Enhancing IoT device security: CNN-SVM hybrid approach for real-time detection of DoS and DDoS attacks
-
Qais Al-Na’amneh
, Ahmad Nasayreh
, Ameera S. Jaradat
Abstract
The Internet of Things (IoT) has expanded into a realm of cutting-edge integrated solutions across numerous applications, following three stages of development: communication, authentication, and computing. However, each layer inside the three tier IoT architecture faces a spectrum of security concerns due to the IoT’s openness, scope, and resource limits. Therefore, developing a secure IoT system is vital, shielding against attackers leveraging IoT devices to obtain network access and maintaining data security during transmission between these devices. Despite developments in Intrusion Detection Systems, identifying Denial-of-Service (DoS) and Distributed Denial-of-Service (DDoS) attacks in real-time remains a significant issue, especially in the environment of IoT devices, which are diverse and resource restricted. This study provides a Convolutional Neural Network-Support Vector Machine (CNN-SVM) hybrid technique, targeted at overcoming these limits by enhancing detection speed and accuracy, thus addressing this substantial gap in the area. This research offers a hybrid model that combines CNN for feature extraction with SVM as a classifier. This model employs a CNN to extract essential elements from the data and classifies attacks as either DDoS or benign. Our results highlight the potential performance of our model, which was trained on the real Canadian institute for cybersecurity (CIC) IoT dataset in 2023. Notably, our hybrid model outperformed classic machine learning (ML) alternatives such as CNN, SVM, K-nearest neighbors, Naïve Bayes, and Logistic Regression. During testing, our model attained a remarkable accuracy rate of 99% and an F1-score of 99%, outperforming the highest-performing SVM ML model with an accuracy of 98% and the other ML methods.
Abbreviations
- Term
-
Description
- CNN
-
convolutional neural networks
- DPI
-
deep packet inspection
- DoS
-
denial-of-service
- DDoS
-
distributed denial-of-service
- ELM
-
extreme learning machines
- IDS
-
intrusion detection systems
- IOV
-
internet of vehicles
- IOT
-
internet of things
- IPS
-
intrusion prevention systems
- KNN
-
k closest neighbor
- LR
-
logistic regression
- ML
-
machine learning
- NB
-
Naïve Bayes
- NN
-
neural network
- RF
-
random forest
- SVM
-
support vector machine
- TPMs
-
trusted platform modules
1 Introduction
Internet of Things (IoT) is the wireless connectivity between smart devices or things connected over the Internet. This technology has rapidly emerged as a transformative solution, seamlessly linking countless devices across the globe. IoT’s far-reaching applications extend from empowering smart homes and advanced transportation systems to revolutionizing healthcare, education, aviation, and even forestry. The advent of the Internet of Vehicles has added yet another dimension to this interconnected landscape [1,2,3,4,5,6,7,8]. However, the allure of IoT also casts a shadow on cyberattacks targeting its infrastructure posing severe threats. These attacks have the potential to disrupt supply chains, sabotage production lines, compromise manufacturing processes, jeopardize vehicle safety, and even endanger public health [9,10]. Vulnerabilities and threats stem from the mismanagement of IoT devices, underscoring the urgency of understanding these risks. Users must be well-versed in potential threats and equipped with strategies to respond to malicious activities targeting IoT devices. The need to fortify IoT interactions’ integrity, confidentiality, availability, and authenticity has prompted comprehensive security services [11,12]. Figure 1 exemplifies the fundamental CIA Triad of confidentiality, integrity, and availability, underpinning the IoT security architecture [13].

CIA triad of confidentiality, integrity, and availability.
As IoT networks expand in complexity and scale, the repercussions of security breaches are amplified. Of particular concern are Denial-of-Service (DoS) and Distributed Denial-of-Service (DDoS) attacks, which can inflict substantial damage. These attacks target service availability by inundating systems with an overwhelming traffic volume, resulting in operational disruptions and user experience degradation. Unfortunately, conventional security measures often prove inadequate against these agile and multifaceted threats, leaving IoT systems exposed and vulnerable to compromise. Addressing these security challenges calls for a multifaceted approach. The proposed security systems need to incorporate essential functions, including Intrusion prevention systems (IPS), Intrusion detection systems (IDS), firewalls, content filtering, Deep packet inspection (DPI) technologies, and Next-Generation Firewalls. With emerging, more sophisticated variants of attacks being launched [14], the necessity of an “Anti-DDoS” solution becomes increasingly apparent. Recent instances of significant server demolitions underscore the immediacy of addressing DDoS defense in IoT, prompting urgent research in this domain [15]. To effectively navigate this evolving landscape of cyber threats within IoT environments, innovative methodologies are imperative. Machine learning (ML) and deep learning techniques offer potential solutions by providing real-time attack detection and classification capabilities. The fusion of Convolutional Neural Networks (CNN) and Support Vector Machine (SVM) algorithms emerges as a promising path. This amalgamation, with its ability to tackle intricate challenges posed by DoS and DDoS attacks, is poised to reshape IoT security.
In this study, we explore the nuances of DDoS attacks’ conceptualization and their profound impact on IoT within the context of ML and deep learning. Recognizing the potential of this fusion, we introduce a hybrid approach that melds CNN and SVM. This fusion not only inherits the legacy of traditional models in recognizing complex patterns [16] but also harnesses SVM’s classification prowess. This innovative hybrid approach holds promise in uncovering perilous attacks directed at IoT devices. Our evaluation leverages the Canadian institute for cybersecurity (CIC) IoT Dataset 2023, sourced from the Canadian Institute for Cybersecurity [17].
The primary motivation of this research is to address the growing challenges created by DoS and DDoS assaults on IoT devices. This study provides a method for detecting cyber intrusions using a hybrid CNN and SVM model. Our technique extracts feature and classifies data appropriately, making IoT devices more immune to changing threats. As a result, our technique helps to build a more reliable and secure IoT application architecture.
A primary objective of this research is to construct a sophisticated hybrid model that marries the capabilities of CNN and SVM algorithms. By synergizing these two distinct approaches, we aim to develop a comprehensive and adaptable model that can effectively discern and classify various attack types, particularly DoS and DDoS attacks. Through the pursuit of these objectives, this research seeks to contribute to the enhancement of IoT security by providing a reliable and proactive defense mechanism against the evolving threat landscape of DoS and DDoS attacks. The successful creation and application of the hybrid model could potentially reshape the IoT security landscape, fostering safer and more resilient IoT ecosystems.
The study is organized as follows: Section 2 discusses the recent related works in literature. A methodology of this research, data description, and processing are presented in Section 3. Section 4 introduces our findings and ensuing discussions. Concluding remarks are summarized in Section 5.
2 Related work
This section delves into earlier studies that have tackled the intricate task of identifying and categorizing malicious activities to DDoS attacks or benign. Researchers have harnessed a spectrum of ML and deep learning algorithms to address these challenges. One noteworthy endeavor by Asad et al. [18] introduced the deep detect neural network (NN), an innovative deep learning paradigm utilizing feed-forward back-propagation. Concentrating on DDoS attacks, this model underwent evaluation using the CIC IDS 2017 Dataset, achieving an impressive 98% accuracy. Another contribution by de Assis et al. [19] focused on a conventional NN, commonly known as CNN, equipped with 2D CONV layers. Designed to tackle DDoS attacks within Software Defined Networking (SDN), this model exhibited a remarkable 95.4% accuracy on the CICDDoS 2019 dataset, which involved simulated IP flows. Table 1 shows the comparison of studies similar to our study.
Summary of previous studies close to our approach
| References | Dataset | Methodology | Best model | Best accuracy (%) |
|---|---|---|---|---|
| [18] | CICIDS 2017 | Deep detect NN | Deep detect NN | 98 |
| [19] | CICDDoS 2019 | CNN | CNN | 95.4 |
| [20] | KDD99 | SVM, DT | SVM | 85 |
| [22] | Transmission control protocol (TCP) traffic | SVM, NN, NB | SVM | 80 |
| [23] | KDDCup 99 NSL-KDD, UNSW-NB15, Kyoto, WSN-DS and CICIDS 2017 | DNN 1 layer | DNN | 992 |
| [24] | IDE2012, UNSW-NB15 | Smart grid network | Smart grid network | 97 |
| [25] | CICIDS dataset 2017 | DNN | DNN | 97.59 |
| [26] | CICIDS 2017 | Deep belief network (DBN), SVM, SNN, RNN, and FNN | Deep belief network | 97.93 |
| [27] | CICIDS 2017 | LR, KNN, Gaussian NB, RF, Linear SVM, and Linear discriminant analysis | RF | 96.5 |
| [28] | SDN-WISE IoT | SVN, NB, DT | DT | 98.1 |
| [29] | CICDDoS2019 | AE-MLP | AE-MLP | 98 |
| [30] | CIC-IDS2017 CIC-DDoS2019 | BI-LSTM and GMM | — | 95.3 |
| [31] | CIC DDoS 2019 | NN with Xavier normal initializer and minimized using SGD | — | 79.93 |
| [32] | CICIDS2017 | Deep learning | CNN-BiLSTM | 99.76 |
| [33] | MIT-BIH arrhythmia | DNNs | DNN | 99.0 |
| [34] | Flood collected traffics | DT, RF, and DJ | DT | 93.2% |
ML algorithms have also played a pivotal role in this domain. Sudar et al. [20] proposed the utilization of SVM and Decision Tree (DT) algorithms for identifying DDoS attacks within Software Defined Networks (SDN). SVM demonstrated 85% accuracy, surpassing DT’s 78%. [21] expanded this exploration by considering a variety of algorithms, including CNN, LSTM, RNN, SVM, Random Forest (RF), K-Nearest Neighbors (KNN), and Naive Bayes (NB). Their aim was to detect and distinguish DDoS attacks, with the RF model achieving an astonishing 100% accuracy, outshining other models. Moreover, communication classification was also a subject of inquiry. Meti et al. [22] employed ML algorithms such as NN, SVM, and NB to categorize communications as legitimate or unauthorized. SVM stood out, achieving an impressive 80% recall rate, surpassing NB and NN. Vinayakumar et al. [23] introduced a Deep Neural Network (DNN) trained on diverse datasets, yielding an accuracy of 0.992 on the binary classification dataset WSN-DS.
