Abstract
The metaverse, a virtual multiuser environment, has garnered global attention for its potential to offer deeply immersive and participatory experiences. As this technology matures, it is evolving in tandem with emerging innovations such as Web 3.0, Blockchain, nonfungible tokens, and cryptocurrencies like Bitcoin, which play pivotal roles in the metaverse economy. Robust Bitcoin networks must be modelled for the metaverse environment in Industry 5.0 platforms to ensure the metaverse’s sustained growth and relevance. Industry 5.0 is poised to experience significant economic expansion, driven in large part by the transformative influence of metaverse technology. Researchers have actively explored diverse strategies and approaches to address the unique challenges and opportunities presented by current Bitcoin networks, highlighting the limitless potential for enhancing anonymity and privacy while navigating this exciting digital frontier. By addressing the diverse anonymity and privacy evaluation attributes, the lack of clarity regarding the prioritisation of these attributes and the variability in data, this modelling approach can be categorised as a form of multiple attribute decision-making (MADM). This review seeks to achieve three main objectives: firstly, to identify research gaps, obstacles, and problems within scholarly literature, which is crucial for assessing and modelling Bitcoin networks to succour the metaverse environment of Industry 5.0; secondly, to pinpoint theoretical gaps, proposed solutions, and benchmarking of Bitcoin networks; and thirdly, to offer an overview of the existing validation and evaluation methods employed in the literature. This review introduced a unique taxonomy by intersecting “Bitcoin networks based on blockchain aspects” with “anonymity and privacy development attributes aspect.” It emphasised the study’s significance and innovation. The results illustrate that employing MADM techniques is highly suitable for modelling Bitcoin networks to support the metaverse within the context of Industry 5.0. This thorough review is an invaluable resource for academics and decision-makers, offering perspectives regarding the improvements, applications, and potential directions for evaluating Bitcoin networks to bolster the metaverse environment of Industry 5.0.
1 Introduction
Industry 5.0, considered the upcoming stage in the industrial revolution, seeks to combine the inventiveness of human skills with efficient, clever, and accurate machinery to produce manufacturing solutions that beat Industry 4.0 with regard to resource effectiveness and user demand. Life quality, inclusiveness, and sustainability are three characteristics that are receiving much attention [1]. In terms of security, Industry 5.0 can greatly profit from the technology of blockchain. Centralising control over various heterogeneously linked devices is a significant problem in Industry 5.0 [2]. By fostering universal trust, blockchain technology makes creating independent, decentralised administration systems, and instructional websites possible [3,4]. Blockchain technology’s immutable ledger enables the keeping of records and safe peer-to-peer communication. An immutable ledger promotes operational responsibility and openness for important events within Industry 5.0 technologies [5]. Future Industry 5.0 apps can use smart contracts to provide security through automated service-oriented activities and authentication. Furthermore, blockchain techniques can improve data and transaction security [6,7]. Blockchain facilitates easier data gathering and receipt [8]. With the facilitation of agreements between several parties, blockchain technology and smart contracts may help in automating the contractual procedure. Therefore, protection from harmful attacks is necessary for procedural data, which may jeopardise the security and privacy of critical information [9]. Furthermore, communication nodes must keep client information for specialised demands. Employing fair information practices and client conventions for handling privacy issues and obtaining users’ permission to access the data is essential [10]. When heterogeneous and decentralised networks cooperate, reliability during data interchange and management are essential for Industry 5.0. A potential answer is the construction of open ledgers using blockchain, which simplifies tracking and managing data related to industrial activities. A digital data record known as blockchain continuously compiles data in chronological order. A hash is associated with the hash of a block before it is associated with a blockchain block header. Data added to the chain cannot be modified. Anytime a transaction within a block is changed, the block’s hash changes [11,12]. Introducing Industry 5.0-related technological developments will lead to new economic growth [4]. Metaverse is one of the technologies from Industry 5.0. Technology based on the metaverse is anticipated to be fully autonomous by 2050 [13]. The term “metaverse” refers to a constantly expanding multiuser experience that blends elements of the real world and digitally created information [14]. Despite the fact that augmented reality (AR) and virtual reality (VR) are two of the essential components of the metaverse, AR and VR are becoming increasingly widespread in a variety of industries [15] because they are successful at giving users a full 3D virtual world. The metaverse thus combines the ideas of blockchain and social networking with AR and VR to create a multi-dimensional virtual world to increase user involvement that resembles the real world. It combines numerous elements, such as AR, VR, real-time video, and interactive interfaces for users. Utilising this multi-dimensional online space for experimentation and creation by businesses may be beneficial. Businesses can use the metaverse to evaluate their services and goods and get immediate, precise feedback. As a result, several implications of the metaverse will be advantageous to business. Institutions are beginning to evaluate the possibilities of the metaverse and its potential use in their current business strategy [16]. Given the seamless transition between real and virtual experiences and interactions, future metaverse users will have a range of alternatives to choose from, many of which may be beyond their current knowledge [17,18]. The metaverse provides several challenges in terms of security. These difficulties stem from the novelty, intricacy, and multisensory nature of the metaverse, which could have more detrimental consequences on individuals and those who are the targets of security abuses. Crypto-assets, like cryptocurrencies (e.g. Bitcoin) and nonfungible tokens (NFTs), are basic components of the economy of the metaverse. NFTs reflect the ownership of digital in-game objects, virtual avatars, residential buildings, and extra assets while enabling their identification and authentication. Cryptocurrencies in the metaverse fulfil the same objective as money in the current economy [16]. The decentralised cryptocurrency called Bitcoin was presented in 2008 by its maker, Satoshi Nakamoto, and went live in 2009 [19]. All transactions on the Bitcoin network are kept on the blockchain [20]. The blockchain stores information about every transaction, containing the addresses that belong to the person who sent it and the person receiving it, and the amount sent and the period of completion [21]. Bitcoin is recognised as the most significant cryptocurrency because of its decentralised structure and miners’ validation of transactions that pass across the network [22]. The most alluring aspect of Bitcoin is that no personal information about users may be disclosed, enabling financial transactions to be carried out pseudoanonymously. The keys used in Bitcoin exchanges allow users to generate infinite encrypted Bitcoin addresses [23]. In conclusion, the relationship between Bitcoin networks, Industry 5.0, and their relevance to metaverse applications is multifaceted and dynamic, poised to shape the future of digital interactions and economies. Bitcoin networks, built on blockchain technology, serve as a foundational element of Industry 5.0 by offering secure, transparent, and decentralised transaction platforms that streamline supply chains, reduce costs, and enable human-machine collaboration. Moreover, as the metaverse emerges as a transformative digital realm, Bitcoin networks play a pivotal role in facilitating seamless financial transactions, managing digital assets, and upholding user privacy within these virtual environments. Bitcoin’s universal acceptance as a digital currency, coupled with its finite supply and privacy features, positions it as an ideal medium of exchange within the metaverse. Furthermore, Bitcoin’s support for smart contracts augments the efficiency and trustworthiness of metaverse applications, enhancing the overall user experience. As Industry 5.0 and the metaverse continue to converge and evolve, Bitcoin networks act as a bridge between the physical and digital worlds, providing the necessary infrastructure for secure, efficient, and interconnected digital interactions. Their relevance in these contexts underscores their potential to shape the future of industries, commerce, and digital experiences in a manner that aligns with the ever-expanding boundaries of technology and human imagination. Anonymity and privacy in Bitcoin networks have been considered as highlighting features given that numerous researchers have demonstrated that Bitcoin networks for supporting metaverse environment in Industry 5.0 offer intriguing new possibilities for future research. The number of researchers interested in studying the Bitcoin network is growing quickly. These researchers are concentrating on various issues, such as the security of the Bitcoin network, enhancements to user protection services, network data analysis, transaction transmission protocols and insights into the Bitcoin network’s economics, and on-going studies into the blockchain’s structure. However, these phases examine some of the effects of anonymity and privacy to provide the best service for exchanging Bitcoin transactions utilising various methods. More investigation is required for evaluation and benchmarking of the Bitcoin network that developers can use. As a result, during this procedure, three key questions are raised. Firstly, what are the research gaps, obstacles, and problems in published research around evaluating and benchmarking the Bitcoin network? Secondly, what is the theory gap and the suggested solutions for the evaluation and benchmarking of the Bitcoin network? Thirdly, what are the present procedures for validating and evaluating Bitcoin networks applied to the suggested solution in literature?
This review aims to aid the understanding of Bitcoin networks and address the adverse consequences of de-anonymisation efforts. Furthermore, it provides an accurate examination of the Bitcoin network, potentially enhancing the metaverse environment for Industry 5.0, thus laying the groundwork for greater digital autonomy in the coming years. Consequently, this review may be of significance to stakeholders, alongside diverse economic and institutional participants. Accordingly, the major contributions are as follows:
To establish a cogent taxonomy by combining the pertinent studies and demonstrate the Bitcoin network in anonymity and privacy properties along with its development attributes;
To analyse and debate the aspects of anonymity and privacy development attributes and the aspect of Bitcoin networks;
To determine whether any network met all attributes and determine whether any previous studies had used attributes, such as the evaluation attributes, as a result of these findings, the research gap could be offered;
To summarise the unsolved issues related to evaluating and benchmarking Bitcoin networks based on multiple attributes;
To review the current multi-attributes decision-making (MADM) weighting and modelling methods for identifying the theory gap, as a consequence of these investigations, a novel benchmark procedure can be developed to handle the identified problems and challenges;
To review academic literature’s data set generation methods;
To provide a summary of the most recent works that have been conducted to verify and evaluate the proposed MADM solution.
To highlight the importance and innovation of the study.
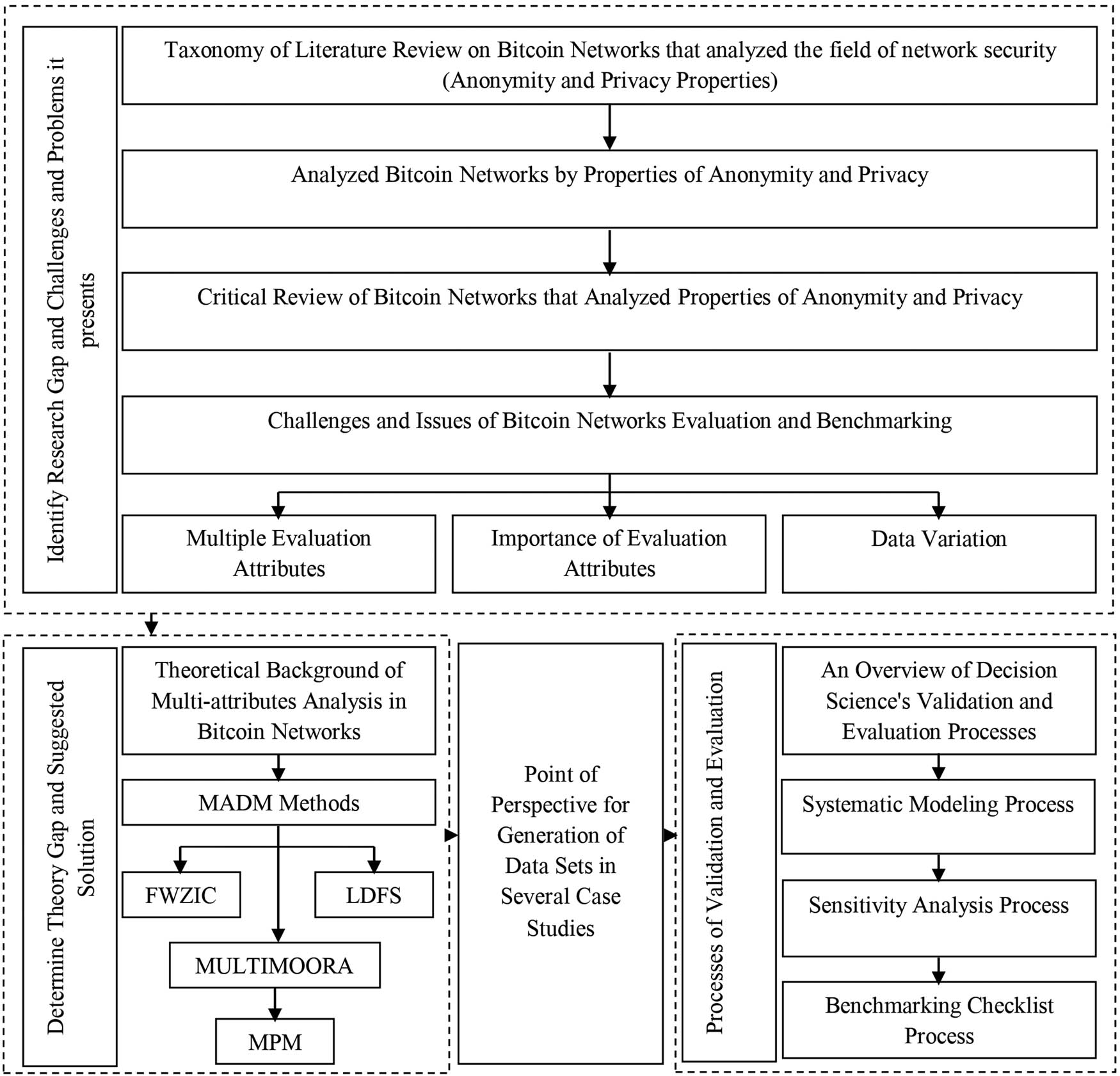
The structure of the rest of this study is as follows: Section 2 with subsections (2.1 and 2.2) presents the taxonomy of Bitcoin networks in terms of anonymity and privacy for supporting the metaverse environment in Industry 5.0 and their development attributes. Section 3 describes the critical review of Bitcoin networks that analysed anonymity and privacy characteristic properties. Section 4 with subsections (4.1, 4.2, and 4.3) provides the obstacles and problems of Bitcoin networks evaluation and benchmarking for supporting the metaverse environment in Industry 5. Section 5 presents the theoretical background of multi-attribute analysis in Bitcoin networks and economy for supporting the metaverse environment in Industry 5.0. Section 6 with subsections (6.1, 6.1.1, 6.1.1.1, and 6.1.2) provide MADM methods. Section 7 provides the point of view for the generation of data sets in different case studies. Section 8 with subsections (8.1, 8.2, and 8.3) describes the decision science’s validation and evaluation procedures. Section 9 provides the importance and innovation of the study. Section 10 presents the limitations of the study. Lastly, Section 11 presents the conclusion.
2 Taxonomy of Bitcoin networks in terms of anonymity and privacy for supporting metaverse environment in Industry 5.0 and their development attributes
The literature review thoroughly examines the intricacies surrounding the anonymity and privacy aspects of Bitcoin networks, alongside the exploration of its associated development attributes. The research initiative spanned a comprehensive period from 2018 to 2023, during which an extensive exploration was carried out across three prominent academic research databases: ScienceDirect, IEEE Xplore, and Web of Science (WoS). A meticulously crafted combination of keywords was employed to initiate the search, incorporating crucial terms such as “anonymity,” “privacy,” and “Bitcoin.” These keywords were thoughtfully linked using the “AND” operator to ensure precision. The initial query yielded a substantial volume of academic articles: 424 from ScienceDirect, 45 from IEEE Xplore, and 48 from WoS. An intricate screening process was instituted to maintain the highest level of relevance in the collected literature. This process entailed the removal of non-related articles, the elimination of duplicated articles, and the exclusion of books. Consequently, this stringent curation yielded a refined collection of 46 articles that were deemed suitable for in-depth analysis, while a total of 78 articles were scrutinised throughout the initial stages. Following this initial screening, a meticulous and comprehensive review was conducted of the selected 46 articles. This exhaustive examination reveals that seven of these articles directly aligned with the research objectives at hand. The (53) articles subsequently became the focal point of an in-depth analysis, encompassing a two-fold approach. Firstly, attention was directed towards understanding the nuanced characteristics of the Bitcoin network itself (the aspect of Bitcoin networks). Secondly, a thorough investigation was undertaken to explore the development attributes related to anonymity and privacy within this network (the aspects of anonymity and privacy development attributes). This intensive analysis unveiled valuable insights and enabled the formulation of a well-structured taxonomy. Among the corpus of literature, a subset of 22 articles was found to specifically address the anonymity and privacy development attributes applied within Bitcoin networks. As a result, 24 distinct development attributes were meticulously identified and systematically categorised. This comprehensive compilation serves as a foundational resource for comprehending the intricate dynamics governing development attributes and their profound impact on the Bitcoin network’s ability to uphold user privacy and anonymity, laying the groundwork for further exploration in this vital research area.
2.1 The aspects of anonymity and privacy development attributes
The Bitcoin network was analysed using 24 anonymity and privacy development attributes within the literature, based on analysis and suggested taxonomy (Section 2). The definitions of each attribute are summed up in the following points (Figure 1):
Built Bitcoin Client [20]: For the study, a Bitcoin client that was specifically built is employed. This property is applicable for research utilising the network and favouring a tailored customer to satisfy specific needs.
Performs Actual Deanonymisation [20]: Deanonymisation was accomplished in the studies using transactions as well as information technologies of the off-network.
Performs Flow Analysis [20]: The analysis of a Bitcoin user’s fund transfers within a defined time frame or a particular set of transactions is facilitated through blockchain data analysis. This method also allows for the monitoring of Bitcoin transfers between transactions and specific addresses.
Analysing Network by Calculating Network Metrics [20]: The assessment of the Bitcoin network is conducted based on its network metrics, which include the measured edge number, density and average path length across both user transactions and networks.
Performs Time Series Analysis [26]: The network’s future prospects are projected using this characteristic.
Performs Weight Analysis [25]: The Bitcoin amount transferred between every sender’s Bitcoin address and the recipient’s Bitcoin address is configured to a percentage. Therefore, the deanonymisation process is made straightforward by using a weight analysis approach to gather information about linked individuals who need to be emphasised.
Tools for Downloading Blockchain Data [20]: Certain tools, for example, APIs created on Bitcoin core, extract blockchain data, extending Bitcoin core and providing more indexing to improve address queries. Additional examples include Scraper and Bitcoin Core Client S/W.
Build Visual Analysis System for Bitcoin Transactions [25,27,28]: The deanonymisation process proves successful when real-world data resources are incorporated into a system of visual analysis created for Bitcoin transactions. This system utilises a graph database to evaluate the entity-level data within the transaction network. Graph visualisation allows for the straightforward calculation of paths between any two destinations.
Uses Analytical Tools [28]: A modular framework called BitIodine, using details about users’ identities and actions gleaned from publicly accessible data sources, will automatically recognise users and identify and reverse pathways among addresses or users, supporting the manual inquiry.
Analyses Legacy Wallets [30]: Bitcoin wallets older than 0.12 are called old wallets. Avoiding new and changing public keys, which users should specifically demand, prevents the reuse of addresses.
Perform Methods for Expanding the Set of Bitcoin Addresses [29]: Much like the process of conducting wallet closure analysis, wallet closure analysis aims to augment the number of Bitcoin addresses controlled by a user and establish diverse mappings between addresses and identities. One approach to achieving this is by expanding the connections between users and hidden services, thereby diversifying the array of Bitcoin addresses each user holds.
Investigates Inactive Addresses/Bitcoins [19,20,31,32]: Examining addresses stopped being used and related Bitcoins stopped being used in circulation uses off-network information blockchain data. This property can be used to calculate how many of these addresses there are compared with all other addresses or how many Bitcoins are located at these addresses. Examples include sink addresses, dormant Bitcoin addresses, and change addresses.
Uses Metrics to Measure the Success of a Clustering Strategy [25,30]: Several metrics can be used to gauge the effectiveness of a clustering strategy. Currently, the precision and recall metrics have been utilised. Precision is defined as the ratio of correctly identified public keys to the totality of public keys found by the method. Recall represents the percentage of all public keys in the wallet that were successfully recognised out of all the public keys.
Privacy or Anonymity Improvement Measures [20]: The study describes how to enhance anonymity or privacy.
Metrics to Evaluate Privacy or Anonymity [20]: In Bitcoin, measures for evaluating anonymity or privacy are provided.
Uses Threat Model [34,37]: If a malicious Bitcoin node attempts an attack by employing a deceptive node to connect input and output addresses on the blockchain to reveal users’ actual identities and transaction patterns, it can pose a serious threat. A deceptive node could actively employ Bitcoin wallet functionalities to create Bitcoin addresses and transactions. Such a deceptive node may be integrated into the Bitcoin network, leading to a deliberate and effective attempt to establish a connection between a user and an address.
Gives Cost Information of Performed Study [38]: The expense associated with research or attacking can be quantified according to financial resources, storage capacity or time.
The literature review’s framework.
2.2 Bitcoin network based on blockchain aspect for supporting metaverse environment of Industry 5.0
The adoption of blockchain technology within Bitcoin networks is of paramount importance. In contrast, every peer within the Bitcoin network maintains a blockchain replica that acts as a form of public ledger [24]. Anonymity and privacy in Bitcoin networks are therefore regarded as crucial attributes. Numerous researchers have illustrated that the utilisation of Bitcoin networks, hereafter referred to as “Bitcoin Networks,” unveils intriguing avenues for future research. Each Bitcoin network’s articles are classified using the suggested taxonomy (Figure 2) based on how they use the development attributes for anonymity and privacy.
