Abstract
In order to better realize the secret-related information monitoring system, an algorithm based on a nonlinear network is proposed and is combined with the traditional algorithm. This article mainly analyzes the theory of nonlinear networks, designs and trains new network parameters according to their own needs, and combines the nonlinear network as a feature extractor with the existing intrusion detection and wandering detection algorithms, which greatly improves the recognition ability of traditional algorithms. The main feature of a nonlinear network is that it can extract the positional features of objects from the network while also extracting object features, that is, positioning and classification are realized in the same network. As a feature extractor, this network can not only have a higher recognition rate than background difference, hog, and other algorithms but also have a greater ability to extract position information than other convolutional neural networks. The successful application of nonlinear production network systems in TV stations at all levels has greatly improved the editing and production capability and efficiency of TV programs. How to ensure the safe, reliable, stable, orderly, and efficient operation of nonlinear production network systems requires vendors and TVS Taiwan technical staff to jointly conduct in-depth research and summarize their findings. In this article, from the perspective of TV users, information components in nonlinear production network systems are analyzed, including class, title management mode, storage space management, material management, security management, and workflow management in nonlinear systems. Make some analysis, discussion, and summaries of network system and operation management problems. The experimental results show that the nonlinear algorithm in this article has a significant advantage over the original tracking algorithm; that is, most tracking algorithms do not have the ability of category recognition during the initial tracking process, which means that these tracking algorithms cannot accurately know what they are tracking. Because the nonlinear network has the ability to output categories, whether it is initial tracking or tracking loss recovery, nonlinearity has fundamentally better advantages than other tracking algorithms. Therefore, it can be predicted that there is a strong recognition ability in the later monitoring and wandering detection. It has been proved that the nonlinear algorithm can be effectively applied to the secret information monitoring system.
1 Introduction
The successful application of nonlinear production network systems at all levels of TV stations has greatly improved the editing and production capability and efficiency of TV programs. How to ensure the safe, reliable, stable, orderly, and efficient operation of nonlinear production network systems requires vendors and TVS Taiwan technical staff to jointly conduct in-depth research and summarize their findings. From the perspective of TV users, this paper analyzes the categories of information components, the management mode of titles, the management of storage space, security management and workflow management in the system.
Nowadays, the network is becoming more and more important, and its scale and complexity are becoming larger and larger. Only using access control, intrusion detection, network isolation, and virus prevention to solve external attacks and some local security cannot meet the needs of intranet security. The traditional security mechanism is no longer competent. Therefore, it is necessary to establish a perfect network information monitoring system in the intranet to capture, analyze, keyword match, query, and collect statistics on the information of the internal network so as to realize the monitoring of the internal information of the network and protect the intranet security that is usually ignored by people [1]. The network information monitoring system uses network monitoring technology to collect network data packets passing through fixed network nodes, analyze the data packets layer-by-layer according to the network protocol model, extract and analyze the data, find harmful information and confidential privacy information, and alert the administrator. The administrator can view the source of these harmful information through the system, close the access of internal network members to these harmful information on time, and locate and deal with internal information leakage on time to prevent unnecessary economic losses [2]. The management and security monitoring of classified places are widely used in various businesses of enterprises and institutions, colleges and universities, government organs, and military and police departments. It is related to the safety of various classified materials and equipment and plays a very important role in ensuring social stability, national security, and the safety of economic construction. Compared with the intelligent security of ordinary public places, the management and monitoring of secret-related places put forward higher requirements for intelligent technology because of the sensitivity of secret-related data and secret-related equipment. In enterprises and institutions, schools, government agencies, military and police departments, and other units, important materials of the unit are stored in secret places in the form of confidential files. The management and security monitoring of classified places and the management of confidential materials in classified places are related to the core interests of the state and enterprises [3]. At present, in order to ensure the safety of archives in secret-related places, the state and enterprises mostly adopt traditional means for the management of secret-related places, such as manual registration, regular inspection, and security monitoring day and night. On the one hand, these manual management methods are greatly affected by human factors, and the temporary negligence of monitoring personnel will bring heavy losses. The overall function of a network information monitoring system includes four modules: packet capture, packet analysis and storage, query statistics, and management. The data packet capture part includes preliminary filtering and capture; the data packet analysis part includes data packet analysis, keyword matching, and storage. The query and statistics part includes data querying, data extraction and analysis, and data flow statistics. The management part includes the management of the key word library and the management of the administrator account. The overall functional structure of the specific network information monitoring system is shown in Figure 1.