Within the realm of smart grids, Ali and Li [24] ventured into DDoS detection, utilizing the IDE2012 and UNSW-NB15 datasets. Their model outperformed six ML algorithms, achieving a noteworthy 97% accuracy on the IDE2012 dataset. Makuvaza et al. [25] employed DNN on the CICIDS 2017 dataset, securing an accuracy of 97.59%. Manimurugan et al. [26] introduced a novel Deep Belief Network (DBN) algorithm model, coupled with SVM, SNN, RNN, and FNN on the CICIDS 2017 dataset. The proposed DBN model emerged as superior, boasting an accuracy of up to 97.93%. And Bindra and Sood [27] made a comparison between different ML algorithm which are Logistic Regression, Gaussian NB, Linear SVM, KNNs, RF, and Linear Discriminant Analysis on CICIDS2017 dataset and best accuracy was 96.5% on RF with an estimator of 20. Bhayo et al. [28] proposed an approach based on ML algorithms in the detection and classification of in the realm of detecting DDoS attacks within SDN-WISE IoT controllers. Wei et al. [29] examined the prowess of NB, DT, and SVM algorithms. The results showcased commendable accuracy rates of 97.4, 96.1, and 98.1% for NB, SVM, and DT, respectively. Another innovative endeavor [29] introduced the AE-MLP hybrid approach, amalgamating Autoencoder (AE) and Multi-layer Perceptron Network (MLP) to identify and classify DDoS attacks. While achieving an impressive f1-score of 98% using the CICDDoS2019 dataset, the study acknowledged limitations, including the absence of a comparison with other deep learning models like CNN and various ML algorithms.
Further exploration led to the design of a novel approach [30] combining Bi-Directional Long Short-Term Memory (BI-LSTM) and Gaussian Mixture Model (GMM) with incremental learning to combat DDoS attacks. The evaluation on CIC-IDS2017 and CIC-DDoS2019 datasets yielded accuracies of 0.953 and 0.946, respectively, albeit with potential limitations in handling encrypted traffic. NNs were harnessed in another study [31], introducing an approach facilitated by automatic feature selection and optimized through techniques like Xavier normal initializer and Stochastic Gradient Descent (SGD). The model’s evaluation using CIC DDoS 2019 demonstrated an average f1-score of 79.93%.
In [32] detect DDOS attacks utilize deep learning algorithms for managing DDoS attacks in IoT networks after that Combining RNN, LSTM-RNN, CNN, and CNN-BiLSTM for DDoS detection. Finally, the models using the CICIDS2017 dataset were tested and assessed. High accuracy rates and precision in detecting DDoS attacks were achieved. Although accuracy of 99.76% and precision of 98.90% were achieved the limitations are insecure nature and dynamic communication between resources of IoT devices (data storage and processing units). Varghese et al. [33] proposed the automated IoT-enabled arrhythmia detection system with deep learning model and automated ECG beat classification method using DNNs. The model achieved a testing accuracy of 99.03% and a training accuracy of 99.09% but the limitation is insecurity in between resources of IoT devices. Finally, the data collected (heartbeats classified into four types: normal beat (N), left bundle branch block beat (L), right bundle branch block beat (R), and premature ventricular contraction (V)) by IoT-enabled ECG monitoring device are analyzed by deep learning model.
Lastly, an IoT-based flood status prediction (IoT-FSP) model was suggested [34] to anticipate flood conditions using internet of things (IoT) technology handle multivariate outputs of 13 different flood statuses and used three ML algorithms (DT algorithm, Decision Jungle algorithm, RF algorithm) for flood prediction to acts as an early warning and flood monitoring system with achieves an average accuracy of 85.72% and DT algorithm scores the highest accuracy of 93.22%.
Despite the considerable volume of research in our domain, it is essential to acknowledge the discernible gaps that persist within the existing literature. Many studies have centered their focus on specific datasets, as underscored in Table 1. However, this concentrated approach risks neglecting the intricate nuances inherent in the ever-evolving realm of real-world networks. This limitation prompts the need for a dataset that offers both comprehensive coverage and diversity, encompassing a broader spectrum of network behaviors and potential threats. By incorporating such a dataset, we embark on a strategic endeavor aimed at enhancing the adaptability and efficiency of our proposed approach. This empowerment enables our solution to adeptly identify nascent intrusion patterns and seamlessly adapt to their evolution.
Several studies have embraced a wide variety of techniques, ranging from traditional ML algorithms to the cutting-edge arena of deep learning methodologies. However, the selection of these techniques, often involving intricate parameters, such as those present within a CNN combined with SVM and Extreme learning machines (ELM), can occasionally fall short in comprehensively addressing critical factors such as network scale, complexity, and data quality. To bridge this gap, a synergistic approach that intelligently amalgamates the strengths of diverse techniques is imperative. The goal is to enhance accuracy while effectively minimizing the occurrence of false positives (FPs).
Therefore, considering these evident gaps, our research takes on a proactive, forward-looking stance. This study is balanced to blaze an unprecedented trail, where the fusion of CNN and SVM gives rise to a meticulously tailored hybrid model engineered to deftly detect real-time DoS and DDoS attacks. This innovative trajectory marries the prowess of deep ML with an exhaustive comparison across a gamut of alternative learning algorithms. Our mission is to bridge these gaps, ultimately contributing to the advancement of intrusion detection within dynamic network environments.
3 Methodology
In this section, we discuss our proposed approach for classification and detection of DDoS, DoS, and benign attacks. We designed a CNN deep learning model with an SVM. A CNN consists of multiple layers that can extract features from the data. In the proposed approach, the CNN architecture consists of 8 layers consisting of three convolutional layers (CV), three MAX Pooling (MP), one of which is Global MP, and two fully connected layers (FC). Most of the features are extracted from the input data through the first convolutional layer, where the output of this layer becomes the input for the next layer, where the SVM was used for the final classification by introducing the features extracted from the CNN by separating the data elements into different categories via a hyperplane. In the proposed CNN + SVM hybrid model, the SVM model was used instead of the classification layer in CNN. The proposed architecture is described in Figure 2.

Flowchart of the proposed technique.
3.1 Dataset collection and description
In the study by Singh et al. [35], an authentic IoT attack dataset was utilized to cultivate practical security analytics applications within real IoT operations. This approach involved employing actual IoT devices both as attackers and victims, fostering a genuine representation of the IoT environment. The primary objective was to empower researchers in developing robust security models to counteract IoT-based attacks effectively. To accomplish this, a comprehensive experimentation was conducted, encompassing a total of 33 distinct attacks. These attacks were executed within a meticulously designed IoT topology comprising 105 devices of different types and brands. The overarching goal was two-fold: first, to comprehend the intricate dynamics of these attacks within an IoT setting, and second, to systematically categorize them into seven distinct categories. These categories encompassed DDoS, DoS, Recon, Web-based, Brute Force, Spoofing, and Mirai attacks. This categorization aimed to facilitate the accurate identification and classification of IoT traffic as either malicious or benign. Table 2 discuss DDoS and DoS attacks affect in IOT environment as follows.
Description of the type of attacks
| Type | Description |
|---|---|
| Benign | Refer to data points that are considered normal, non-malicious, and safe. These instances represent regular, legitimate, or expected behavior. In cybersecurity, benign instances could include legitimate user actions, network traffic that follows normal patterns, and non-malicious software applications. In ML or data analysis, the benign class is often used to represent the normal state or behavior of the system |
| ACK fragmentation | A limited number of maximum-sized packets are used to compromise network functionality. These fragmented packets are often successfully sent and processed by routers, firewalls, and IPSs [37] |
| User datagram protocol (UDP) flood | This is also known as a session-less networking protocol attack. In this attack, the attacker floods several UDP packets on random target ports, causing the host to continually check for an application listening port and respond with “ICMP Destination” unreachable packets [38] |
| Slow Loris | The attacker sends partial HTTP GET requests, and the server starts a connection, but the attacker fails to react to the server to complete the connection. This Slow DoS variation is frequently misinterpreted as legitimate network activity when LN has either poor or slow connections [39] |
| Ping/ICMP flood | This assault works similar to the UDP flood attack in that it floods the target host resource with ICMP Echo Request (ping) packets. Because the target servers frequently attempt to respond with ICMP Echo Reply packets, this form of attack can use both incoming and outgoing bandwidth, resulting in considerable overall system delay [40] |
| Reset/Finish (RST/FIN) flood | RST-FIN flood is a DDoS attack that aims to disrupt network activity by exhausting bandwidth and resources on stateful devices in its route. As a result, various systems may react differently to these packets, resulting in unforeseen problems [41] |
| Acknowledge/Push (ACK/PSH) flood | An ACK-PSH flood is a DDoS attack that aims to disrupt network activity by overflowing bandwidth and resources on stateful devices in its route. Stateful defenses can be brought down (in some situations, into a failure open mode) by continually sending ACK-PSH packets toward a target [42] |
| ICMP/UDP fragmentation | In a UDP fragmentation attack, attackers send large UDP packets (1,500 + bytes) to maximize transmission speed with fewer packets [43] |
| TCP flood | Synchronize (SYN) flood is a kind of (DoS) attack in which a threat actor floods a server with many requests but fails to acknowledge the connection, leaving it half-opened, usually with the intent of consuming server resources and denying other users access to that service [44] |
| SYN flood | A SYN flood DDoS assault takes advantage of a known flaw in the TCP connection process (the “three-way handshakes. Synchronize (SYN) SYN requests but either does not respond to the host’s SYN-ACK answer or sends the SYN queries from a faked IP address in a SYN flood scenario [45] |
| Synonymous-IP flood | Many modified (TCP-SYN) packets with the source and destination addresses as the targeted address, cause the server to spend its resources to process the incoming traffic [17] |
3.2 Countermeasures
Countermeasures indicated in Table 3 for IoT attacks include a combination of technological and organizational measures targeted at improving security and protecting IoT devices and networks from potential threats. By implementing these measures, enterprises may significantly enhance the security posture of their IoT ecosystem and lower the chance of falling victim to IoT-related cyber-attacks.
