Abstract
These days, 5G mobile technology highly influences the wireless communication process, which is more responsive than the other generation. However, the 5G communication process handles the speed and latency issues while transmitting data over the network. Especially in rural areas, most people face this speed and latency problem while connecting to the network. Therefore, the network uses massive amounts of data to analyse this problem by integrating 5G with the Internet of things (IoT). The IoT-based data transmission and collection helps manage the data capacity, connection, and transmission rate. Therefore, this study uses the novel secured narrowband IoT framework for 5G communication and operational goals based on their position in the market. The 5G network uses business connectivity and access information to manage the data transmission. The network uses cellular bandwidth and IoT devices to connect more during this process. According to the connection, the information is transmitted with the minimum delay. Thus, experimental results have proposed these parameters: an accuracy ratio of 92.5%, a security ratio of 94.4%, a reliability ratio of 93.5%, a latency ratio of 91.8%, a cost-effective ratio of 20.5%, and a throughput ratio of 25.4% compared to other methods.
1 Introduction
Customers can benefit from higher and more reliable communications since 5G’s improved technical performance and reliability. There is a huge interest in 5G now as it is the next generation of mobile communication networks [1]. In 5G mobile communication networks, ultra-dense networking and software-defined networking (SDN) technologies are widely used, which offer significant advantages in communication network mobility and reliability [2]. Traffic density, end-to-end latency, maximum rate, flexibility, and the number of connections increased with 5G mobile communication networks [3]. Reaching out to customers can allow large device connections and unique service scenarios [4]. It can handle triple play’s network data information interaction requirements and the Internet of things (IoT) [5]. The new 5G mobile communication network offers a broad range of capabilities and can be used in numerous applications. This requires highly high network security requirements [6]. 5G mobile communication systems can support all businesses by providing voice and data services [7]. Many new service requirements can be addressed using the 5G mobile communication network with a more comprehensive, efficient, cost-effective communications infrastructure [8]. The 5G mobile communication networks can maintain the security of devices on the access network [9]. Mobile device security and authentication are handled by a single security management system [10]. Mobile communication networks using 5G can provide a variety of security measures to protect the privacy of various connected devices from fulfilling the demand of private business and vertical industrial services [11]. SDN provides a network system that combines digital distribution sinking with centralized management to address the issue of business demand in the 5G mobile communication networks [12]. Consumer layer processing delays and transmission costs can be greatly reduced by distributing business qualities to sources closer to the customer’s location, making interaction increasingly enjoyable [13,14]. During implementation, mobile communication networks can transfer security management and control to the 5G network customer level [15].
Cellular bandwidth, IoT devices, and the 5G network enhance business connections and data access. Working together improves data transfer efficiency and brings several benefits. Faster data transfer and better connectivity between IoT devices and the leading network are made possible by 5G’s far higher data rates. A smaller number of IoT devices can transmit data at once thanks to the improved bandwidth, which allows for more data transfer capacity. In business settings with a large number of linked devices, this is helpful. 5G’s design makes it easier to link several devices in a given area, which improves scalability in heterogeneous business settings. Applications such as intelligent workspaces, industrial facilities, and commercial regions may be assured of an uninterrupted connection with this. The network’s ability to handle several connections at once is critical for many IoT deployments. Faster data transfer between IoT devices and the leading network is possible with 5G networks due to their much-decreased latency. Applications requiring rapid input, such as augmented reality in services or mission-critical industrial processes, place a premium on the capacity to react instantly. Data transmission efficiency and the ability to make quicker decisions are improved by lowering latency. With 5G network slicing, specialized virtual networks may be created for different types of businesses. This update allows companies to allocate dedicated network slices to specific IoT applications, allowing them to tailor their connection and bandwidth to meet their unique requirements. Slicing the network provides for separating IoT traffic, which reduces congestion and boosts network efficiency. Data processing may now occur closer to IoT devices thanks to 5G’s ability to incorporate edge computing functions. Reduced latency and improved data transmission efficiency result from this since less data must travel great distances to reach central servers. With the help of edge computing, IoT devices can make decisions independently, which means they can respond quickly and use less power from the cloud. Sophisticated authentication and encryption methods are a part of the 5G network’s security architecture. Protecting data accuracy and maintaining secret company data ensures secure data transmission among IoT devices and the network. Ensuring the continuous validity and access to information, the safety precautions of the network are crucial for securing IoT gadgets and data from cyber-attacks.
In business segments, the 5G system transmits many components of business-processing information [16]. Security management and control techniques can be tailored to the specific characteristics of every business. User layer network security can be addressed throughout the networking process [17]. Customers are a critical part of the network. Digital lowering is used in certain 5G mobile communication network basic functions to separate the appropriate functions, and the digital core network’s communication system is semi-open [18]. Many interactive and open data eventualities need a change to the network security management architecture, which has to go from centralized to decentralized [19]. As a result, the service slice processing technique has been used in the 5G mobile communication network structure, and security has become one of the important components in the planning process [20]. Accessible data are encrypted by mobile network operators within a single security management framework using a suitable encryption technique [21]. Information such as customer privacy and security is secured using authentication, and a reliable encryption method is used from the core network to the communication link when available [22]. After service slicing, the comprehensive evaluation of network capacity, communication, latency in information transmission, and security strategy can be completed to evaluate network security architecture and policy application properly. Slices of video and low-latency IoT services are integrated into 5G mobile networks [23]. An operator authenticates this service and customer characteristics together in the core cloud. A unified approach to authentication and security management is used in the edge cloud for applications that transmit more information than the main cloud. This is accomplished by emphasizing key authentication security management techniques. A low latency technique is used to create the information encryption technology, security management, and control architecture [24]. This study uses 5G communication networks as a research study to describe the security risks, needs, and experiences related to 5G mobile communications deployment. Major topics include business sector security, base station attack patterns detection, and customer security protection. To better understand the network’s technical challenges, we analysed important security defensive methods and provided references for 5G mobile communication network technical study and implementation. The main contributions of this study are as follows:
This research developed a narrowband IoT framework (NB-IoT) network and evaluated various installation options using NB-IoT devices and a long-term evolution (LTE) base station in this paper.
The 5G spectrum can allow digital communication networks to transfer data at higher frequencies. A proposed private authorized NB-IoT network addresses security and latency criteria and worldwide spectrum installation opportunities.
Analysing the proposed communications technology, factors such as network compatibility, installation cost, security, and mobility influence the selection of wireless connections.
The remainder of this study is structured as follows: The relevant work and debate are described in Section 2. The design of the novel secured narrowband IoT framework (NSNB-IoTF) utilized for 5G communication is presented in Section 3. The findings and comparison to an existing approach are outlined in Section 4. Based on the analysis and discussion from the preceding section, Section 5 comes to an end.
2 Related work
The accuracy, reliability, throughput, safety, latency, and NSNB-IoTF design outperform existing methods. Improving 5G communication in business networks through an integrated protected NB-IoT raises several concerns that need careful investigation. There are many moving parts in implementation, and problems like integration complexity, transition phase disruptions, and the need for comprehensive compatibility testing are all parts of the process. A strong security strategy is necessary to resolve worries that introducing a new framework may lead to security holes and cyberattacks. The framework’s advanced capabilities can impact energy use and overall system performance, and they may need significant resources. Therefore, scaling and resource utilization must be prioritized. Training users and adoption are challenges that organizations must face. These challenges include dealing with resistance to change and ensuring employees are adequately trained on the new system. According to Varga et al. [25] demonstrated different communications needs for industrial IoT, including high dependability, low latency, adaptability, and security. Due to the 5G, mobile technology’s basic ability to deliver these was a close choice for enabling the Industrial IoT. In this article, they choose to identify major research challenges and solutions connected to 5G-enabled industrial IoT with the assistance of early requirements and promises from both sectors. This includes mobile edge cloud applications and industrial IoT support requirements for 5G and private campus network security and blockchain technologies. In addition to evaluating the existing problems and solutions, the paper’s goal was to make relevant comparisons in each area to infer the existing research limitations.
Vuojala et al. [26] initialized that the 5G could increase mobile technology adoption outside the communications sector, connecting an ever-increasing number of devices and services. Different spectrum access methods were required to address the various 5G business demands and the problem of spectrum scarcity. This article should illustrate significant characteristics of spectrum access methods and evaluate their feasibility for 5G vertical application models. They proposed five alternative spectrum access options for 5G vertical network service providers (VNSPs) to provide network services to end customers or other businesses. The service brands in the spectrum granting process were identified, and their responsibilities were analysed. These parameters were analysed for each scenario to determine its appropriateness for VNSPs.
Wang [27] explored the industrial, logistics, distribution, accounting, marketing, finance, human resources, and other applications that were part of an enterprise system (ES). Providing real-time data, ESs were designed to automate. Sharing computer resources, sophisticated features such as income Human Resource Management (HRM) subsystems and focusing on small and medium-sized businesses were some of the features they provide. This research proposed and implemented an Enterprise Human Resource Management System (EHRMS) to address IoT technology’s HR problems. A standard module-based HRM framework was suggested, with most of the modules used in other well-known frameworks.
According to Togou et al. [28], the 5G was expected to enable numerous new applications in numerous disciplines. These applications have various requirements (e.g., high data rate, low latency, high reliability, and high availability). To meet these needs, 5G networks encourage network slicing and mobile edge computing. The architecture described in this article, distributed blockchain-enabled network slicing (DBNS), enables service and resource providers to actively contract resources to guarantee good performance for their end-to-end solution. Global service provisioning, a key component of their framework, enables dynamic resource distribution through a blockchain-based contracting procedure. The goal was to improve the user experience while lowering capital and operating expenses for providers.
Energy management reduces quality of service (QoS). Shuvo et al. [29] introduced that scheduling small cells in 5G networks was important for customer energy efficiency and QoS. Users of mobile applications demanding high data rates have added to the problem. The literature’s energy-saving methods were limited by their dependence on historical information on two-state small-cell operating modes. A nonlinear optimization technique was used to arrange small cells. A meta-heuristic evolutionary algorithm (MHEA) was then provided to help solve the problem in polynomial time. The proposed method includes four small-cell operating modes to reduce energy usage while dependent on QoS. For example, their proposed algorithm surpasses existing energy savings and switching latency work.
Abbas et al. [30] evaluated the 5G mobile network supports a wide variety of services with varying performance, bandwidth, reliability, and latency requirements. Instead of providing homogeneous resources to all services, network virtualization allows them to be heterogeneous. This research designed and deployed an intent-based network slicing system (IBNSS) to slice and manage core network and RAN resources efficiently. Through reducing technology, network configurations were now fully automated, saving costs. It includes an IBN application that manages, controls, and monitors network slice components. Also, there are many uses of IoT in traffic issues and cloud storage encryption to provide more secure and efficient performance [31,32].
This proposed research solution tries to improve the performance compared to the above solutions. This research took into account several factors based on the results of the survey of EHRMS, DBNS, MHEA, and IBNSS techniques in terms of accuracy/security/reliability/latency/cost-effective/throughput ratios. As a result of this study, the NSNB-IoTF for 5G communication and operational goals based on their position in the market are covered in this article, which enables overcoming the traditional obstacles mentioned above.