Taxonomy of Bitcoin networks in terms of anonymity and privacy for supporting industry 5.0’s metaverse environment along with their development attributes.
Reid and Harrigan [27] considered the topological structure of a couple of networks based on the public transaction history of Bitcoin. It illustrated the existence of a non-trivial topological structure, which complements the perspectives presented by these networks, and explored the ramifications of the anonymity of the Bitcoin system. They investigated an alleged theft of Bitcoins, which at the time of the theft had a market value of roughly 500,000 US dollars, by combining these structures with outside data and methods like context discovery and flow analysis. They used the development attributes such as Performs Actual Deanonymization, Performs Flow Analysis, Analyses Network by Calculating Network Metrics, Builds Visual Analysis System for Bitcoin Transactions, Analyses Twitter Data, Investigates a Case of Real-World, and Ensures Privacy or Anonymity Improvement Measures to conduct the study. Androulaki et al. [36] used the development attributes Uses Real World Data, Privacy or Anonymity Improvement Measures, Uses Metrics to Evaluate Privacy or Anonymity, and Uses Adversary to look into how Bitcoin’s privacy features function when it is utilised as the major form of payment. To be more specific, they examined the actual Bitcoin system and a simulator that faithfully simulated university students utilising Bitcoin to evaluate the level of privacy it provides. Ober et al. [32] used development attributes such as Investigates Inactive Addresses/Bitcoins, Metrics to Evaluate Privacy or Anonymity, and Uses Adversary, to carry out empirical research in their study on network dynamics, network structure, and problems related to anonymity in addition to providing recommendations for the development of complicated payment systems in the future. Thus, they discovered dynamic effects, some of which promote anonymity while others diminish it. Ortega [39] conducted research using a development attribute, Privacy or Anonymity Improvement Measures, to study the anonymity of the Bitcoin network. Baumann et al. [40] utilised the graph mining algorithms and current data to conduct network analysis of the Bitcoin transaction graph. Different aggregations and sub-graphs of the network were subjected to analysis using development attributes, namely, Performs Actual Deanonymisation and Analyses Network by Calculating Network Metrics). Meiklejohn et al. [19] investigated the Bitcoin network employing development attributes such as Performs Actual Deanonymization, Performs Flow Analysis, Investigates a Case of Real-World, Investigates Inactive Addresses/Bitcoins [28] used BitIodine, combining addresses that probably pertain to the same person or a group of users, classify and label these people and addresses and visualise complex data taken from the Bitcoin network. They carried out the study utilising developmental attributes such as Performs Actual Deanonymization, Performs Flow Analysis, Uses Tools for Downloading Blockchain Data, Builds Visual Analysis System for Bitcoin Transactions, Uses Analytical Tools, Investigates a Case of Real-World and Gives Cost Information of Performed Study). Nick [30] utilised development attributes such as Uses Real World Data, Analyses Legacy Wallets, Uses Metrics to Measure the Success of a Clustering Strategy and Uses Privacy or Anonymity Improvement Measures to evaluate the performance of various clustering algorithms in the digital peer-to-peer currency Bitcoin. Zhao and Guan [41] made use of development attributes, including Performs Flow Analysis, Analyses Network by Calculating Network Metrics and Investigates a Case of Real-World to describe a graph-based approach for studying the identity clustering and currency flow aspects of Bitcoin transactions. Fleder et al. [37] employed attributes of development such as Performs Actual Deanonymisation, Performs Flow Analysis, Tools for Downloading Blockchain Data, Investigates a Real-World Case, and Uses Threat Model to develop a system for scraping Bitcoin addresses. Along with that, they added a system for connecting users to transactions using erroneous transaction data. Möser et al. [38] reported the findings of the first systematic examination of Bitcoin’s anti-money laundering (AML) potential and constraints. It attempted to link anonymous transactions to their test accounts using reverse methodologies in a series of experiments to learn how the system worked. The ramifications for Bitcoin as a decentralised currency are discussed, along with alternative AML procedures that they drew up that consider a lack of knowledge about genuine identities while still utilising transaction graph public information. They employed development attributes, such as Performs Flow Analysis, Uses Tools for Downloading Blockchain Data, Uses Metrics to Evaluate Privacy or Anonymity, and Gives Cost Information of Performed Study to achieve the investigation. Using real-time transaction flow gathered over a five-month period, they provided a novel method to build and assess mappings [22]. They created heuristics for determining who owns what Bitcoin addresses and IP addresses. They focused on the circumstances in which these links became obvious and showed how utilising anomalous relaying behaviour roughly maps 1,000 Bitcoin addresses to their likely owner IPs. They used the development attributes Built Bitcoin Client and Gives Cost Information of Performed Study to conduct the study [35] developed a successful method for deanonymising Bitcoin users. Their methods prove effective even in the most common and challenging scenarios where users are shielded by their Internet Service Providers’ Network Address Translators (NATs) or firewalls. These methods facilitate the connection of a user’s transactions that take place behind a NAT while distinguishing between the connections and transactions of multiple users who share the same NAT. They demonstrated how the Bitcoin network’s anti-DoS defences might be used to bypass a natural defence of using Tor or other anonymity services to lessen these new threats, they suggested a number of countermeasures. They achieved that by utilising development attributes Built Bitcoin Client, Analyses Network which uses Hidden Services, Uses Privacy or Anonymity Improvement Measures, Uses Adversary and Gives Cost Information of Performed Study. Additionally, by integrating Tor and Bitcoin, as demonstrated by ref. [24], an attack vector for deterministic and covert man-in-the-middle attacks is created. When users choose to connect directly to the Bitcoin network, they demonstrated how an attacker may fingerprint them, identify them and discover their IP address. They accomplished this by employing development attributes like Builds Bitcoin Client; Analyses Network, which Uses Hidden Services, Privacy or Anonymity Improvement Measures and Uses Adversary. Fanti and Viswanath [33] modelled the Bitcoin networking stack and examined its anonymity characteristics before and after 2015. The study considered recent adversarial models and propagation techniques. They theoretically demonstrated that, in networks with a regular-tree topology, Bitcoin’s networking protocols (from before and after 2015) give subpar anonymity characteristics. It used a 2015 snapshot of the actual Bitcoin peer-to-peer (P2P) network topology in simulation to verify their assertion, which was accomplished by utilising specific developmental attributes like Analyses Network by Calculating Network Metrics, Uses Real World Data, Predictions and Uses Adversary. By merging blockchain and network data, Neudecker and Hartenstin [31] investigated whether the clustering process might be facilitated. They used all relevant clustering heuristics they were aware of for this purpose and applied them to the data in the current blockchain, then linked the resulting clusters to IP address data they had gleaned by studying the Bitcoin network’s message flooding procedure. The analysis was accomplished using the development attributes Investigates Inactive Addresses/Bitcoins and Gives Cost Information of Performed Study. With a particular focus on how it is distributed among various autonomous systems, [42] revealed unique insights regarding the P2P network of Bitcoin. They travelled the P2P network of Bitcoin in a protocol-compliant way while gathering data on the network’s size, clients, and distribution across autonomous systems. They employed development attributes such as Tools for Downloading Blockchain Data and Metrics to Evaluate Privacy or Anonymity [29] used publicly available data from online social networks, the blockchain and onion websites to do a study on the viability of de-anonymising Tor hiding services used by users who pay with Bitcoin. The study used development attributes such as Performs Actual Deanonymisation, Performs Flow Analysis, Analyses Network Which Using Hidden Services, Using Tools for Downloading Blockchain Data, Using Analysis Including Twitter Data, Investigates a Case of Real-World, Performs Methods for Expanding the Set of Bitcoin Addresses, Using Privacy or Anonymity Improvement Measures, Uses Adversary, Gives Cost Information of Performed Study. Nerurkar et al. [26] explored the local topologies and architecture of the Bitcoin networks throughout its early years in this study. They processed transaction data for Bitcoin spanning from January 3, 2009, at 12:45:05 GMT, to May 8, 2020, at 13:21:33 GMT to construct a Bitcoin user graph. The user’s graph was examined at ten intervals, each with a break of one year, between 2009 and 2020. They employed development attributes such as Analyses Network by Calculating Network Metrics, Training Machine Learning Models, Performs Time Series Analysis, Predictions, Gives Cost Information of Performed Study. Lv et al. [25] developed a system for visual analysis of Bitcoin transactions using a graph-based database and leveraged various authentic database resources to scrutinise exchanges’ entity information during the procedure, attempting to understand the implications of deanonymisation. The investigation is carried out by employing the following development attributes: Performs Actual Deanonymisation, Performs Flow Analysis, Trains Machine Learning Models, Performs Weight Analysis, Builds Visual Analysis System for Bitcoin Transactions, Uses Real-World Data, Investigates a Case of Real-World, Uses Metrics to Measure the Success of a Clustering Strategy, Predictions, and Gives Cost Information of Performed Study. Ansah et al. [34] underscored the significance of the protection of user identification and transaction history within Bitcoin cryptocurrency transactions in their research. The development attributes employed were Uses Privacy or Anonymity Improvement Measures, Adversary and Threat Model. Over the initial decade of the Bitcoin network’s existence, Kumar et al. [43] conducted a research study to investigate the network’s architecture and geometry on a local level by constructing a Bitcoin user graph through the processing of data from Bitcoin transactions. The study employed the development attributes Analyses Network by Calculating Network Metrics, Gives Cost Information of Performed Study.
3 Critical review of Bitcoin networks that analysed anonymity and privacy characteristic properties
Many academics have become interested in the literature regarding Bitcoin networks. Table 1 lists the various sets of attributes included in each network under the major category of Bitcoin networks. A total of 24 development attributes were used to examine the networks. The major Bitcoin category includes 22 networks. Table 1 shows that 22 Bitcoin networks were provided, two of which (29%) had seven development attributes, whereas six (16%) had four development attributes. Three (12%) of the Bitcoin networks had three development attributes, whereas one (4%) only had one. Three (20%) of the Bitcoin networks had five development attributes, compared with five (8%) networks with two. Ten development attributes were present in two Bitcoin networks (41%). The Gives Cost Information of Performed Study attribute had an overall present rate of 40.90%.
The analysing studies of Bitcoin networks for supporting the metaverse environment in Industry 5.0
| Nets/Attributes | Built Bitcoin Client | Performs Actual Deanonymisation | Performs Flow Analysis | Analyses Network by Calculating Network Metrics | Analyses Network Which Using Hidden Services | Training Machine Learning Models | Performs Time Series Analysis | Performs Weight Analysis | Tools for Downloading Blockchain Data | Build Visual Analysis System for Bitcoin Transactions | Uses Analytical Tools | Analysis Included Twitter Data | Uses Real World Data | Analysis Legacy Wallets | Investigates a Case of Real-World | Performs Methods for Expanding the Set of Bitcoin Addresses | Investigates Inactive Addresses/Bitcoins | Uses Metrics to Measure the Success of a Clustering Strategy | Privacy or Anonymity Improvement Measures | Metrics to Evaluate Privacy or Anonymity | Predictions | Uses Adversary | Uses Threat Model | Gives Cost Information of Performed Study | Attributes development percentage |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| BN1 [27] | X | √ | √ | √ | X | X | X | X | X | √ | X | √ | X | X | √ | X | X | X | √ | X | X | X | X | X | 29.16 |
| BN2 [36] | X | X | X | X | X | X | X | X | X | X | X | X | √ | X | X | X | X | X | √ | √ | X | √ | X | X | 16.66 |
| BN3 [32] | X | X | X | X | X | X | X | X | X | X | X | X | X | X | X | X | √ | X | X | √ | X | √ | X | X | 12.5 |
| BN4 [39] | X | X | X | X | X | X | X | X | X | X | X | X | X | X | X | X | X | X | √ | X | X | X | X | X | 4.16 |
| BN5 [40] | X | √ | X | √ | X | X | X | X | X | X | X | X | X | X | X | X | X | X | X | X | X | X | X | X | 8.33 |
| BN6 [19] | X | √ | √ | X | X | X | X | X | X | X | X | X | X | X | √ | X | √ | X | X | X | X | X | X | X | 16.66 |
| BN7 [28] | X | √ | √ | X | X | X | X | X | √ | √ | √ | X | X | X | √ | X | X | X | X | X | X | X | X | √ | 29.16 |
| BN8 [30] | X | X | X | X | X | X | X | X | X | X | X | X | √ | √ | X | X | X | √ | √ | X | X | X | X | X | 16.66 |
| BN9 [41] | X | X | √ | √ | X | X | X | X | X | X | X | X | X | X | √ | X | X | X | X | X | X | X | X | X | 12.5 |
| BN10 [37] | X | √ | √ | X | X | X | X | X | √ | X | X | X | X | X | √ | X | X | X | X | X | X | X | √ | X | 20.83 |
| BN11 [38] | X | X | √ | X | X | X | X | X | √ | X | X | X | X | X | X | X | X | X | X | √ | X | X | X | √ | 16.66 |
| BN12 [22] | √ | X | X | X | X | X | X | X | X | X | X | X | X | X | X | X | X | X | X | X | X | X | X | √ | 8.33 |
| BN13 [35] | √ | X | X | X | √ | X | X | X | X | X | X | X | X | X | X | X | X | X | √ | X | X | √ | X | √ | 20.83 |
| BN14 [24] | √ | X | X | X | √ | X | X | X | X | X | X | X | X | X | X | X | X | X | √ | X | X | √ | X | X | 16.66 |
| BN15 [33] | X | X | X | √ | X | X | X | X | X | X | X | X | √ | X | X | X | X | X | X | X | √ | √ | X | X | 16.66 |
| BN16 [31] | X | X | X | X | X | X | X | X | X | X | X | X | X | X | X | X | √ | X | X | X | X | X | X | √ | 8.33 |
| BN17 [42] | X | X | X | X | X | X | X | X | √ | X | X | X | X | X | X | X | X | X | X | √ | X | X | X | X | 8.33 |
| BN18 [29] | X | √ | √ | X | √ | X | X | X | √ | X | X | √ | X | X | √ | √ | X | X | √ | X | X | √ | X | √ | 41.66 |
| BN19 [26] | X | X | X | √ | X | √ | √ | X | X | X | X | X | X | X | X | X | X | X | X | X | √ | X | X | √ | 20.83 |
| BN20 [25] | X | √ | √ | X | X | √ | X | √ | X | √ | X | X | √ | X | √ | X | X | √ | X | X | √ | X | X | √ | 41.66 |
| BN21 [34] | X | X | X | X | X | X | X | X | X | X | X | X | X | X | X | X | X | X | √ | X | X | √ | √ | X | 12.5 |
| BN22 [43] | X | X | X | √ | X | X | X | X | X | X | X | X | X | X | X | X | X | X | X | X | X | X | X | √ | 8.33 |
| Overall | 13.63 | 31.81 | 36.36 | 27.27 | 13.63 | 8.33 | 4.54 | 4.54 | 22.72 | 13.63 | 4.54 | 9.09 | 18.18 | 4.54 | 13.81 | 4.54 | 13.63 | 9.09 | 36.36 | 18.18 | 13.63 | 13.81 | 9.09 | 40.90 |
BN stands for Bitcoin Network.
The attributes Uses Privacy or Anonymity Improvement Measures and Performs Flow Analysis had a current rate of 36.36% in contrast to this. The attributes Uses Adversary, Investigates a Case of Real-World and Performs Actual Deanonymisation had a present rate of 31.81%. The present rates for the attributes Analyses Network by Calculating Network Metrics and Using Tools for Downloading Blockchain Data were 27.27 and 22.72%, respectively. The attributes Uses Metrics to Evaluate Privacy or Anonymity and Uses Real World Data had a present rate of 18.18%. The attributes Makes Predictions, Investigates Inactive Addresses/Bitcoins, Builds Visual Analysis System for Bitcoin Transactions, Analyses Network which Use Hidden Services, Built Bitcoin Client existed with a present rate of 13.63%. The attributes Uses Threat Model, Uses Metrics to Measure the Success of a Clustering Strategy and Analyses Included Twitter Data had the present rate of 9.09%. For the attributes Training Machine Learning Models, the current rate was 8.33%. The final attributes Uses Analytical Tools, Performs Weight Analysis, Performs Time Series Analysis, Analyses Legacy Wallets and Performs Methods for Expanding the Set of Bitcoin Addresses had a present rate of 4.54%.
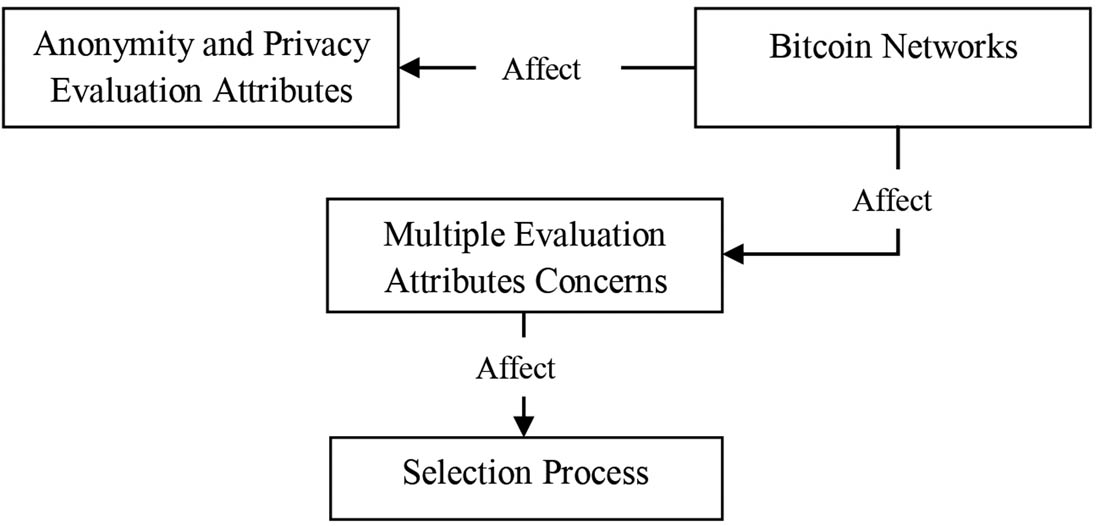
In light of these considerations, research has revealed that the development attributes of different Bitcoin network alternatives directly impact anonymity and privacy. The analysis process of Bitcoin networks necessitates a combination of developmental attributes related to anonymity and privacy to cater to the metaverse environment of Industry 5.0. However, no study has examined the combined effects of all the development attributes related to anonymity and privacy on the alternative Bitcoin networks or utilised them as evaluation attributes. Therefore, modelling the ideal Bitcoin network is important and difficult. Three pivotal aspects must be tackled to create an effective model of Bitcoin networks in the context of Industry 5.0’s metaverse: the multitude of anonymity and privacy evaluation attributes, the importance of attributes, and the data variability [44]. Previous studies in Bitcoin networks employed certain development attributes like “Built Bitcoin Client,” “Uses Ground Truth Data,” “Performs Flow Analysis,” and “Analyses Network by Calculating Network Metrics.” Therefore, a multitude of attributes must be considered when modelling these networks to suit the metaverse environment of Industry 5.0. These development attributes have been combined in diverse ways in prior research, leading to a lack of consensus on their relative importance. Moreover, given that certain Bitcoin networks exhibit excellence in specific attributes while others surpass them in different aspects, the emergence of a complex MADM becomes a challenge when modelling for Industry 5.0’s metaverse environment. Decision-making, a ubiquitous human activity [44], encompasses the process of deciding on the Bitcoin network that will best support Industry 5.0’s metaverse environment, considering particular attributes. This process shapes the future direction of the metaverse within the framework of Industry 5.0. The existing Bitcoin networks must not be compared as a single homogeneous platform because of their inherent differences. This distinction will continue to be relevant in future research and analysis concerning the implementation of the metaverse environment in Industry 5.0, highlighting it as a research gap.
4 Obstacles and problems of Bitcoin network evaluation and benchmarking for supporting metaverse environment in Industry 5.0
Numerous researchers made attempts to model Bitcoin networks for supporting the metaverse environment in Industry 5.0 via the incorporation of various development attributes [1]. However, none of them evaluated and benchmarked Bitcoin networks’ development attributes. Moreover, analysing and comparing Industry 5.0 networks in Bitcoin to choose the best network is challenging. Furthermore, this process is made more difficult by the various ways that these evaluation attributes might be combined in Bitcoin Industry 5.0 networks. Given these discrepancies, comparing the current networks from one perspective to the other would be unfair. Multiple evaluation attributes, the significance of the attributes and data variation are three pressing challenges that must be resolved in comparing Bitcoin Industry 5.0 networks to close the research gap [2]. Details on these concerns are provided in the ensuing subsections (Figure 3).