Countermeasures
| Type | Description |
|---|---|
| Authentication | Using strong authentication measures, such as two-factor authentication, to ensure that only authorized users and devices can connect to the IoT network [46] |
| Firmware and software updates | Updating IoT device firmware and software on a regular basis to patch vulnerabilities and ensure the most recent security upgrades are in place [47] |
| Secure communication | To prevent data interception and tampering, enforce encrypted connection between IoT devices and servers [48] |
| Network segmentation | IoT devices are separated from essential systems in separate networks, limiting the potential impact of a hack [48] |
| Firewalls and IDS | Using firewalls and IDSs to monitor and manage network traffic for any suspicious activity or intrusions |
| Secure boot and trusted platform modules (TPMs) | Secure boot and TPMs: Using secure boot processes and TPMs to ensure the device’s and software’s integrity [49] |
| Least privilege principle | Assigning the bare minimum of permissions and privileges to IoT devices and users to minimize potential damage in the event of a breach [49] |
| Data encryption | To secure sensitive data from unauthorized access, information is encrypted during transit [50] |
| IoT device management | Using strong device management solutions to remotely monitor the health and security of IoT devices and apply appropriate upgrades [50] |
| Regular security audits | Conducting security audits on a regular basis to detect vulnerabilities and flaws in the IoT infrastructure [51] |
| Vendor security assurance | Working with reliable IoT device manufacturers who prioritize security and upgrade their products on a regular basis [51] |
| Privacy protection | Assuring compliance with privacy requirements and safeguarding user data against unwanted access or misuse [52] |
| Continuous monitoring and incident response | Implementing 24/7 monitoring and an efficient incident response plan to promptly address any security breaches or incidents [52] |
3.3 Preprocessing
All rows containing a missing value have been removed which consists of five rows, and each row that contains a missing value has also been removed. Also, due to the discrepancy in the values in the data, we decided to use Min Max scaler [36] which contributes to scaling the data. And before entering data into a CNN or traditional models in ML, it is better that all data and values be in the same range with the least degree of variation, as Min Max scaler was used, and all related values were confined between [0, 1]. Equation (1) shows Min-max Scaling.
3.4 Hybrid CNN: Integrating SVM and ELM
Our proposed hybrid model 1D CNN + SVM was built for classification between DDoS, DoS, and Benign. The hybrid model 1D CNN + SVM, proposed in this study for classifying DDoS, DoS, and Benign attacks, operates through two distinct stages. In the initial stage, a CNN is employed to extract intricate features from the data. The CNN architecture in this approach is composed of eight layers. The model initiates with three convolutional layers (Conv1D), each having 32, 64, and 128 filters, respectively, with a kernel size of (3 × 3). This configuration enables the network to discern intricate patterns, aiding in the prevention of overfitting. Furthermore, the architecture incorporates MP with a size of 2, effectively reducing the spatial dimensions of the data. The activation function Rectified linear unit (ReLU) is applied, which rectifies negative values to zero while retaining positive values unchanged. This choice helps mitigate the vanishing gradient problem. The final layer comprises Dense layers housing 512 output units. For binary classification, the sigmoid activation function is employed as the output layer, and the optimizer Adam is selected. The training dataset is partitioned into 75% for training, 10% for validation, and 15% for testing purposes. Moving to the second stage, pivotal features extracted by the initial CNN stage are utilized to represent the data comprehensively. The classification task is then undertaken by the SVM ML algorithm. Renowned for its adeptness at categorizing data using hyperplanes, SVM facilitates effective separation of data into distinct categories as binary classification [53] as shown in Table 4. The study also touches on the concept of ELM [54], which serves as an interesting avenue that can enhance the performance of the hybrid model. It is one of the deep learning algorithms that are characterized by speed and performance in classification, as it works without modifications during the training phase, unlike other traditional methods, where the number of neurons is determined within the hidden layers, and this is what distinguishes it because it assigns weights that link between the input layers and the hidden layers, and therefore, does not need to adjust parameters a lot, and if we look at it when it consists of a NN that contains one hidden layer, let us assume we have S arbitrary samples
Pseudocode for implementing the CNN-SVM model
| Pseudocode for implementing the CNN-SVM model |
|---|
| Begin |
| //Construct a CNN modeldef CNN generate ():CNN_model = Sequential () # Construct a sequential model#Convolution layerCNN_model.add (Conv1D (32, (3,3), input_shape = X_train. shape [1], 1))CNN_model.add (Activation (‘relu’)) #Convolution functionCNN_model.add (MaxPool1D (pool_size = (2,2)) #Subsampling layerCNN_model.add (Conv1D (64, (3,3), input_shape = X_train. shape [1], 1))CNN_model.add (Activation (‘relu’)) #Convolution functionCNN_model.add (MaxPool1D (pool_size = (2,2)) #Subsampling layerCNN_model.add (Conv1D (128, (3,3), input_shape = X_train. shape [1], 1))CNN_model.add (Activation (‘relu’)) #Convolution functionCNN_model.add (GlobalMaxPool1D () #Subsampling layerCNN_model.add (Flatten ())# Fully connected layerCNN_model.add (Dense (512)), Activation (‘relu’)CNN_model.add (nb_classes), Activation = ‘Sigmoid’…# Model compilationCNN_model.add (optimizer = ‘Adam’, loss = ‘binary_crossentropy’)# Construct the SVM classification modeldef SVM_model_generate (cnn_features_train, target_train): // CNN-SVM Attacks classification (Determine if the attack Malicious or Benign) End |
If we have K nodes hidden layer, then the NN containing one hidden layer is expressed in formula (2):
where
3.5 Performance assessment
The performance evaluation of the model unfolds through the lens of the confusion matrix, shown in Table 5. To compare and evaluate a model’s performance, a test dataset was applied to estimate the performance metrics: accuracy, specificity, sensitivity, and F1-score. These estimates were calculated using the number of True Positives (TPs), True Negatives (TNs), FPs, and False Negatives (FNs) resulting from applying an undertaken model to the test dataset, as explained in equations (2)–(6).
Confusion matrix
| Prediction | |||
|---|---|---|---|
| Positive | Negative | ||
| Actual | Positive | Number of TPs | Number of FNs |
| Negative | Number of FPs | Number of TNs | |
In this study, TPs show that the model’s perceptiveness is breathtakingly precise, with its discernment seamlessly coinciding with the reality at hand. It astutely identifies and classifies malicious IoT traffic, which is truly malicious, TNs come into play when the model exhibits its acumen by discerning and categorizing benign IoT traffic as exactly benign. This alignment mirrors the veritable actual classification, The FPs narrative is where the model falters a misstep in which it erroneously labels benign IoT traffic as malicious. This misjudgment births a disconcerting divergence, fueling misleading classification. In this study, several metrics were used to assess the performance of both the suggested and compared models, with accuracy being the most important. As described in equation (5), accuracy is the fraction of accurately anticipated instances compared to the total number of cases. Precision refers to TPs relative to TPs and FPs as shown in equation (6). Recall indicates the ratio of positive cases to FPs and FNs as indicated in equations (7) and F1-score refers to a measure of the level of precision and recall, which achieves a balanced scale of rating as presented in equation (8). Equation (9) shows the calculation of the error rate that results from the ratio of false predictions to the total.
The computation of the area under the receiver operating characteristic (ROC) curve (AUC) serves as a crucial numerical measure that enhances our understanding of the model’s capabilities. This supplementary metric occupies a central role in our study’s evaluation framework. An AUC value below 0.5 indicates that a classifier exhibits weaker performance. In the range of 0.7–0.8, a classifier falls within the spectrum of mediocrity and commendable performance – a zone denoting moderate achievement. Finally, the interval from 0.8 to 1 characterizes a classifier with excellent performance.
3.6 ML algorithms
Table 6 summarizes the working principle of each of the following ML algorithms: SVM, NB, KNN, and LR.
Classification algorithms working principle
| Classification model | Description |
|---|---|
| SVM | It is a powerful ML algorithm [55] that classifies both binary and multiclass, and separates data by important features using hyperplane [53] |
| KNN | It is a classification algorithm based on the majority vote for its nearest neighbor by assigning the value of K responsible for measuring the distance, where K is chosen through experiments [56] |
| LR | It is a statistical classification algorithm that depends on the logistic function in its classification and builds a relationship between the input features and the probability of a specific category [54] |
| NB | It is a probability-based algorithm that predicts strength between independent features and is widely used in the field of classification [58] |
4 Results and discussion
This section explains our results obtained from the CIC IoT 2023 exercise, which consist of a malicious DDoS attack, a DoS attack, and a benign attack, which were evaluated based on seven ML algorithms SVM, KNN, LR, NB, CNN, CNN + ELM and the proposed algorithm that combines CNN + SVM. Additionally, the suggested technique makes use of the hybrid CNN + SVM model to strengthen IoT devices’ defenses against evolving cyberthreats, creating an accurate environment for IoT applications.
4.1 Experiments
In this section, the basis of the proposed model presented in Table 7 shows the parameters used for our CNN + SVM model. Also, the proposed model was evaluated based on four other ML algorithms which are SVM, KNN, NB, and LR, where the data were divided into 80% for training and 20% for testing. All experiment in this study were conducted using Python tool on a laptop with i5-10H CPU, NVIDIA GeForce GTX 1660Ti 4GB, 8GB RAM, 250 GB SSD, and 1 TB HDD.
Parameters for training model
| Parameters | Function/value used |
|---|---|
| Loss function | Binary cross-entropy |
| Optimizer | Adam |
| Epochs | 50 |
| Activation | ReLU |
| Batch size | 32 |
4.2 Results analysis
A detailed summary of the model evaluation findings is given in Table 8. Based on the models’ F1-score, accuracy, precision, recall, and error rate percentages, they are compared. A boxplot of the performance metrics for each assessed model is shown in Figure 3. The table makes it evident that the CNN + SVM model is the most accurate and precise, showcasing its exceptional ability to classify instances with precision while maintaining a low error rate. The accuracy surged to an impressive 99.8%, matched by equally remarkable precision, recall, and F1-score values, all standing at 99%. Another noteworthy performance was recorded by the CNN + ELM model, with a promising accuracy of 99% alongside precision, recall, and F1-score scores of 99%. The SVM model secured solid results with an accuracy of 98%, while precision, recall, and F1-score held steady at 98, 97, and 98%, respectively. Figure 3 demonstrates the boxplot of performance metrics of different models.
Performance metrics of different models
| Model | Accuracy (%) | Precision (%) | Recall (%) | F1-score (%) | Error Rate (%) |
|---|---|---|---|---|---|
| SVM | 98 | 98 | 97 | 98 | 2.0 |
| NB | 96 | 95 | 96 | 95 | 4.0 |
| KNN | 97 | 96 | 98 | 97 | 3.0 |
| LR | 96 | 94 | 98 | 96 | 4.0 |
| CNN | 99 | 98 | 99 | 99 | 1.0 |
| CNN + ELM | 99 | 99 | 99 | 99 | 1.0 |
| CNN + SVM | 99.8 | 100 | 99 | 99 | 0.2 |

Boxplot of performance metrics of different models.