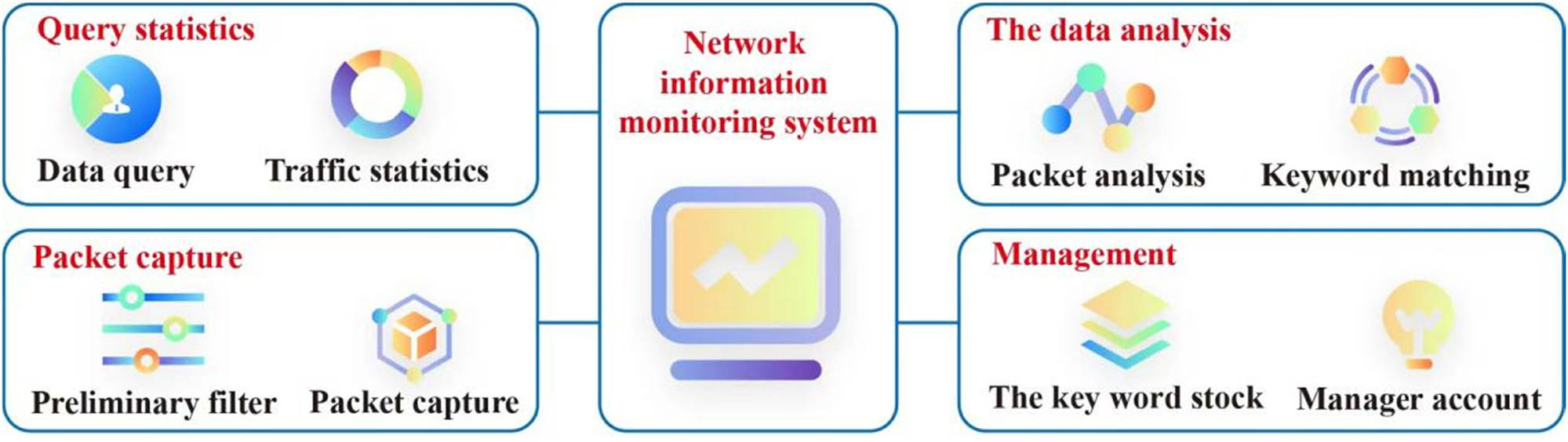
The overall functional structure of the network information monitoring system.
2 Literature review
In addition to the ability and efficiency of network system editing and production programs‚ the most important is how to solve the network system operation row management issues.
With the continuous development of network technology and the increasing complexity and heterogeneity of networks, especially with the emergence of distributed computing, network management has become a key technology of the computer network. Now, with the continuous improvement of network technology and application level, higher and higher requirements are put forward for network management, which also makes more and more enterprises realize that in addition to relying on the reliability of network equipment itself and network architecture, network management is a key link. Network systems with more and more complex structure and a larger scale need network management software to ensure the normal operation of the system [4]. Kong believes that the quality of network management will directly affect the operational quality of the network. Managing a network well is as important as its construction. Network management has been the key factor to ensure the normal operation of computer networks, especially large-scale computer networks [5]. Pecheniuk believes that the monitoring and management network needs to design an appropriate network monitoring system software to check the status of the whole network in real time, detect possible bottlenecks in network performance, and have the function of automatic alarm generation and alarm display, so as to ensure the efficient and reliable operation of the network. Network management software has become an indispensable part of the network, which is also the direct driving force behind the demand for network management software [6]. In the research, Hui-Ming et al. studied the actual application scenarios of a railway digital video monitoring system and a school digital video monitoring system, respectively, and realized the application of a simple video monitoring and recognition system in these two directions [7]. Far et al. combined with automatic detection and diagnosis technology proposed a new monitoring and recognition technology, which also provided a new scheme for the later research work of video monitoring system [8]. Magomedov et al. used neural networks as the basic algorithm for monitoring and recognition. According to the characteristics of strong robustness of neural networks and high recognition rate of training results, the intelligence of video monitoring system is becoming higher and higher [9]. Park and Lee analyze and expound the future development trend according to the application of existing video surveillance systems and some bottlenecks in their development. He believes that the further development of intelligent video surveillance technology must be based on the further development of the recognition algorithm [10]. Batista and Solanas believe that intrusion detection detects the unauthorized use of the system by users and the attempts of intruders outside the system to invade the system by using the security defects of the system by monitoring the use of the system. According to the user’s historical behavior and based on the user’s current operation, it completes the decision-making of the attack and records the attack evidence, so as to provide the basis for data recovery and accident handling. At present, there are mainly two kinds of intrusion detection systems: network-based and host-based. The former monitors the data flow of a specific network segment during the connection process, finds the hidden malicious intrusion in each data packet, and makes a timely response to the found intrusion. The latter is to check the unauthorized suspicious behavior recorded in the system log of a host and respond in time [11]. Jayakumar et al. believes that other conventional security systems, such as cryptography, digital signature, digital postmark, digital certificate, and the Certification Center, can protect core secrets and resist foreign illegal attacks. Some of these technologies ensure the security of the host and network in hardware, and some ensure the security of the host and network in software, such as fingerprint application technology to ensure the security of system login and anti-virus technology to ensure the virus protection of the information of the whole network [12]. Steadman et al. believe that the network monitoring and management system realizes the billing management, fault diagnosis, and network flow control of the server. From the perspective of client requirements, a network monitoring and management system needs to realize network monitoring and control functions and support most network protocols. The system overhead should be as small as possible, the management scope should be as large as possible, and the servers of different systems can be monitored. In this context, the simple network management protocol (SNMP) has developed rapidly [13]. Xu and Mao proposed the first version of simple network management, SNMPv1. SNMP forms a part of the Internet Protocol cluster defined by the Internet Engineering Task Force. The SNMP can support the standard network monitoring and management system to monitor whether the managed devices connected to the server are abnormal. SNMP consists of a set of network management standards, including an application layer protocol, a database model, and a set of data objects. Similar to the IPv4 protocol, SNMP has become a de facto network management standard once it is published and is supported by many hardware manufacturers, including IBM, HP, CISCO, etc. [14].
Based on the current research, this article proposes an algorithm based on a nonlinear network that is combined with the traditional algorithm. This article mainly analyzes the theory of nonlinear networks, designs and trains new network parameters according to their own needs, and combines the nonlinear network as a feature extractor with the existing intrusion detection and wandering detection algorithms, which greatly improves the recognition ability of traditional algorithms. Ethernet and FC are commonly used to construct a dual network architecture for nonlinear manufacturing network systems. Fibre channel-storage area network is responsible for high quality video data Real-time transmission, storage, sharing, and management‚ Ethernet is responsible for system management Scientific information, low-quality video data, audio data, documents, etc. Transport, storage, and sharing. The network system can upload materials, edit scripts and programs, add special effects, add subtitles, match sounds, edit and synthesize program strings, review movies, download (broadcast), and archive multimedia physical data in the network environment.
3 Intrusion detection and wandering detection algorithms based on a nonlinear network model
3.1 Analysis of nonlinear network
The main feature of a nonlinear network is that it can extract the positional features of objects from the network while also extracting object features, that is, positioning and classification are realized in the same network. As a feature extractor, this network can not only have a higher recognition rate than background difference, hog, and other algorithms but also have a greater ability to extract position information than other convolutional neural networks.
The nonlinear network embodies an end-to-end idea, which uses a network to learn the categories of the original pictures in blocks and outputs the specific positions of the objects. This idea makes the nonlinear network different from the regions with CNN features. The framing and classification of objects are two separate processes that are completely unified in one network operation.