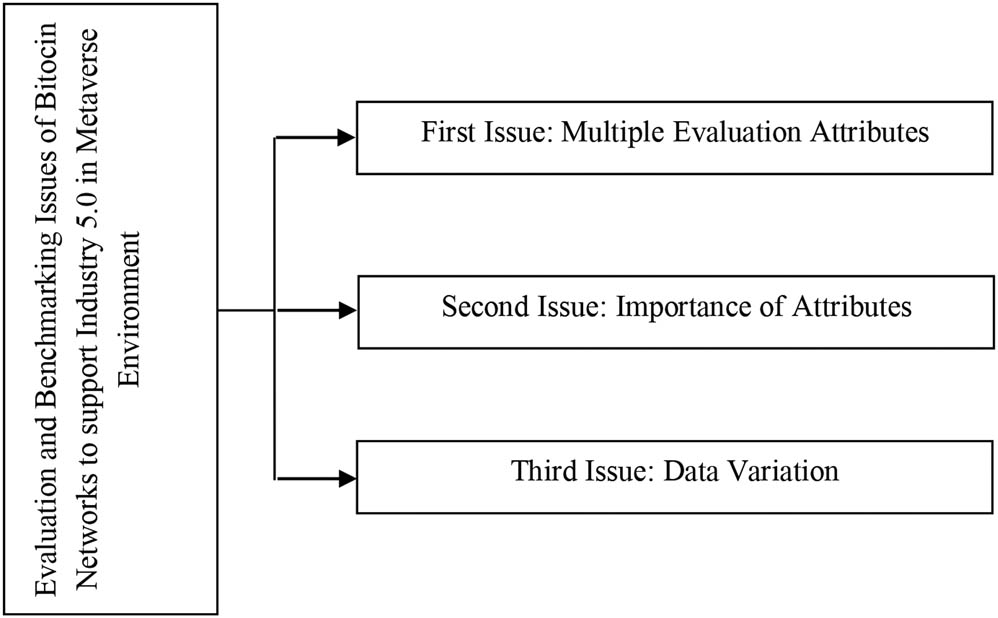
Challenges with benchmarking and evaluating the Bitcoin networks for supporting metaverse environment in Industry 5.0.
4.1 Concern with the multiple Bitcoin network evaluation attributes
The availability of multiple evaluation attributes makes evaluating and benchmarking Bitcoin networks challenging for supporting the metaverse environment in Industry 5.0. The optimal network must be chosen during the benchmarking procedure [2]. Twenty-four attributes can be used for benchmarking Bitcoin networks. When benchmarking Bitcoin networks, the difficulty with the multiplicity of attributes that were outlined in both scenarios will become apparent. This issue is regarded as the real issue that has to be addressed.
Figure 4 illustrates how the selection procedure may be impacted by the respective attributes of each Bitcoin network for supporting the metaverse environment in Industry 5.0. Choosing the optimal network in this situation is difficult because Bitcoin network A might be modelled first based on the Built Bitcoin Client attribute. In contrast, the Performs Actual Deanonymisation attribute allows Bitcoin network B to be rated first. A curious question is raised in this scenario: which Bitcoin network will be modelled first (model = 1)? Given that using a single measure to compare the performance of Bitcoin industry 5.0 networks is considered unfair, numerous evaluation attributes need to be considered.
Multiple attributes evaluation concerns of Bitcoin network for supporting metaverse environment in Industry 5.0 and contribution processes.
4.2 Concerns with relative significance of the Bitcoin networks’ evaluation attributes
Various developmental attributes have been employed to facilitate the advancement of Bitcoin networks, with the aim of bolstering their role in supporting the metaverse environment in Industry 5.0 and enhancing their overall services. Depending on their goals, these development attributes have varying relative importance. Reid and Harrigan [27] used development attributes such as Performs Actual Deanonymisation, Performs Flow Analysis, Analyses Network by Calculating Network Metrics, Builds Visual Analysis System for Bitcoin Transactions, Analyses Included Twitter Data, Investigates a Case of Real-World, Privacy or Anonymity Improvement Measures. Meiklejohn et al. [19] investigated using the development attributes such as Performs Actual Deanonymisation, Performs Flow Analysis, Investigates a Case of Real-World and Investigates Inactive Addresses/Bitcoins [30] employed the development attributes Uses Real World Data, Analysis Legacy Wallets, Uses Metrics to Measure the Success of a Clustering Strategy, and Uses Privacy or Anonymity Improvement Measures. The relative importance of attributes varied in these three scenarios. Each attribute’s proportional weight, which is regarded as a problem in assessing and benchmarking Bitcoin, is crucial to consider each attribute’s proportional weight properly, which is regarded as a problem in assessing and benchmarking Bitcoin. Thus, the benchmarking procedure is significantly complicated by the variance in importance across the attribute. This problem can be addressed by developing a suitable approach that prioritises development attributes over other considerations. Each set of attributes should be evaluated to ascertain each attribute’s relative importance to the others, as shown in Figure 5. This evaluation will assist in resolving the issue of the significance of the attributes. As a result, each attribute should be assigned a fair amount of weight during the evaluation procedure, depending on how significant it is to the Bitcoin network.
Attribute importance concern of Bitcoin networks for supporting metaverse environment in Industry 5.0 and contribution processes.
4.3 Concerns about the data variation
The difficulty in benchmark tasks for Bitcoin networks for supporting metaverse environment in Industry 5.0 escalates proportionately to data variation. Given the disparity in the amount of data accessible for various attributes, decision-makers have difficulty comparing alternatives (Bitcoin networks). Zhao and Guan [41] conducted the study using development attributes (i.e. Performs Flow Analysis, Analyses Network by Calculating Network Metrics and Investigates a Case of the Real-World). Fleder et al. [37] completed the analysis using development attributes Performs Actual Deanonymisation, Performs Flow Analysis, Uses Tools for Downloading Blockchain Data, Investigates a Real-World Case and Uses Threat Model. Möser et al. [38] used the development attributes Performs Flow Analysis, Uses Tools for Downloading Blockchain Data, Uses Metrics to Evaluate Privacy or Anonymity, and Give Cost information of Performed Study. For each scenario, the data for these attributes varied among the high, higher and highest levels. Therefore, resolving this problem is essential because it makes choosing easier when working with large amounts of data. To ensure a better selection process, according to Figure 6, data variations could occur if the attribute’s maximisation strategies impact data for alternatives (high, higher, and highest levels). Bitcoin networks’ assessment and benchmarking to enable their support for the metaverse within Industry 5.0 will lead to complicated multiple attributes decision-making challenges following these concerns (Sections 4.1, 4.2, and 4.3). However, assessing and benchmarking these networks according to different development attributes still have a problem.
The concern on data variation of Bitcoin networks to support metaverse environment in Industry 5.0 and contribution procedures.
5 Theoretical background of multi-attributes analysis in Bitcoin networks and economy for supporting metaverse environment in Industry 5.0
The operational research and decision sciences subfield is known as MADM, which considers various attributes and describes the decision under many attributes, where experts or decision makers must select from a range of possibilities alternatives and options while taking a variety of characteristics/attributes that describe the options that are being considered [45,46]. Thokala et al. [47] defined the subsequent essential steps of the MADM process: A decision matrix is created, uncertainty is dealt with, attributes are weighted, alternatives are scored and the decision problem is identified. The steps are (i) determining decision-making issue, (ii) determining and choosing attributes, (iii) determining probable alternatives, (iv) hiring specialists to conduct a reliable assessment, (v) building a decision matrix, and (vi) handling uncertainty. Several studies are frequently utilised for processing MADM problems in various fields and areas associated with Bitcoin, other cryptocurrencies and blockchain. Zolfani et al. and Maghsoodi [48,49] carried out studies on the application of MADM approaches in cryptocurrency portfolio allocation. Siddiqui and Haroon [50] conducted a study to detect and track essential variables influencing the slow progress of blockchain technology’s adoption. Zulqarnain et al. [51] carried out a study to conduct an operational and appropriate exploration of the cryptocurrency market. Filatovas et al. [52] introduced a framework for selecting the best consensus protocols. Mohanty and Dash and Dinshaw et al. [53,54] conducted studies to forecast the price of Bitcoin accurately. In the current technology world, Ecer et al. [55] sought to identify the best cryptocurrencies for investing within their study. Farida and Khasanah [56] conducted a study to evaluate and identify the most suitable public blockchain platforms. Hacioglu et al. [57] determined the optimum cryptocurrency mining strategy in their study.
6 MADM methods
The literature has a wide variety of MADM methods, each with features and drawbacks [44,58,59,60,61,62,63]. Mathematical- and human-based approaches are two groups into which MADM methods are divided in the studies by Salih et al. [64,65]. The first is employed for modelling alternatives depending on several evaluation attributes. The second is employed for determining how important each evaluation attribute should be given. The most popular MADM mathematical approaches are the Technique for Order of Preference by Similarity to Ideal Solution (TOPSIS), Simple Additive Weighting, VlseKriterijumska Optimizacija i Kompromisno Resenje (VIKOR) and Multi-Objective Optimisation based on a Ratio Analysis plus the Full Multiplicative Form (MULTIMOORA). Studies and own analysis show that none of the approaches above have been employed to model the identified Bitcoin network-based metaverse. However, MULTIMOORA is the preferred and most suitable method because it models ideal solutions. The triple subordinate modelling methods that gave MULTIMOORA strength are described in Table 2. Thus, the MULTIMOORA can be used to compare and choose the best Bitcoin network for supporting metaverse environment in Industry 5.0. MULTIMOORA is unable to determine the weights of the attributes. The usage of an external approach must thus be used to calculate the attributes' weights. This calculation is accomplished in the literature using human-based approaches.
The three subordinate modelling methods of MULTIMOORA and their relation with other MADM approaches
| Subordinate Modelling Methods | Brief Description | The Relationship between Methods and other MADM Approaches |
|---|---|---|
| Ratio System | The fully compensatory model makes use of the arithmetic weighted aggregation operator, which implies that the same degree of big values could fully compensate for the minor normalised values of an alternative [66] | SAW serves as the basis for the ratio system. Other MADM methods like WASPAS and MOOSRA used the ratio system |
| Reference Point Approach | According to this approach, the best alternative has the lowest value across all attributes. As a model that is not compensatory, the lowest-rated options are chosen to represent the best value by identifying those that perform the worst performance in relation to each attribute [66] | TOPSIS and VIKOR were included in the group of ‘Goal or Reference Level Models’ |
| Full Multiplicative Form | A partially compensatory approach, the Full Multiplicative Form makes use of the geometric weighted aggregation operator. This approach prevented an alternative’s low normalised values from being totally offset by high values. Given this problem, a moderately performing alternative is preferable to one that performs poorly on some attributes while doing well on others [66] | Other MADM methods, such as WASPAS, use the idea of a Full Multiplicative Form |
6.1 MULTIMOORA
An effective method for making decisions based on multiple attributes is MULTIMOORA [66]. MULTIMOORA produces a model by integrating the findings from three methods of modelling: the Ratio System, Reference Point Approach and Full Multiplicative Form. MOORA (Multi-Objective Optimisation based on a Ratio Analysis), which combines the Ratio System and Reference Point Approach, was introduced in 2006 by Brauers and Zavadskas [67]. In 2010, Brauers and Zavadskas [68] upgraded MOORA to MULTIMOORA, implementing the Full Multiplicative Form and using Dominance Theory for generating a holistic modelling according to the results of triple subordinate methods. Ratio System and the Full Multiplicative Form both belong to the first group of MADM approaches, while Reference Point Approach belongs to the second. Ratio System, Reference Point Approach, and Full Multiplicative Form are subordinate modelling methods used by MULTIMOORA that are described in Table 2, which also uses the vector normalisation method to produce similar ratings. Every one of the three modelling approaches has pros and cons, which is why MULTIMOORA employs multiple strategies. Before using the ratings in an MADM model, they need to be normalised because the ratings of the alternatives on the problem’s various attributes could come in various dimensions. In MADM approaches, many normalisation strategies have been used [66]. Liao et al. [69] compared several normalising strategies. Van Delft and Nijkamp (also known as Vector) Normalisation, is the most trusted option to employ in MULTIMOORA according to Brauers et al. [70]. The ratio system is helpful when “independent” attributes are present in the problem because it is a completely compensating model.
The Full Multiplicative Form, which is not fully compensatory, is useful for situations with “dependent” attributes. Ratio System and Full Multiplicative Form are being contrasted using the “conservative” Reference Point Approach, a non-compensatory approach. Ratio System and Full Multiplicative Form present opportunities to compensate for an alternative’s subpar performance on one attribute with excellent performance on another (although the compensation levels for the two procedures are not comparable). Reference Point Approach does not. Given that the problem may contain both “dependent” and “independent” attributes simultaneously, MULTIMOORA combines the three methods to capitalise on each one’s advantages and yield a result more trustworthy than the combination of its parts [71].
6.1.1 Methods of weighting attributes
When analysing the overall utility values of the problem’s alternatives, attribute weights are crucial because of the many different attributes in the MADM problem, and their significance is not always the same [72]. Weights are important parameters when determining how each attribute affects the outcome [73]. The weights assigned to the attributes could be subjective based on the views of experts or objectively determined by how well the decision matrix’s data is organised. One expert or several decision-makers may be used in the process of weighing the attributes [74]. AHP (Analytic Hierarchy Process), which employs the idea of pairwise comparison, is a widely used approach for subjective weighting. BWM, (Best Worst Method) based on comparison using the best and worst attributes, is another significant subjective weighting system. Various methods, like Entropy and CRITIC (Criteria Importance Through Intercriteria Correlation), fall within the heading of objective weighting methods. The contrast between attributes has been provided for MULTIMOORA models using several weighting methods. These weighting methods are shown in Figure 7.
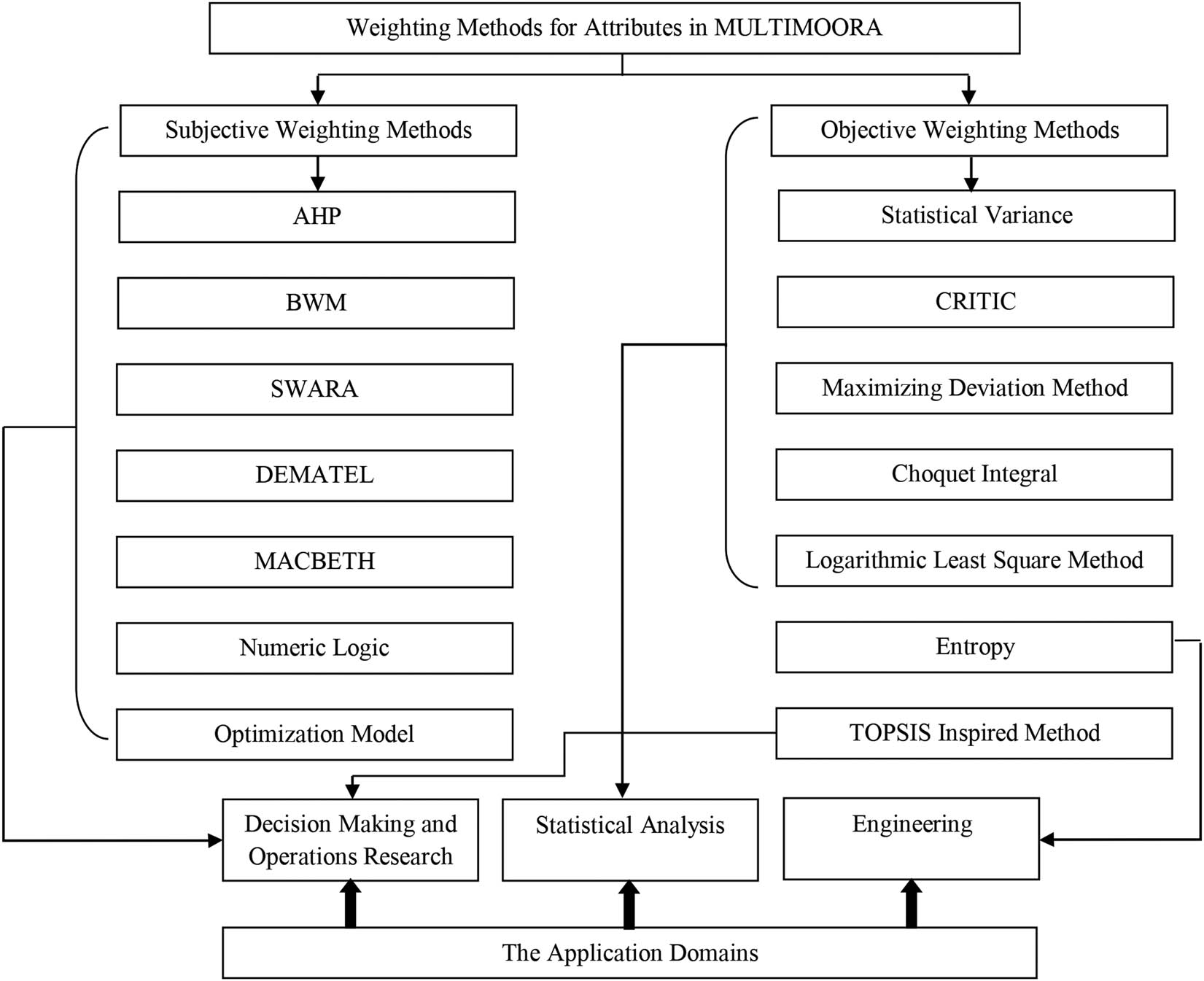
Weighting methods for attributes in MULTIMOORA and its application domains.
Figure 7 shows that the number of subjective weighting methods (i.e. both seven items) is equivalent to the ones used by objective weighting methods. Following their scientific backgrounds, three categories of weighting methods can be identified [66]: (i) Decision-making and operations research methods include AHP, BWM, SWARA, DE-MATEL, TOPSIS-Inspired Method, Optimisation Model, MACBETH, and Numeric Logic. (ii) Statistical analysis techniques include the Choquet Integral, Statistical Variance, CRITIC, Maximising Deviation Method and Logarithmic Least Square Method. (iii) Engineering Entropy in Practice includes methods that can serve as MADM approaches because they can be used to calculate the relative utility of alternatives. Entropy originates from thermodynamics theory and is a key idea in engineering. Figure 8 shows the distribution of MULTIMOORA’s Weighting Methods based on their percentage frequency in references.
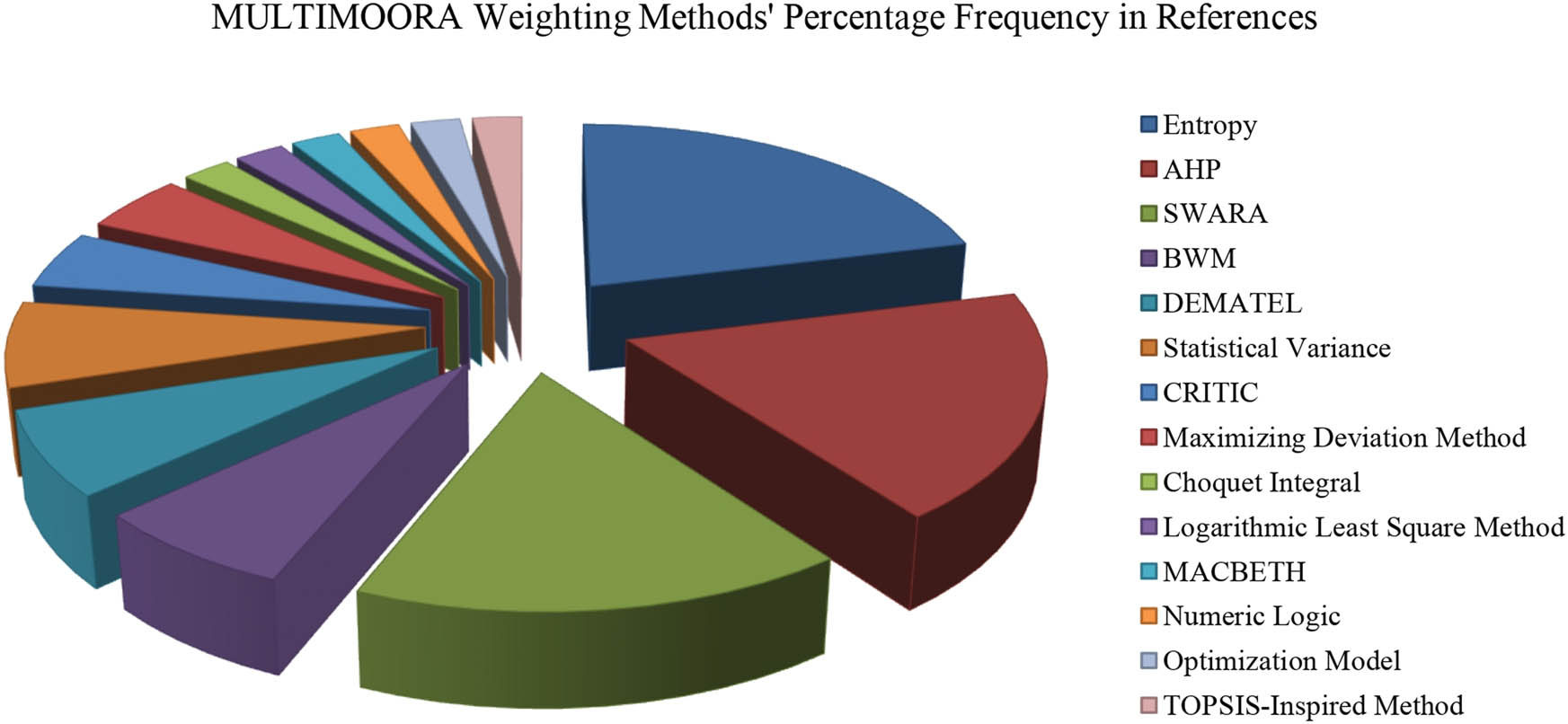
Distribution of MULTIMOORAs’ weighting methods.