3 Proposed method
IoT connection and services using LTE-based radio access. NB-IoT has been used to support global device systems for mobile communication (GSM), LTE, and 5G communication systems. Optimizing the cellular IoT evolution packet system provides better coverage, installation flexibility, deep penetration, and reduced energy usage. Its wide range of frequency bands allows for a highly flexible solution. For example, the minimal frequency requirements for uplink and downlink allow one GSM frequency inside an LTE network to be used for NB-IoT implementation. This research evaluates a standard industrial NB-IoT network demonstrating recent NB-IoT development. We demonstrated that NB-IoT is better for major business wireless systems. The research evaluates IoT energy usage, cost, latency, and device security requirements for NB-IoT implementation in a cyber-connected society. However, as evaluated, NB-IoT equipment maintains the authority to communicate on any LTE frequency in a location.
The business allows LTE devices to be connected to cellular networks by secure narrowband data transmission. Due to LTE’s slow cost benefits, businesses, including less advanced economies, can adopt the technology within the next 5 years. IoT usage is increasing rapidly; as a result, the physical and digital worlds have become more connected. IoT can increasingly influence how business leaders, designers, and industries approach research, innovation, marketing, and security. Introducing innovations into a business where customer expectations change is challenging. These businesses can use IoT to improve their service and communication. IoT forces businesses to aim beyond the digital product and adapt industrial processes to keep up with change. Businesses can use IoT data to identify themselves, manage real-time changes, and make future-focused decisions. A business can evaluate whether an IoT solution can address a specific development challenge and how it can benefit customers. IoT industrial sensors can improve production processes by collecting data streams from end to end.
The network optimizes connectivity by leveraging cellular bandwidth and IoT devices through strategic mechanisms. QoS prioritization classifies data based on urgency, allocating higher priority and bandwidth to critical information. Dynamic bandwidth allocation adjusts transmission rates based on connection status, ensuring efficient resource utilization. Low-latency protocols reduce communication overhead, enabling quick responses in real-time applications. Integrating edge and fog computing brings data processing closer to the source, minimizing latency and enhancing overall efficiency. Continuous connection status monitoring allows dynamic adjustments in routing paths, optimizing data transmission. Predictive analytics further contributes by anticipating connectivity issues and enabling preemptive resource allocation. Together, these mechanisms prioritize and maximize information transmission, minimizing delays and promoting efficient communication in the network.
Moreover, IoT can influence business models to address the challenge of digital disruption, requiring IoT-enabled industries. Data analysis can help identify production problems and increase daily output. To use IoT applications to improve services, businesses can communicate security requirements. Every device on a business network represents a threat. Business model and cost reduction are essential in data security. Encrypting 5G communications and IoT data streams reduces this vulnerability.
Figure 1 shows the model for 5G and IoT data transmission in parallel and IoT structure based on 5G. Audio and video communications using the 5G network and sensor information can be sent through the IoT network. Two types of 5G and IoT data transmission models have been combined: the time-changing and power-splitting models. The time-changing model divides the transmission time into several periods, each of which has two-time slots. 5G and IoT transmitters can operate simultaneously on time-division multiplexing-style IoT nodes. Therefore, as the transmitter and receiver are in perfect time synchronization, the receiver can properly send and receive information. 5G and IoT connectivity needs may be met by tailoring the duration of time slots. This is similar to the 5G data transmission model in that the IoT node uses a part of the power for 5G and the rest for IoT data transmission. The receiver can recover data using successive interference cancellation in 5G and IoT data demodulations. The initial data transfer resources devoted to 5G and IoT communications can subtract from 5G performance attributed to increased IoT performance. Therefore, the cost–benefit trade-off between IoT and 5G communications is evaluated. The object naming service (ONS) control unit comprises IoT devices and internal applications. With an ONS server, customers can obtain the IoT server. An IoT uploading server provides a data service interface to exchange relevant data between IoT devices, making it a scalable and adaptable data service. The internal middleware interfaces with the server through the 5G core network to collect IoT data. Efficient data transmission is mainly the responsibility of the 5G core network. The system’s two most important components are the mobile management entity (MME) and base station. The MME’s providing gateway device can integrate multiple Internet protocols and unify the 5G network’s accessing devices. In addition to achieving local area short transmission access needs, the gateway can connect to a network and conduct forwarding, control, signal exchange, and other activities. Wireless terminals communicate directly with evolved nodes, considering a base station in telecom networks. Evolved nodes are hardware systems connected to mobile networks that can communicate with wireless terminals directly. Additional features such as IoT business terminal management, security authentication, and others help keep things safe in the IoT ecosystem. To connect to the 5G system, the integrated network uses a base station with a reader and middleware to connect the wireless sensor network. Integrating a sensor and middleware can significantly expand the perceived geographical reach of IoT data. We can perform operations on IoT server data using the terminal and make necessary changes.
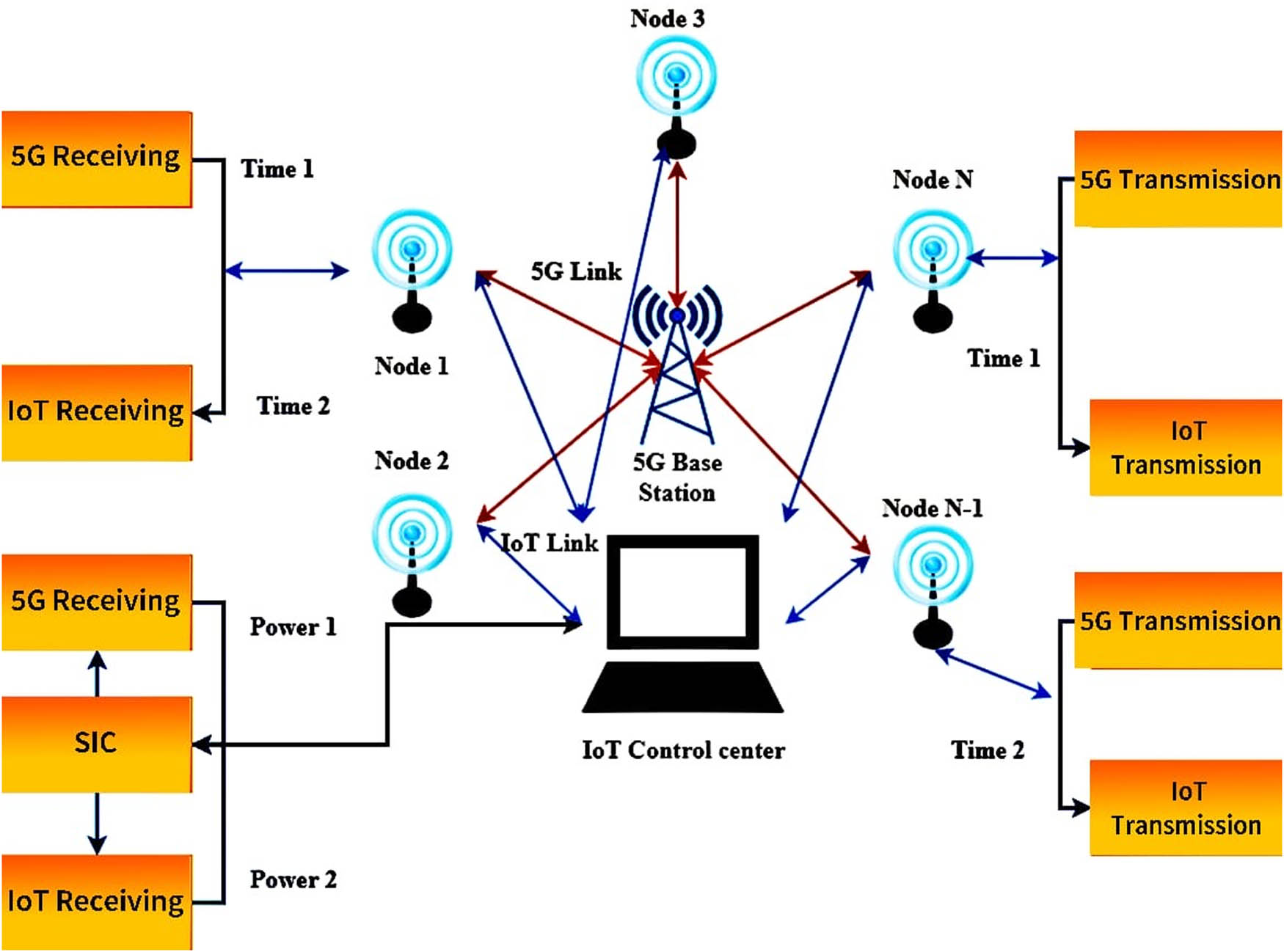
Model for 5G and IoT data transmission in parallel and IoT structure based on 5G.
Figure 2 shows the five important business IoT ecosystem entities. The business IoT ecosystem is shown in Figure 1 by the five major companies. A business cannot be considered a part of a single sector, a component of a business ecosystem that encompasses several sectors. Ecosystems can have a flat mesh structure and a hub-centred top structure. IoT ecosystems everywhere are organized around big IT businesses that connect with many smaller ones. At the same time, those in the single market are structured around small, flexible IoT enterprises, providing a horizontal lattice structure. An enterprise ecosystem helps businesses collaborate and compete to support new products and services, grow markets, and promote innovation. As a specific kind of business ecosystem that includes businesses and people involved in the IoT and the socio-economic environment in which it operates, an IoT business ecosystem. An IoT ecosystem includes hardware platform suppliers, software platform providers, and standards organizations. Stakeholders from many industries provide some value to a business IoT ecosystem. Since IoT services need multiple devices and software modules from various suppliers, most businesses lack technical expertise in IoT services. The knowledge of the business IoT ecosystem can assist in selecting the most appropriate IoT platforms to create new services. Supply chain management (SCM) businesses, for example, can try to use IoT platforms connected to SCM to create IoT services efficiently and cost-effectively. Enterprise IoT ecosystem main stakeholders are identified in this article: software platform developers, network technology providers, hardware platform developers, implementation providers, and customers. These important players work together to benefit businesses, users, and customers by promoting innovation, expanding markets, and facilitating cooperation and competition.