Meanwhile, the CNN model demonstrated a notable accuracy of 99%, while boasting precision, recall, and F1-score values of 98, 99, and 99%, respectively. In contrast, the KNN model showcased commendable results with a strong accuracy of 97%, while precision, recall, and F1-score were pegged at 96, 98, and 97%. On the other hand, LR and NB struggled to keep pace, sharing the lowest accuracy of 96%. For NB, this translated to precision, recall, and F1-score of 95, 96, and 95%, respectively. Meanwhile, LR exhibited a precision score of 94%, recall of 98%, and an F1-score of 96%. This powerful validation of our approach stems from the idea of merging features extracted from CNN and integrating them with the original features. This ingenious fusion, coupled with the utilization of the SVM classifier on an authentic IoT attack dataset, yielded results that hold immense promise. The practicality of utilizing real-world IoT scenarios, with actual devices assuming both attacking and victim roles, underscores the potential of these findings in bolstering the development of security analytics applications within real IoT operations. Figure 4 presents with a straightforward visual depiction of how our models fared. A swift assessment of the outcomes distinctly highlights the dominance of the (CNN + SVM) model, outshining all other algorithms. Close on its heels are three contenders CNN, CNN + ELM, and SVM each equally promising performances, all clocking in at an accuracy of 98%. The KNN model secures its place at an accuracy of 97%. Finally, we see the NB and LR models rounding off the chart, both achieving an accuracy of 96%.

Performance metrics of different models.
Figure 5 presents a visual depiction that lays out the training and validation accuracy, alongside the training and validation loss of the CNN model that underwent meticulous training on our dataset. The aim behind this endeavor encompassed extracting pivotal features from the dataset over the course of 20 epochs. The outcome of this endeavor is nothing short of remarkable training accuracy that soared to an impressive 99.45%. A noteworthy point arises when we closely examine the validation accuracy, as it hovered tantalizingly close to the 98.7% mark during the final epoch. This achievement distinctly underscores the robustness embedded within our proposed methodology. Moreover, a truly remarkable observation surfaces when we consider the validation loss. It experienced a staggering drop, plummeting to an almost negligible value of 0.04 at the 20 epochs. This revelation serves as a powerful testament to the efficacy of our approach. Collectively, these findings interlock to furnish a compelling body of evidence that attests to the effectiveness and promise deeply embedded within our chosen methodology.

(a) Training and validation accuracy and (b) training and validation loss.
Figure 6 presents the error rates associated with each model. These rates effectively reflect the percentage of accurate predictions made by each model, offering a complementary view to the concept of accuracy itself. To add depth to this understanding, Figure 6 complements the narrative by emphasizing the importance of lower error rates in elevating accuracy and overall effectiveness. Notably, our proposed model, the hybrid (CNN + SVM) configuration, emerges as the standout performer, boasting an impressive error rate of 1.0. This places it ahead of the other models, with the CNN model closely trailing at an error rate of 2.0, paralleled by the SVM model at the same error rate of 2.0. As the sequence unfolds, the KNN model enters the scene with an error rate of 3.0, while the two models, NB and LR, wrap up the series with the highest error rate of 4.0. The crux of these data lies in the stark contrast exhibited by the (CNN + SVM) model. Beyond its superior performance, it manages to underscore its prowess by maintaining a significantly lower error rate in comparison to its counterparts.
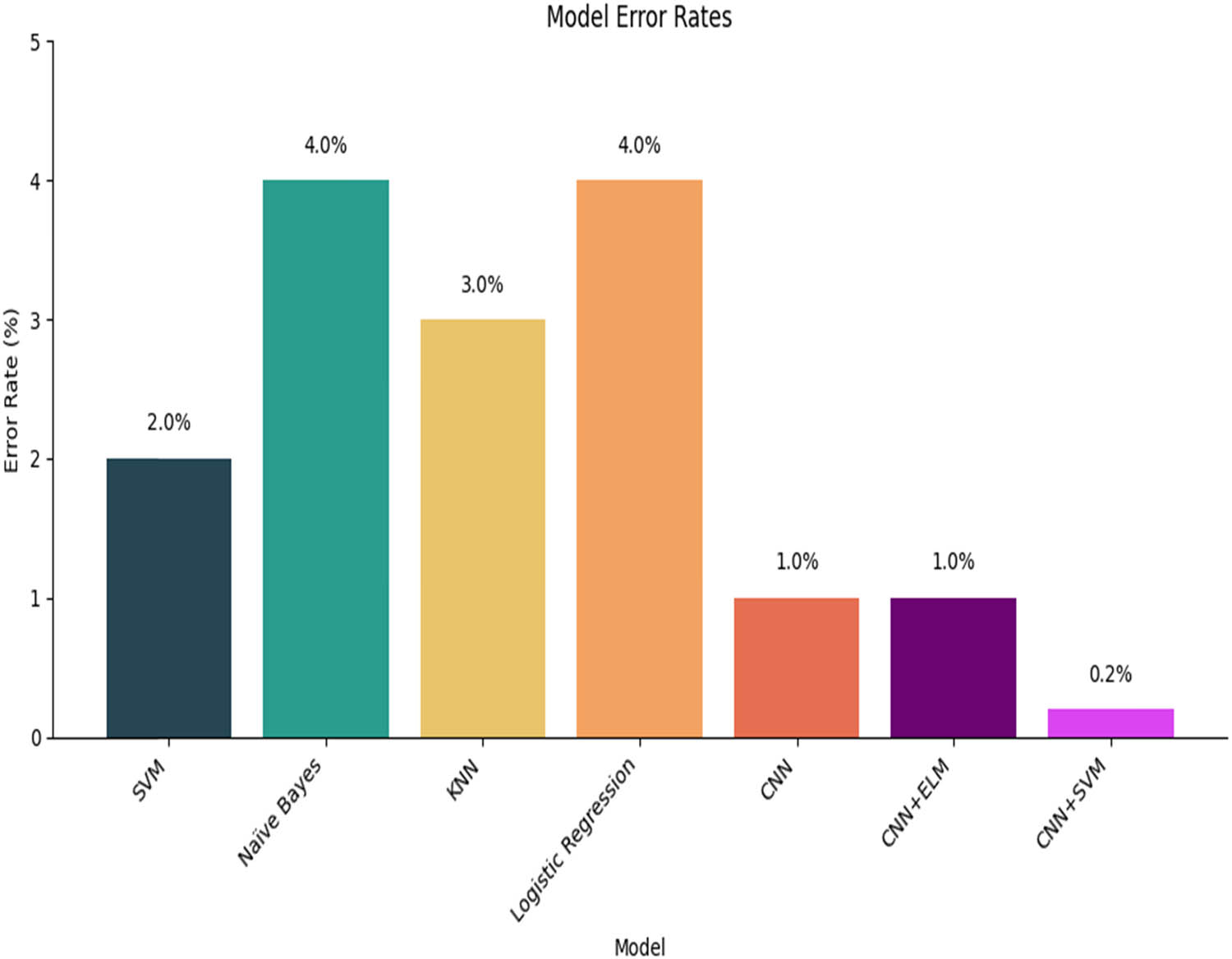
Error rates of different models for accuracy.
Figure 7 presents a confusion matrix that encompasses all the models employed for classification. What catches our attention is how our proposed model (CNN + SVM) stands out as a frontrunner in terms of accuracy and various performance metrics. It is worth noting that while other models also demonstrate their strengths, our (CNN + SVM) model truly shines. On the flip side, certain errors are observed in the classification performed by the LR and NB models. However, despite these results, when considering the practical landscape, they show substantial promise as compared to earlier research findings. In our analysis, we dedicated our efforts to evaluating the prowess of the (CNN + SVM) hybrid model, which outshines its counterparts in terms of effectiveness. Our focus zoomed in on the specific confusion matrix linked to the (CNN + SVM) model insights as the best model. This matrix played a pivotal role in gauging the model’s accuracy when it came to distinguishing between the realms of DoS and DDoS conditions.

A confusion matrix that encompasses all the models.
In our confusion matrix, we bore witness to the (CNN + SVM) model amassing an impressive tally of TPs in specific categories, a testament to its precision in making accurate forecasts. For instance, during this close inspection, the hybrid model’s commendable strength truly shone. It adeptly identified a substantial 3,399 instances as malicious attacks, aligning its affirmative “malicious” (positive) predictions remarkably well with the actual instances of malicious activities. This spotlights the model’s innate capacity to astutely detect and adeptly label genuine threats. The model’s proficiency further manifested as it correctly classified 3,413 instances as benign. These instances, tagged as “benign” (negative) by the model, impeccably harmonized with their genuinely harmless nature. This underscores the model’s finesse in meticulously discerning and categorizing routine activities. However, the model’s journey encountered an intriguing twist as it attempted to predict 42 instances of benign behavior. Contrary to the model’s classification of these instances as “benign” (negative), their actual intent was malicious. This revelation shines a light on instances where the model grappled with accurately identifying truly malicious actions. Our study’s findings found a poignant echo in the matrix’s narrative. While the hybrid model effectively attained notable TPs and TNs, emblematic of its precision in classification, sporadic instances of misclassification emerged as well.
Nevertheless, the hybrid model resounds with significant potential in reinforcing IoT device security by adeptly detecting and addressing the intricacies entailed in DoS and DDoS attacks.
It appears that the ROC curve is applied to various models as shown in Figure 8. The ROC curve is a graphical depiction illustrating a binary classification model’s performance at different classification thresholds. An AUC value of 1.0 signifies flawless classification performance. Both SVM and KNN models have a ROC curve AUC of 0.98, implying that these models demonstrate highly commendable performance. Moreover, the CNN + SVM model boasts an AUC of 0.999, indicating impeccable classification performance based on the ROC curve assessment. This compellingly underscores the model’s proficiency in accurately distinguishing between positive and negative instances.

ROC curve.
4.3 Discussion
In this section, we discuss the performance evaluation of various ML models for classifying IoT traffic as either malicious or benign. Our study successfully identifies models that exhibit strong performance in terms of accuracy, recall, F-score, and the AUC. The hallmark of our innovation lies in the seamless integration of CNN and SVM, a union meticulously orchestrated within our groundbreaking CNN + SVM framework. This fusion acts as an invigorating catalyst, consistently propelling us beyond the benchmarks set by our peers. Our model boasts an impressive accuracy rate of 99.8%, accompanied by precision, recall, and F1-score metrics of 100, 99, and 99%, respectively. These outcomes stand as a testament to the strength and efficacy embedded within our approach, affirming its proficiency in precise classification.
Table 9 offers a comprehensive comparison between our research and other related studies within the realm of intrusion detection. This table provides insights into each study’s research number, source, best model employed, and the corresponding accuracy achieved. The studies showcased encompass a diverse array of ML models, spanning from DNN, CNN, and SVM, to Smart Grid Networks, DBNs, and RF. This reflects the wide spectrum of methodologies explored within the intrusion detection field. The recurrent use of deep learning models such as DNN, CNN, and DBFs across various studies underscores their robust performance, highlighting the potential of deep learning in uncovering intricate patterns within network data. Worth noting is that some studies have chosen the same model more than once, amplifying the model’s proven efficacy. For instance, both Asad et al. [18] and Vinayakumar et al. [23] have leveraged the DNN model as their optimal choice, achieving notable accuracies of 98 and 99.2%, respectively. Similarly, SVM emerged as the preferred model in previous studies [20,22], yielding accuracies of 85 and 80%, respectively.