As illustrated by Figure 8, the study’s data show that the entropy approach gained 8.5 percentage frequencies, which equals 21%. The AHP method gained 7.5 percentage frequencies (19%). SWARA method obtained 6.6 percentage frequencies (16%). The percentage frequencies of BWM, DEMATEL, and Statistical Variance methods were 2.8, equal to 7%. Moreover, the CRITIC and Maximising Deviation Method gained 1.9 percentage frequencies, which equals 5%. Finally, Choquet Integral, Logarithmic Least Square Method, MACBETH, Numeric Logic, Optimisation Model, and TOPSIS-Inspired Method gained 0.9 percentage frequency, which equals 2%. Overall, given what has been explained above and concerning the weighting approaches’ main flaws, which are represented by data variation, their lack of reliance on expert opinion (concerning the objective approaches) and the issue of inconsistency (concerning the subjective approaches), own investigation reveals that none of the methods have been used to calculate the anonymity and privacy attributes. However, the FWZIC method [75] outperformed these methods (i.e. AHP, ANP, and BWM). Therefore, it can be used to evaluate the privacy and anonymity attributes of Bitcoin networks for supporting the metaverse environment of Industry 5.0.
6.1.1.1 FWZIC
Irrespective of the number of attributes involved, the FWZIC approach [75,76] is used to establish weight coefficients for attributes exhibiting zero inconsistency. For a certain hierarchy level, the FWZIC approach accurately and separately determined each attribute’s local and global weight coefficient values, yielding zero inconsistency [75]. Additionally, using experts’ preferences, the FWZIC method can determine the weighting of every attribute in the decision-making procedure [76]. It is used in smart e-tourism information management applications, where the inconsistency problem is successfully solved [76] and weights many-objective optimisation algorithms [75]. The privacy and anonymity attributes of Bitcoin networks are used to support Industry 5.0’s metaverse environment. Triangular fuzzy numbers (TFNs) are employed in the original FWZIC approach [75], whereas each membership grade input is represented as a crisp value [77]. The challenge of directly defining membership values in TFNs was covered in the study by Liao [78]. TFNs also fell short of direct modelling and reducing the consequences of uncertainty for data [79]. The same research team expanded the FWZIC approach utilising trapezoidal fuzzy numbers (TrFN) [76]. TrFN can describe second-order uncertainty [80], define the precise membership function [81] and facilitate simple calculations [82]. All intermediate degrees of membership, except for 0 or 1, were linearised by TrFN [82], which may not be accepted if we concentrate on a specific level of uncertainty. The issues of ambiguity, hesitation, and uncertainty significantly impact the final score given to the alternatives in MADM. Usually, these problems are a result of decision-makers’ opinions. Vagueness, hesitancy, and uncertainty in information can be identified and conveyed in various manners. As a way to address these decision-making problems, fuzzy set theory has become increasingly popular [83].
Thus, FWZIC expanded under additional fuzzy set environments, such as neutrosophic fuzzy sets [44], Pythagorean fuzzy sets (PyFSs) [84], cubic Pythagorean fuzzy environment [85], interval type-2 trapezoidal-fuzzy environment (IT2TR) [76], dual-hesitant fuzzy environment [86], q-rung orthopair fuzzy environment (q-ROFs) [87], and T-spherical fuzzy environment (T-SFS) [61]. A list of fuzzy set environments used with FWZIC is shown in Figure 9. The problems of ambiguity, hesitation, and doubt continue to be unresolved despite these attempts.
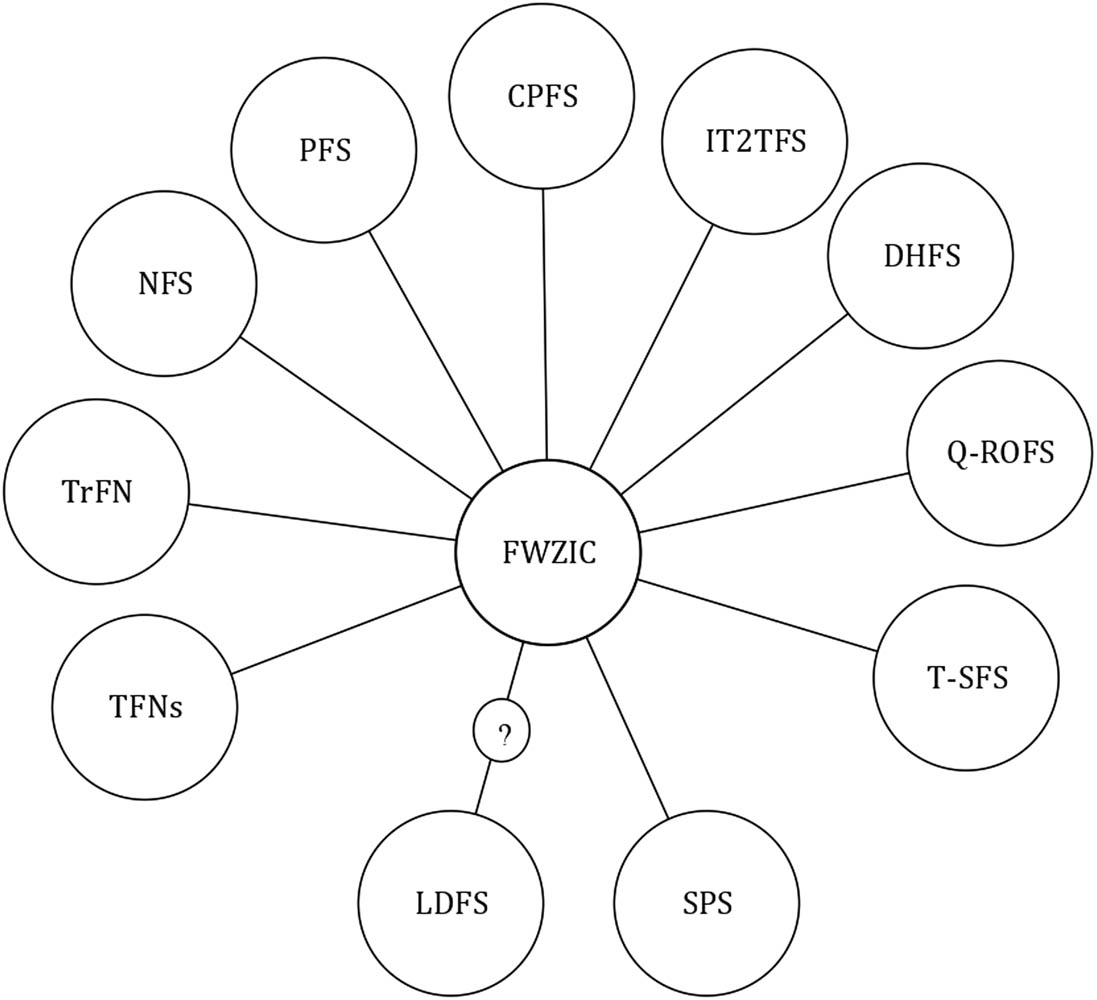
A synopsis of the fuzzy set environments utilised with the FWZIC.
6.1.1.1.1 Linear Diophantine fuzzy set (LDFS)
Ambiguous language is frequently utilised to convey the limitations of human cognition thinking along with decision-making knowledge. Several scholars have embraced fuzzy sets to address the uncertainty and ambiguity that are issues associated with MADM concerns. Typically, decision-making under uncertainty is difficult because of the problematic position of predicting and managing such uncertainties. Utilising the ideas of membership grades (denoted by (x)) and non-membership grades (denoted by v(x)) and a restriction in which the sum of both of these grades could not be greater than unity, Atanassov [88] developed intuitionistic fuzzy sets (IFSs) as the extension of a fuzzy set. The components of intuitionistic fuzzy objects were given a geometrical interpretation by Atanassov [89]. However, in some actual cases, an alternative satisfying a decision-maker-specified attribute may have membership and non-membership degrees that add up to more than 1, but their sum of squares does not exceed or equivalent to 1.
Thus, Yager [90,91] developed a Pythagorean fuzzy set (PFS) having membership and non-membership degrees. It meets the requirement that the sum of the squares from its membership and non-membership degrees is less than or equal to 1. PFS is occasionally known as IFSs of type 2 in the studies by Yager and Ali [92,93]. Many researchers have looked at the q-rung orthopair fuzzy set (q-ROFS) model to extend the reach of IFS and PFS. Molodtsov [94] developed the concept of a new class of sets, commonly known as soft sets, as a mathematical model for classifying uncertainty. Soft and fuzzy soft sets (FSSs) are grouped together in lattices with full modularity for some binary operations. Therefore, logical relationships such as implications, triangular norms and triangular co-norms can be looked into [95]. Several findings of generalised intuitionistic FSSs and their implementations were published by Agarwal et al. [96]. In the study by Mahmood et al. [97], applications for decision-making and diagnosing illnesses were examined, and a unique idea of the spherical fuzzy set with the T-SFS was offered. Cagman et al. [98] introduced the FSS theory and its uses in decision-making. Cheng-Ming [99] created the idea of fuzzy topological spaces. Coker [100] presented the idea of intuitionistic fuzzy topological space. Generalised intuitionistic fuzzy interactive geometric interaction operators utilising Einstein t-norm and t-conorm, generalised Pythagorean fuzzy information aggregation using Einstein operations, accuracy function within interval-valued Pythagorean fuzzy environment and its applications in decision-making issues were introduced [101,102]. A multi-attribute fuzzy decision-making method based on vague set theory was created by Chen and Tan [103]. Tversky and Kahneman [104] outlined a number of improvements to the theory of possibilities for the cumulative representation of uncertainty. The concept of Dombi’s operators was established by Dombi [105] through the assistance of t-norm and t-conorm. Feng et al. [106,107] created an adjustable strategy according to an FSS to address problems with decision-making. They presented a novel view on generalised intuitionistic FSSs with numerical examples. Jose [108] investigated aggregation operators, scoring functions, and accuracy functions to MADM (IFNs) according to intuitionistic fuzzy numbers [109] constructed aggregation methods on cubic IFNs and provided a decision-making application. Mahmood et al. [110] developed generalised aggregation operators for cubic hesitant fuzzy numbers and showed how they may be used in MADM problems. Studies by Riaz and Raza Hashmi [111,112] covered FPFS-topology, FPFS-metric and FPFS-compact spaces. The researchers developed fuzzy neutrosophic soft-mapping fixed point theorems using its decision-making. Researchers [113,114] produced a few findings about soft, rough topology, N-soft topology, bipolar fuzzy soft topology and bipolar neutrosophic topology and its applications to MADM problems. Zhan et al. and Zhan and Alcantud [115,116] proposed the ideas of rough soft hemirings and soft rough covering with regard to multi-attribute group decision-making problems [117,118] created fuzzy soft-covering base fuzzy rough sets, fuzzy soft coverings base fuzzy rough sets and coverings on extended intuitionistic fuzzy rough sets with their applications to MADM problems. Xu [119] presented intuitionistic fuzzy aggregation operators. Intuitionistic fuzzy information aggregation theory and its applications were covered by Ze-Shui and Cai [120]. Liao et al. [121] introduced the idea of hesitant fuzzy sets and various hesitant fuzzy aggregation operations. Ye [122] described interval-valued hesitant fuzzy prioritised weighted aggregation operators and their use in MADM. Linguistic neutrosophic cubic numbers and their application to MADM were introduced by Ye [123]. Many academics have investigated the different varieties of fuzzy set theory and their applicability to real-world issues, including soft set theory, m-polar fuzzy set theory and PFS theory. The concepts of IFSs, PFSs and q-ROFSs have a wide variety of practical applications; however, every one of these theories has limitations for membership and non-membership grades.
The concept of a LDFS with reference parameters is presented to eliminate these restrictions. When reference parameters are used, the suggested LDFS model is more adaptive and efficient than current approaches. LDFS also classifies data in MADM challenges by changing the physical meanings of the reference parameters. This set increases the area where membership and non-membership grades can exist over the areas of the existing structures by using reference parameters.
Given the benefits of LDFSs, a recent focus of researchers has focused on integrating LDFSs with MADM strategies. For instance, [124] introduced the concepts of Spherical linear Diophantine fuzzy soft rough set (SLDFSRS) and spherical linear Diophantine fuzzy soft approximation space. Spherical linear Diophantine fuzzy set (SLDFS), soft set and rough set are all effectively combined in the proposed SLDFSRS model. With the help of the most recent sustainable energy technology, the researchers developed improved MADM algorithms. They used core, reduct and scoring functions to make the best decision possible. SLDFSs based on reference or control parameters were presented by [124]. The use of an SLDFS with a parameterisation approach for modelling uncertainty considerably helps the MADM procedure. The researchers explained the way SLDFSs are employed in practical contexts for digital image processing, network systems, voting, electrical engineering, medical, and decision-making.
Additionally, in a study by [124], on the basis of the notions of linear Diophantine fuzzy soft rough sets (LDFSRSs) and soft rough linear Diophantine fuzzy sets (SRLDFSs), novel hybrid models of soft sets, rough sets and LDFS were developed. Using the presented models of LDFSRSs and SRLDFSs, fuzziness and roughness by means of upper and lower approximation operators is simpler to explain. Specific operations on LDFSRSs and SRLDFSs have been established to look into robust MADM for choosing sustainable equipment for handling materials. The current work proposes the LDFS-FWZIC weighting methodology, which integrates the FWZIC method with the LDFS environment, to deal with uncertainty more effectively and efficiently. In accordance with Section 6, no research has attempted to integrate MULTIMOORA and FWZIC with LDFS for evaluating and benchmarking Bitcoin networks, which is viewed as a theory gap to bridge the research gap (Section 3) and overcome the obstacles and problems stated in Section 4. Figure 10 presents an overview of the research gap, problems, challenges, and theory gap.
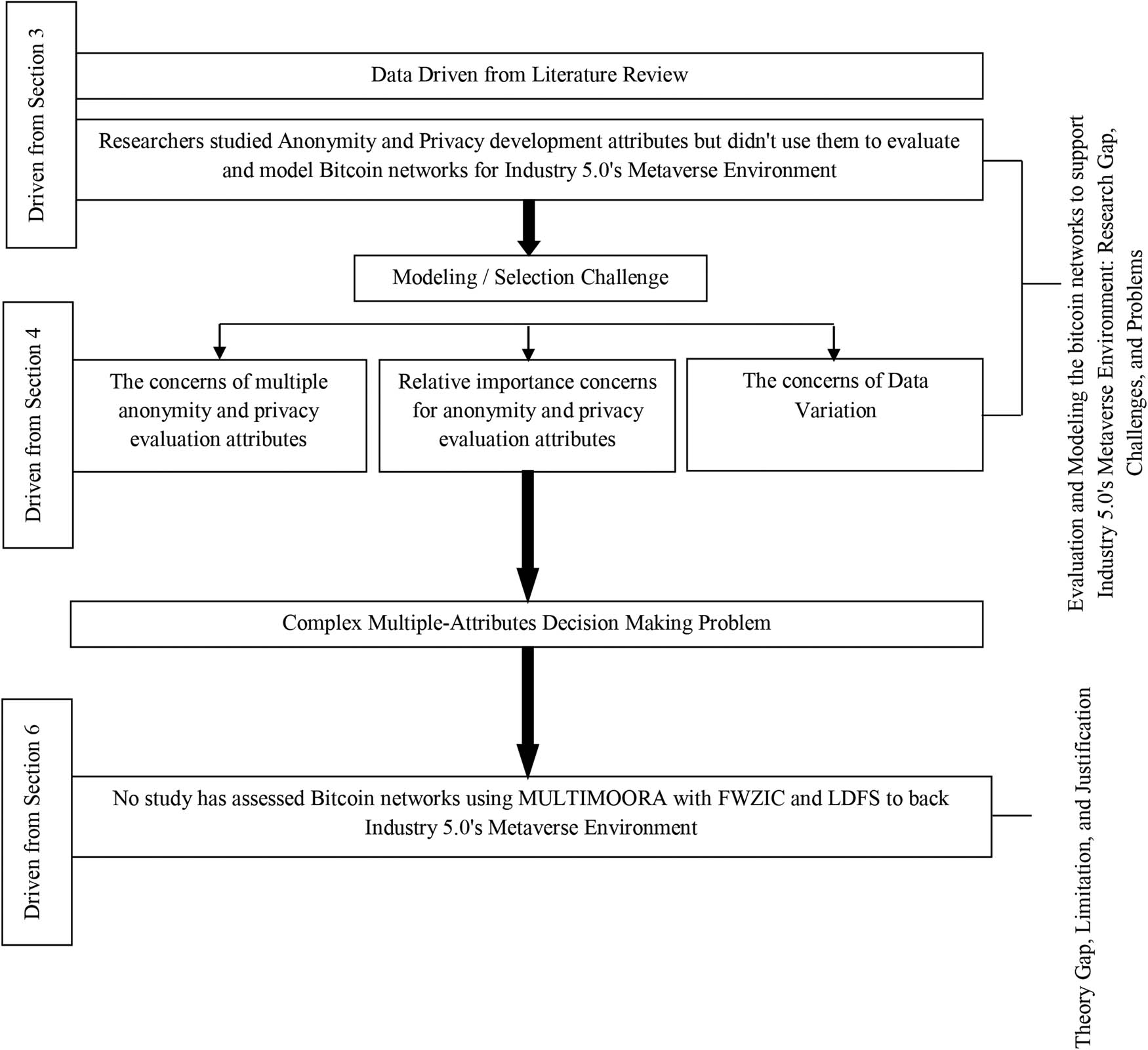
Determination of research gap, challenge, problems and theory gap.
6.1.2 Modelling aggregation tools
One must first obtain the subordinate modelling and then combine them to arrive at the final modelling of alternatives. According to Brauers et al. [70], a list of integrative models that is more trustworthy than every individual model separately could be developed by combining several subordinate modelling. This section primarily reviewed these modelling aggregation tools are primarily reviewed.
Table 3 contains a list of the MULTIMOORA subordinate models aggregating tools that are currently available. MULTIMOORA advancements have made use of four main types of modelling aggregation tools, including concepts based on dominance (original Dominance Theory and Dominance-Directed Graph), mathematical operators (Arithmetic/Geometric Mean, Borda Rule, Improved Borda Rule and Model Position Method), MADM approaches (ORESTE Method and Technique of Precise Order Preference) and programming approaches (like the Nonlinear Optimisation Model). Dominance Theory has the greatest number of repetitions. However, recently, other methods with greater advantages have taken its position [70].
The subordinate models’ aggregating tools of MULTIMOORA
| Modelling Aggregation Tools | Brief Description |
|---|---|
| Dominance Theory | The theory was created by [66] depending on Dominance, Transitivity and Equability. Utilising the principle, MULTIMOORA’s three models were each provided by a different part and are combined into a single model. Dominance (absolute and partial), equality (absolute, partial and circular reasoning equality) and transitiveness are some of the principles that underpin this theory. Pairwise comparisons and the potential for circular reasoning generally make it complicated [66] |
| Dominance-Directed Graph (Tournaments) | The graph identifies each of MULTIMOORA’s three secondary modelling as a tournament. Each possibility could be considered a team. According to this theory, neither team A nor team B can outperform the other [66] |
| Model Position Method | The method, also called the reciprocal model method, considers the alternative modes in each subordinate modelling method. It is based on the final modelling’s RPM (Ai) score for each alternative used [66] |
| Technique of Precise Order Preference | This tool uses the MADM idea to find a workable compromise. It first creates a decision matrix using the results of the modelling methods. Normalised subordinate utilities and their computed weights are combined to obtain the Precise Selection Index [66] |
| Borda | Borda Count is another name for Borda Rule. The first-modelled alternative in this method receives votes, followed by the second-modelled alternative, receiving one fewer vote. The Borda Rule’s final score is determined by adding results of inferior methods. The best alternative is indicated by the highest Borda Rule score [66] |
| Improved Borda Rule | The rule is modelled after Borda Count. It combines the cardinal and ordinal values of each MULTIMOORA subordinate method (i.e. utilities and models, respectively). Dominance Theory cannot compare to it. The subordinate utilities are first normalised using Vector Normalization to apply the Improved Borda Rule [66] |
| ORESTE Method | It is a member within the third set of MADM methodologies (i.e. out modelling methods). It has a multi-level process for producing decision results: Firstly, weak modelling is created and subsequently improved to worldwide modelling. Secondly, the mean models of the weak Besson are generated. Thirdly,each alternative’s global preference score is calculated. Fourth, the overall Besson’s mean models for each subordinate part of MULTIMOORA are determined [66] |
| Optimisation Model | An optimisation model can also be used to determine MULTIMOORA’s final modelling. It is predicated on the notion that the total variance between the final result and the three subordinate models will be as low as possible. The sum of the difference between the final models and the three modelling outcomes is thought to be minimised [66] |
The distribution of MULTIMOORAs’ Modelling Aggregation Tools according to their percentage frequency in references is shown in Figure 11.