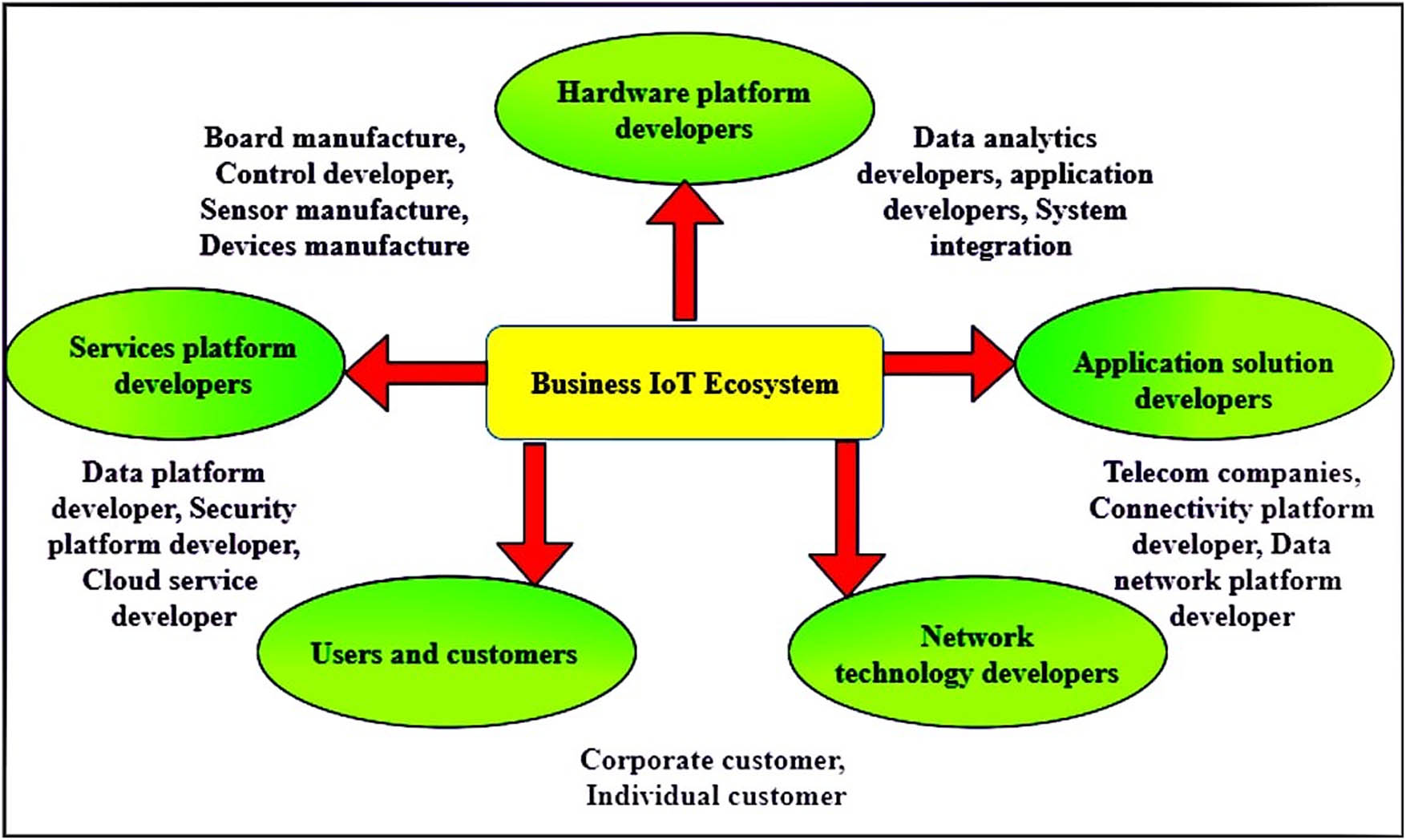
The five important business IoT ecosystem entities.
3.1 Software platform developers
Many fundamental functions are observed in the IoT applications. It enables IoT application developers to focus on the customized aspects of their services, minimize duplication, and improve the IoT application process by making common functionalities accessible in an IoT software platform. Cloud-based and operating system platforms are all types of IoT software platforms. Various academic and industrial IoT data systems have been developed to help with data clearing, processing, and storage tasks. Healthcare, business, security, transportation, and education benefit from new choices made possible by digitalization. Digitalization, which offers practically limitless storage and processing capacity, complements IoT and helps resolve its limitations. Data are stored on the cloud IoT platform, which serves as an operator and a distributor, sending data to services for processing. Small, low-cost hardware platforms have helped the rapid expansion of corporate IoT. Hardware platforms in the IoT contain developing systems and off-boards, including microcontrollers, CPUs, and other components. These platforms can focus on physical events and connect to other systems to collect monitoring data. IoT hardware platforms such as smartphone, laptop, passive components, tablets, sensor, and actuator.
3.2 Hardware platform developers
They can make their little IoT gadgets more effective. Several IoT microcontroller has system-on-a-chip (SoC) technology, which integrates input, output, CPU, secondary storage, memory, and power devices on a microchip. Occasionally, the speed, power, and space of the commercial off-the-shelf boards used in IoT devices are constrained. Each device makes high-performance systems with graphics processing units, fixed-function field-programmable gate array implementations, and application-specific integrated circuits popular among developers thanks to integrated chips, thinner printed circuit boards, and lower total prices. Sensors are effective factors for gathering current environmental data. Some IoT sensors are connected to an IoT controller, which becomes involved based on activity. Battery-powered sensors can now have their durations extended due to the development of energy-recovery technologies. Open-source hardware platforms are more widespread as commercial hardware systems become difficult for new developers to implement.
3.3 Network technology providers
The development of IoT networks uses several top wireless carriers and platform providers, including bluetooth low energy, low power wide-area (LPWA) network technologies, and Zigbee. Most of the time, devices connect directly, independent of a network. A low-power, minimum data rate, and immediacy wireless ad-hoc network is one of the enterprises’ most popular device-to-device communication methods. These technologies are extensively used in short-range device connections. 5G enables enormous IoT devices to communicate in a novel setting. To meet the increased demand for fast information rates, small latency, low energy consumption, and greater network security, 5G was created. Huge machine-type communication, improved mobile broadband, and ultra-reliable short-latency communication are all features of 5G services. The effectiveness of IoT-enabled 5G networks and IoT applications may be constrained by security and privacy issues brought on by the development of edge devices for particular services and logical network slicing.
3.4 Implementation providers
Different IoT platforms are used by internal developers, systems integrators, and third-party developers. Applications and solutions are scattered and challenging to scale because of the IoT, and they take time to develop. Integrating and communicating across devices can be important for implementing end-to-end solutions. To address this important issue, designers and developers must use platforms to develop, evaluate, and improve applications and services. By combining IoT software and hardware platforms, developers can generate new IoT services. Because of the lack of technical and conceptual documentation, even experienced developers find it difficult to develop IoT systems. In the development of implementations, systems integrators play a crucial role due to their extensive experience in integrating IoT solutions across various industries and businesses. Creating applications for users and consumers is something that systems designers help businesses identify architectural components and develop. Users and consumers use IoT-based services to enhance company processes and customer service. Users benefit from and support IoT innovation. To help users and customers, IoT can help them manage business security and energy costs while improving device maintenance and monitoring ships and cars.
Figure 3 shows an NB-IoT network from end to end. NB-IoT implementation in a 5G system is shown in Figure 3. Low-power wide-area networks and the 5G licensed entire frequency standards in cellular systems are the frameworks under which NB-IoT functions. NB-IoT has been designed to work with current LTE and 5G architectures for minimal complexity and high performance. To maintain this standard as simple as possible, several complex features of current LTE and 5G systems have been removed to preserve power and improve the number of communication channels. The NB-IoT application layer is designed to offer a 200 kHz system bandwidth for both uplink and downlink. In this study, end device (ED) refers to any NB-IoT wireless and network access customers.
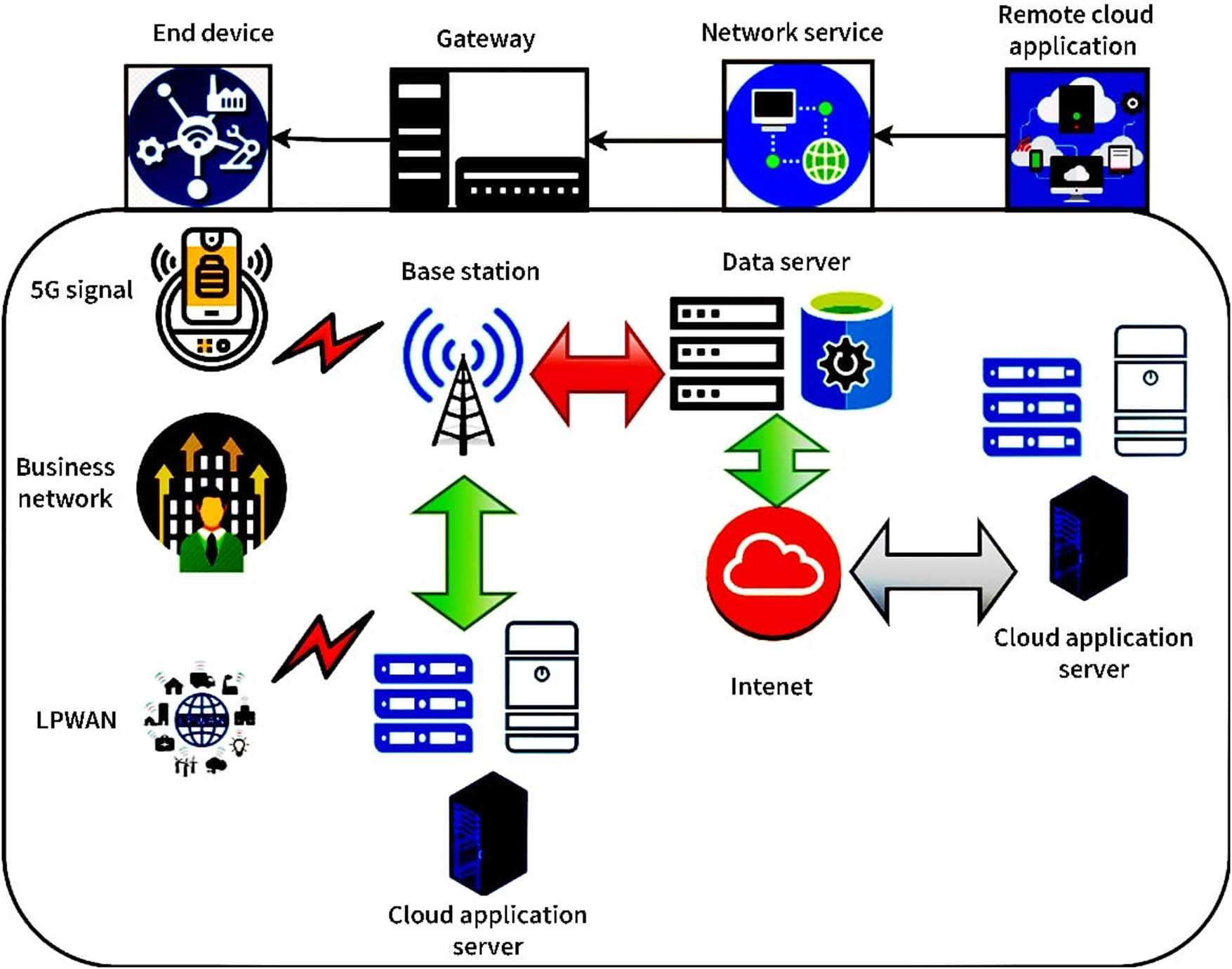
An NB-IoT network from end-to-end.
Data are collected and sent to the network using various EDs in the NB-IoT system. A gateway and network device, ED, can be connected to the network through radio resources provided by the base station. Many devices serve as gateways, including wireless modems, access points, and sink nodes. As a means to connect electronic information systems, ED, with network services, the gateway is important. The network service’s responsibility is to shift and direct ED data across several networks. There are types of network services: remote and local. Local network services connect a radio gateway to a cloud application server. There are two kinds of cloud computing: local cloud computing and remote cloud computing. Cloudlets, cloud technology, and mobile edge computing are all examples of small clouds. ED are any NB-IoT clients in the radio and network access. In the NB-IoT era, heterogeneous gadgets collect data and send it to the network. Gateway service: Embedded device provides radio source to QwsdzzAA’attach ED to the network. Devices that perform as gateways include wireless broadband, access points, and sink nodes. The gateway is important in data transfer from ED to the data network. Network service: It transfers and routes ED information across networks. The network service connects a radio gateway to a cloud application server. Application servers can be in local and remote clouds. Local clouds are cloud application servers, while distant clouds are data servers.