First, in addition, the algorithm to be designed in this article must first meet the premise of real-time detection and identification, and the nonlinear network is just a very excellent network in terms of speed. Because the whole network can be unified in object framing and object category detection, the recognition speed of nonlinearity can be faster than other similar algorithms. The nonlinear detection speed can reach 45 fps, which can achieve real-time detection. The class detection of subgrid is very different from the recognition network of object class in the past [15]. When the two are combined, it is the confidence that an object frame contains objects of a certain category. If the small grid does not contain objects, that is, if it is considered that the grid is completely the background part, then the final output confidence is 0, otherwise the confidence formula is used. The following is the confidence formula (1):
Confidence is the intersection over union (IOU) of the predicted box and the ground truth box. Each object box contains five predicted values: x, y, w, h, and truth. (x, y) represents the coordinates of the center point of the frame relative to the boundary of the small grid, and W and H represent the width and height of object frames. Finally, the confidence score represents the IOU of the object frame and any ground truth boxes. In each small grid, the conditional probability pr (class object) of class C under the condition that there is an object at the position of the small grid is predicted. The nonlinear network can only predict object category C for S × S small grids, regardless of the number of object frames B.
According to formula (2), the confidence scores of each frame can be obtained. These scores represent the probability that the category appears in the frame and the degree to which these predicted boxes are suitable for the object.
3.2 Algorithm design and implementation
3.2.1 Intrusion detection algorithm
Figure 2 is the flow chart of the intrusion detection algorithm using a nonlinear network. The algorithm flow for intrusion detection is as follows: (i) Initialize the nonlinear network and load the parameter file saved after retraining into the network. (ii) Preprocess the video frame, normalize the video frame, and input it into the network. (iii) Calculate the video frame through the forward calculation of the network and output the feature vector. (iv) The classification feature part of the output feature vector is passed through the classifier to obtain the category information, and the location feature is generated into the object box.

Intrusion detection flow chart.
After combining the location information and category information of each area, judge whether there is data intrusion. If the category of people must be identified in an object frame, it is considered that there is an intrusion. In order to prevent an abnormal misidentification of a network, a continuous frame of intrusion identification must be formed during judgment before it can be determined that there is indeed an intrusion [16].
3.2.2 Wandering detection algorithm
Based on the aforementioned intrusion detection algorithm, the wandering detection algorithm in this article adds motion trajectory information and color feature information to comprehensively determine whether the same data is wandering abnormally in the current monitoring scene. In the previous example, the category of data could already be judged, but in the wandering detection algorithm, the track tracking error caused by the crosswalking of different data need to be avoided. This error is mainly due to the wrong judgment of the track when there is occlusion between the two data, resulting in the state of long-time staying. In this article, the change values of action track and color characteristics are combined to solve the previous misidentification to a certain extent [17].
First, wandering detection is based on intrusion detection. Once an intrusion is detected in the system, the whole wandering judgment process will be started. The core of the whole wandering judgment is whether the detection of the wandering path and the staying time exceed the preset value. During the detection process, it is believed that the presence of more than 200 frames of video belongs to abnormal wandering, which is about 10 s. After the intrusion judgment, the location of the intrusion target will be passed to the wandering detection algorithm. This article will generate the wandering path of the target to be tracked and detected according to the central point of the detected data location [18].
Without occlusion and detection loss, this detection method can completely realize the whole task of tracking and wandering detection. However, in fact, occlusion in the tracking process is inevitable, mainly in two cases. The first is that the data are blocked by some objects, and the second is the occlusion between data. In our detection algorithm, these two kinds of occlusion are about a few frames in the actual video, that is, there is target loss in the process of detecting the wandering path. This loss is easily different from the target loss when the data go out of the boundary because this loss is the loss of the target in the non-boundary area. Once this non-boundary area is lost, wandering detection will temporarily retain the current detection path. Once the intrusion target is re-detected, it will judge whether it matches the previous path according to the location of the intrusion target at this time. If it matches, it will re-track the last path. This solution can solve not only the first occlusion but also the occasional false alarm of intrusion detection, which greatly reduces the false alarm probability of wandering detection [19].