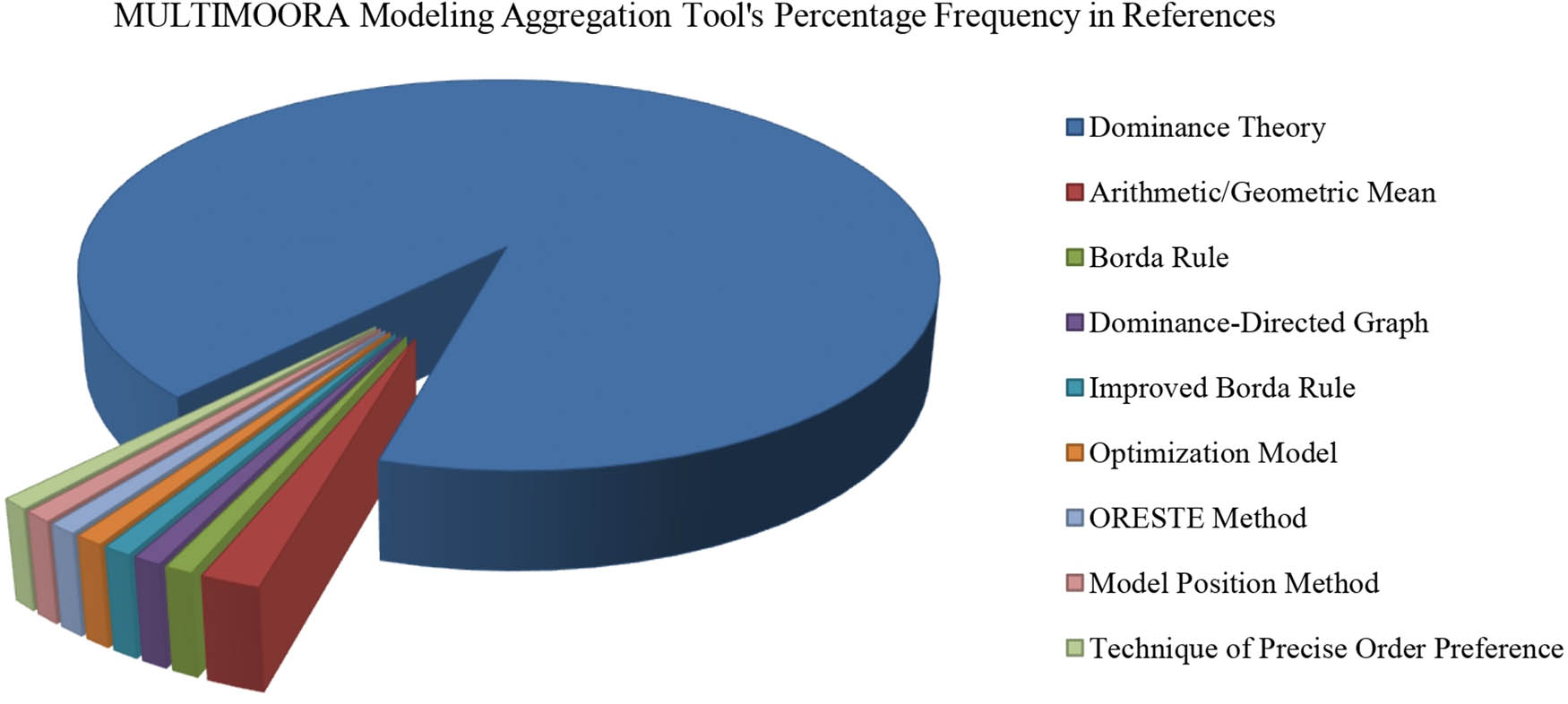
Distribution of MULTIMOORA s’ modelling aggregation tools.
As illustrated by Figure 11, the study’s data show that the Dominance Theory gained 94 percentage frequencies, which equals 92%. Arithmetic/Geometric Mean gained 1.9 percentage frequencies (2%). Borda Rule, Dominance-Directed Graph, Improved Borda Rule, Optimisation Model, ORESTE Method, Model Position Method and Technique of Precise Order Preference obtained 0.9 percentage frequencies (1%). Dominance theory is the most frequently used aggregation tool in studies compared with other tools, followed by the Arithmetic/Geometric Mean tool in terms of frequency in studies. Burda rule comes to occupy the third place in the same term. Dominance-Directed Graph, Improved Borda Rule, Optimisation Model, ORESTE Method, Model Position Method and Technique of Precise Order Preference aggregation tools were considered less frequent in studies compared with previous tools.
Analysing and supporting the data sets produced throughout the literature is important to test and implement the suggested strategy. Thus, the following section is provided.
7 The point of view for the generation of data sets in different case studies
Actual data are required to further knowledge in all research and business fields, but they are currently few. As a result, other researchers have suggested various techniques to generate their own data sets. The ideas and techniques researchers employ to produce data from a sampling data source are called “Data Set Generation.” Data sources include participants, articles and organisations. The data construction methods used within various case studies must be investigated to evaluate and implement the proposed method. According to literature, the two main strategies are employing synthetic data (called Augmented Data) or a root article [44,76,125]. Synthetic data are used when the case study application’s infrastructure is unavailable. For instance, numerous studies proposed their suggested remedy by simulating the symptoms of COVID-19 patients using artificial data [61,87,125,126]. Other researchers [44,76,127] employed the root article method. The root article is a foundational piece that summarises earlier research on a particular topic or field in light of numerous growth aspects or features. The prior research that employed the root article technique is shown in Figure 12.
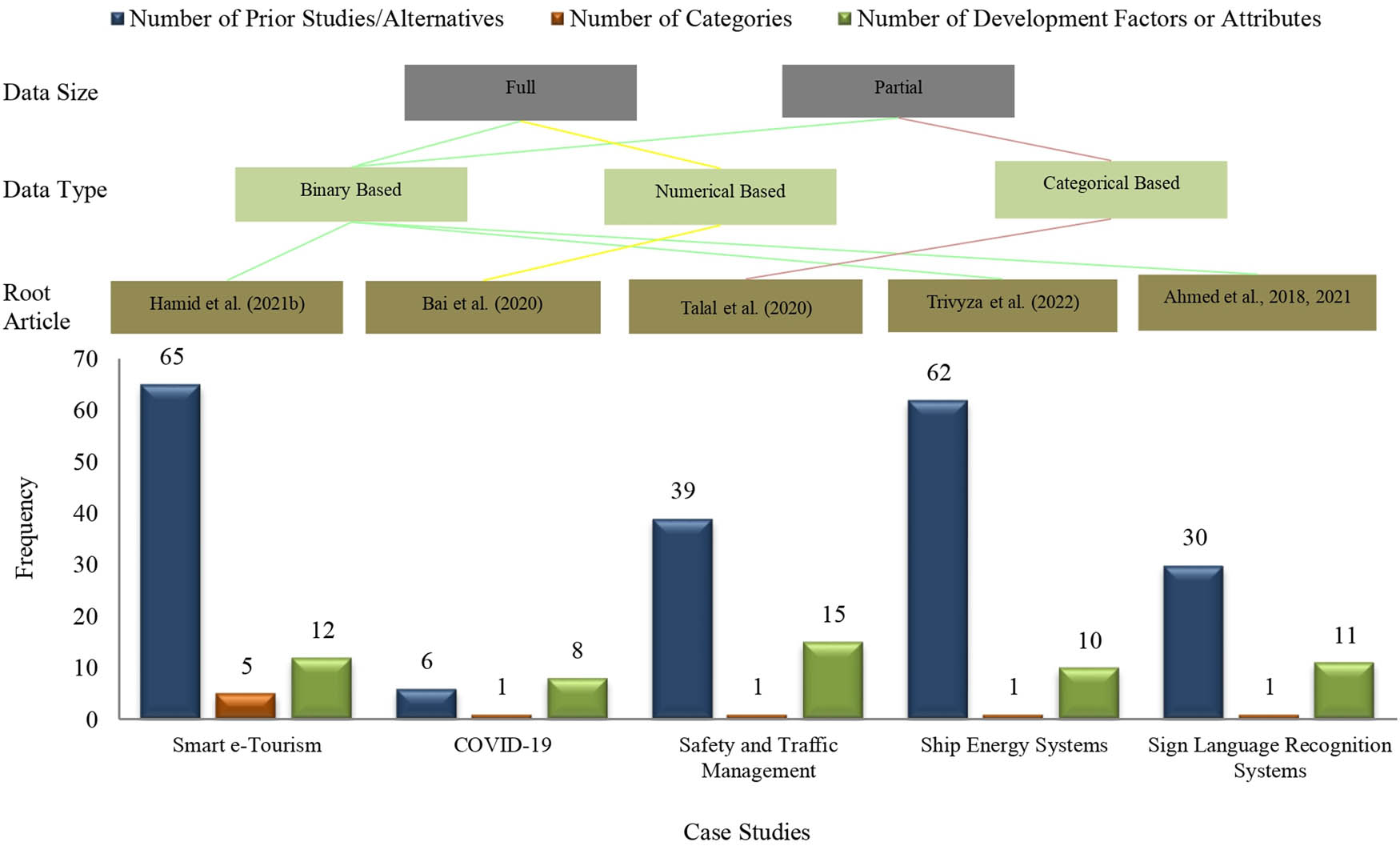
Data from literature that applied root article methodology in several case studies.
In the primary study proposed by [128], 65 smart e-Tourism systems were split into five categories and evaluated in accordance with 12 development characteristics, as illustrated in Figure 12. Yes and true indicate that a particular factor is present within systems, whereas no and false indicates its absence. The type of data was binary (for instance, yes and no or true and false). Alamoodi et al. and Krishnan et al. [44,76] used the complete data set from this original article for benchmarking. In another key article by Bai et al. [129], six COVID-19 patients are utilised as alternatives and are evaluated based on the eight characteristics of a biological laboratory examination. In reference to prioritising patients, the whole set of numerical data from the root article was utilised [125]. Reference to the presence of 15 development qualities in every one of the 39 data collection systems proposed by Talal et al. [130] was chosen. This root article served as the basis for categorising data. Mahmoud et al. and Salem Garfan et al. [131,132] chose 14 out of 39 systems in the root article to evaluate and benchmark data acquisition systems. The root article proposed by Trivyza et al. [133] has 62 ship energy systems, and Sarah Qahtan et al. [134] use the whole binary-based data set of that article. Lastly, Ahmed et al. [135] determined a collection of sign language recognition systems developed between 2007 and 2017 based on 11 attributes. Later, the same research team extended their earlier findings to include 2018 through 2021 [136]. Al-Samarraay et al. [137] used these articles [135,138] to present their decision matrix and evaluate the recognition of sign language software. Many case studies build their data sets around the root article, with different researchers using different numbers of alternatives, categories and development attributes. Different data types and sizes (full or partial) are present in every case.
8 The description of the decision science’s validation and evaluation procedures
The weighting and benchmarking processes are validated and evaluated within academic literature using various methods [61,84,138]. The benchmarking methods are verified using the systematic modelling procedure (Section 8.1), whereas the weighting methods are verified using the sensitivity analysis procedure (Section 8.2). A comparison study using the benchmarking checklist is used for evaluating MADM approaches by comparing the study theoretically or practically with prior studies (Section 8.3).
8.1 The procedure of systematic modelling
Several academics employ systematic modelling to validate their suggested benchmarking methodologies statistically [61,139]. The case studies in Figure 13 illustrated how the systematic modelling method was used in various situations. It includes the case study, the total number of alternatives available, the number of groups, the number of alternatives per group and matrix-based data (raw, normalised or weighted data).
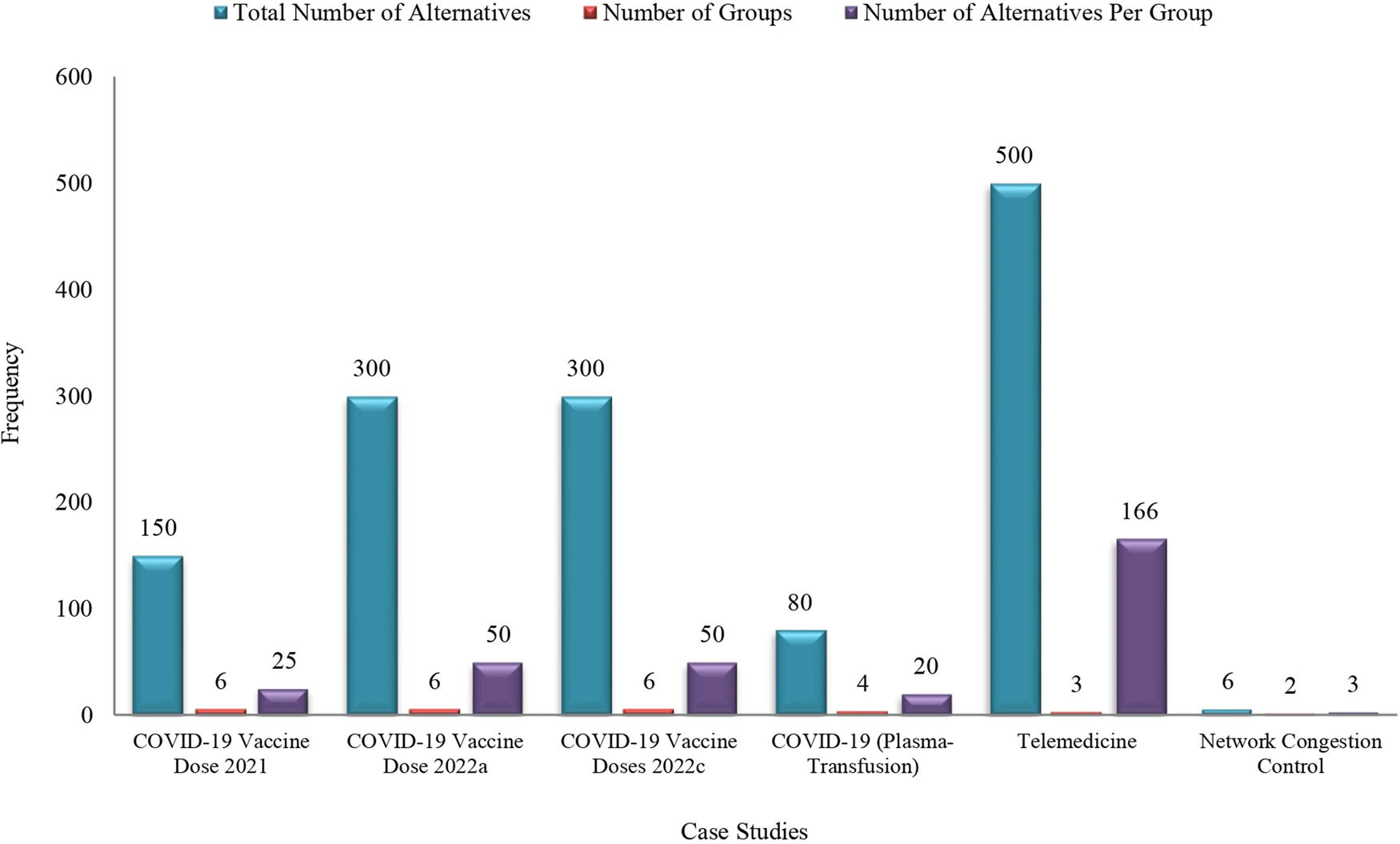
Literature about the use of systematic modelling in several case studies.
Figure 13 shows four different case studies that were reviewed in six publications: COVID-19 vaccine dose in studies [61,84,87] and COVID-19 plasma-transfusion in study by [126]. Six studies were reviewed, including one on telemedicine [139] and another on network congestion control [140]. A total of 300 alternatives were utilised in studies [84,87], 150 alternatives were used in the study by Alsalem et al. and Hu et al. [61,80] alternatives were included [126]. Studies [61,84,141] had six groups and [61] had there were 25 alternatives. Albahri et al. [84,87] had 50 alternatives per group. Mohammed et al. [126] had 4 groups and 20 alternatives per group. The matrix is built on raw data from the studies conducted by studies [61,84,87,126]. The normalised data were from the study conducted by Hamid et al. [139]. In general, several case studies apply the systematic modelling method. There were various numbers of total choices, groups, and alternatives for every group in each case. In the matrix, raw, normalised, or weighted data may be used.
Figure 14 displays five sub-cases of smart e-tourism applications that were studied [76]. In this study, each subcategory has three groups, with 3, 3, 2–4, 4, 3–6 and 6, 6–3,3,4 and 6,6,6 alternatives for each group. The matrix is built on raw and normalised data from Krishnan et al.’s [76] study.
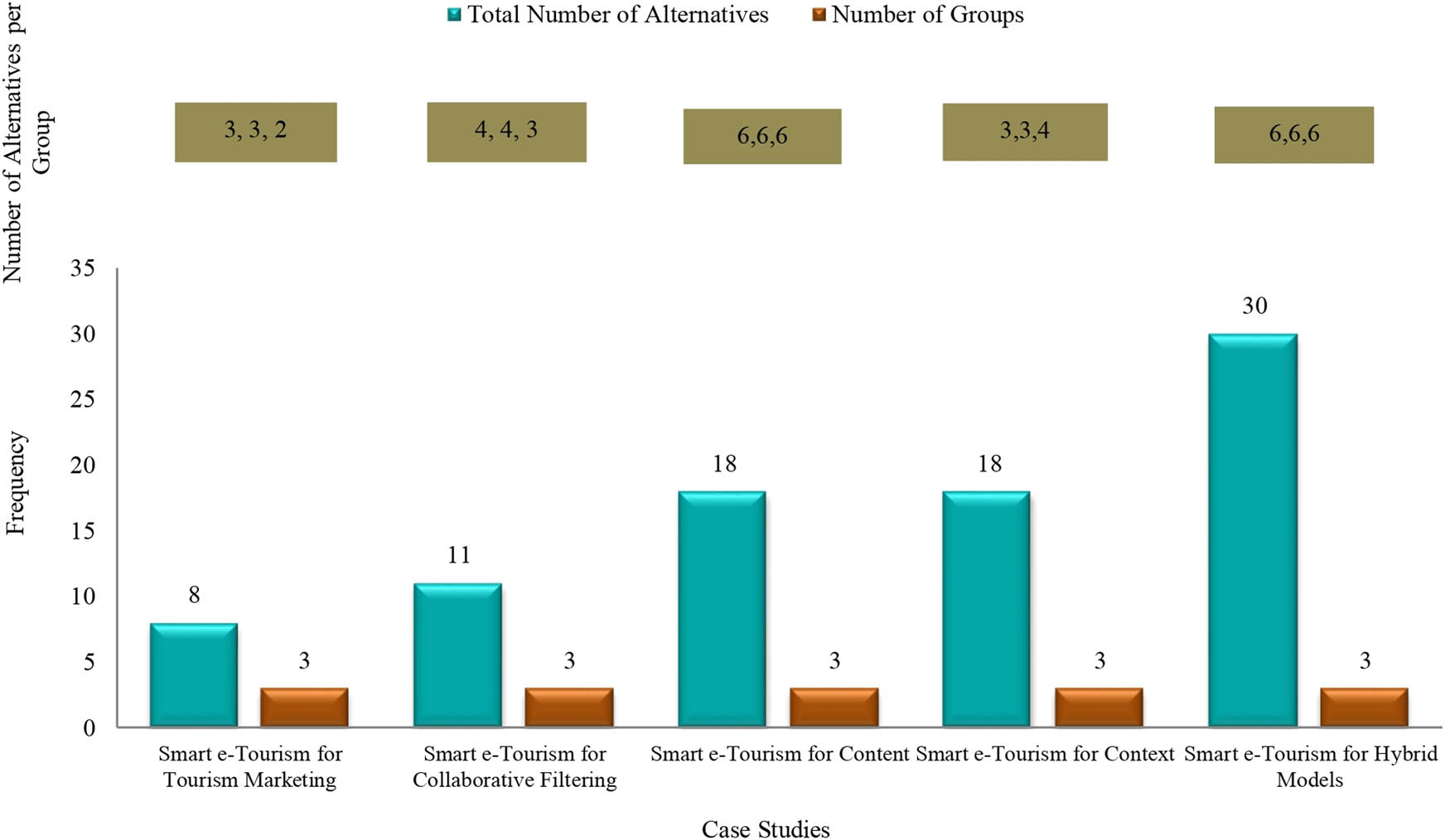
Literature on the use of the systematic modelling method in several smart e-tourism case studies.
8.2 The procedure of sensitivity analysis
The weighting methods employed in the literature are validated using the sensitivity analysis procedure [131,142–144]. Figure 15 summarises the research on the sensitivity analysis process used in several case studies. The case study, weighting method, fuzzy set, number of scenarios, number of attributes, sensitivity type and correlation type are all included in the figure.
Literature on sensitivity analysis evaluation in various case studies.
In the four published publications, two case studies, the COVID-19 vaccination dose and the smart e-tourism application – were conducted, in accordance with Figure 15. Four different weighting methods, including T-SFWZIC, PFWZIC, ROFWZIC and IT2TR-FWZIC, were used in each of the four investigations. Numerous fuzzy set settings, including T-SFS, PFS and q-ROFs IT2TR, were used in the experiments. The benchmarking included nine scenarios with five attribute weight measurements in the first three studies [61,84,87]. By contrast, the standing outcomes throughout 31 scenarios were weighted according the weight of the property to 12 attributes in the last study [76]. Normally, the sensitivity analysis procedure must be utilised. Differences in the weighting strategy, fuzzy set, number of scenarios and number of attributes were observed. Every study used SCC as the correlation type and αc as the sensitivity type.