Figure 4 shows the NB-IoT technology advantages. Large packet size and high data rate: NB-maximum IoT’s packet size and data rate are determined by network provider offers and the capacity of the NB-IoT devices, as compared to long-range (LoRa) technologies, which have maximum download speeds of 84 and 140 direct messages, respectively. The maximum LoRa packet size is 62 bytes for both the uplink and the downlink. Lora’s data rate ranges from 0.1 to 0.6 kbps, with packet sizes maximum at 12 bytes for uplink and 8 bytes for downlink. A standard LTE-M and NB-IoT download speed of megabits per second is available, with the second capable of increasing with the implementation of novel LTE-M releases. Improved coverage: It can enhance coverage for applications in remote locations such as offshore oil platforms and stations hundreds of miles distant by utilizing repeat transmission of up to 128 and 2,048 bits for Up link and Down link, correspondingly. While LTE has superior indoor coverage, NB-IoT has a 20 decibels improvement in maximum coupling loss over LTE. It uses 5G infrastructures to provide indoor and deep coverage with a better response rate than LoRa. It can achieve that at low frequencies below 1 GHz, exceeding LoRa’s maximum distance of 20 km.
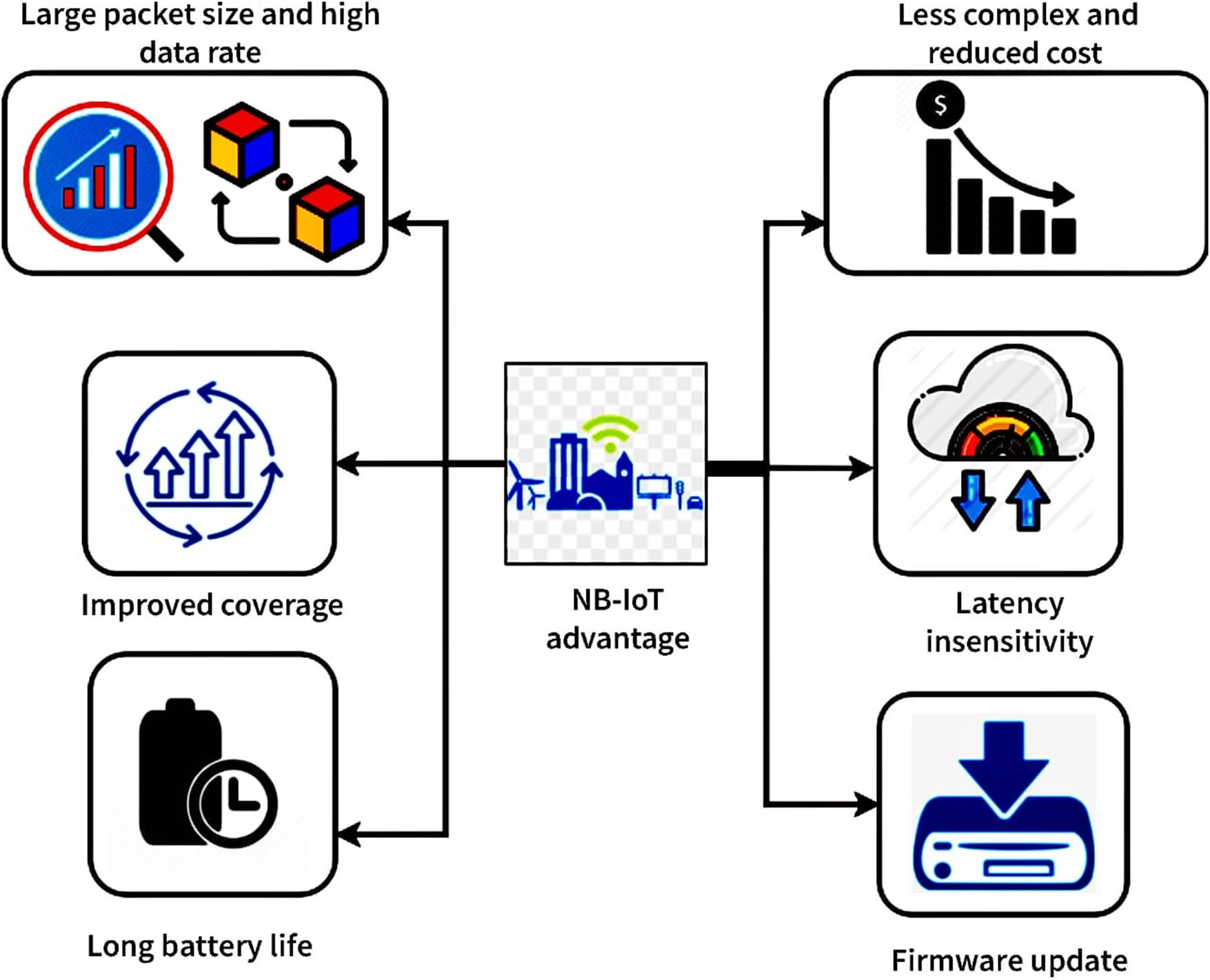
NB-IoT technology’s advantages.
One approach to enhance coverage to 100 km is to perform a software update. Latency insensitivity: The NB-IoT network does not promote latency; technology can tolerate an error transmission latency of up to microseconds in applications such as security devices. Packet delivery latencies are usually caused by the method of transmission, the frequency of transmission, the time, the acquisition process of cellular, and so on. Hybrid automatic–repeat–request and early data transmission are innovative methods developed to reduce repeat and ensure successful transmissions. Long battery life: Batteries can last for years using NB-IoT due to low power consumption and high connection losses (up to 164 decibels). Due to huge reduced power backoff, batteries improve operational efficiency. During the inactivity, while connected to the base station, the user equipment enters power save mode and cannot be contacted by the ethical objectives. In extended discontinuous reception mode, the hardware enters into an inactive state and is interrupted by sensor input data, which the software implementation can manage. Possible firmware update: Firmware is difficult to achieve on the NB-IoT network, and it has potential. Research designs have an extremely slow downlink transmission speed, making it impossible to maintain with software upgrades. Roaming can be difficult as a result, reducing the mobility of the device even further. The number of network nodes supported by NB-IoT on a major carrier is impressive. To maximize the use of the resources unit allocation, each access point is given all its 3.75 kHz suitable for different and 15 kHz bandwidths. Less complex and reduced cost: To keep the NB-IoT standard low-cost, the user equipment has to have limited storage capacity, operate at a lower frequency, have one transmitter, and use a basic modulation method. There is greater packet delay, higher channel interference, and less estimation incorporated into the transmission connection for less complicated network nodes than for more advanced tasks.
Figure 5 shows NB-IoT network access. NB-IoT system: The physical layer is composed of the different between sensor nodes that receive and send data to the base station according to the commands. Mobile network nodes and base stations transmit the sensing data from NB-IoT devices in the NB-IoT network. Data are received from the base station and stored in an NB-IoT cloud, where it is processed. This platform can be a business such as cloud services and entirely different based on the end-user. The application programming interface is part of the NB-IoT cloud platform. The main NB-IoT security issues differ from this layer. The NB-IoT application server provides a user application server for NB-IoT items. The businesses produce their specifications. An hypertext transfer protocol request from any IoT device to the NB-IoT cloud platform goes by the device, then to the NB-IoT device when a user request data from any IoT device.
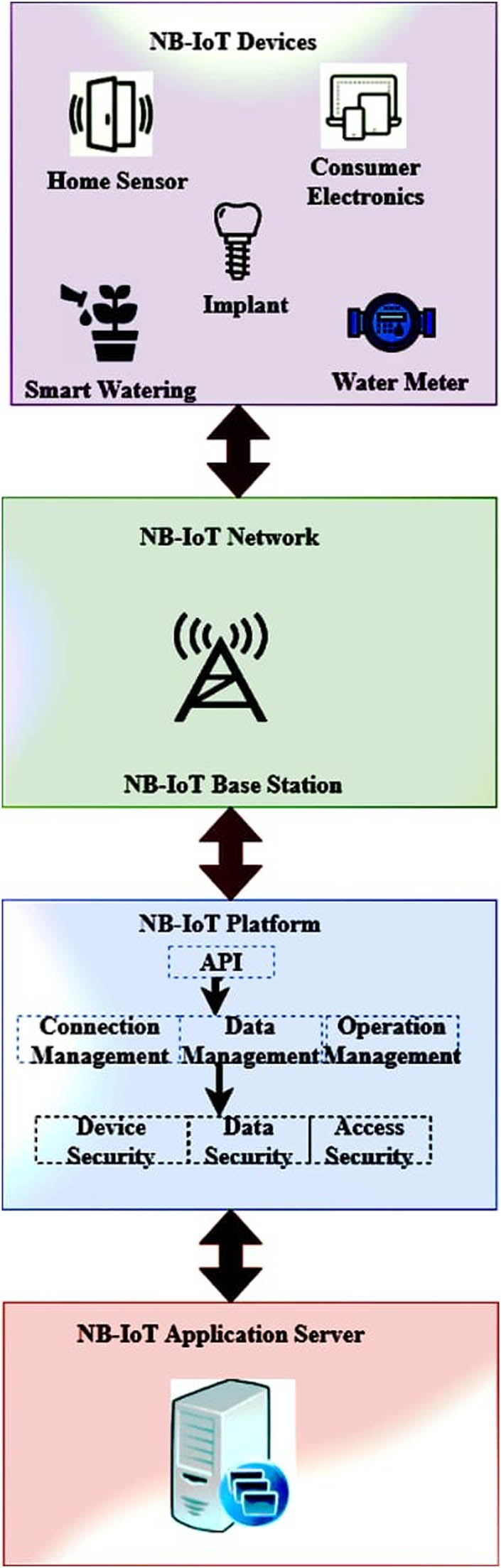
NB-IoT access network.
The device can respond to the cloud platform based on the received request. Some 5G wireless technologies are being proposed by different network operators, while others are currently operational. NB-IoT and LTE have authorized 5G technologies, both parts of the mobile network. IoT devices can be made with the help of the NB-IoT network. Since the IoT devices are small and economical, security is often dismissed. To avoid a solution when describing this technology, the standardization is carried out by the 5G networks. Devices based on NB-IoT can access LTE security directly since NB-IoT is not based on any defined architecture for security. Applications and resource allocation can lead to many security attacks on NB-IoT devices.
4 Results and discussions
5G’s main significant characteristics serve as an enabler for business. Manufacturing technology’s current direction toward automation and data sharing is the “business” tendency. In addition to automation and control systems, it focuses on IoT, cloud computing, and cognitive computing. Business industries are formed in commercial contexts. The IoT system monitoring dynamic systems generates an intelligent vision of the real environment and decentralized industrial automation decisions are made. Currently, 4G/3G has the following limitations: energy consumption, reliability, latency, and computability. In addition, the 5G process restricts the inaccessible applications. Time-critical and reliable processes can be divided into non-time-critical communication and industrial remote control (remote workers, augmented reality). An economic demonstration system with a mobile device and manufacturing units is described in the article. That 5G can be used in a business setting with various data sources has been demonstrated. In such business applications, 5G communications’ capabilities show real potential as a solution for wired transmission. The research found additional benefits of 5G when searching from a wider perspective of business applications. Several business applications and technological needs for the main capabilities are described in the article, including upgrading facilities, using mobile devices, integrating logistics activity for industrial, developing a modular system contributes, and using connector technology.