Comparison with related studies
| No. | Research | Best model | Best model (%) |
|---|---|---|---|
| 1 | [18] | DNN | 98 |
| 2 | [19] | CNN | 95.4 |
| 3 | [20] | SVM | 85 |
| 4 | [22] | SVM | 80 |
| 5 | [23] | DNN | 99.2 |
| 6 | [24] | Smart grid network | 97 |
| 7 | [25] | DNN | 97.59 |
| 6 | [26] | DBN | 97.93 |
| 9 | [27] | RF | 96.5 |
| 10 | Our Proposed | CNN + SVM | 99.8 |
Bold represents hybrid approach result in this paper.
However, it is our research that takes center stage in this comparative narrative. Through the ingenious fusion of CNN and SVM, we achieved an astonishing accuracy of 99.8%, as depicted in Figure 9. This bold amalgamation exemplifies how hybrid models can harness the strengths of both NNs and traditional ML methods, yielding unparalleled outcomes in accurately identifying intrusion patterns. Our research propels us forward, establishing new benchmarks in the realms of intrusion detection and network security. The comprehensive comparison detailed in Table 9 highlights the gradual evolution of methodologies, progressing from NNs to hybrid approaches. Our contribution, showcased by the CNN-SVM hybrid model, not only raises the bar for accuracy but also encapsulates the synergy between established and cutting-edge techniques. Through this comparative analysis, we embrace the essence of progress in fortifying network environments against evolving threats. Future research endeavors could delve into exploring the model’s adaptability to evolving attack strategies, along with strategies to enhance its resilience against adversarial attacks. Moreover, extending the model’s capabilities to encompass a broader array of attack types and subjecting it to real-world deployment scenarios would substantially validate its practical utility and robustness. Additionally, optimizing the model’s computational efficiency to cater to resource constrained IoT devices, coupled with the exploration of collaborative security mechanisms, holds the potential to pave the way for the development of more comprehensive and effective IoT security solutions. The outcomes of this study serve as a robust foundation for these future directions, contributing to the ongoing evolution of IoT security measures.

Comparison of our model with previous studies.
4.4 Trust of network (ToN)-IoT dataset
In this section, we also tested the proposed approach on another dataset to ensure scalability and to see how robust the proposed CNN-SVM model is against other attacks that may not have been present in the CIC IoT 2023 dataset.
The ToN-IoT dataset used in this study compiles a wide range of data from a whole industrial internet of things (IIoT) system. This comprises telemetry data from linked IoT devices, operational records from the Linux and Windows operating systems, and detailed network traffic data for the IIoT system. The dataset, created by UNSW Canberra IoT Labs and the Cyber Range, is formatted in CSV format and intended to reflect activities inside a medium-scale IoT network. Each entry in the dataset is labeled to indicate whether it corresponds to normal operations or attack behaviors, and includes a sub-category that identifies the type of attack ranging from ransomware, password attacks, and scanning to DDoS, data injection, backdoor, cross-site scripting (XSS), man-in-the-middle (MITM) attacks, and more.
The ToN-IoT dataset used in this study collects a wide range of data from a full IIoT system. This comprises telemetry data from linked IoT devices, operational records from the Linux and Windows operating systems, and detailed network traffic data particular to the IIoT system. The dataset, which was created by UNSW Canberra IoT Labs and the Cyber Range, is formatted in CSV format and intended to depict activities inside a medium-scale IoT network. Each entry in the dataset is labeled to indicate whether it corresponds to normal operations or attack behaviors, and includes a sub-category that identifies the type of attack – ranging from ransomware, password attacks, and scanning to DoS, DDoS, data injection, backdoor, XSS, MITM attacks, and more. This structure aids in the detailed analysis and identification of various threats launched against different IoT and IIoT sensors, with full details available in the ToN-IoT repository.
In our research, we verified the CNN-SVM model using the ToN-IoT dataset, achieving impressive performance metrics that demonstrate the resilience of our suggested approach. The confusion matrix, a critical tool for assessing the efficacy of classification models, exhibited excellent predictive power. Our model achieved an accuracy of 99.85%, suggesting that practically all predictions matched the actual classifications. Precision was calculated at 99.70%, demonstrating the model’s high level of accuracy in identifying TPs. Surprisingly, the model obtained a recall of 100%, indicating that all instances of targeted attacks in the test dataset were properly detected. Furthermore, the F1-score was 99.85%, demonstrating a balance between precision and recall (Figure 10).

Matrix of ToN-IoT dataset.
These indicators, particularly those derived from a complex and diverse set of IoT attack scenarios in the ToN-IoT dataset, demonstrate the model’s promise as a highly reliable tool for real-time threat identification in IoT systems.
4.5 Scalability considerations
In addressing the key feature of scalability for our CNN-SVM hybrid solution, we recognize the various needs and complexities of bigger IoT networks. Scalability in IoT security refers to the capacity to efficiently adapt to a rising number of devices while retaining high detection accuracy and low latency. Our solution, which is based on modular components, allows scalability by default due to its layered architecture. The CNN component enables feature extraction that may be efficiently parallelized across several devices or computational nodes, addressing the heterogeneous nature and volume of IoT traffic.
The subsequent SVM phase provides a robust classification mechanism that can be scaled vertically, depending on the complexity and volume of the detected features. While our current study does not empirically evaluate these scalability aspects, the theoretical underpinnings of our model suggest that by leveraging distributed computing resources and optimizing algorithmic efficiency, our approach could be extended to larger networks. Future work will aim to validate these scalability propositions through extensive testing across varied IoT environments, focusing on metrics such as throughput, detection time, and resource utilization to ensure the model’s effectiveness and efficiency at scale.
We adopted several essential measures to ensure that the CNN-SVM hybrid model is scalable and computationally efficient, making it appropriate for deployment in a variety of IoT scenarios. First, we created the model with a lightweight architecture that decreases computational burden and memory utilization, making it suitable for resource-constrained devices. This entails using optimized convolutional processes and fewer parameters to achieve high detection accuracy while reducing computing needs. Additionally, we used model compression approaches including pruning and quantization. Pruning helped eliminate extraneous model weights, and quantization reduced the precision of the numerical parameters, resulting in a substantially smaller model size and faster inference times. These adjustments are critical for deployment on devices with limited computing power.
To improve scalability, the model allows distributed computing, which distributes detection jobs among numerous IoT devices in the network. This technique not only takes advantage of the processing capability of several nodes, but it also minimizes data transmission burden, which is critical for system responsiveness and efficiency.
Furthermore, edge computing techniques were used to process data at the network’s edge, lowering latency and bandwidth consumption by removing the need to send data to centralized cloud servers. This local processing means that the model can quickly respond to attacks in real time, which is crucial for IoT security. Finally, we implemented incremental learning capabilities, which enable the model to dynamically react to new threats without requiring substantial retraining. This component ensures that the model stays successful when network behaviors and attack techniques change, ensuring its durability over time. These innovations collectively ensure that our CNN-SVM hybrid model not only meets the stringent criteria of IoT security in terms of detection accuracy but also tackles the practical obstacles of implementation in diverse IoT ecosystems, which are characterized by their diverse computational constraints.
In addition to the tactics described above, we evaluated our model’s scalability and efficiency by using an additional dataset throughout the training phase. This dataset, which simulates real-world IoT network traffic, was used to assess the robustness and adaptability of our CNN-SVM hybrid model across a variety of IoT scenarios. By training our model on a broader set of data, we demonstrated its capacity to efficiently manage a wide range of network conditions and attack behaviors. This method not only improves the generalizability of our model, but also demonstrates its potential to expand over a broader range of IoT networks without sacrificing computing efficiency. The successful application of our approach to numerous datasets emphasizes its potential for wider implementation in IoT devices with diverse processing capabilities, affirming our commitment to creating a scalable and computationally efficient security solution for the growing IoT landscape.
5 Conclusion
This study undertook a thorough and comprehensive evaluation of various machine-learning models, with the core objective of distinguishing between benign and malicious IoT traffic. A fresh approach to bolstering IoT device security was introduced, entailing the seamless integration of CNN and SVM techniques. The harmonious collaboration between CNN and SVM yielded an impressive accuracy rate of 99% in effectively detecting DoS and DDoS attacks. The empirical results extracted from our experiments offered compelling validation of the model’s efficacy in accurately identifying and categorizing both DoS and DDoS attacks. This accomplishment bears the potential to significantly enhance the security landscape within IoT environments. The success achieved in this endeavor holds promise for fortifying the resilience of IoT ecosystems. In future work, we are planning to use metaheuristic optimization algorithms to identify important features that achieve the best performance, while using machine and deep learning algorithms as a classifier along with the optimization algorithm. Also, we will use another modern dataset to validate the proposed model.
Acknowledgements
The research work is scientifically supported by Zarqa University, Zarqa 13110 Jordan.
-
Funding information: This research was supported by the Department of Computer Science, Faculty of Information Technology, Zarqa University, Zarqa 13110 Jordan.
-
Author contributions: Conceptualization: A.N., Q.A., and A.A.; formal analysis: Q.A., M.A., A.N., and R.A.; funding acquisition: M.A. and G.S.: investigation: A.N., Q.A., and H.G.; methodology: A.N., Q.A., H.G, and M.A.; resources: A.N., H.G., G.S.; supervision: M.A. and A.A.; validation: A.N., R.A., Q.A., A.J.; writing: Q.A., A.N., R.A., and M.A.; review and editing: A.N., G.S., R.A., A.J., and A.A.
-
Conflict of interest: The authors declare no conflict of interest.
-
Data availability statement: All datas are available in the following link https://www.unb.ca/cic/datasets/iotdataset-2023.html.