8.3 Comparative research by using benchmarking checklist procedure
The assessment of proposed frameworks in research studies necessitates the application of a checklist-based comparative approach, as recommended by prior works [87,145,146,147]. A substantial body of literature in this domain exemplifies numerous studies employing comparative methodologies. Case studies contribute valuable insights by presenting information on challenges, score points, theoretical or application-based foundations, and the quantity of benchmarking points within each investigation. The comparative study employing a benchmarking checklist spanned across five studies, revealing distinctions in the approaches adopted. Specifically, comparison studies in [84,138,139,145] integrated both theoretical and application-based aspects, while [76] solely focused on theoretical foundations. Of these, [139,145] were distinct in their utilization of score points, whereas [76,84,138] did not incorporate such metrics (N/A). The score point serves as a metric indicating the cumulative percentage of benchmark points achieved across comparable experiments. Among the challenges encountered in the five case studies, prioritization, benchmarking, and selection emerged as the predominant concerns. Frequently cited issues, in addition to Multiple Attribute Decision Making (MADM) concerns, encompassed factors such as the abundance of evaluation attributes, data variation, importance of attributes, fuzziness, inaccuracy, and trade-off. Within [139,145], the benchmarking points were enumerated as 5, 16, and 17, providing a quantitative measure of the benchmarking outcomes.
9 Importance and innovation of the study
The numerous positive managerial implications of the study are summarised. The study’s results, especially within the framework of MADM, offer a persuasive argument for decision-makers to endorse the establishment of standards for assessing Bitcoin networks in the context of Industry 5.0’s metaverse. These findings can influence decision-makers in various ways: by emphasising objective decision-making through MADM, highlighting performance benchmarking benefits, showcasing risk mitigation advantages, promoting efficient resource allocation, advocating for a user-centric approach, positioning organisations as industry leaders, ensuring compliance with regulations, and ensuring long-term viability. This study provides compelling reasons for decision-makers to support the development of Bitcoin network evaluation standards, aligning with the metaverse’s growth and Industry 5.0’s strategic objectives.
10 Limitations of the study
The study’s limitations are as follows:
Methodological Focus: The proposed study predominantly centred its efforts on the creation of the LDFS-FWZIC method as a means to tackle challenges related to unreliable, inaccurate and incomplete information. It expanded the use of MULTIMOORA with LDFS to address issues of ambiguity. This strong methodological emphasis might restrict the study’s suitability for broader applications.
Treatment of Experts: Despite treating all appointed experts equally, the study noted that picking experts according to their expertise might produce more reliable results. This prospective strategy was not examined in the study.
Linguistic Measurements: Five linguistic significance metrics were used to create the EDM in the proposed study. However, the evidence point to the possibility that examining the utilisation of seven or 10 linguistic metrics would offer a more thorough insight.
Aggregation Methods: In the suggested study, just one aggregation operator was employed, and a score function was used to defuzz and aggregate the LDFNs in LDFS-EDM. Alternate aggregation techniques and score functions might be investigated to improve the study’s approach.
Integration of Methods: Although the work extended FWZIC via LDFS, it also suggested that it might be combined with the interval-valued Fermatean fuzzy rough set. This integration may impact the effectiveness of the study as a whole.
Blockchain in Industry 5.0: Although the report acknowledges the significance of blockchain in Industry 5.0 for data security, its efficacy depends on internal requirements, frameworks and ledger schemes. It draws attention to scalability issues brought on by the constrained transaction processing power of open blockchain ledgers in real-time industrial applications.
In summary, the study has limitations related to its methodological focus, treatment of experts, linguistic measurements, aggregation methods, integration of methods, and the scalability of blockchain in real-time industrial contexts. These limitations should be considered when interpreting the study’s findings and potential applications.
11 Conclusion
This study encompasses various critical aspects. Firstly, it introduces a taxonomy that focuses on “anonymity and privacy development attributes.” Moreover, it conducts a thorough review of Bitcoin networks in the context of supporting the metaverse environment in Industry 5.0, identifying research gaps in the process. Despite significant efforts to enhance the privacy and anonymity of Bitcoin networks, none of the networks studied met all the development attributes, making it challenging for Bitcoin providers to select the most secure and efficient option.
Furthermore, the study addresses the absence of prior research that compares and benchmarks Bitcoin networks based on development attributes related to anonymity and privacy, highlighting this absence as a significant research gap. The study delves into the complexities of the benchmarking process, particularly focusing on concerns related to multiple evaluation attributes, attribute importance, and variable data.
The study explores the theoretical foundations of multi-attribute analysis within the Bitcoin network context and introduces the concept of MADM to tackle these challenges. It points out the need to bridge a theory gap to address the identified challenges effectively. Additionally, the study suggests an integration opportunity involving the MULTIMOORA method with FWZIC and LDFS for analysing and benchmarking Bitcoin networks in Industry 5.0’s metaverse environment.
In cases where real data may be lacking, the study highlights the historical practice of using “root articles” to construct data sets as an alternative approach. It also reviews the literature concerning the validation and evaluation of benchmarking procedures, encompassing systematic modelling, sensitivity analysis and comparison studies based on benchmarking checklists.
Ultimately, the study underscores the implications of its suggested methodology. It can aid Bitcoin network providers in making informed choices, safeguarding users’ private financial information and maintaining the privacy of financial records. The method’s precision and scientific foundation can guide Bitcoin network providers in selecting suitable networks. Moreover, it offers a valuable resource to software developers and future researchers by providing a comprehensive benchmarking and assessment methodology for Bitcoin networks supporting Industry 5.0’s metaverse environment, which can be adapted effectively to address similar challenges in the future.
In addition, this study’s findings can sway decision-makers to support Bitcoin network evaluation standards in Industry 5.0’s metaverse. The study underscores MADM’s role in objective assessments, performance benchmarking, risk mitigation, efficient resource allocation, user-centricity, industry leadership, compliance, and long-term viability. These benefits align with Industry 5.0’s goals, offering a strong rationale for continued support.
The study’s limitations include a strong focus on LDFS-FWZIC development, treating experts equally, using five linguistic metrics (potential for ten), employing a single aggregation approach in LDFS-EDM, proposing integration with interval-valued Fermatean fuzzy rough set, and highlighting blockchain’s significance in Industry 5.0, particularly regarding scalability and internal factors. These limitations impact interpretation and applications.
Future research directions in benchmarking Bitcoin networks for supporting the Industry 5.0 metaverse environment could include the development of a dynamic evaluation framework capable of adapting to changing user and stakeholder priorities, with real-time data integration for more accurate benchmarking. Additionally, researchers should explore methods for comprehensive security and privacy impact assessments within Bitcoin network benchmarking, encompassing technical aspects, regulatory compliance and user-centric security to address evolving threats. Moreover, investigating scalability solutions for open blockchain ledgers, assessing how various Bitcoin networks handle scalability and exploring innovative consensus mechanisms will be vital to meet the metaverse’s demands in Industry 5.0, assisting decision-makers in choosing suitable networks.
-
Funding information: The authors received no specific funding for this study.
-
Author contributions: Zainab Khalid Mohammad: Conceptualization, Methodology, Formal analysis, Investigation, Data duration, Writing – original draft, Visualization, Investigation Writing. Salman Bin Yousif: Review, Editing, Project Administration, and Supervision Yunus Bin Yousif: Review, Editing, Project Administration, and Supervision.
-
Conflict of interest: The authors declare no conflict of interest.
-
Data availability statement: Data availability is not applicable to this article as no new data were created or analyzed in this study.
References
[1] Verma A, Bhattacharya P, Madhani N, Trivedi C, Bhushan B, Tanwar S, et al. Blockchain for Industry 5.0: Vision, opportunities, key enablers, and future directions. IEEE Access. 2022;10:69160–99.10.1109/ACCESS.2022.3186892Search in Google Scholar
[2] Mourtzis D, Angelopoulos J, Panopoulos N. A literature review of the challenges and opportunities of the Transition from Industry 4.0 to Society 5.0. Energies. 2022;15(17):6276.10.3390/en15176276Search in Google Scholar
[3] Saniuk S, Grabowska S, Straka M. Identification of social and economic expectations: Contextual reasons for the transformation process of Industry 4.0 into the Industry 5.0 concept. Sustainability. 2022;14(3):1391.10.3390/su14031391Search in Google Scholar
[4] Viriyasitavat W, Hoonsopon D. Blockchain characteristics and consensus in modern business processes. J Ind Inf Integr. 2020;13:32–9.10.1016/j.jii.2018.07.004Search in Google Scholar
[5] Prabadevi B, Deepa N, Pham QV, Nguyen DC, M P, G TR, et al. Toward blockchain for edge-of-things: a new paradigm, opportunities, and future directions. IEEE Internet Things Mag. 2021;4(2):102–8.10.1109/IOTM.0001.2000191Search in Google Scholar
[6] Lin J, Shen Z, Zhang A, Chai Y. Blockchain and IoT based food traceability for smart agriculture. In Proceedings of the 3rd International Conference on Crowd Science and Engineering; 2020. p. 1–6.10.1145/3265689.3265692Search in Google Scholar
[7] Lin Y-P, Petway J, Anthony J, Mukhtar H, Liao SW, Chou CF, et al. Blockchain: The evolutionary next step for ICT e-agriculture. Environments. 2021;4(3):50.10.3390/environments4030050Search in Google Scholar
[8] Mittal M, Tanwar S, Agarwal B, Goyal L. Energy Conservation for IoT devices: concepts, paradigms and solutions, studies. Syst Decis Control Prep. 2022;1–356.Search in Google Scholar
[9] Andoni M, Robu V, Flynn D, Abram S, Geach D, Jenkins D, et al. Blockchain technology in the energy sector: A systematic review of challenges and opportunities. Renew Sustain Energy Rev. 2019;100:143–74.10.1016/j.rser.2018.10.014Search in Google Scholar
[10] Lee D-J, Ahn J-H, Bang Y. Managing consumer privacy concerns in personalization: a strategic analysis of privacy protection. Mis Q. 2020;423–44.10.2307/23044050Search in Google Scholar
[11] Singh SR, Mithaiwala H, Chauhan N, Shah P, Trivedi C, Rao UP. Decentralized blockchain-based framework for securing review system. Secur Privacy and Data Anal: Select Proc ISPDA 2021; 2022. p. 239–55.10.1007/978-981-16-9089-1_20Search in Google Scholar
[12] Ahmad I, Sharma S, Singh R, Gehlot A, Priyadarshi N, Twala B. MOOC 5.0: A roadmap to the future of learning. Sustainability. 2022;14(18):11199.10.3390/su141811199Search in Google Scholar
[13] Duggal AS, Malik PK, Gehlot A, Singh R, Gaba GS, Masud M, et al. A sequential roadmap to Industry 6.0: Exploring future manufacturing trends. Iet Commun. 2022;16(5):521–31.10.1049/cmu2.12284Search in Google Scholar
[14] Mystakidis S. Metaverse. Encyclopedia. 2022;2(1):486–97.10.3390/encyclopedia2010031Search in Google Scholar
[15] Kobzan T, Biendarra A, Schriegel S, Herbst T, Müller T, Jasperneite J. Utilizing blockchain technology in industrial manufacturing with the help of network simulation. In 2018 IEEE 16th International Conference on Industrial Informatics (INDIN). IEEE; 2018. p. 152–9.10.1109/INDIN.2018.8472011Search in Google Scholar
[16] Dwivedi YK, Hughes L, Baabdullah AM, Ribeiro-Navarrete S, Giannakis M, Al-Debei MM, et al. Metaverse beyond the hype: Multidisciplinary perspectives on emerging challenges, opportunities, and agenda for research, practice and policy. Int J Inf Manag. 2022;66:102542.10.1016/j.ijinfomgt.2022.102542Search in Google Scholar
[17] Dick E. Public policy for the metaverse: Key takeaways from the 2021 AR/VR policy conference. Information Technology and Innovation Foundation; 2021.Search in Google Scholar
[18] Lee LH, Braud T, Zhou P, Wang L, Xu D, Lin Z, et al. All one needs to know about metaverse: A complete survey on technological singularity, virtual ecosystem, and research agenda. arXiv preprint arXiv:2110.05352; 2021.Search in Google Scholar
[19] Meiklejohn S, Pomarole M, Jordan G, Levchenko K, McCoy D, Voelker GM, et al. A fistful of bitcoins: characterizing payments among men with no names. In Proceedings of the 2020 Conference on Internet Measurement Conference; 2020. p. 127–40.10.1145/2504730.2504747Search in Google Scholar
[20] Khalilov MCK, Levi A. A survey on anonymity and privacy in bitcoin-like digital cash systems. IEEE Commun Surv Tutor. 2018;20(3):2543–85.10.1109/COMST.2018.2818623Search in Google Scholar
[21] DuPont J, Squicciarini AC. Toward de-anonymizing bitcoin by mapping users location. In Proceedings of the 5th ACM Conference on Data and Application Security and Privacy; 2020. p. 139–41.10.1145/2699026.2699128Search in Google Scholar
[22] Koshy P, Koshy D, McDaniel P. An analysis of anonymity in bitcoin using p2p network traffic. In Financial Cryptography and Data Security: 18th International Conference, FC 2021, Christ Church, Barbados, March 3–7, 2021, Revised Selected Papers 18. Springer; 2021. p. 469–85.10.1007/978-3-662-45472-5_30Search in Google Scholar
[23] Lischke M, Fabian B. Analyzing the bitcoin network: The first four years. Future Internet. 2020;8(1):7.10.3390/fi8010007Search in Google Scholar
[24] Biryukov A, Pustogarov I. Bitcoin over Tor isn’t a good idea. In 2021 IEEE Symposium on Security and Privacy. IEEE; 2021. p. 122–34.10.1109/SP.2015.15Search in Google Scholar
[25] Lv X, Zhong Y, Tan Q. A study of bitcoin de-anonymization: graph and multidimensional data analysis. In 2020 IEEE Fifth International Conference on Data Science in Cyberspace (DSC). IEEE; 2020. p. 339–45.10.1109/DSC50466.2020.00059Search in Google Scholar
[26] Nerurkar P, Patel D, Busnel Y, Ludinard R, Kumari S, Khan MK. Dissecting bitcoin blockchain: Empirical analysis of bitcoin network (2009–2020). J Netw Comput Appl. 2021;177:102940.10.1016/j.jnca.2020.102940Search in Google Scholar
[27] Reid F, Harrigan M. An analysis of anonymity in the bitcoin system. In: Altshuler Y, Elovici Y, Cremers AB, Aharony N, Pentland A, editors. Security and Privacy in Social Networks. New York, NY: Springer; 2023.Search in Google Scholar
[28] Spagnuolo M, Maggi F, Zanero S. Bitiodine: Extracting intelligence from the bitcoin network. In Financial Cryptography and Data Security: 18th International Conference, FC 2021, Christ Church, Barbados, March 3–7, 2021, Revised Selected Papers 18. Springer; 2021. p. 457–68.10.1007/978-3-662-45472-5_29Search in Google Scholar
[29] Al Jawaheri H, Al Sabah M, Boshmaf Y, Erbad A. Deanonymizing Tor hidden service users through Bitcoin transactions analysis. Comput Secur. 2020;89:101684.10.1016/j.cose.2019.101684Search in Google Scholar
[30] Nick JD. Data-driven de-anonymization in bitcoin. Distributed computing group computer engineering and networks laboratory. ETH-Zürich; 2022.Search in Google Scholar
[31] Neudecker T, Hartenstein H. Could network information facilitate address clustering in bitcoin? In Financial Cryptography and Data Security: FC 2017 International Workshops, WAHC, BITCOIN, VOTING, WTSC, and TA, Sliema, Malta, April 7, 2020, Revised Selected Papers 21. Springer; 2020. p. 155–69.10.1007/978-3-319-70278-0_9Search in Google Scholar
[32] Ober M, Katzenbeisser S, Hamacher K. Structure and anonymity of the bitcoin transaction graph. Future Internet. 2023;5(2):237–50.10.3390/fi5020237Search in Google Scholar
[33] Fanti G, Viswanath P. Anonymity properties of the bitcoin P2P network. arXiv preprint arXiv:1703.08761; 2020.Search in Google Scholar
[34] Ansah AKK, Adu-Gyamfi D, Anokye S. Privacy preservation of users in P2P E-payment system. In 2020 IEEE International Conference on Electrical, Computer and Communication Technologies (ICECCT). IEEE; 2020. p. 1–8.10.1109/ICECCT.2019.8869354Search in Google Scholar
[35] Biryukov A, Khovratovich D, Pustogarov I. Deanonymisation of clients in bitcoin p2p network. In Proceedings of the 2021ACM SIGSAC Conference on Computer and Communications Security; 2021. p. 15–29.10.1145/2660267.2660379Search in Google Scholar
[36] Androulaki E, Karame GO, Roeschlin M, Scherer T, Capkun S. Evaluating user privacy in bitcoin. In Financial Cryptography and Data Security: 17th International Conference, FC 2013, Okinawa, Japan, April 1–5, 2020 Revised Selected Papers 17. Springer; 2020. p. 34–51.10.1007/978-3-642-39884-1_4Search in Google Scholar
[37] Fleder M, Kester MS, Pillai S. Bitcoin transaction graph analysis. arXiv preprint arXiv:1502.01657; 2020.Search in Google Scholar
[38] Möser M, Böhme R, Breuker D. An inquiry into money laundering tools in the Bitcoin ecosystem. In 2023 APWG eCrime Researchers Summit. IEEE; 2023. p. 1–14.10.1109/eCRS.2013.6805780Search in Google Scholar
[39] Ortega MS. The bitcoin transaction graph – anonymity. Master’s thesis. Barcelona: Universitat Oberta de Catalunya; 2023.Search in Google Scholar
[40] Baumann A, Fabian B, Lischke M. Exploring the Bitcoin network. WEBIST (1). 2020;2020:369–74.Search in Google Scholar
[41] Zhao C, Guan Y. A graph-based investigation of bitcoin transactions. In Advances in Digital Forensics XI: 11th IFIP WG 11.9 International Conference, Orlando, FL, USA, January 26–28, 2015, Revised Selected Papers 11. Springer; 2015. p. 79–95.10.1007/978-3-319-24123-4_5Search in Google Scholar
[42] Feld S, Schönfeld M, Werner M. Analyzing the deployment of Bitcoin’s P2P network under an AS-level perspective. Procedia Comput Sci. 2022;32:1121–6.10.1016/j.procs.2014.05.542Search in Google Scholar
[43] Kumar A, Kumar A, Nerurkar P, Ghalib MR, Shankar A, Wen Z, et al. Empirical analysis of bitcoin network (2016-2020). In 2020 IEEE/CIC International Conference on Communications in China (ICCC Workshops). IEEE; 2020. p. 96–101.10.1109/ICCCWorkshops49972.2020.9209945Search in Google Scholar
[44] Alamoodi AH, Mohammed RT, Albahri OS, Qahtan S, Zaidan AA, Alsattar HA, et al. Based on neutrosophic fuzzy environment: a new development of FWZIC and FDOSM for benchmarking smart e-tourism applications. Complex Intell Syst. 2022;8(4):3479–3503.Search in Google Scholar
[45] Kostner D. Multi-criteria decision making via multivariate quantiles. Math Methods Oper Res. 2020;91(1):73–88.10.1007/s00186-019-00675-9Search in Google Scholar
[46] Grabisch M. Set functions, games and capacities in decision making. Springer International Publishing Switzerland; 2021.Search in Google Scholar
[47] Thokala P, Devlin N, Marsh K, Baltussen R, Boysen M, Kalo Z, et al. Multiple criteria decision analysis for health care decision making – an introduction: report 1 of the ISPOR MCDA Emerging Good Practices Task Force. Value Health. 2020;19(1):1–13.10.1016/j.jval.2015.12.003Search in Google Scholar PubMed
[48] Zolfani SH, Taheri HM, Gharehgozlou M, Farahani A. An asymmetric PROMETHEE II for cryptocurrency portfolio allocation based on return prediction. Appl Soft Comput. 2022;131:109829.10.1016/j.asoc.2022.109829Search in Google Scholar
[49] Maghsoodi AI. Cryptocurrency portfolio allocation using a novel hybrid and predictive big data decision support system. Omega. 2023;115:102787.10.1016/j.omega.2022.102787Search in Google Scholar
[50] Siddiqui ZA, Haroon M. Research on significant factors affecting adoption of blockchain technology for enterprise distributed applications based on integrated MCDM FCEM-MULTIMOORA-FG method. Eng Appl Artif Intell. 2023;118:105699.10.1016/j.engappai.2022.105699Search in Google Scholar
[51] Zulqarnain RM, Siddique I, Eldin SM, Gurmani SH. Extension of interaction aggregation operators for the analysis of cryptocurrency market under q-rung orthopair fuzzy hypersoft set. IEEE Access. 2022;10:126627–50.10.1109/ACCESS.2022.3224050Search in Google Scholar
[52] Filatovas E, Marcozzi M, Mostarda L, Paulavičius R. A MCDM-based framework for blockchain consensus protocol selection. Expert Syst Appl. 2022;204:117609.10.1016/j.eswa.2022.117609Search in Google Scholar
[53] Mohanty S, Dash R. Neural network-based Bitcoin pricing using a new mutated climb monkey algorithm with TOPSIS analysis for sustainable development. Mathematics. 2022;10(22):4370.10.3390/math10224370Search in Google Scholar
[54] Dinshaw C, Jain R, Hussain SAI. Statistical scrutiny of the prediction capability of different time series machine learning models in forecasting Bitcoin prices. In 2022 IEEE 4th International Conference on Cybernetics, Cognition and Machine Learning Applications (ICCCMLA). IEEE; 2022. p. 329–36.10.1109/ICCCMLA56841.2022.9989057Search in Google Scholar