Table 1 shows the NSNB-IoT outputs. A communication network design is then presented in the article, which integrates into business and Industrial IoT standard designs to meet the requirements of the identified business applications. Customers, wireless carriers, and businesses everywhere are vulnerable to 5G’s novel application factors. The 2G, 3G, and 4G networks are evident specifically for people. End devices are connected to these networks in significant numbers. There’s a decent possibility that devices can use 5G’s essentially untapped resources. The basic household appliances, cars, and IoT devices are all used for this technology. As a result of 5G, we can monitor development in real time, determining when the technology we acquire can be developed and where it is in the production process. So it helps with the growth of real-time business and improving services where accuracy is very important to the business. As a result, the development of 5G can benefit the entire business. It is important to focus on which business industries are influenced and how much to evaluate the economic implications. Studies on this issue are many and are probably updated and changed annually. Businesses are, without such uncertainty, the most important parties in networked systems. 5G and IoT are anticipated to have a short-term effect. 5G is used in various high-impact areas, mainly in mobile applications.
NSNB-IoT outputs
| Parameters (%) | EHRMS | DBNS | MHEA | IBNSS | NSNB-IoTF |
|---|---|---|---|---|---|
| Accuracy ratio | 45.7 | 66.6 | 75.6 | 87.7 | 92.5 |
| Security ratio | 55.6 | 60.5 | 70.4 | 82.8 | 94.4 |
| Reliability ratios | 52.3 | 68.3 | 72.3 | 84.3 | 93.5 |
| Latency ratio | 53.5 | 63.5 | 71.5 | 85.5 | 91.8 |
| Cost-effective ratio | 82.2 | 71.1 | 58.1 | 44.9 | 20.5 |
| Throughput ratio | 77.8 | 55.12 | 46.1 | 38.7 | 25.4 |
4.1 Accuracy ratio (%)
Mobile phone users can benefit from the more accurate location due to 5G. Ten meters of location accuracy is expected in city settings with acceptable installation density. Based on the line intersection of neighbouring cells, the base station can determine which sector a user is in while using LTE. 5G base station channel estimation technology separates base station broadcasts into several spatial components at a few degrees, resulting in much-improved location accuracy. Wideband transmitters are a two-dimensional array of base station elements, not simply horizontal arrays. We can determine a customer’s vertical position by determining which vertical beam the individual uses.
The accuracy ratio (%) is shown in Figure 6. Higher frequencies can improve wideband resolution. There can be even fewer degrees between 5G mobile network nodes when they expand into millimetre-wave frequencies, allowing them to be more accurate horizontally and vertically. According to the research, sub-meter positioning accuracy can be technically achieved by combining minor cell networks with millimetre-wave movers and transceivers. Practical problems such as node organization, connection, and ultra-dense network operation costs can be solved. When properly implemented, location-based services can enhance accuracy while speeding up the collection and distribution of location data in 5G networks.
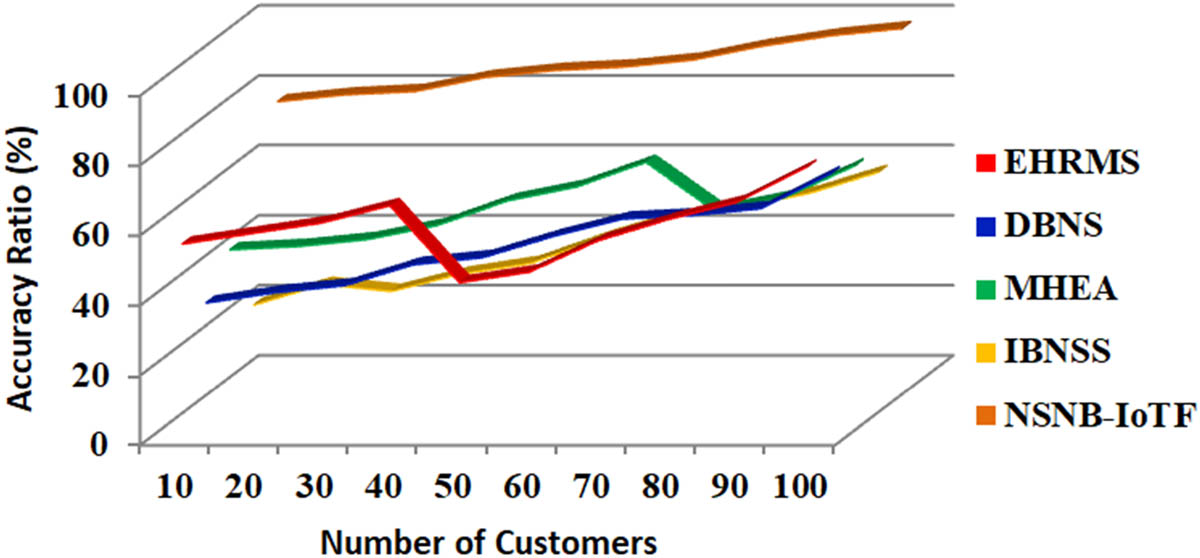
Accuracy ratio (%).
4.2 Security ratio (%)
5G mobile communication networks can build an effective, low-energy service models to develop the effective network structure with local service requirement. The 5G mobile network can provide access to network security. A centralized security management system protects privacy and authentication. These new 5G mobile communication networks can provide a variety of security measures to protect the privacy of various network-connected devices. Wireless access security management can be transferred to the 5G network access network to manage and control the security. Business slices contain a lot of data in the 5G network topology. Various business features need different security management and control methods. During the networking procedure, the access network security has been addressed.
The security ratio (%) is shown in Figure 7. Many 5G core network facilities offer simulated sinking to divide the various important functions, and the virtual core network architecture is semi-open. Network security design has shifted from centralized to distributed due to maximize the open data and number of interactive scenarios. In this research, we can analyse simulated base station attack behaviour and use digital assets to safeguard network customer data to develop a secure 5G network service slice. IoT-based 5G mobile network security technology is being developed, and several problems exist. The usage of 5G in mobile network security decreases throughput and the problems mentioned earlier.
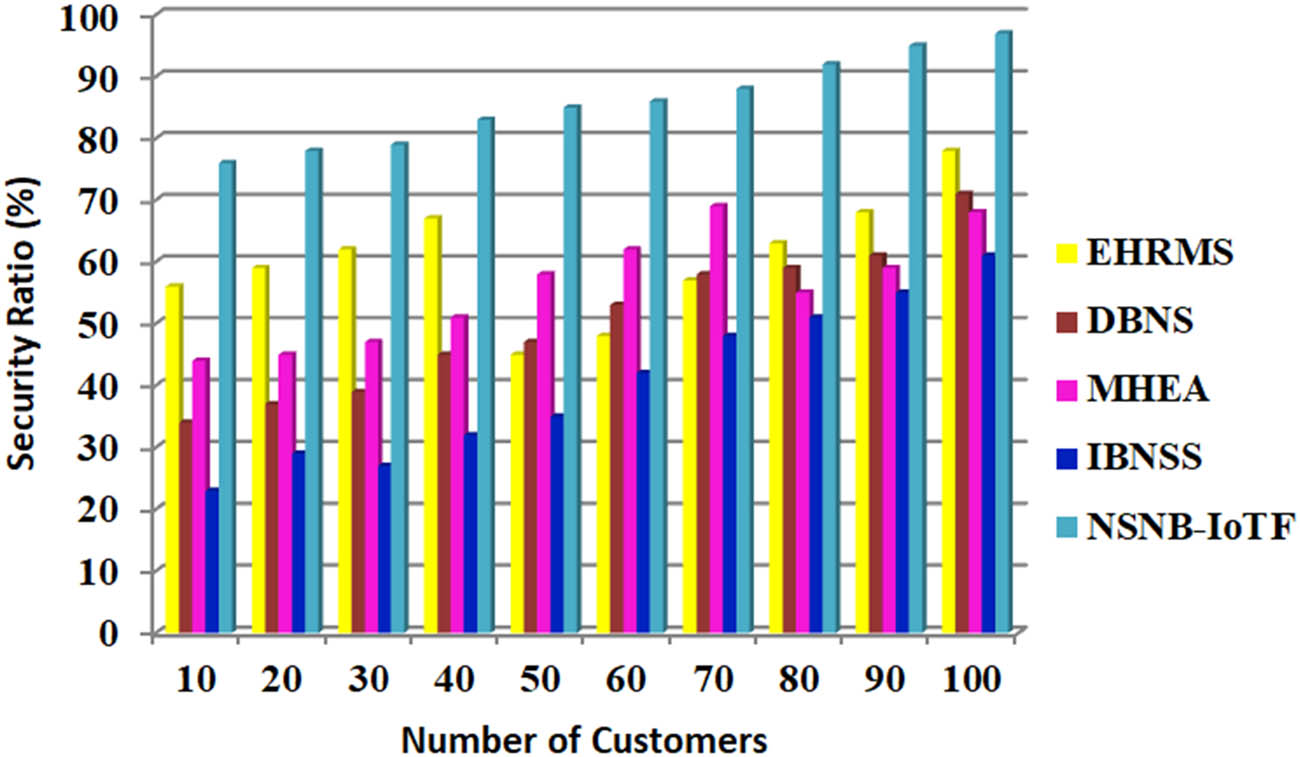
Security ratio (%).
4.3 Latency ratio (%) and reliability ratio (%)
Using 5G technology, a mobile network can send and receive data over short distances, reduce communication latency, and improve throughput. The 5G network has emerged as an effective computing platform for IoT. 3G collaboration enables NB-IoT device connection in low-throughput cellular networks, allowing a wide range of IoT devices to be used together. The NB-IoT network architecture is the same as the 5G, enabling large customer devices without end-to-end latency. This technique claims a greater transmission capacity and ultra-low latency. An important challenge in capability restriction occurs when a high-resource computation application needs to access the mobile cloud computing server remotely. Due to the unstable transmission protocol used by IoT devices, packet loss can occur when the network is unmanaged. The IoT device’s end-to-end delay and processing time need not exceed the communication time for data to be dropped. The proposed program lowers waiting times and latency from end to end, which helps lower errors.
The latency ratio (%) and reliability ratio (%) are shown in Figure 8. Due to its distinction from traditional intelligent heterogeneous networks and unlicensed wireless spectrum, high dependability is essential for 5G. 5G research requires great work on reliability, latency, and bandwidth. A geographically distributed network makes providing high reliability for innovative 5G services easier. Broadband networking and its well-known disadvantages on application performance is the challenge. Current 4G/3G limitations include wireless connection reliability, device energy usage, end-to-end latency, and device concentration. In the previous, 5G is restricted by such limitations. Since user equipment has limited resource capacity, achieving service requirements such as latency and reliability is challenging. The proposed method reduces 5G augmented services’ system failure probability while maintaining reliability and latency. Early adopters of industrial IoT systems have a real-time operation, security, high reliability, and complexity.