4 Experimental results and discussion
Wandering detection algorithm is completely based on the intrusion detection algorithm; therefore, experiment with the wandering algorithm in the whole performance test of the two algorithms has been chosen. Figures 3 and 4 are the test diagrams of the two algorithms. Figure 3 is the precision (PR) diagram, which shows the accuracy of the algorithm, the vertical axis is the accuracy, and the horizontal axis is the error threshold between the center point of the predicted position and the center point of the real position. Figure 4 is the area under curve (AUC) diagram, which represents the degree of overlapping with the real frame, the vertical axis represents the success rate of the overlapping area greater than the threshold, and the horizontal axis represents the threshold of the overlapping area [20,21]. In Figures 3 and 4, all blue lines (solid lines) are nonlinear algorithms in this article, and green lines (dotted lines) are the results of traditional algorithms:

Unobstructed PR diagram.

Unobstructed AUC diagram.
Figures 3 and 4 are the results of a group of relatively common tracking and recognition techniques. It can be seen from the left figure that the PR value of the nonlinear algorithm at almost every threshold can be greater than that of the traditional algorithm, while the nonlinear curve in the right figure is located above the traditional curve as a whole, which means that the nonlinear algorithm is better than the traditional algorithm no matter the error distance or overlap degree of the recognition center point [22,23].
Figures 5 and 6 are the test results in the case of occlusion. It can also be found that the nonlinear algorithm in this article has higher algorithm accuracy than the traditional algorithm. The reason why nonlinearity can surpass traditional recognition accuracy is the difference in feature extraction ability. The data features extracted by the tiny nonlinear network in this article have better recognition ability than the traditional felzenszwalb histogram of oriented gradients features. It cannot be ignored that the nonlinear algorithm in this article has a great advantage over the original tracking algorithm, that is, most tracking algorithms do not have the ability of category recognition during the initial tracking process, which means that these tracking algorithms cannot accurately know what they are tracking. Because the nonlinear network has the ability of output category, whether it is initial tracking or tracking loss recovery, nonlinearity fundamentally has better advantages than other tracking algorithms. Therefore, it can be predicted that there will be strong recognition ability in the later monitoring and wandering detection [24,25,26].

Blocked PR diagram.
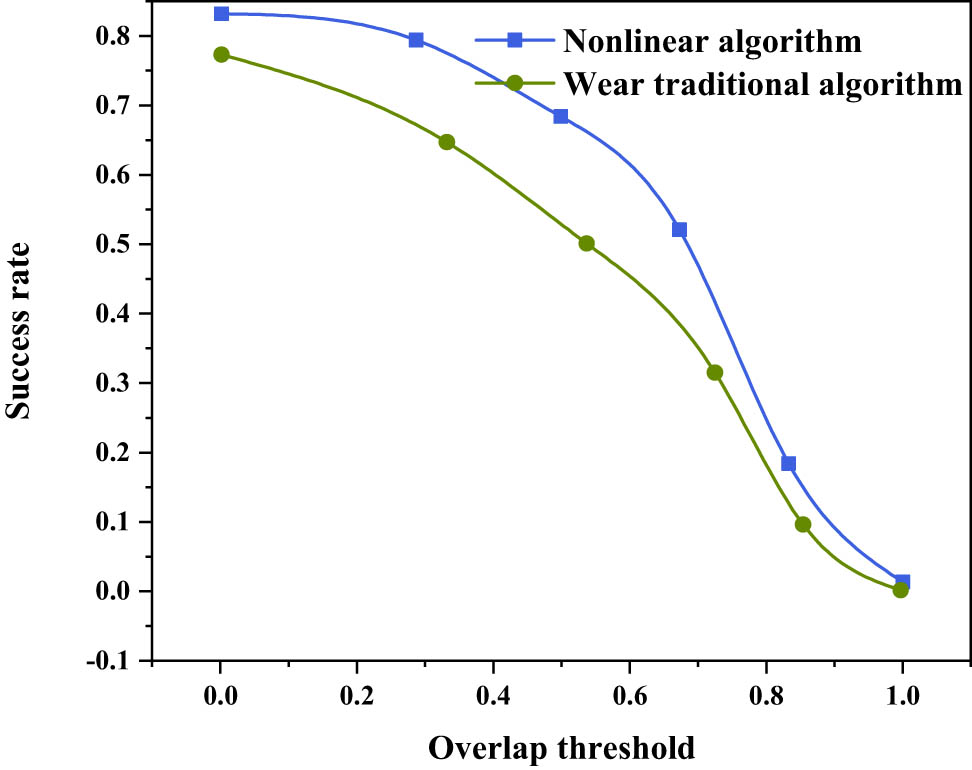
Blocked AUC diagram.