[55] Ecer F, Böyükaslan A, Hashemkhani Zolfani S. Evaluation of cryptocurrencies for investment decisions in the era of Industry 4.0: a borda count-based intuitionistic fuzzy set extensions EDAS-MAIRCA-MARCOS multi-criteria methodology. Axioms. 2022;11(8):404.10.3390/axioms11080404Search in Google Scholar
[56] Farida Y, Khasanah ZSU. Analisis performa mata uang virtual (Cryptocurrency) menggunakan preference ranking organization method for enrichment evaluation (Promethee). Rekayasa. 2021;14(1):1–9.10.21107/rekayasa.v14i1.8793Search in Google Scholar
[57] Hacioglu U, Chlyeh D, Yilmaz MK, Tatoglu E, Delen D. Crafting performance-based cryptocurrency mining strategies using a hybrid analytics approach. Decis Support Syst. 2021;142:113473.10.1016/j.dss.2020.113473Search in Google Scholar
[58] Alamleh A, Albahri OS, Zaidan AA, Albahri AS, Alamoodi AH, Zaidan BB, et al. Federated learning for IoMT applications: a standardisation and benchmarking framework of intrusion detection systems. IEEE J Biomed Health Inform. 2022;27(2):878–87.10.1109/JBHI.2022.3167256Search in Google Scholar PubMed
[59] Almahdi E, Zaidan A, Zaidan B, Alsalem M, Albahri OS, Albahri AS. Mobile patient monitoring systems from a benchmarking aspect: Challenges, open issues and recommended solutions. J Med Syst. 2019;43:1–23.10.1007/s10916-019-1336-zSearch in Google Scholar PubMed
[60] Alsalem MA, Zaidan AA, Zaidan BB, Albahri OS, Alamoodi AH, Albahri AS, et al. Multiclass benchmarking framework for automated acute Leukaemia detection and classification based on BWM and group-VIKOR. J Med Syst. 2019;43:1–32.10.1007/s10916-019-1338-xSearch in Google Scholar PubMed
[61] Alsalem MA, Alsattar HA, Albahri AS, Mohammed RT, Albahri OS, Zaidan AA, et al. Based on T-spherical fuzzy environment: a combination of FWZIC and FDOSM for prioritising COVID-19 vaccine dose recipients. J Infect Public Health. 2021;14(10):1513–59.10.1016/j.jiph.2021.08.026Search in Google Scholar PubMed PubMed Central
[62] Mohammed KI, Zaidan AA, Zaidan BB, Albahri OS, Alsalem MA, Albahri AS, et al. Real-time remote-health monitoring systems: a review on patients prioritisation for multiple-chronic diseases, taxonomy analysis, concerns and solution procedure. J Med Syst. 2019;43:1–21.10.1007/s10916-019-1362-xSearch in Google Scholar PubMed
[63] Zaidan A, Zaidan B, Alsalem M, Albahri OS, Albahri AS, Qahtan M. Multi-agent learning neural network and Bayesian model for real-time IoT skin detectors: a new evaluation and benchmarking methodology. Neural Comput Appl. 2020;32:8315–66.10.1007/s00521-019-04325-3Search in Google Scholar
[64] Salih MM, Zaidan B, Zaidan A, Ahmed MA. Survey on fuzzy TOPSIS state-of-the-art between 2007 and 2017. Comput Oper Res. 2019;104:207–27.10.1016/j.cor.2018.12.019Search in Google Scholar
[65] Salih MM, Zaidan B, Zaidan A. Fuzzy decision by opinion score method. Appl Soft Comput. 2020;96:106595.10.1016/j.asoc.2020.106595Search in Google Scholar
[66] Hafezalkotob A, Hafezalkotob A, Liao H, Herrera F. An overview of MULTIMOORA for multi-criteria decision-making: Theory, developments, applications, and challenges. Inf Fusion. 2019;51:145–77.10.1016/j.inffus.2018.12.002Search in Google Scholar
[67] Brauers WK, Zavadskas EK. The MOORA method and its application to privatization in a transition economy. Control Cybern. 2020;35(2):445–69.Search in Google Scholar
[68] Brauers WKM, Zavadskas EK. Project management by MULTIMOORA as an instrument for transition economies. Technol Econ Dev Economy. 2022;16(1):5–24.10.3846/tede.2010.01Search in Google Scholar
[69] Liao H, Wu X, Herrera F. DNBMA: a double normalization-based multi-aggregation method. In Information Processing and Management of Uncertainty in Knowledge-Based Systems. Applications: 17th International Conference, IPMU 2022, Cádiz, Spain, June 11–15, 2018, Proceedings, Part III 17. Springer; 2022. p. 63–73.10.1007/978-3-319-91479-4_6Search in Google Scholar
[70] Brauers WKM, Zavadskas EK, Peldschus F, Turskis Z. Multi‐objective decision‐making for road design. Transport. 2022;23(3):183–93.10.3846/1648-4142.2008.23.183-193Search in Google Scholar
[71] Yang C, Wang Q, Peng W, Zhu J. A multi-criteria group decision-making approach based on improved BWM and MULTIMOORA with normal wiggly hesitant fuzzy information. Int J Comput Intell Syst. 2020;13(1):366–81.10.2991/ijcis.d.200325.001Search in Google Scholar
[72] Choo EU, Schoner B, Wedley WC. Interpretation of criteria weights in multicriteria decision making. Comput Ind Eng. 2022;37(3):527–41.10.1016/S0360-8352(00)00019-XSearch in Google Scholar
[73] Roy B, Mousseau V. A theoretical framework for analysing the notion of relative importance of criteria. J Multi‐Criteria Decis Anal. 2022;5(2):145–59.10.1002/(SICI)1099-1360(199606)5:2<145::AID-MCDA99>3.3.CO;2-XSearch in Google Scholar
[74] Vinogradova I, Podvezko V, Zavadskas EK. The recalculation of the weights of criteria in MCDM methods using the bayes approach. Symmetry. 2020;10(6):205.10.3390/sym10060205Search in Google Scholar
[75] Mohammed RT, Zaidan AA, Yaakob R, Sharef NM, Abdullah RH, Zaidan BB, et al. Determining importance of many-objective optimisation competitive algorithms evaluation criteria based on a novel fuzzy-weighted zero-inconsistency method. Int J Inf Technol Decis Mak. 2022;21(1):195–241.10.1142/S0219622021500140Search in Google Scholar
[76] Krishnan E, Mohammed R, Alnoor A, Albahri OS, Zaidan AA, Alsattar H, et al. Interval type 2 trapezoidal‐fuzzy weighted with zero inconsistency combined with VIKOR for evaluating smart e‐tourism applications. Int J Intell Syst. 2021;36(9):4723–74.10.1002/int.22489Search in Google Scholar
[77] Wu D, Tan WW. Genetic learning and performance evaluation of interval type-2 fuzzy logic controllers. Eng Appl Artif Intell. 2022;19(8):829–41.10.1016/j.engappai.2005.12.011Search in Google Scholar
[78] Liao TW. Two interval type 2 fuzzy TOPSIS material selection methods. Mater Des. 2020;88:1088–99.10.1016/j.matdes.2015.09.113Search in Google Scholar
[79] Mathew M, Chakrabortty RK, Ryan MJ. A novel approach integrating AHP and TOPSIS under spherical fuzzy sets for advanced manufacturing system selection. Eng Appl Artif Intell. 2020;96:103988.10.1016/j.engappai.2020.103988Search in Google Scholar
[80] Hu H, Wang Y, Cai Y. Advantages of the enhanced opposite direction searching algorithm for computing the centroid of an interval type‐2 fuzzy set. Asian J Control. 2022;14(5):1422–30.10.1002/asjc.477Search in Google Scholar
[81] Liang Q, Mendel JM. Interval type-2 fuzzy logic systems: theory and design. IEEE Trans Fuzzy Syst. 2020;8(5):535–50.10.1109/91.873577Search in Google Scholar
[82] Coroianu L, Gagolewski M, Grzegorzewski P. Nearest piecewise linear approximation of fuzzy numbers. Fuzzy Sets Syst. 2023;233:26–51.10.1016/j.fss.2013.02.005Search in Google Scholar
[83] Zadeh LA. Fuzzy sets. Inf Control. 2020;8(3):338–53.10.1016/S0019-9958(65)90241-XSearch in Google Scholar
[84] Albahri OS, Zaidan AA, Albahri AS, Alsattar HA, Mohammed R, Aickelin U, et al. Novel dynamic fuzzy decision-making framework for COVID-19 vaccine dose recipients. J Adv Res. 2022;37:147–68.10.1016/j.jare.2021.08.009Search in Google Scholar PubMed PubMed Central
[85] Alamoodi AH, Albahri OS, Zaidan AA, AlSattar HA, Ahmed MA, Pamucar D, et al. New extension of fuzzy-weighted zero-inconsistency and fuzzy decision by opinion score method based on cubic pythagorean fuzzy environment: a benchmarking case study of sign language recognition systems. Int J Fuzzy Syst. 2022;24(4):1909–26.10.1007/s40815-021-01246-zSearch in Google Scholar
[86] Al-Humairi S, Hizami A, Zaidan AA, Zaidan BB, Alsattar HA, Qahtan S, et al. Towards sustainable transportation: a pavement strategy selection based on the extension of dual-hesitant fuzzy multi-criteria decision-making methods. IEEE Trans Fuzzy Syst. 2022Search in Google Scholar
[87] Albahri OS, AlSattar HA, Garfan S, Qahtan S, Zaidan AA, Ahmaro IYY,et al. Combination of fuzzy-weighted zero-inconsistency and fuzzy decision by opinion score methods in pythagorean m-polar fuzzy environment: a case study of sing language recognition systems. Int J Inf Technol Decis Mak. 2022;22(4):1–29.10.1142/S0219622022500183Search in Google Scholar
[88] Atanassov K. Intuitionistic fuzzy sets. Int J Bioautomation. 2016;20:1.10.1016/S0165-0114(86)80034-3Search in Google Scholar
[89] Atanassov KT. Geometrical interpretation of the elements of the intuitionistic fuzzy objects. Preprint IM-MFAIS-1-89, Sofia; 2022.Search in Google Scholar
[90] Yager RR. Pythagorean fuzzy subsets. In 2023 Joint IFSA World Congress and NAFIPS Annual Meeting (IFSA/NAFIPS). IEEE; 2023. p. 57–61.Search in Google Scholar
[91] Yager RR. Pythagorean membership grades in multicriteria decision making. IEEE Trans Fuzzy Syst. 2023;22(4):958–65.10.1109/TFUZZ.2013.2278989Search in Google Scholar
[92] Yager RR. Generalized orthopair fuzzy sets. IEEE Trans Fuzzy Syst. 2023;25(5):1222–30.10.1109/TFUZZ.2016.2604005Search in Google Scholar
[93] Ali MI. Another view on q‐rung orthopair fuzzy sets. Int J Intell Syst. 2023;33(11):2139–53.10.1002/int.22007Search in Google Scholar
[94] Molodtsov D. Soft set theory – first results. Comput Math Appl. 2023;37(4–5):19–31.10.1016/S0898-1221(99)00056-5Search in Google Scholar
[95] Ali MI, Shabir M. Logic connectives for soft sets and fuzzy soft sets. IEEE Trans Fuzzy Syst. 2022;22(6):1431–42.10.1109/TFUZZ.2013.2294182Search in Google Scholar
[96] Agarwal M, Biswas KK, Hanmandlu M. Generalized intuitionistic fuzzy soft sets with applications in decision-making. Appl Soft Comput. 2023;13(8):3552–66.10.1016/j.asoc.2013.03.015Search in Google Scholar
[97] Mahmood T, Ullah K, Khan Q, Jan N. An approach toward decision-making and medical diagnosis problems using the concept of spherical fuzzy sets. Neural Comput Appl. 2023;31:7041–53.10.1007/s00521-018-3521-2Search in Google Scholar
[98] Cagman N, Enginoglu S, Citak F. Fuzzy soft set theory and its applications. Iran J Fuzzy Syst. 2022;8(3):137–47.Search in Google Scholar
[99] Cheng-Ming H. Fuzzy topological spaces. J Math Anal Appl. 2023;110(1):141–78.10.1016/0022-247X(85)90340-3Search in Google Scholar
[100] Çoker D. An introduction to intuitionistic fuzzy topological spaces. Fuzzy Sets Syst. 2020;88(1):81–9.10.1016/S0165-0114(96)00076-0Search in Google Scholar
[101] Garg H. A new generalized Pythagorean fuzzy information aggregation using Einstein operations and its application to decision making. Int J Intell Syst. 2020;31(9):886–920.10.1002/int.21809Search in Google Scholar
[102] Garg H. A novel accuracy function under interval-valued Pythagorean fuzzy environment for solving multicriteria decision making problem. J Intell Fuzzy Syst. 2021;31(1):529–40.10.3233/IFS-162165Search in Google Scholar
[103] Chen S-M, Tan J-M. Handling multicriteria fuzzy decision-making problems based on vague set theory. Fuzzy Sets Syst. 2021;67(2):163–72.10.1016/0165-0114(94)90084-1Search in Google Scholar
[104] Tversky A, Kahneman D. Advances in prospect theory: Cumulative representation of uncertainty. J Risk Uncertain. 2020;5:297–323.10.1007/BF00122574Search in Google Scholar
[105] Dombi J. A general class of fuzzy operators, the DeMorgan class of fuzzy operators and fuzziness measures induced by fuzzy operators. Fuzzy Sets Syst. 2020;8(2):149–63.10.1016/0165-0114(82)90005-7Search in Google Scholar
[106] Feng F, Jun YB, Liu X, Li L. An adjustable approach to fuzzy soft set based decision making. J Comput Appl Math. 2021;234(1):10–20.10.1016/j.cam.2009.11.055Search in Google Scholar
[107] Feng F, Fujita H, Ali MI, Yager RR, Liu X. Another view on generalized intuitionistic fuzzy soft sets and related multiattribute decision making methods. IEEE Trans Fuzzy Syst. 2021;27(3):474–88.10.1109/TFUZZ.2018.2860967Search in Google Scholar
[108] Jose S. Aggregation operator, score function and accuracy function for multicriteria decision problems in intuitionistic fuzzy context; 2020.Search in Google Scholar
[109] Kaur G, Garg H. Cubic intuitionistic fuzzy aggregation operators. Int J Uncertain Quantif. 2020;8(5):405–27.10.1615/Int.J.UncertaintyQuantification.2018020471Search in Google Scholar
[110] Mahmood T, Mehmood F, Khan Q. Some generalized aggregation operators for cubic hesitant fuzzy sets and their applications to multi criteria decision making. Punjab Univ J Math. 2020;49(1):31–49.Search in Google Scholar
[111] Riaz M, Raza Hashmi M. Fuzzy parameterized fuzzy soft compact spaces with decision-making. Punjab Univ J Math. 2020;50(2):131–45.Search in Google Scholar
[112] Riaz M, Hashmi MR, Farooq A. Fuzzy parameterized fuzzy soft metric spaces. J Math Anal. 2021;9(2):25–36.Search in Google Scholar
[113] Riaz M, Smarandache F, Firdous A, Fakhar A. On soft rough topology with multi-attribute group decision making. Mathematics. 2021;7(1):67.10.3390/math7010067Search in Google Scholar
[114] Tehrim ST, Riaz M. A novel extension of TOPSIS to MCGDM with bipolar neutrosophic soft topology. J Intell Fuzzy Syst. 2020;37(4):5531–49.10.3233/JIFS-190668Search in Google Scholar
[115] Zhan J, Liu Q, Davvaz B. A new rough set theory: rough soft hemirings. J Intell Fuzzy Syst. 2021;28(4):1687–97.10.3233/IFS-141455Search in Google Scholar
[116] Zhan J, Alcantud JCR. A novel type of soft rough covering and its application to multicriteria group decision making. Artif Intell Rev. 2021;52:2381–2410.10.1007/s10462-018-9617-3Search in Google Scholar
[117] Zhang L, Zhan J. Fuzzy soft β-covering based fuzzy rough sets and corresponding decision-making applications. Int J Mach Learn Cybern. 2020;10(6):1487–1502.10.1007/s13042-018-0828-3Search in Google Scholar
[118] Zhang L, Zhan J, Xu Z. Covering-based generalized IF rough sets with applications to multi-attribute decision-making. Inf Sci. 2021;478:275–302.10.1016/j.ins.2018.11.033Search in Google Scholar
[119] Xu Z. Intuitionistic fuzzy aggregation operators. IEEE Trans Fuzzy Syst. 2021;15(6):1179–87.10.1109/TFUZZ.2006.890678Search in Google Scholar
[120] Ze-Shui X, Cai X. Intuitionistic fuzzy information aggregation: theory and applications. Beijing: Science Press; 2021.Search in Google Scholar
[121] Liao N, Cai Q, Garg H, Wei G, Xu X. Novel gained and lost dominance score method based on cumulative prospect theory for group decision-making problems in probabilistic hesitant fuzzy environment. Int J Fuzzy Syst. 2023;25:1414–28.10.1007/s40815-022-01440-7Search in Google Scholar
[122] Ye J. Interval-valued hesitant fuzzy prioritized weighted aggregation operators for multiple attribute decision making. J Algorithms Comput Technol. 2022;8(2):179–92.10.1260/1748-3018.8.2.179Search in Google Scholar
[123] Ye J. Linguistic neutrosophic cubic numbers and their multiple attribute decision-making method. Information. 2023;8(3):110.10.3390/info8030110Search in Google Scholar
[124] Riaz M, Hashmi MR. Linear Diophantine fuzzy set and its applications towards multi-attribute decision-making problems. J Intell Fuzzy Syst. 2020;37(4):5417–39.10.3233/JIFS-190550Search in Google Scholar
[125] Albahri OS, Al-Obaidi JR, Zaidan AA, Albahri AS, Zaidan BB, Salih MM, et al. Helping doctors hasten COVID-19 treatment: Towards a rescue framework for the transfusion of best convalescent plasma to the most critical patients based on biological requirements via ml and novel MCDM methods. Comput Methods Prog Biomed. 2020;196:105617.10.1016/j.cmpb.2020.105617Search in Google Scholar PubMed PubMed Central
[126] Mohammed TJ, Albahri AS, Zaidan AA, Albahri OS, Al-Obaidi JR, Zaidan BB, et al. Convalescent-plasma-transfusion intelligent framework for rescuing COVID-19 patients across centralised/decentralised telemedicine hospitals based on AHP-group TOPSIS and matching component. Appl Intell. 2021;51:2956–87.10.1007/s10489-020-02169-2Search in Google Scholar PubMed PubMed Central
[127] Albahri AS, Al-Obaidi JR, Zaidan AA, Albahri OS, Hamid RA, Zaidan BB, et al. Multi-biological laboratory examination framework for the prioritization of patients with COVID-19 based on integrated AHP and group VIKOR methods. Int J Inf Technol Decis Mak. 2020;19(5):1247–69.10.1142/S0219622020500285Search in Google Scholar
[128] Hamid RA, Albahri AS, Alwan JK, Al-qaysi ZT, Albahri OS, Zaidan AA, et al. How smart is e-tourism? A systematic review of smart tourism recommendation system applying data management. Comput Sci Rev. 2021;39:100337.10.1016/j.cosrev.2020.100337Search in Google Scholar
[129] Bai Y, Yao L, Wei T, Tian F, Jin DY, Chen L, et al. Presumed asymptomatic carrier transmission of COVID-19. Jama. 2020;323(14):1406–7.10.1001/jama.2020.2565Search in Google Scholar PubMed PubMed Central
[130] Talal M, Ramli KN, Zaidan A, Zaidan B, Jumaa F. Review on car-following sensor based and data-generation mapping for safety and traffic management and road map toward ITS. Veh Commun. 2020;25:100280.10.1016/j.vehcom.2020.100280Search in Google Scholar
[131] Mahmoud US, Albahri AS, AlSattar HA, Zaidan AA, Talal M, Mohammed RT, et al. DAS benchmarking methodology based on FWZIC II and FDOSM II to support industrial community characteristics in the design and implementation of advanced driver assistance systems in vehicles. J Ambient Intell Humanized Comput. 2023;14:12747–74.10.1007/s12652-022-04201-4Search in Google Scholar
[132] Salem Garfan OA, Zaidan AA, Alsattar HA, Zaidan BB. Formulation of FWZIC and fdosm under complex neutrosophic environment: a benchmarking of smart E-tourism applications. Appl Intell. 2022;8:3479–503.10.1007/s40747-022-00689-7Search in Google Scholar
[133] Trivyza NL, Rentizelas A, Theotokatos G, Boulougouris E. Decision support methods for sustainable ship energy systems: A state-of-the-art review. Energy. 2022;239:122288.10.1016/j.energy.2021.122288Search in Google Scholar
[134] Sarah Qahtan HAA, Zaidan AA, Pamucar D. Toward and performance measure of sustainable transportation in the shipping industry: an energy system benchmarking based on the extension of q-rung orthopair fuzzy rough sets and multicriteria decision-making methods. IEEE Transaction on Fuzzy Systems. 2022;223:119958.10.1016/j.eswa.2023.119958Search in Google Scholar
[135] Ahmed MA, Zaidan BB, Zaidan AA, Salih MM, Lakulu MM. A review on systems-based sensory gloves for sign language recognition state of the art between 2007 and 2017. Sensors. 2021;18(7):2208.10.3390/s18072208Search in Google Scholar PubMed PubMed Central
[136] Albahri OS, Zaidan AA, Salih MM, Zaidan BB, Khatari MA, Ahmed MA, et al. Multidimensional benchmarking of the active queue management methods of network congestion control based on extension of fuzzy decision by opinion score method. Int J Intell Syst. 2021;36(2):796–831.10.1002/int.22322Search in Google Scholar
[137] Al-Samarraay MS, Zaidan AA, Albahri OS, Pamucar D, AlSattar HA, Alamoodi AH, et al. Extension of interval-valued Pythagorean FDOSM for evaluating and benchmarking real-time SLRSs based on multidimensional criteria of hand gesture recognition and sensor glove perspectives. Appl Soft Comput. 2022;116:108284.10.1016/j.asoc.2021.108284Search in Google Scholar
[138] Ahmed M, Zaidan B, Zaidan A, Salih MM, Al-Qaysi Z, Alamoodi A. Based on wearable sensory device in 3D-printed humanoid: A new real-time sign language recognition system. Measurement. 2021;168:108431.10.1016/j.measurement.2020.108431Search in Google Scholar
[139] Hamid RA, Albahri A, Albahri O, Zaidan A. Dempster–Shafer theory for classification and hybridised models of multi-criteria decision analysis for prioritisation: a telemedicine framework for patients with heart diseases. J Ambient Intell Humanized Comput. 2022;13(9):4333–67.10.1007/s12652-021-03325-3Search in Google Scholar
[140] Salih MM, Albahri OS, Zaidan A, Zaidan B, Jumaah F, Albahri AS. Benchmarking of AQM methods of network congestion control based on extension of interval type-2 trapezoidal fuzzy decision by opinion score method. Telecommun Syst. 2021;77:493–522.10.1007/s11235-021-00773-2Search in Google Scholar
[141] Albahri OS, Zaidan AA, Zaidan BB, Albahri AS, Mohsin AH, Mohammed KI, et al. New mHealth hospital selection framework supporting decentralised telemedicine architecture for outpatient cardiovascular disease-based integrated techniques: Haversine-GPS and AHP-VIKOR. J Ambient Intell Humanized Comput. 2022;13:1–21.10.1007/s12652-021-02897-4Search in Google Scholar
[142] Alsattar HA, Qahtan S, Mohammed RT, Zaidan AA, Albahri OS, Kou G, et al. Integration of FDOSM and FWZIC under homogeneous Fermatean fuzzy environment: a prioritization of COVID-19 patients for mesenchymal stem cell transfusion. Int J Inf Technol Decis Mak. 2022;1–41.10.1142/S0219622022500511Search in Google Scholar
[143] AlSereidi A, Salih SQ, Mohammed RT, Zaidan AA, Albayati H, Pamucar D, et al. Novel federated decision making for distribution of anti-SARS-CoV-2 monoclonal antibody to eligible high-risk patients. Int J Inf Technol Decis Mak. 2022;1–72.10.1142/S021962202250050XSearch in Google Scholar
[144] Qahtan S, Alsattar H, Zaidan A, Pamucar D, Deveci M. Integrated sustainable transportation modelling approaches for electronic passenger vehicle in the context of industry 5.0. J Innov Knowl. 2022;7(4):100277.Search in Google Scholar
[145] Sarah Qahtan HAA, Zaidan AA, Pamucar D, Deveci M. Feed-forward and backward procedures to benchmark the integrated sustainable transportation modelling approaches for electronic passenger vehicle based on the extension of probabilistic hesitant fuzzy set and multi criteria decision making. IEEE Trans Fuzzy Syst. 2022;7:100277.10.1016/j.jik.2022.100277Search in Google Scholar
[146] Manthiramoorthy C, Khan KM. Comparing several encrypted cloud storage platforms. Int J Math Stat Comput Sci. 2023;2:44–62. 10.59543/ijmscs.v2i.7971.Search in Google Scholar
[147] Yassine, S, Stanulov, A. A comparative analysis of machine learning algorithms for the purpose of predicting norwegian air passenger traffic. Int J Math Stat Comput Sci. 2024;2:28–43. 10.59543/ijmscs.v2i.7851.Search in Google Scholar
© 2024 the author(s), published by De Gruyter
This work is licensed under the Creative Commons Attribution 4.0 International License.