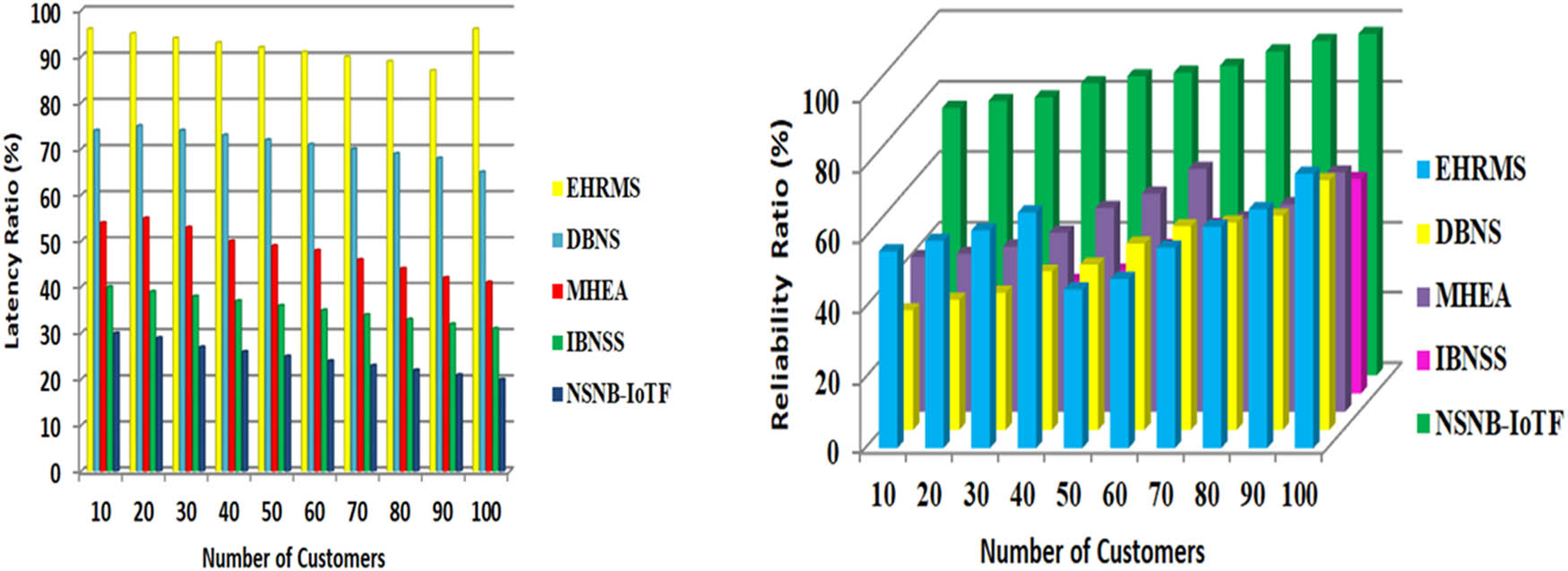
Latency ratio (%) and reliability ratio (%).
Moreover, immutable distributed ledgers acquire IoT data traceability and reliability, allowing for moment data inclusion, change tracking, and data quality control. Digital optimization techniques optimized for 5G connectivity and computation abilities can improve reliability and reduce costs. Industrial IoT connectivity requires high reliability, reduced latency, and security.
4.4 Cost-effective ratio (%)
This new NB-IoT technology has reduced the number of requirements that are not needed for LPWA. This indicates that NB-IoT is well positioned to provide advantages to those other technologies such as 2G, 3G, or LTE that cannot be duplicated without incurring high costs. As an outcome, NB-IoT can have a long battery life, a larger indoor coverage area, and reduced module costs. An 180 kHz low-frequency bandwidth is used by NB-IoT, making it ideal for low-cost devices. An 180 kHz frequency range is used for combined uplink and downlink operation, making it ideal for low-cost devices.
NB-IoT devices are compact and cost-effective. Table 2 shows the cost-effective ratio (%). In locations with weak communications, IoT device has minimum delay and have a high throughput of 164 dB. Regarding data transmission, NB-IoT has both internet protocol (IP) and non-IP methods. A major problem in IoT is security in low-cost, lightweight NB-IoT devices and developing efficient, cost-effective techniques suitable for all types of IoT communication.
Cost-effective ratio (%)
| Number of customers | Cost-effective ratio (%) | ||||
|---|---|---|---|---|---|
| EHRMS | DBNS | MHEA | IBNSS | NSNB-IoTF | |
| 10 | 91.3 | 80.9 | 67.8 | 57.2 | 42.6 |
| 20 | 90.4 | 79.6 | 66.7 | 56.3 | 41.7 |
| 30 | 89.0 | 78.5 | 65.4 | 55.6 | 40.1 |
| 40 | 88.0 | 77.2 | 64.5 | 53.9 | 39.3 |
| 50 | 87.8 | 76.4 | 63.7 | 51.5 | 35.7 |
| 60 | 86.8 | 75.1 | 62.2 | 50.4 | 33.9 |
| 70 | 85.7 | 74.2 | 61.3 | 49.6 | 30.5 |
| 80 | 84.9 | 73.0 | 60.6 | 47.2 | 28.0 |
| 90 | 83.5 | 72.1 | 59.8 | 45.5 | 25.2 |
| 100 | 82.2 | 71.1 | 58.1 | 44.9 | 20.5 |
4.5 Throughput ratio (%)
Device-to-device communication allows for direct mobile phone to mobile phone communication. Direct sharing is important for data transmission. Each innovative installation can have a basic design plan to achieve a competent execution result. Realistic analysis indicates users want to use the downloading mode with branch and bound computation to improve the framework’s throughput and energy level. It is an effort to support 5G. QoS of the boundaries of (limitation, delay, and cost) has been proposed to improve the network cloud management supply system, model.
These include reducing end-to-end latency, increasing communication throughput, decreasing packet loss, and boosting communication dependability. This article offers a generic framework for narrowband IoT data fusion. By providing customizable data fusion services, it can be possible to deal with real-time and historical data generated by heterogeneous IoT devices. We can assess real-time data stream processing forms, such as data throughput, reaction time, and historical data stream replication accuracy. The NB-IoT design supports many low-throughput devices connected to a single location cell. Table 3 shows the throughput ratio (%). NB-IoT is developed to help current LTE and 5G architectures with low complexity and low throughput. The experimental results from NSNB-IoTF demonstrate improvements in parameters such as accuracy ratio, security ratio, reliability ratio, latency ratio, cost-effectiveness ratio, and throughput ratio when compared to EHRMS, DBNS, MHEA, and IBNSS, as proposed.
Throughput ratio (%)
| Number of customers | Throughput ratio (%) | ||||
|---|---|---|---|---|---|
| EHRMS | DBNS | MHEA | IBNSS | NSNB-IoTF | |
| 10 | 87.6 | 65.3 | 57.5 | 45.2 | 37.6 |
| 20 | 86.7 | 64.6 | 54.2 | 44.1 | 36.7 |
| 30 | 85.1 | 63.5 | 53.9 | 43.1 | 35.1 |
| 40 | 84.3 | 62.2 | 52.5 | 42.1 | 34.3 |
| 50 | 83.7 | 61.4 | 51.7 | 41.2 | 33.7 |
| 60 | 82.6 | 59.1 | 50.3 | 40.4 | 32.6 |
| 70 | 81.7 | 58.5 | 49.4 | 40.2 | 31.7 |
| 80 | 79.9 | 57.0 | 48.6 | 39.9 | 29.9 |
| 90 | 78.3 | 56.1 | 47.8 | 38.3 | 26.3 |
| 100 | 77.8 | 55.12 | 46.1 | 38.7 | 25.4 |
Key areas, including accuracy, dependability, throughput, safety, latency, and cost-effectiveness, are where the NSNB-IoTF design excels over existing methods. Implementing narrowband interaction, dynamic data rate control, and decisive edge processing make the framework a robust solution, particularly for scenarios involving several IoT devices, guaranteeing accurate results. By ensuring the integrity and confidentiality of data, NSNB-IoTF’s reputation is strengthened by including security features such as end-to-end encryption, secure key management, and intrusion detection. In contrast to more traditional methods, which could struggle in dynamic network environments, this framework is more reliable because of its adaptability and ability to react in real time. Being close to data sources, edge computing, and low-latency protocols all contribute to NSNB-IoTF’s outstanding latency reduction performance. This system is cost-effective since it optimizes resources, is scalable, and uses bandwidth efficiently. This framework is excellent for many IoT scenarios since these features boost its claimed data processing capacity. Details on the experimental methods, datasets, and specific performance metrics are included in the article. Nonetheless, the potential benefits of NSNB-IoTF over existing approaches are brought to light by this comprehensive comparative research.
5 Conclusion
The 5G mobile communication services framework aims to be a novel circumstance of digital distribution, coordination, and lowering. 5G wireless communication network activities have various and unique characteristics. These architectural modifications have presented many novel secure management and control methods for 5G communication networks. An analysis of base station attacks and the protection of IoT network customers’ data is presented in this study, which focuses on 5G wireless transmission network security technology research. Wireless 5G network security using IoT is developing, and various issues can be solved. Wireless communication network security systems’ transmission bandwidth is reduced by IoT computations such as encryption, decryption, and authentication. Based on their market position, this study employs the innovative secured narrowband IoT framework (NSNB-IoTF) for 5G communication and operational goals. To govern data transmission, the 5G network employs corporate connection and access information. During this process, the network takes advantage of cellular bandwidth and IoT devices to connect new devices. The information is transferred with the least amount of delay possible based on the connection. In comparison to other approaches, experimental findings suggested the following parameters: an accuracy ratio of 92.5%, a security ratio of 94.4%, a reliability ratio of 93.5%, a latency ratio of 91.8%, a cost-effective ratio of 20.5%, and a throughput ratio of 25.4%. This study analyses the need for a novel digital network, considering all types of business, from the basic to the complicated. Transmission business network communications can be quicker, secure, and smarter due to 5G communication network slicing.
-
Funding information: The author received no specific funding for this study.
-
Author contributions: Hiba A.Tarish: Conceptualization, Methodology, Formal analysis, Investigation, Writing – review & editing, and Funding acquisition.
-
Conflict of interest: The author declares no conflict of interest.
-
Data availability statement: The dataset used in this study is available upon request from the corresponding author.
