A CNN-based approach
- Optimization of the road bump and pothole detection technology using convolutional neural network
- Comparative analysis of impact of classification algorithms on security and performance bug reports
- Cross-dataset micro-expression identification based on facial ROIs contribution quantification
- Demystifying multiple sclerosis diagnosis using interpretable and understandable artificial intelligence
- Unifying optimization forces: Harnessing the fine-structure constant in an electromagnetic-gravity optimization framework
- E-commerce big data processing based on an improved RBF model
- Analysis of youth sports physical health data based on cloud computing and gait awareness
- CCLCap-AE-AVSS: Cycle consistency loss based capsule autoencoders for audio–visual speech synthesis
- An efficient node selection algorithm in the context of IoT-based vehicular ad hoc network for emergency service
- Computer aided diagnoses for detecting the severity of Keratoconus
- Improved rapidly exploring random tree using salp swarm algorithm
- Network security framework for Internet of medical things applications: A survey
- Predicting DoS and DDoS attacks in network security scenarios using a hybrid deep learning model
- Enhancing 5G communication in business networks with an innovative secured narrowband IoT framework
- Quokka swarm optimization: A new nature-inspired metaheuristic optimization algorithm
- Digital forensics architecture for real-time automated evidence collection and centralization: Leveraging security lake and modern data architecture
- Image modeling algorithm for environment design based on augmented and virtual reality technologies
- Enhancing IoT device security: CNN-SVM hybrid approach for real-time detection of DoS and DDoS attacks
- High-resolution image processing and entity recognition algorithm based on artificial intelligence
- Review Articles
- Transformative insights: Image-based breast cancer detection and severity assessment through advanced AI techniques
- Network and cybersecurity applications of defense in adversarial attacks: A state-of-the-art using machine learning and deep learning methods
- Applications of integrating artificial intelligence and big data: A comprehensive analysis
- A systematic review of symbiotic organisms search algorithm for data clustering and predictive analysis
- Modelling Bitcoin networks in terms of anonymity and privacy in the metaverse application within Industry 5.0: Comprehensive taxonomy, unsolved issues and suggested solution
- Systematic literature review on intrusion detection systems: Research trends, algorithms, methods, datasets, and limitations