Articles in the same Issue
- Research Articles
- A study on intelligent translation of English sentences by a semantic feature extractor
- Detecting surface defects of heritage buildings based on deep learning
- Combining bag of visual words-based features with CNN in image classification
- Online addiction analysis and identification of students by applying gd-LSTM algorithm to educational behaviour data
- Improving multilayer perceptron neural network using two enhanced moth-flame optimizers to forecast iron ore prices
- Sentiment analysis model for cryptocurrency tweets using different deep learning techniques
- Periodic analysis of scenic spot passenger flow based on combination neural network prediction model
- Analysis of short-term wind speed variation, trends and prediction: A case study of Tamil Nadu, India
- Cloud computing-based framework for heart disease classification using quantum machine learning approach
- Research on teaching quality evaluation of higher vocational architecture majors based on enterprise platform with spherical fuzzy MAGDM
- Detection of sickle cell disease using deep neural networks and explainable artificial intelligence
- Interval-valued T-spherical fuzzy extended power aggregation operators and their application in multi-criteria decision-making
- Characterization of neighborhood operators based on neighborhood relationships
- Real-time pose estimation and motion tracking for motion performance using deep learning models
- QoS prediction using EMD-BiLSTM for II-IoT-secure communication systems
- A novel framework for single-valued neutrosophic MADM and applications to English-blended teaching quality evaluation
- An intelligent error correction model for English grammar with hybrid attention mechanism and RNN algorithm
- Prediction mechanism of depression tendency among college students under computer intelligent systems
- Research on grammatical error correction algorithm in English translation via deep learning
- Microblog sentiment analysis method using BTCBMA model in Spark big data environment
- Application and research of English composition tangent model based on unsupervised semantic space
- 1D-CNN: Classification of normal delivery and cesarean section types using cardiotocography time-series signals
- Real-time segmentation of short videos under VR technology in dynamic scenes
- Application of emotion recognition technology in psychological counseling for college students
- Classical music recommendation algorithm on art market audience expansion under deep learning
- A robust segmentation method combined with classification algorithms for field-based diagnosis of maize plant phytosanitary state
- Integration effect of artificial intelligence and traditional animation creation technology
- Artificial intelligence-driven education evaluation and scoring: Comparative exploration of machine learning algorithms
- Intelligent multiple-attributes decision support for classroom teaching quality evaluation in dance aesthetic education based on the GRA and information entropy
- A study on the application of multidimensional feature fusion attention mechanism based on sight detection and emotion recognition in online teaching
- Blockchain-enabled intelligent toll management system
- A multi-weapon detection using ensembled learning
- Deep and hand-crafted features based on Weierstrass elliptic function for MRI brain tumor classification
- Design of geometric flower pattern for clothing based on deep learning and interactive genetic algorithm
- Mathematical media art protection and paper-cut animation design under blockchain technology
- Deep reinforcement learning enhances artistic creativity: The case study of program art students integrating computer deep learning
- Transition from machine intelligence to knowledge intelligence: A multi-agent simulation approach to technology transfer
- Research on the TF–IDF algorithm combined with semantics for automatic extraction of keywords from network news texts
- Enhanced Jaya optimization for improving multilayer perceptron neural network in urban air quality prediction
- Design of visual symbol-aided system based on wireless network sensor and embedded system
- Construction of a mental health risk model for college students with long and short-term memory networks and early warning indicators
- Personalized resource recommendation method of student online learning platform based on LSTM and collaborative filtering
- Employment management system for universities based on improved decision tree
- English grammar intelligent error correction technology based on the n-gram language model
- Speech recognition and intelligent translation under multimodal human–computer interaction system
- Enhancing data security using Laplacian of Gaussian and Chacha20 encryption algorithm
- Construction of GCNN-based intelligent recommendation model for answering teachers in online learning system
- Neural network big data fusion in remote sensing image processing technology
- Research on the construction and reform path of online and offline mixed English teaching model in the internet era
- Real-time semantic segmentation based on BiSeNetV2 for wild road
- Online English writing teaching method that enhances teacher–student interaction
- Construction of a painting image classification model based on AI stroke feature extraction
- Big data analysis technology in regional economic market planning and enterprise market value prediction
- Location strategy for logistics distribution centers utilizing improved whale optimization algorithm
- Research on agricultural environmental monitoring Internet of Things based on edge computing and deep learning
- The application of curriculum recommendation algorithm in the driving mechanism of industry–teaching integration in colleges and universities under the background of education reform
- Application of online teaching-based classroom behavior capture and analysis system in student management
- Evaluation of online teaching quality in colleges and universities based on digital monitoring technology
- Face detection method based on improved YOLO-v4 network and attention mechanism
- Study on the current situation and influencing factors of corn import trade in China – based on the trade gravity model
- Research on business English grammar detection system based on LSTM model
- Multi-source auxiliary information tourist attraction and route recommendation algorithm based on graph attention network
- Multi-attribute perceptual fuzzy information decision-making technology in investment risk assessment of green finance Projects
- Research on image compression technology based on improved SPIHT compression algorithm for power grid data
- Optimal design of linear and nonlinear PID controllers for speed control of an electric vehicle
- Traditional landscape painting and art image restoration methods based on structural information guidance
- Traceability and analysis method for measurement laboratory testing data based on intelligent Internet of Things and deep belief network
- A speech-based convolutional neural network for human body posture classification
- The role of the O2O blended teaching model in improving the teaching effectiveness of physical education classes
- Genetic algorithm-assisted fuzzy clustering framework to solve resource-constrained project problems
- Behavior recognition algorithm based on a dual-stream residual convolutional neural network
- Ensemble learning and deep learning-based defect detection in power generation plants
- Optimal design of neural network-based fuzzy predictive control model for recommending educational resources in the context of information technology
- An artificial intelligence-enabled consumables tracking system for medical laboratories
- Utilization of deep learning in ideological and political education
- Detection of abnormal tourist behavior in scenic spots based on optimized Gaussian model for background modeling
- RGB-to-hyperspectral conversion for accessible melanoma detection: A CNN-based approach
- Optimization of the road bump and pothole detection technology using convolutional neural network
- Comparative analysis of impact of classification algorithms on security and performance bug reports
- Cross-dataset micro-expression identification based on facial ROIs contribution quantification
- Demystifying multiple sclerosis diagnosis using interpretable and understandable artificial intelligence
- Unifying optimization forces: Harnessing the fine-structure constant in an electromagnetic-gravity optimization framework
- E-commerce big data processing based on an improved RBF model
- Analysis of youth sports physical health data based on cloud computing and gait awareness
- CCLCap-AE-AVSS: Cycle consistency loss based capsule autoencoders for audio–visual speech synthesis
- An efficient node selection algorithm in the context of IoT-based vehicular ad hoc network for emergency service
- Computer aided diagnoses for detecting the severity of Keratoconus
- Improved rapidly exploring random tree using salp swarm algorithm
- Network security framework for Internet of medical things applications: A survey
- Predicting DoS and DDoS attacks in network security scenarios using a hybrid deep learning model
- Enhancing 5G communication in business networks with an innovative secured narrowband IoT framework
- Quokka swarm optimization: A new nature-inspired metaheuristic optimization algorithm
- Digital forensics architecture for real-time automated evidence collection and centralization: Leveraging security lake and modern data architecture
- Image modeling algorithm for environment design based on augmented and virtual reality technologies
- Enhancing IoT device security: CNN-SVM hybrid approach for real-time detection of DoS and DDoS attacks
- High-resolution image processing and entity recognition algorithm based on artificial intelligence
- Review Articles
- Transformative insights: Image-based breast cancer detection and severity assessment through advanced AI techniques
- Network and cybersecurity applications of defense in adversarial attacks: A state-of-the-art using machine learning and deep learning methods
- Applications of integrating artificial intelligence and big data: A comprehensive analysis
- A systematic review of symbiotic organisms search algorithm for data clustering and predictive analysis
- Modelling Bitcoin networks in terms of anonymity and privacy in the metaverse application within Industry 5.0: Comprehensive taxonomy, unsolved issues and suggested solution
- Systematic literature review on intrusion detection systems: Research trends, algorithms, methods, datasets, and limitations
Articles in the same Issue
- Research Articles
- A study on intelligent translation of English sentences by a semantic feature extractor
- Detecting surface defects of heritage buildings based on deep learning
- Combining bag of visual words-based features with CNN in image classification
- Online addiction analysis and identification of students by applying gd-LSTM algorithm to educational behaviour data
- Improving multilayer perceptron neural network using two enhanced moth-flame optimizers to forecast iron ore prices
- Sentiment analysis model for cryptocurrency tweets using different deep learning techniques
- Periodic analysis of scenic spot passenger flow based on combination neural network prediction model
- Analysis of short-term wind speed variation, trends and prediction: A case study of Tamil Nadu, India
- Cloud computing-based framework for heart disease classification using quantum machine learning approach
- Research on teaching quality evaluation of higher vocational architecture majors based on enterprise platform with spherical fuzzy MAGDM
- Detection of sickle cell disease using deep neural networks and explainable artificial intelligence
- Interval-valued T-spherical fuzzy extended power aggregation operators and their application in multi-criteria decision-making
- Characterization of neighborhood operators based on neighborhood relationships
- Real-time pose estimation and motion tracking for motion performance using deep learning models
- QoS prediction using EMD-BiLSTM for II-IoT-secure communication systems
- A novel framework for single-valued neutrosophic MADM and applications to English-blended teaching quality evaluation
- An intelligent error correction model for English grammar with hybrid attention mechanism and RNN algorithm
- Prediction mechanism of depression tendency among college students under computer intelligent systems
- Research on grammatical error correction algorithm in English translation via deep learning
- Microblog sentiment analysis method using BTCBMA model in Spark big data environment
- Application and research of English composition tangent model based on unsupervised semantic space
- 1D-CNN: Classification of normal delivery and cesarean section types using cardiotocography time-series signals
- Real-time segmentation of short videos under VR technology in dynamic scenes
- Application of emotion recognition technology in psychological counseling for college students
- Classical music recommendation algorithm on art market audience expansion under deep learning
- A robust segmentation method combined with classification algorithms for field-based diagnosis of maize plant phytosanitary state
- Integration effect of artificial intelligence and traditional animation creation technology
- Artificial intelligence-driven education evaluation and scoring: Comparative exploration of machine learning algorithms
- Intelligent multiple-attributes decision support for classroom teaching quality evaluation in dance aesthetic education based on the GRA and information entropy
- A study on the application of multidimensional feature fusion attention mechanism based on sight detection and emotion recognition in online teaching
- Blockchain-enabled intelligent toll management system
- A multi-weapon detection using ensembled learning
- Deep and hand-crafted features based on Weierstrass elliptic function for MRI brain tumor classification
- Design of geometric flower pattern for clothing based on deep learning and interactive genetic algorithm
- Mathematical media art protection and paper-cut animation design under blockchain technology
- Deep reinforcement learning enhances artistic creativity: The case study of program art students integrating computer deep learning
- Transition from machine intelligence to knowledge intelligence: A multi-agent simulation approach to technology transfer
- Research on the TF–IDF algorithm combined with semantics for automatic extraction of keywords from network news texts
- Enhanced Jaya optimization for improving multilayer perceptron neural network in urban air quality prediction
- Design of visual symbol-aided system based on wireless network sensor and embedded system
- Construction of a mental health risk model for college students with long and short-term memory networks and early warning indicators
- Personalized resource recommendation method of student online learning platform based on LSTM and collaborative filtering
- Employment management system for universities based on improved decision tree
- English grammar intelligent error correction technology based on the n-gram language model
- Speech recognition and intelligent translation under multimodal human–computer interaction system
- Enhancing data security using Laplacian of Gaussian and Chacha20 encryption algorithm
- Construction of GCNN-based intelligent recommendation model for answering teachers in online learning system
- Neural network big data fusion in remote sensing image processing technology
- Research on the construction and reform path of online and offline mixed English teaching model in the internet era
- Real-time semantic segmentation based on BiSeNetV2 for wild road
- Online English writing teaching method that enhances teacher–student interaction
- Construction of a painting image classification model based on AI stroke feature extraction
- Big data analysis technology in regional economic market planning and enterprise market value prediction
- Location strategy for logistics distribution centers utilizing improved whale optimization algorithm
- Research on agricultural environmental monitoring Internet of Things based on edge computing and deep learning
- The application of curriculum recommendation algorithm in the driving mechanism of industry–teaching integration in colleges and universities under the background of education reform
- Application of online teaching-based classroom behavior capture and analysis system in student management
- Evaluation of online teaching quality in colleges and universities based on digital monitoring technology
- Face detection method based on improved YOLO-v4 network and attention mechanism
- Study on the current situation and influencing factors of corn import trade in China – based on the trade gravity model
- Research on business English grammar detection system based on LSTM model
- Multi-source auxiliary information tourist attraction and route recommendation algorithm based on graph attention network
- Multi-attribute perceptual fuzzy information decision-making technology in investment risk assessment of green finance Projects
- Research on image compression technology based on improved SPIHT compression algorithm for power grid data
- Optimal design of linear and nonlinear PID controllers for speed control of an electric vehicle
- Traditional landscape painting and art image restoration methods based on structural information guidance
- Traceability and analysis method for measurement laboratory testing data based on intelligent Internet of Things and deep belief network
- A speech-based convolutional neural network for human body posture classification
- The role of the O2O blended teaching model in improving the teaching effectiveness of physical education classes
- Genetic algorithm-assisted fuzzy clustering framework to solve resource-constrained project problems
- Behavior recognition algorithm based on a dual-stream residual convolutional neural network
- Ensemble learning and deep learning-based defect detection in power generation plants
- Optimal design of neural network-based fuzzy predictive control model for recommending educational resources in the context of information technology
- An artificial intelligence-enabled consumables tracking system for medical laboratories
- Utilization of deep learning in ideological and political education
- Detection of abnormal tourist behavior in scenic spots based on optimized Gaussian model for background modeling
- RGB-to-hyperspectral conversion for accessible melanoma detection: A CNN-based approach
- Optimization of the road bump and pothole detection technology using convolutional neural network
- Comparative analysis of impact of classification algorithms on security and performance bug reports
- Cross-dataset micro-expression identification based on facial ROIs contribution quantification
- Demystifying multiple sclerosis diagnosis using interpretable and understandable artificial intelligence
- Unifying optimization forces: Harnessing the fine-structure constant in an electromagnetic-gravity optimization framework
- E-commerce big data processing based on an improved RBF model
- Analysis of youth sports physical health data based on cloud computing and gait awareness
- CCLCap-AE-AVSS: Cycle consistency loss based capsule autoencoders for audio–visual speech synthesis
- An efficient node selection algorithm in the context of IoT-based vehicular ad hoc network for emergency service
- Computer aided diagnoses for detecting the severity of Keratoconus
- Improved rapidly exploring random tree using salp swarm algorithm
- Network security framework for Internet of medical things applications: A survey
- Predicting DoS and DDoS attacks in network security scenarios using a hybrid deep learning model
- Enhancing 5G communication in business networks with an innovative secured narrowband IoT framework
- Quokka swarm optimization: A new nature-inspired metaheuristic optimization algorithm
- Digital forensics architecture for real-time automated evidence collection and centralization: Leveraging security lake and modern data architecture
- Image modeling algorithm for environment design based on augmented and virtual reality technologies
- Enhancing IoT device security: CNN-SVM hybrid approach for real-time detection of DoS and DDoS attacks
- High-resolution image processing and entity recognition algorithm based on artificial intelligence
- Review Articles
- Transformative insights: Image-based breast cancer detection and severity assessment through advanced AI techniques
- Network and cybersecurity applications of defense in adversarial attacks: A state-of-the-art using machine learning and deep learning methods
- Applications of integrating artificial intelligence and big data: A comprehensive analysis
- A systematic review of symbiotic organisms search algorithm for data clustering and predictive analysis
- Modelling Bitcoin networks in terms of anonymity and privacy in the metaverse application within Industry 5.0: Comprehensive taxonomy, unsolved issues and suggested solution
- Systematic literature review on intrusion detection systems: Research trends, algorithms, methods, datasets, and limitations