References
[1] Sutrala AK, Obaidat MS, Saha S, Das AK, Alazab M, Park Y. Authenticated key agreement scheme with user anonymity and untraceability for 5G-enabled softwarized industrial cyber-physical systems. IEEE Trans Intell Transp Sys. 2021;23:2316–30.10.1109/TITS.2021.3056704Search in Google Scholar
[2] Seyhan K, Nguyen TN, Akleylek S, Cengiz K, Islam SH. Bi-GISIS KE: Modified key exchange protocol with reusable keys for IoT security. J Inf Secur Appl. 2021;58:102788.10.1016/j.jisa.2021.102788Search in Google Scholar
[3] Althobaiti OS, Dohler M. Narrowband-internet of things device-to-device simulation: an open-sourced framework. Sensors. 2021;21(5):1824.10.3390/s21051824Search in Google Scholar PubMed PubMed Central
[4] Gao J, Wang H, Shen H. Task failure prediction in cloud data centers using deep learning. IEEE Trans Serv Comput. 2020;15:1411–22.10.1109/TSC.2020.2993728Search in Google Scholar
[5] Li J, Lei G, Manogaran G, Mastorakis G, Mavromoustakis CX. D2D communication mode selection and resource optimization algorithm with optimal throughput in 5G network. IEEE Access. 2019;7:25263–73.10.1109/ACCESS.2019.2900422Search in Google Scholar
[6] Rastogi E, Saxena N, Roy A, Shin DR. Narrowband internet of things: A comprehensive study. Comput Networks. 2020;173:107209.10.1016/j.comnet.2020.107209Search in Google Scholar
[7] Gao J, Wang H, Shen H. Machine learning based workload prediction in cloud computing. In 2020 29th International Conference on Computer Communications and Networks (ICCCN). IEEE; 2020. p. 1–9.10.1109/ICCCN49398.2020.9209730Search in Google Scholar
[8] Le Nguyen B, Lydia EL, Elhoseny M, Pustokhina I, Pustokhin DA, Selim MM, et al. Privacy-preserving blockchain technique to achieve secure and reliable sharing of IoT data. Comput Mater Continua. 2020;65(1):87–107.10.32604/cmc.2020.011599Search in Google Scholar
[9] Beshley M, Kryvinska N, Seliuchenko M, Beshley H, Shakshuki EM, Yasar AUH. End-to-End QoS “smart queue” management algorithms and traffic prioritization mechanisms for narrowband internet of things services in 4G/5G networks. Sensors. 2020;20(8):2324.10.3390/s20082324Search in Google Scholar PubMed PubMed Central
[10] Amudha G. Dilated transaction access and retrieval: improving the information retrieval of blockchain-assimilated Internet of Things Transactions. Wireless Pers Commun. 2021;127:1–21.10.1007/s11277-021-08094-ySearch in Google Scholar
[11] Naeem MA, Nguyen TN, Ali R, Cengiz K, Meng Y, Khurshaid T. Hybrid cache management in IoT-based named data networking. IEEE IOT J. 2021;9:7140–50.10.1109/JIOT.2021.3075317Search in Google Scholar
[12] Kakarash ZA, Mardukhi F. A review of properties and functions of narrow band Internet of Things and its security requirements. UHD J Sci Technol. 2020;4(1):71–80.10.21928/uhdjst.v4n1y2020.pp71-80Search in Google Scholar
[13] Abidi MH, Alkhalefah H, Moiduddin K, Alazab M, Mohammed MK, Ameen W, et al. Optimal 5G network slicing using machine learning and deep learning concepts. Comput Stand Interfaces. 2021;76:103518.10.1016/j.csi.2021.103518Search in Google Scholar
[14] Selvaraj R, Kuthadi VM, Baskar S, Shakeel PM, Ranjan A. Creating security modelling framework analysing in the Internet of Things using EC-GSM-IoT. Arabian J Sci Eng. 2021;48:1–13.10.1007/s13369-021-05887-ySearch in Google Scholar
[15] Xu X, Li D, Sun M, Yang S, Yu S, Manogaran G, et al. Research on key technologies of smart campus teaching platform based on 5G network. IEEE Access. 2019;7:20664–75.10.1109/ACCESS.2019.2894129Search in Google Scholar
[16] Elhoseny M, Hassan MK, Pejic-Bach M. Special issue on “Cognitive big data analytics for intelligent information systems”. Inf Syst E-Bus Manage. 2020;18:485–6.10.1007/s10257-020-00483-3Search in Google Scholar
[17] Liu Y, Yang X, Wen W, Xia M. Smarter grid in the 5G era: integrating power Internet of Things with cyber physical system. Front Commun Networks. 2021;2:23.10.3389/frcmn.2021.689590Search in Google Scholar
[18] Amudha G, Narayanasamy P. Distributed location and trust based replica detection in wireless sensor networks. Wireless Pers Commun. 2018;102(4):3303–21.10.1007/s11277-018-5369-2Search in Google Scholar
[19] Sanchez-Gomez J, Garcia-Carrillo D, Marin-Perez R, Skarmeta AF. Secure authentication and credential establishment in narrowband IoT and 5G. Sensors. 2020;20(3):882.10.3390/s20030882Search in Google Scholar PubMed PubMed Central
[20] Ding F, Zhu G, Alazab M, Li X, Yu K. Deep-learning-empowered digital forensics for edge consumer electronics in 5G HetNets. IEEE Consum Electron Mag. 2020;11:42–50.10.1109/MCE.2020.3047606Search in Google Scholar
[21] Shakeel PM, Baskar S, Fouad H, Manogaran G, Saravanan V, Xin Q. Creating collision-free communication in IoT with 6G using multiple machine access learning collision avoidance protocol. Mobile Networks Appl. 2021;26(3):969–80.10.1007/s11036-020-01670-9Search in Google Scholar
[22] Al-Turjman F, Lemayian JP. Intelligence, security, and vehicular sensor networks in internet of things (IoT)-enabled smart-cities: an overview. Comput Electr Eng. 2020;87:106776.10.1016/j.compeleceng.2020.106776Search in Google Scholar
[23] Zhao Y, Yu Y, Shakeel PM, Montenegro-Marin CE. Research on operational research-based financial model based on e-commerce platform. Inf Syst e-Bus Manag. 2021;21:1–17.10.1007/s10257-021-00509-4Search in Google Scholar
[24] Fang X, Feng W, Wei T, Chen Y, Ge N, Wang CX. 5G embraces satellites for 6G ubiquitous IoT: Basic models for integrated satellite terrestrial networks. IEEE IOT J. 2021;8(18):14399–417.10.1109/JIOT.2021.3068596Search in Google Scholar
[25] Varga P, Peto J, Franko A, Balla D, Haja D, Janky F, et al. 5G support for industrial IoT applications – challenges, solutions, and research gaps. Sensors. 2020;20(3):828.10.3390/s20030828Search in Google Scholar PubMed PubMed Central
[26] Vuojala H, Mustonen M, Chen X, Kujanpää K, Ruuska P, Höyhtyä M, et al. Spectrum access options for vertical network service providers in 5G. Telecommun Policy. 2020;44(4):101903.10.1016/j.telpol.2019.101903Search in Google Scholar
[27] Wang Y. Enterprise human resource management system based on 5G network and internet of things system. Microprocessors Microsyst. 2020;7:103427.10.1016/j.micpro.2020.103427Search in Google Scholar
[28] Togou MA, Bi T, Dev K, McDonnell K, Milenovic A, Tewari H, et al. DBNS: A distributed blockchain-enabled network slicing framework for 5G networks. IEEE Commun Mag. 2020;58(11):90–6.10.1109/MCOM.001.2000112Search in Google Scholar
[29] Shuvo MSA, Munna MAR, Sarker S, Adhikary T, Razzaque MA, Hassan MM, et al. Energy-efficient scheduling of small cells in 5G: A meta-heuristic approach. J Network Comput Appl. 2021;178:102986.10.1016/j.jnca.2021.102986Search in Google Scholar
[30] Abbas K, Afaq M, Ahmed Khan T, Rafiq A, Song WC. Slicing the core network and radio access network domains through intent-based networking for 5g networks. Electronics. 2020;9(10):1710.10.3390/electronics9101710Search in Google Scholar
[31] Yassine S, Stanulov A. A comparative analysis of machine learning algorithms for the purpose of predicting norwegian air passenger traffic. Int J Math Stat Comput Sci. 2024;2:28–43. 10.59543/ijmscs.v2i.7851.Search in Google Scholar
[32] Manthiramoorthy C, Khan KMS. Comparing several encrypted cloud storage platforms. Int J Math Stat Comput Sci. 2023;2:44–62. 10.59543/ijmscs.v2i.7971.Search in Google Scholar
© 2024 the author(s), published by De Gruyter
This work is licensed under the Creative Commons Attribution 4.0 International License.
Articles in the same Issue
- Research Articles
- A study on intelligent translation of English sentences by a semantic feature extractor
- Detecting surface defects of heritage buildings based on deep learning
- Combining bag of visual words-based features with CNN in image classification
- Online addiction analysis and identification of students by applying gd-LSTM algorithm to educational behaviour data
- Improving multilayer perceptron neural network using two enhanced moth-flame optimizers to forecast iron ore prices
- Sentiment analysis model for cryptocurrency tweets using different deep learning techniques
- Periodic analysis of scenic spot passenger flow based on combination neural network prediction model
- Analysis of short-term wind speed variation, trends and prediction: A case study of Tamil Nadu, India
- Cloud computing-based framework for heart disease classification using quantum machine learning approach
- Research on teaching quality evaluation of higher vocational architecture majors based on enterprise platform with spherical fuzzy MAGDM
- Detection of sickle cell disease using deep neural networks and explainable artificial intelligence
- Interval-valued T-spherical fuzzy extended power aggregation operators and their application in multi-criteria decision-making
- Characterization of neighborhood operators based on neighborhood relationships
- Real-time pose estimation and motion tracking for motion performance using deep learning models
- QoS prediction using EMD-BiLSTM for II-IoT-secure communication systems
- A novel framework for single-valued neutrosophic MADM and applications to English-blended teaching quality evaluation
- An intelligent error correction model for English grammar with hybrid attention mechanism and RNN algorithm
- Prediction mechanism of depression tendency among college students under computer intelligent systems
- Research on grammatical error correction algorithm in English translation via deep learning
- Microblog sentiment analysis method using BTCBMA model in Spark big data environment
- Application and research of English composition tangent model based on unsupervised semantic space
- 1D-CNN: Classification of normal delivery and cesarean section types using cardiotocography time-series signals
- Real-time segmentation of short videos under VR technology in dynamic scenes
- Application of emotion recognition technology in psychological counseling for college students
- Classical music recommendation algorithm on art market audience expansion under deep learning
- A robust segmentation method combined with classification algorithms for field-based diagnosis of maize plant phytosanitary state
- Integration effect of artificial intelligence and traditional animation creation technology
- Artificial intelligence-driven education evaluation and scoring: Comparative exploration of machine learning algorithms
- Intelligent multiple-attributes decision support for classroom teaching quality evaluation in dance aesthetic education based on the GRA and information entropy
- A study on the application of multidimensional feature fusion attention mechanism based on sight detection and emotion recognition in online teaching
- Blockchain-enabled intelligent toll management system
- A multi-weapon detection using ensembled learning
- Deep and hand-crafted features based on Weierstrass elliptic function for MRI brain tumor classification
- Design of geometric flower pattern for clothing based on deep learning and interactive genetic algorithm
- Mathematical media art protection and paper-cut animation design under blockchain technology
- Deep reinforcement learning enhances artistic creativity: The case study of program art students integrating computer deep learning
- Transition from machine intelligence to knowledge intelligence: A multi-agent simulation approach to technology transfer
- Research on the TF–IDF algorithm combined with semantics for automatic extraction of keywords from network news texts
- Enhanced Jaya optimization for improving multilayer perceptron neural network in urban air quality prediction
- Design of visual symbol-aided system based on wireless network sensor and embedded system
- Construction of a mental health risk model for college students with long and short-term memory networks and early warning indicators
- Personalized resource recommendation method of student online learning platform based on LSTM and collaborative filtering
- Employment management system for universities based on improved decision tree
- English grammar intelligent error correction technology based on the n-gram language model
- Speech recognition and intelligent translation under multimodal human–computer interaction system
- Enhancing data security using Laplacian of Gaussian and Chacha20 encryption algorithm
- Construction of GCNN-based intelligent recommendation model for answering teachers in online learning system
- Neural network big data fusion in remote sensing image processing technology
- Research on the construction and reform path of online and offline mixed English teaching model in the internet era
- Real-time semantic segmentation based on BiSeNetV2 for wild road
- Online English writing teaching method that enhances teacher–student interaction
- Construction of a painting image classification model based on AI stroke feature extraction
- Big data analysis technology in regional economic market planning and enterprise market value prediction
- Location strategy for logistics distribution centers utilizing improved whale optimization algorithm
- Research on agricultural environmental monitoring Internet of Things based on edge computing and deep learning
- The application of curriculum recommendation algorithm in the driving mechanism of industry–teaching integration in colleges and universities under the background of education reform
- Application of online teaching-based classroom behavior capture and analysis system in student management
- Evaluation of online teaching quality in colleges and universities based on digital monitoring technology
- Face detection method based on improved YOLO-v4 network and attention mechanism
- Study on the current situation and influencing factors of corn import trade in China – based on the trade gravity model
- Research on business English grammar detection system based on LSTM model
- Multi-source auxiliary information tourist attraction and route recommendation algorithm based on graph attention network
- Multi-attribute perceptual fuzzy information decision-making technology in investment risk assessment of green finance Projects
- Research on image compression technology based on improved SPIHT compression algorithm for power grid data
- Optimal design of linear and nonlinear PID controllers for speed control of an electric vehicle
- Traditional landscape painting and art image restoration methods based on structural information guidance