References
[1] Naik K, Patel S. An open source smart home management system based on IOT. Wirel Network. 2023;29:989–95. 10.1007/s11276-018-1884-z.Search in Google Scholar
[2] Venkatamune N, PrabhaShankar J. A VANET collision warning system with cloud aided pliable Q-Learning and safety message dissemination. Int Arab J Inf Technol. 2023;20(1):113–24.10.34028/iajit/20/1/12Search in Google Scholar
[3] Saied O, Kaiwartya O, Aljaidi M, Kumar S, Mahmud M, Kharel R, et al. LiNEV: visible light networking for connected vehicles. Photonics. 2023;10(8):925MDPI.10.3390/photonics10080925Search in Google Scholar
[4] Al-Emran M, Malik SI, Al-Kabi MN. A survey of internet of things (IoT) in education: opportunities and challenges. In A. Hassanien, R. Bhatnagar, N. Khalifa, & M. Taha (Eds.), Toward social internet of things (SIoT): Enabling technologies, architectures and applications. Studies in Computational Intelligence, vol. 846. Springer, Cham. 10.1007/978-3-030-24513-9_12.Search in Google Scholar
[5] Manderna A, Kumar S, Dohare U, Aljaidi M, Kaiwartya O, Lloret J. Vehicular network intrusion detection using a cascaded deep learning approach with multi-variant metaheuristic. Sensors. 2023;23(21):8772.10.3390/s23218772Search in Google Scholar PubMed PubMed Central
[6] Quttoum AN, Alsarhan A, Aljaidi M, Alshammari M. PLUG: A city-friendly navigation model for electric vehicles with power load balancing upon the grid. World Electr Veh J. 2023;14(12):338.10.3390/wevj14120338Search in Google Scholar
[7] Hussain SA, Yusof KM, Hussain SM, Singh AV. A review of quality of service issues in internet of vehicles (IoV). Proceeding – 2019 Amity International Conference on Artificial Intelligence. AICAI; 2019. p. 380–3. 10.1109/AICAI.2019.8701299.Search in Google Scholar
[8] Yaduwanshi R, Kumar S, Kumar A, Kaiwartya O, Aljaidi M, Lloret J. Efficient route planning using temporal reliance of link quality for highway IoV traffic environment. Electronics. 2022;12(1):130.10.3390/electronics12010130Search in Google Scholar
[9] Strecker S, Dave R, Siddiqui N, Seliya N. A modern analysis of aging machine learning based IoT Cybersecurity methods. J Comput Sci Appl. 2021;9(1):16–22. 10.12691/jcsa-9-1-2.Search in Google Scholar
[10] Snehi M, Bhandari A. Vulnerability retrospection of security solutions for software-defined cyber-physical system against DDoS and IoT-DDoS attacks. Comput Sci Rev. 2021;40:100371. 10.1016/j.cosrev.2021.100371.Search in Google Scholar
[11] Aljaidi M, Alsarhan A, Samara G, Alazaidah R, Almatarneh S, Khalid M, et al. NHS wannaCry ransomware attack: technical explanation of the vulnerability, exploitation, and countermeasures. 2022 International Engineering Conference on Electrical, Energy, and Artificial Intelligence (EICEEAI). IEEE; 2022. p. 1–6.10.1109/EICEEAI56378.2022.10050485Search in Google Scholar
[12] Aljaidi M, Alsarhan A, Samara G, AL-Khassawneh YA, Al-Gumaei YA, Aljawawdeh H, et al. A critical evaluation of a recent cybersecurity attack on itunes software updater. In 2022 International Engineering Conference on Electrical, Energy, and Artificial Intelligence (EICEEAI). IEEE; 2022. p. 1–6.10.1109/EICEEAI56378.2022.10050464Search in Google Scholar
[13] “What is The CIA TRAID & its important for Cybersecurity,” https://websitesecuritystore.com/blog/what-is-the-cia-triad, 2021, [Online; accessed 18 Augest 2021].Search in Google Scholar
[14] Elsayed N, ElSayed Z, Bayoumi M. IoT Botnet Detection Using an Economic Deep Learning model. In 2023 IEEE World AI IoT Congress (AIIoT). IEEE; 2023. p. 0134–0142.10.1109/AIIoT58121.2023.10174322Search in Google Scholar
[15] Kumar A, Kumar SA, Dutt V, Dubey AK, Narang S. A hybrid secure cloud platform maintenance based on improved attribute-based encryption strategies. Int J Interact Multimed Artif Intell. 2023;8(2):150–7.10.9781/ijimai.2021.11.004Search in Google Scholar
[16] Shih E, Cho SH, Ickes N, Min R, Sinha A, Wang A, et al. Physical layer driven protocol and algorithm design for energy-efficient wireless sensor networks. In Proceedings of the 7th annual international conference on Mobile computing and networking; 2001. p. 272–87. 10.1145/381677.381703.Search in Google Scholar
[17] Neto ECP, Dadkhah S, Ferreira R, Zohourian A, Lu R, Ghorbani AA. CICIoT2023: A real-time dataset and benchmark for large-scale attacks in IoT environment. Sensors. 2023;23:5941.10.3390/s23135941Search in Google Scholar PubMed PubMed Central
[18] Asad M, Asim M, Javed T, Beg MO, Mujtaba H, Abbas S. DeepDetect: Detection of distributed denial of service attacks using deep learning. Comput J. 2021;63(7):983–94. 10.1093/COMJNL/BXZ064.Search in Google Scholar
[19] de Assis MVO, Carvalho LF, Rodrigues JJPC, Lloret J, Proença ML. Near real-time security system applied to SDN environments in IoT networks using convolutional neural network. Comput Electr Eng. 2020;86:1–16. 10.1016/j.compeleceng.2020.106738.Search in Google Scholar
[20] Sudar KM, Beulah M, Deepalakshmi P, Nagaraj P, Chinnasamy P. Detection of distributed denial of service attacks in SDN using machine learning techniques. 2021 International Conference on Computer Communication and Informatics (ICCCI); 2021. p. 0–4. 10.1109/ICCCI50826.2021.9402517.Search in Google Scholar
[21] Xiao L, Wan X, Lu X, Zhang Y, Wu D. IoT security techniques based on machine learning: How do IoT devices use AI to enhance security?. IEEE Signal Process Mag. 2018;35(5):41–9.10.1109/MSP.2018.2825478Search in Google Scholar
[22] Meti N, Narayan DG, Baligar VP. Detection of distributed denial of service attacks using machine learning algorithms in software defined networks. 2017 International Conference on Advances in Computing, Communication and Informatics, ICACCI 2017; 2017. p. 1366–71. 10.1109/ICACCI.2017.8126031.Search in Google Scholar
[23] Vinayakumar R, Alazab M, Soman KP, Poornachandran P, Al-Nemrat A, Venkatraman S. Deep learning approach for intelligent intrusion detection system. IEEE Access. 2019;7:41525–50. 10.1109/ACCESS.2019.2895334.Search in Google Scholar
[24] Ali S, Li Y. Learning multilevel auto-encoders for DDOS attack detection in smart grid network. IEEE Access. 2019;7:108647–59. 10.1109/ACCESS.2019.2933304.Search in Google Scholar
[25] Makuvaza A, Jat DS, Gamundani AM. Deep neural network (DNN) solution for real-time detection of distributed denial of service (DDoS) attacks in software defined networks (SDNs). SN Comput Sci. 2021;2(2):1–10. 10.1007/s42979-021-00467-1.Search in Google Scholar
[26] Manimurugan S, Al-Mutairi S, Aborokbah MM, Chilamkurti N, Ganesan S, Patan R. Effective attack detection in internet of medical things smart environment using a deep belief neural network. IEEE Access. 2020;8:77396–404. 10.1109/ACCESS.2020.2986013.Search in Google Scholar
[27] Bindra N, Sood M. Detecting DDoS attacks using machine learning techniques and contemporary intrusion detection dataset. Autom Control Comput Sci. 2019;53(5):419–28. 10.3103/S0146411619050043.Search in Google Scholar
[28] Bhayo J, Shah SA, Hameed S, Ahmed A, Nasir J, Draheim D. Towards a machine learning-based framework for DDOS attack detection in software-defined IoT (SD-IoT) networks. Eng Appl Artif Intell. 2022;123:106432. 10.1016/j.engappai.2023.106432.Search in Google Scholar
[29] Wei Y, Jang-Jaccard J, Sabrina F, Singh A, Xu W, Camtepe S. AE-MLP: A hybrid deep learning approach for DDoS detection and classification. IEEE Access. 2021;9:146810–21. 10.1109/ACCESS.2021.3123791.Search in Google Scholar
[30] Sinthuja M, Suthendran K. DDoS attack detection using enhanced long-short term memory with hybrid machine learning algorithms. 3rd International Conference on Smart Electronics and Communication (ICOSEC 2022); 2022. p. 1213–8. 10.1109/ICOSEC54921.2022.9951976.Search in Google Scholar
[31] Can DC, Le HQ, Ha QT. Detection of distributed denial of service attacks using automatic feature selection with enhancement for imbalance dataset. In Intelligent Information and Database Systems: 13th Asian Conference, ACIIDS 2021, Phuket, Thailand, April 7–10, 2021, Proceedings 13 (pp. 386–398). Springer International Publishing.10.1007/978-3-030-73280-6_31Search in Google Scholar
[32] Aswad FM, Ahmed AMS, Alhammadi NAM, Khalaf BA, Mostafa SA. Deep learning in distributed denial-of-service attacks detection method for Internet of Things networks. J Intell Syst. 2023;32(1):20220155.10.1515/jisys-2022-0155Search in Google Scholar
[33] Varghese A, Muraleedharan Sylaja M, Kurian J. Conception and realization of an IoT-enabled deep CNN decision support system for automated arrhythmia classification. J Intell Syst. 2022;31(1):407–19.10.1515/jisys-2022-0015Search in Google Scholar
[34] Aswad FM, Kareem AN, Khudhur AM, Khalaf BA, Mostafa SA. Tree-based machine learning algorithms in the Internet of Things environment for multivariate flood status prediction. J Intell Syst. 2021;31(1):1–14.10.1515/jisys-2021-0179Search in Google Scholar
[35] Singh S, Sharma PK, Moon SY, Park JH. Advanced lightweight encryption algorithms for IoT devices: survey, challenges and solutions. J Ambient Intell Humaniz Comput. 2024;15:1625–42. 10.1007/s12652-017-0494-4.Search in Google Scholar
[36] Patro SGK, Sahu KK. Normalization: a preprocessing stage. Iarjset. 2015;2(3):20–2. 10.17148/iarjset.2015.2305.Search in Google Scholar
[37] Meidan Y, Bohadana M, Shabtai A, Ochoa M, Tippenhauer NO, Guarnizo J, et al. Detection of Unauthorized IoT Devices Using Machine Learning Techniques; 2017. http://arxiv.org/abs/1709.04647.Search in Google Scholar
[38] Ngo QD, Nguyen HT, Le VH, Nguyen DH. A survey of IoT malware and detection methods based on static features. ICT Express. 2020;6(4):280–6. 10.1016/j.icte.2020.04.005.Search in Google Scholar
[39] Sharma N, Shamkuwar M, Singh I. The history, present and future with IOT. Intell Syst Ref Libr. 2019;154:27–51. 10.1007/978-3-030-04203-5_3.Search in Google Scholar
[40] Minerva R, Lee GM, Crespi N. Digital twin in the IoT context: a survey on technical features, scenarios, and architectural models. Proc IEEE. 2020;108(10):1785–824. 10.1109/JPROC.2020.2998530.Search in Google Scholar
[41] Stiawan D, Wahyudi D, Septian TW, Idris MY, Budiarto R. The development of an internet of things (IoT) network traffic dataset with simulated attack data. J Internet Technol. 2023;24(2):345–56. 10.53106/160792642023032402013.Search in Google Scholar
[42] Shaaban AR, Abdelwaness E, Hussein M. TCP and HTTP Flood DDOS attack analysis and detection for space ground network. 2019 IEEE Int. Conf. Veh. Electron. Safety, ICVES 2019; 2019. p. 1–6. 10.1109/ICVES.2019.8906302.Search in Google Scholar
[43] Gaurav A, Gupta BB, Alhalabi W, Visvizi A, Asiri Y. A comprehensive survey on DDoS attacks on various intelligent systems and it’s defense techniques. Int J Intell Syst. 2022;37(12):11407–31. 10.1002/int.23048.Search in Google Scholar
[44] Swami R, Dave M, Ranga V. Detection and analysis of TCP-SYN DDoS attack in software-defined networking. Wirel Pers Commun. 2021;118(4):2295–317. 10.1007/s11277-021-08127-6.Search in Google Scholar
[45] Evmorfos S, Vlachodimitropoulos G, Bakalos N, Gelenbe E. Neural network architectures for the detection of SYN flood attacks in IoT systems. The ACM International Conference Proceeding Series; 2020. p. 495–8. 10.1145/3389189.3398000.Search in Google Scholar
[46] Doss AN, Shah D, Smaisim GF, Olha M, Jaiswal S. A comprehensive analysis of Internet of Things (IOT) in enhancing data security for better system integrity - a critical analysis on the security attacks and relevant countermeasures. In 2022 2nd International Conference on Advance Computing and Innovative Technologies in Engineering (ICACITE). IEEE; 2022, April. p. 165–7.10.1109/ICACITE53722.2022.9823817Search in Google Scholar
[47] Rao PM, Deebak BD. A comprehensive survey on authentication and secure key management in internet of things: challenges, countermeasures, and future directions. Ad Hoc Network. 2023;146:103159.10.1016/j.adhoc.2023.103159Search in Google Scholar