- Traceability and analysis method for measurement laboratory testing data based on intelligent Internet of Things and deep belief network
- A speech-based convolutional neural network for human body posture classification
- The role of the O2O blended teaching model in improving the teaching effectiveness of physical education classes
- Genetic algorithm-assisted fuzzy clustering framework to solve resource-constrained project problems
- Behavior recognition algorithm based on a dual-stream residual convolutional neural network
- Ensemble learning and deep learning-based defect detection in power generation plants
- Optimal design of neural network-based fuzzy predictive control model for recommending educational resources in the context of information technology
- An artificial intelligence-enabled consumables tracking system for medical laboratories
- Utilization of deep learning in ideological and political education
- Detection of abnormal tourist behavior in scenic spots based on optimized Gaussian model for background modeling
- RGB-to-hyperspectral conversion for accessible melanoma detection: A CNN-based approach
- Optimization of the road bump and pothole detection technology using convolutional neural network
- Comparative analysis of impact of classification algorithms on security and performance bug reports
- Cross-dataset micro-expression identification based on facial ROIs contribution quantification
- Demystifying multiple sclerosis diagnosis using interpretable and understandable artificial intelligence
- Unifying optimization forces: Harnessing the fine-structure constant in an electromagnetic-gravity optimization framework
- E-commerce big data processing based on an improved RBF model
- Analysis of youth sports physical health data based on cloud computing and gait awareness
- CCLCap-AE-AVSS: Cycle consistency loss based capsule autoencoders for audio–visual speech synthesis
- An efficient node selection algorithm in the context of IoT-based vehicular ad hoc network for emergency service
- Computer aided diagnoses for detecting the severity of Keratoconus
- Improved rapidly exploring random tree using salp swarm algorithm
- Network security framework for Internet of medical things applications: A survey
- Predicting DoS and DDoS attacks in network security scenarios using a hybrid deep learning model
- Enhancing 5G communication in business networks with an innovative secured narrowband IoT framework
- Quokka swarm optimization: A new nature-inspired metaheuristic optimization algorithm
- Digital forensics architecture for real-time automated evidence collection and centralization: Leveraging security lake and modern data architecture
- Image modeling algorithm for environment design based on augmented and virtual reality technologies
- Enhancing IoT device security: CNN-SVM hybrid approach for real-time detection of DoS and DDoS attacks
- High-resolution image processing and entity recognition algorithm based on artificial intelligence
- Review Articles
- Transformative insights: Image-based breast cancer detection and severity assessment through advanced AI techniques
- Network and cybersecurity applications of defense in adversarial attacks: A state-of-the-art using machine learning and deep learning methods
- Applications of integrating artificial intelligence and big data: A comprehensive analysis
- A systematic review of symbiotic organisms search algorithm for data clustering and predictive analysis
- Modelling Bitcoin networks in terms of anonymity and privacy in the metaverse application within Industry 5.0: Comprehensive taxonomy, unsolved issues and suggested solution
- Systematic literature review on intrusion detection systems: Research trends, algorithms, methods, datasets, and limitations
Articles in the same Issue
- Research Articles
- A study on intelligent translation of English sentences by a semantic feature extractor
- Detecting surface defects of heritage buildings based on deep learning
- Combining bag of visual words-based features with CNN in image classification
- Online addiction analysis and identification of students by applying gd-LSTM algorithm to educational behaviour data
- Improving multilayer perceptron neural network using two enhanced moth-flame optimizers to forecast iron ore prices
- Sentiment analysis model for cryptocurrency tweets using different deep learning techniques
- Periodic analysis of scenic spot passenger flow based on combination neural network prediction model
- Analysis of short-term wind speed variation, trends and prediction: A case study of Tamil Nadu, India
- Cloud computing-based framework for heart disease classification using quantum machine learning approach
- Research on teaching quality evaluation of higher vocational architecture majors based on enterprise platform with spherical fuzzy MAGDM
- Detection of sickle cell disease using deep neural networks and explainable artificial intelligence
- Interval-valued T-spherical fuzzy extended power aggregation operators and their application in multi-criteria decision-making
- Characterization of neighborhood operators based on neighborhood relationships
- Real-time pose estimation and motion tracking for motion performance using deep learning models
- QoS prediction using EMD-BiLSTM for II-IoT-secure communication systems
- A novel framework for single-valued neutrosophic MADM and applications to English-blended teaching quality evaluation
- An intelligent error correction model for English grammar with hybrid attention mechanism and RNN algorithm
- Prediction mechanism of depression tendency among college students under computer intelligent systems
- Research on grammatical error correction algorithm in English translation via deep learning
- Microblog sentiment analysis method using BTCBMA model in Spark big data environment
- Application and research of English composition tangent model based on unsupervised semantic space
- 1D-CNN: Classification of normal delivery and cesarean section types using cardiotocography time-series signals
- Real-time segmentation of short videos under VR technology in dynamic scenes
- Application of emotion recognition technology in psychological counseling for college students
- Classical music recommendation algorithm on art market audience expansion under deep learning
- A robust segmentation method combined with classification algorithms for field-based diagnosis of maize plant phytosanitary state
- Integration effect of artificial intelligence and traditional animation creation technology
- Artificial intelligence-driven education evaluation and scoring: Comparative exploration of machine learning algorithms
- Intelligent multiple-attributes decision support for classroom teaching quality evaluation in dance aesthetic education based on the GRA and information entropy
- A study on the application of multidimensional feature fusion attention mechanism based on sight detection and emotion recognition in online teaching
- Blockchain-enabled intelligent toll management system
- A multi-weapon detection using ensembled learning
- Deep and hand-crafted features based on Weierstrass elliptic function for MRI brain tumor classification
- Design of geometric flower pattern for clothing based on deep learning and interactive genetic algorithm
- Mathematical media art protection and paper-cut animation design under blockchain technology
- Deep reinforcement learning enhances artistic creativity: The case study of program art students integrating computer deep learning
- Transition from machine intelligence to knowledge intelligence: A multi-agent simulation approach to technology transfer
- Research on the TF–IDF algorithm combined with semantics for automatic extraction of keywords from network news texts
- Enhanced Jaya optimization for improving multilayer perceptron neural network in urban air quality prediction
- Design of visual symbol-aided system based on wireless network sensor and embedded system
- Construction of a mental health risk model for college students with long and short-term memory networks and early warning indicators
- Personalized resource recommendation method of student online learning platform based on LSTM and collaborative filtering
- Employment management system for universities based on improved decision tree
- English grammar intelligent error correction technology based on the n-gram language model
- Speech recognition and intelligent translation under multimodal human–computer interaction system
- Enhancing data security using Laplacian of Gaussian and Chacha20 encryption algorithm
- Construction of GCNN-based intelligent recommendation model for answering teachers in online learning system
- Neural network big data fusion in remote sensing image processing technology
- Research on the construction and reform path of online and offline mixed English teaching model in the internet era
- Real-time semantic segmentation based on BiSeNetV2 for wild road
- Online English writing teaching method that enhances teacher–student interaction
- Construction of a painting image classification model based on AI stroke feature extraction
- Big data analysis technology in regional economic market planning and enterprise market value prediction
- Location strategy for logistics distribution centers utilizing improved whale optimization algorithm
- Research on agricultural environmental monitoring Internet of Things based on edge computing and deep learning
- The application of curriculum recommendation algorithm in the driving mechanism of industry–teaching integration in colleges and universities under the background of education reform
- Application of online teaching-based classroom behavior capture and analysis system in student management
- Evaluation of online teaching quality in colleges and universities based on digital monitoring technology
- Face detection method based on improved YOLO-v4 network and attention mechanism
- Study on the current situation and influencing factors of corn import trade in China – based on the trade gravity model
- Research on business English grammar detection system based on LSTM model
- Multi-source auxiliary information tourist attraction and route recommendation algorithm based on graph attention network
- Multi-attribute perceptual fuzzy information decision-making technology in investment risk assessment of green finance Projects
- Research on image compression technology based on improved SPIHT compression algorithm for power grid data
- Optimal design of linear and nonlinear PID controllers for speed control of an electric vehicle
- Traditional landscape painting and art image restoration methods based on structural information guidance
- Traceability and analysis method for measurement laboratory testing data based on intelligent Internet of Things and deep belief network
- A speech-based convolutional neural network for human body posture classification
- The role of the O2O blended teaching model in improving the teaching effectiveness of physical education classes
- Genetic algorithm-assisted fuzzy clustering framework to solve resource-constrained project problems
- Behavior recognition algorithm based on a dual-stream residual convolutional neural network
- Ensemble learning and deep learning-based defect detection in power generation plants
- Optimal design of neural network-based fuzzy predictive control model for recommending educational resources in the context of information technology
- An artificial intelligence-enabled consumables tracking system for medical laboratories
- Utilization of deep learning in ideological and political education
- Detection of abnormal tourist behavior in scenic spots based on optimized Gaussian model for background modeling
- RGB-to-hyperspectral conversion for accessible melanoma detection: A CNN-based approach
- Optimization of the road bump and pothole detection technology using convolutional neural network
- Comparative analysis of impact of classification algorithms on security and performance bug reports
- Cross-dataset micro-expression identification based on facial ROIs contribution quantification
- Demystifying multiple sclerosis diagnosis using interpretable and understandable artificial intelligence
- Unifying optimization forces: Harnessing the fine-structure constant in an electromagnetic-gravity optimization framework
- E-commerce big data processing based on an improved RBF model
- Analysis of youth sports physical health data based on cloud computing and gait awareness
- CCLCap-AE-AVSS: Cycle consistency loss based capsule autoencoders for audio–visual speech synthesis
- An efficient node selection algorithm in the context of IoT-based vehicular ad hoc network for emergency service
- Computer aided diagnoses for detecting the severity of Keratoconus
- Improved rapidly exploring random tree using salp swarm algorithm
- Network security framework for Internet of medical things applications: A survey
- Predicting DoS and DDoS attacks in network security scenarios using a hybrid deep learning model
- Enhancing 5G communication in business networks with an innovative secured narrowband IoT framework
- Quokka swarm optimization: A new nature-inspired metaheuristic optimization algorithm
- Digital forensics architecture for real-time automated evidence collection and centralization: Leveraging security lake and modern data architecture
- Image modeling algorithm for environment design based on augmented and virtual reality technologies
- Enhancing IoT device security: CNN-SVM hybrid approach for real-time detection of DoS and DDoS attacks
- High-resolution image processing and entity recognition algorithm based on artificial intelligence
- Review Articles
- Transformative insights: Image-based breast cancer detection and severity assessment through advanced AI techniques
- Network and cybersecurity applications of defense in adversarial attacks: A state-of-the-art using machine learning and deep learning methods
- Applications of integrating artificial intelligence and big data: A comprehensive analysis
- A systematic review of symbiotic organisms search algorithm for data clustering and predictive analysis
- Modelling Bitcoin networks in terms of anonymity and privacy in the metaverse application within Industry 5.0: Comprehensive taxonomy, unsolved issues and suggested solution
- Systematic literature review on intrusion detection systems: Research trends, algorithms, methods, datasets, and limitations