[48] Altulaihan E, Almaiah MA, Aljughaiman A. Cybersecurity threats, countermeasures and mitigation techniques on the IoT: future research directions. Electronics. 2022;11(20):3330.10.3390/electronics11203330Search in Google Scholar
[49] Aldahmani A, Ouni B, Lestable T, Debbah M. Cyber-security of embedded IoTs in smart homes: challenges, requirements, countermeasures, and trends. IEEE Open J Veh Technol. 2023;4:281–92.10.1109/OJVT.2023.3234069Search in Google Scholar
[50] Mishra V. IoT: Emerging technologies-challenges and countermeasures. Eduzone: Int Peer Rev/Ref Multidiscip J. 2022;11(2):336–40.Search in Google Scholar
[51] Sadhu PK, Yanambaka VP, Abdelgawad A. Internet of things: Security and solutions survey. Sensors. 2022;22(19):7433.10.3390/s22197433Search in Google Scholar PubMed PubMed Central
[52] Alam H, Tomai E. Security attacks and countermeasures in smart homes. Int J Cybern Inform (IJCI). 2023;12(12):109.10.5121/ijci.2023.120209Search in Google Scholar
[53] Al Mamlook RE, Nasayreh A, Gharaibeh H, Shrestha S. Classification of cancer genome atlas glioblastoma multiform (TCGA-GBM) using machine learning method. IEEE International Conference on Electro/Information Technology; 2023. p. 265–70. 10.1109/eIT57321.2023.10187283.Search in Google Scholar
[54] Huang GB, Zhu QY, Siew CK. Extreme learning machine: theory and applications. Neurocomputing. 2006;70(1–3):489–501.10.1016/j.neucom.2005.12.126Search in Google Scholar
[55] Vishwanathan SVN, Murty MN. SSVM: A simple SVM algorithm. Proceedings of the International Joint Conference on Neural Networks. Vol. 3, No. 1, 2002. p. 2393–8. 10.1109/ijcnn.2002.1007516.Search in Google Scholar
[56] Zhang S, Li X, Zong M, Zhu X, Cheng D. Learning k for kNN Classification. ACM Trans Intell Syst Technol. 2017;8(3):1–19. 10.1145/2990508.Search in Google Scholar
[57] LaValley MP. Logistic regression. Circulation. 2008;117(18):2395–9. 10.1161/CIRCULATIONAHA.106.682658.Search in Google Scholar PubMed
[58] Sulzmann JN, Fürnkranz J, Hüllermeier E. On pairwise naive bayes classifiers. In European conference on machine learning. Berlin, Heidelberg: Springer Berlin Heidelberg; 2007. p. 371–81.10.1007/978-3-540-74958-5_35Search in Google Scholar
© 2024 the author(s), published by De Gruyter
This work is licensed under the Creative Commons Attribution 4.0 International License.
Articles in the same Issue
- Research Articles
- A study on intelligent translation of English sentences by a semantic feature extractor
- Detecting surface defects of heritage buildings based on deep learning
- Combining bag of visual words-based features with CNN in image classification
- Online addiction analysis and identification of students by applying gd-LSTM algorithm to educational behaviour data
- Improving multilayer perceptron neural network using two enhanced moth-flame optimizers to forecast iron ore prices
- Sentiment analysis model for cryptocurrency tweets using different deep learning techniques
- Periodic analysis of scenic spot passenger flow based on combination neural network prediction model
- Analysis of short-term wind speed variation, trends and prediction: A case study of Tamil Nadu, India
- Cloud computing-based framework for heart disease classification using quantum machine learning approach
- Research on teaching quality evaluation of higher vocational architecture majors based on enterprise platform with spherical fuzzy MAGDM
- Detection of sickle cell disease using deep neural networks and explainable artificial intelligence
- Interval-valued T-spherical fuzzy extended power aggregation operators and their application in multi-criteria decision-making
- Characterization of neighborhood operators based on neighborhood relationships
- Real-time pose estimation and motion tracking for motion performance using deep learning models
- QoS prediction using EMD-BiLSTM for II-IoT-secure communication systems
- A novel framework for single-valued neutrosophic MADM and applications to English-blended teaching quality evaluation
- An intelligent error correction model for English grammar with hybrid attention mechanism and RNN algorithm
- Prediction mechanism of depression tendency among college students under computer intelligent systems
- Research on grammatical error correction algorithm in English translation via deep learning
- Microblog sentiment analysis method using BTCBMA model in Spark big data environment
- Application and research of English composition tangent model based on unsupervised semantic space
- 1D-CNN: Classification of normal delivery and cesarean section types using cardiotocography time-series signals
- Real-time segmentation of short videos under VR technology in dynamic scenes
- Application of emotion recognition technology in psychological counseling for college students
- Classical music recommendation algorithm on art market audience expansion under deep learning
- A robust segmentation method combined with classification algorithms for field-based diagnosis of maize plant phytosanitary state
- Integration effect of artificial intelligence and traditional animation creation technology
- Artificial intelligence-driven education evaluation and scoring: Comparative exploration of machine learning algorithms
- Intelligent multiple-attributes decision support for classroom teaching quality evaluation in dance aesthetic education based on the GRA and information entropy
- A study on the application of multidimensional feature fusion attention mechanism based on sight detection and emotion recognition in online teaching
- Blockchain-enabled intelligent toll management system
- A multi-weapon detection using ensembled learning
- Deep and hand-crafted features based on Weierstrass elliptic function for MRI brain tumor classification
- Design of geometric flower pattern for clothing based on deep learning and interactive genetic algorithm
- Mathematical media art protection and paper-cut animation design under blockchain technology
- Deep reinforcement learning enhances artistic creativity: The case study of program art students integrating computer deep learning
- Transition from machine intelligence to knowledge intelligence: A multi-agent simulation approach to technology transfer
- Research on the TF–IDF algorithm combined with semantics for automatic extraction of keywords from network news texts
- Enhanced Jaya optimization for improving multilayer perceptron neural network in urban air quality prediction
- Design of visual symbol-aided system based on wireless network sensor and embedded system
- Construction of a mental health risk model for college students with long and short-term memory networks and early warning indicators
- Personalized resource recommendation method of student online learning platform based on LSTM and collaborative filtering
- Employment management system for universities based on improved decision tree
- English grammar intelligent error correction technology based on the n-gram language model
- Speech recognition and intelligent translation under multimodal human–computer interaction system
- Enhancing data security using Laplacian of Gaussian and Chacha20 encryption algorithm
- Construction of GCNN-based intelligent recommendation model for answering teachers in online learning system
- Neural network big data fusion in remote sensing image processing technology
- Research on the construction and reform path of online and offline mixed English teaching model in the internet era
- Real-time semantic segmentation based on BiSeNetV2 for wild road
- Online English writing teaching method that enhances teacher–student interaction
- Construction of a painting image classification model based on AI stroke feature extraction
- Big data analysis technology in regional economic market planning and enterprise market value prediction
- Location strategy for logistics distribution centers utilizing improved whale optimization algorithm
- Research on agricultural environmental monitoring Internet of Things based on edge computing and deep learning
- The application of curriculum recommendation algorithm in the driving mechanism of industry–teaching integration in colleges and universities under the background of education reform
- Application of online teaching-based classroom behavior capture and analysis system in student management
- Evaluation of online teaching quality in colleges and universities based on digital monitoring technology
- Face detection method based on improved YOLO-v4 network and attention mechanism
- Study on the current situation and influencing factors of corn import trade in China – based on the trade gravity model
- Research on business English grammar detection system based on LSTM model
- Multi-source auxiliary information tourist attraction and route recommendation algorithm based on graph attention network
- Multi-attribute perceptual fuzzy information decision-making technology in investment risk assessment of green finance Projects
- Research on image compression technology based on improved SPIHT compression algorithm for power grid data
- Optimal design of linear and nonlinear PID controllers for speed control of an electric vehicle
- Traditional landscape painting and art image restoration methods based on structural information guidance
- Traceability and analysis method for measurement laboratory testing data based on intelligent Internet of Things and deep belief network
- A speech-based convolutional neural network for human body posture classification
- The role of the O2O blended teaching model in improving the teaching effectiveness of physical education classes
- Genetic algorithm-assisted fuzzy clustering framework to solve resource-constrained project problems
- Behavior recognition algorithm based on a dual-stream residual convolutional neural network
- Ensemble learning and deep learning-based defect detection in power generation plants
- Optimal design of neural network-based fuzzy predictive control model for recommending educational resources in the context of information technology
- An artificial intelligence-enabled consumables tracking system for medical laboratories
- Utilization of deep learning in ideological and political education
- Detection of abnormal tourist behavior in scenic spots based on optimized Gaussian model for background modeling
- RGB-to-hyperspectral conversion for accessible melanoma detection: A CNN-based approach
- Optimization of the road bump and pothole detection technology using convolutional neural network
- Comparative analysis of impact of classification algorithms on security and performance bug reports
- Cross-dataset micro-expression identification based on facial ROIs contribution quantification
- Demystifying multiple sclerosis diagnosis using interpretable and understandable artificial intelligence
- Unifying optimization forces: Harnessing the fine-structure constant in an electromagnetic-gravity optimization framework
- E-commerce big data processing based on an improved RBF model
- Analysis of youth sports physical health data based on cloud computing and gait awareness
- CCLCap-AE-AVSS: Cycle consistency loss based capsule autoencoders for audio–visual speech synthesis
- An efficient node selection algorithm in the context of IoT-based vehicular ad hoc network for emergency service
- Computer aided diagnoses for detecting the severity of Keratoconus
- Improved rapidly exploring random tree using salp swarm algorithm
- Network security framework for Internet of medical things applications: A survey
- Predicting DoS and DDoS attacks in network security scenarios using a hybrid deep learning model
- Enhancing 5G communication in business networks with an innovative secured narrowband IoT framework
- Quokka swarm optimization: A new nature-inspired metaheuristic optimization algorithm
- Digital forensics architecture for real-time automated evidence collection and centralization: Leveraging security lake and modern data architecture
- Image modeling algorithm for environment design based on augmented and virtual reality technologies
- Enhancing IoT device security: CNN-SVM hybrid approach for real-time detection of DoS and DDoS attacks
- High-resolution image processing and entity recognition algorithm based on artificial intelligence
- Review Articles
- Transformative insights: Image-based breast cancer detection and severity assessment through advanced AI techniques
- Network and cybersecurity applications of defense in adversarial attacks: A state-of-the-art using machine learning and deep learning methods
- Applications of integrating artificial intelligence and big data: A comprehensive analysis
- A systematic review of symbiotic organisms search algorithm for data clustering and predictive analysis
- Modelling Bitcoin networks in terms of anonymity and privacy in the metaverse application within Industry 5.0: Comprehensive taxonomy, unsolved issues and suggested solution
- Systematic literature review on intrusion detection systems: Research trends, algorithms, methods, datasets, and limitations
Articles in the same Issue
- Research Articles
- A study on intelligent translation of English sentences by a semantic feature extractor
- Detecting surface defects of heritage buildings based on deep learning
- Combining bag of visual words-based features with CNN in image classification
- Online addiction analysis and identification of students by applying gd-LSTM algorithm to educational behaviour data
- Improving multilayer perceptron neural network using two enhanced moth-flame optimizers to forecast iron ore prices
- Sentiment analysis model for cryptocurrency tweets using different deep learning techniques
- Periodic analysis of scenic spot passenger flow based on combination neural network prediction model
- Analysis of short-term wind speed variation, trends and prediction: A case study of Tamil Nadu, India
- Cloud computing-based framework for heart disease classification using quantum machine learning approach
- Research on teaching quality evaluation of higher vocational architecture majors based on enterprise platform with spherical fuzzy MAGDM
- Detection of sickle cell disease using deep neural networks and explainable artificial intelligence
- Interval-valued T-spherical fuzzy extended power aggregation operators and their application in multi-criteria decision-making
- Characterization of neighborhood operators based on neighborhood relationships
- Real-time pose estimation and motion tracking for motion performance using deep learning models
- QoS prediction using EMD-BiLSTM for II-IoT-secure communication systems
- A novel framework for single-valued neutrosophic MADM and applications to English-blended teaching quality evaluation
- An intelligent error correction model for English grammar with hybrid attention mechanism and RNN algorithm
- Prediction mechanism of depression tendency among college students under computer intelligent systems
- Research on grammatical error correction algorithm in English translation via deep learning
- Microblog sentiment analysis method using BTCBMA model in Spark big data environment
- Application and research of English composition tangent model based on unsupervised semantic space
- 1D-CNN: Classification of normal delivery and cesarean section types using cardiotocography time-series signals
- Real-time segmentation of short videos under VR technology in dynamic scenes
- Application of emotion recognition technology in psychological counseling for college students
- Classical music recommendation algorithm on art market audience expansion under deep learning
- A robust segmentation method combined with classification algorithms for field-based diagnosis of maize plant phytosanitary state
- Integration effect of artificial intelligence and traditional animation creation technology
- Artificial intelligence-driven education evaluation and scoring: Comparative exploration of machine learning algorithms
- Intelligent multiple-attributes decision support for classroom teaching quality evaluation in dance aesthetic education based on the GRA and information entropy
- A study on the application of multidimensional feature fusion attention mechanism based on sight detection and emotion recognition in online teaching
- Blockchain-enabled intelligent toll management system
- A multi-weapon detection using ensembled learning
- Deep and hand-crafted features based on Weierstrass elliptic function for MRI brain tumor classification
- Design of geometric flower pattern for clothing based on deep learning and interactive genetic algorithm
- Mathematical media art protection and paper-cut animation design under blockchain technology
- Deep reinforcement learning enhances artistic creativity: The case study of program art students integrating computer deep learning
- Transition from machine intelligence to knowledge intelligence: A multi-agent simulation approach to technology transfer
- Research on the TF–IDF algorithm combined with semantics for automatic extraction of keywords from network news texts
- Enhanced Jaya optimization for improving multilayer perceptron neural network in urban air quality prediction
- Design of visual symbol-aided system based on wireless network sensor and embedded system
- Construction of a mental health risk model for college students with long and short-term memory networks and early warning indicators
- Personalized resource recommendation method of student online learning platform based on LSTM and collaborative filtering
- Employment management system for universities based on improved decision tree
- English grammar intelligent error correction technology based on the n-gram language model
- Speech recognition and intelligent translation under multimodal human–computer interaction system
- Enhancing data security using Laplacian of Gaussian and Chacha20 encryption algorithm
- Construction of GCNN-based intelligent recommendation model for answering teachers in online learning system
- Neural network big data fusion in remote sensing image processing technology
- Research on the construction and reform path of online and offline mixed English teaching model in the internet era
- Real-time semantic segmentation based on BiSeNetV2 for wild road
- Online English writing teaching method that enhances teacher–student interaction
- Construction of a painting image classification model based on AI stroke feature extraction
- Big data analysis technology in regional economic market planning and enterprise market value prediction
- Location strategy for logistics distribution centers utilizing improved whale optimization algorithm
- Research on agricultural environmental monitoring Internet of Things based on edge computing and deep learning
- The application of curriculum recommendation algorithm in the driving mechanism of industry–teaching integration in colleges and universities under the background of education reform
- Application of online teaching-based classroom behavior capture and analysis system in student management
- Evaluation of online teaching quality in colleges and universities based on digital monitoring technology
- Face detection method based on improved YOLO-v4 network and attention mechanism
- Study on the current situation and influencing factors of corn import trade in China – based on the trade gravity model
- Research on business English grammar detection system based on LSTM model
- Multi-source auxiliary information tourist attraction and route recommendation algorithm based on graph attention network
- Multi-attribute perceptual fuzzy information decision-making technology in investment risk assessment of green finance Projects
- Research on image compression technology based on improved SPIHT compression algorithm for power grid data
- Optimal design of linear and nonlinear PID controllers for speed control of an electric vehicle
- Traditional landscape painting and art image restoration methods based on structural information guidance
- Traceability and analysis method for measurement laboratory testing data based on intelligent Internet of Things and deep belief network
- A speech-based convolutional neural network for human body posture classification
- The role of the O2O blended teaching model in improving the teaching effectiveness of physical education classes
- Genetic algorithm-assisted fuzzy clustering framework to solve resource-constrained project problems
- Behavior recognition algorithm based on a dual-stream residual convolutional neural network
- Ensemble learning and deep learning-based defect detection in power generation plants
- Optimal design of neural network-based fuzzy predictive control model for recommending educational resources in the context of information technology
- An artificial intelligence-enabled consumables tracking system for medical laboratories
- Utilization of deep learning in ideological and political education
- Detection of abnormal tourist behavior in scenic spots based on optimized Gaussian model for background modeling
- RGB-to-hyperspectral conversion for accessible melanoma detection: A CNN-based approach
- Optimization of the road bump and pothole detection technology using convolutional neural network
- Comparative analysis of impact of classification algorithms on security and performance bug reports
- Cross-dataset micro-expression identification based on facial ROIs contribution quantification
- Demystifying multiple sclerosis diagnosis using interpretable and understandable artificial intelligence
- Unifying optimization forces: Harnessing the fine-structure constant in an electromagnetic-gravity optimization framework
- E-commerce big data processing based on an improved RBF model
- Analysis of youth sports physical health data based on cloud computing and gait awareness
- CCLCap-AE-AVSS: Cycle consistency loss based capsule autoencoders for audio–visual speech synthesis
- An efficient node selection algorithm in the context of IoT-based vehicular ad hoc network for emergency service
- Computer aided diagnoses for detecting the severity of Keratoconus
- Improved rapidly exploring random tree using salp swarm algorithm
- Network security framework for Internet of medical things applications: A survey
- Predicting DoS and DDoS attacks in network security scenarios using a hybrid deep learning model
- Enhancing 5G communication in business networks with an innovative secured narrowband IoT framework
- Quokka swarm optimization: A new nature-inspired metaheuristic optimization algorithm
- Digital forensics architecture for real-time automated evidence collection and centralization: Leveraging security lake and modern data architecture
- Image modeling algorithm for environment design based on augmented and virtual reality technologies
- Enhancing IoT device security: CNN-SVM hybrid approach for real-time detection of DoS and DDoS attacks
- High-resolution image processing and entity recognition algorithm based on artificial intelligence
- Review Articles
- Transformative insights: Image-based breast cancer detection and severity assessment through advanced AI techniques
- Network and cybersecurity applications of defense in adversarial attacks: A state-of-the-art using machine learning and deep learning methods
- Applications of integrating artificial intelligence and big data: A comprehensive analysis
- A systematic review of symbiotic organisms search algorithm for data clustering and predictive analysis
- Modelling Bitcoin networks in terms of anonymity and privacy in the metaverse application within Industry 5.0: Comprehensive taxonomy, unsolved issues and suggested solution
- Systematic literature review on intrusion detection systems: Research trends, algorithms, methods, datasets, and limitations