5 Conclusion
This chapter first analyzes the basic theory of nonlinear networks and then combines the nonlinear networks with the traditional intrusion detection and wandering detection algorithms to complete the intrusion detection and wandering detection algorithms with better recognition ability. In order to avoid occlusion interference in the wandering algorithm, the judgment of motion direction and color feature are added. These two algorithms will also be used as the identification algorithms of an intelligent monitoring and identification system. Finally, the recognition accuracy and speed of the wandering detection algorithm are tested, which proves the excellent performance of the algorithm. At present, there are a variety of Internet/Intranet information publishing schemes, such as common gateway interface, java database connectivity, and active server pages. However, these Web information publishers write scripts based on their own programming systems, which cannot well inherit the powerful functions of the information management system development tools themselves. The scripts they write are more suitable for a small amount of data processing, especially for the logical processing of information query business. If you want to take full advantage of the management information system development tools themselves PowerBuilder provides Web development tools that are ideal for the processing function for Web information publishing. PowerBuilder Web.PB, Web.PB class libraries, and Web.PB Plug-ins are provided. Web.PB is the core of Web components such as Wizard and Website. With these components, programmers familiar with PowerBuilder can move quickly to the Web application development model. This article focuses on the analysis based on Web.PB Intranet information publishing solution; developers can also select Plug-ins as required to enrich the data representation on the Web Type.
Acknowledgements
The author acknowledges Anhui University blockchain application integration subcenter (2020qkl17), He Jun Technical Skill Master Studio (2020dsgzs17), and Application Research of a credit bank based on blockchain (azcg29).
-
Conflict of interest: Author states no conflict of interest.
References
[1] Kumar C, Bharati TS, Prakash S. Online social network security: A comparative review using machine learning and deep learning. Neural Process Lett. 2021;53(1):843–61.10.1007/s11063-020-10416-3Suche in Google Scholar
[2] Novak S, Djordjevic N. Information system for evaluation of healthcare expenditure and health monitoring. Phys A Stat Mech Appl. 2019;520(C):72–80.10.1016/j.physa.2019.01.007Suche in Google Scholar
[3] Lee CH, Yang HC, Wei YC, Hsu WK. Enabling blockchain based SCM systems with a real time event monitoring function for preemptive risk management. Appl Sci. 2021;11(11):4811.10.3390/app11114811Suche in Google Scholar
[4] Ignatenko NV, Polikanin AN. Methods and means of counteraction of acoustic and optical reconnaissance UAV. Interexpo GEO-Siberia. 2020;6(1):149–54.10.33764/2618-981X-2020-6-1-149-154Suche in Google Scholar
[5] Kong JH. User privacy protection behavior and information sharing in mobile health application. Int J Adv Trends Comput Sci Eng. 2020;9(4):5250–8.10.30534/ijatcse/2020/155942020Suche in Google Scholar
[6] Pecheniuk AV. Conceptual principles for ensuring effective protection of information in the context of economic security of the enterprise. Ekonomìka Ta Upravlìnnâ APK. 2020;1(1(155)):84–92.10.33245/2310-9262-2020-155-1-84-92Suche in Google Scholar
[7] Wang HM, Zhang Y, Zhang X, Li Z. Secrecy and covert communications against UAV surveillance via multi-hop networks. IEEE Trans Commun. 2019;68(1):389–401.10.1109/TCOMM.2019.2950940Suche in Google Scholar
[8] Far H, Bayat M, Das AK, Fotouhi M, Doostari MA. Laptas: Lightweight anonymous privacy-preserving three-factor authentication scheme for WSN-based IIoT. Wirel Netw. 2021;27(4):1–24.10.1007/s11276-020-02523-9Suche in Google Scholar
[9] Magomedov S, Gusev A, Ilin D, Nikulchev EV. Users’ reaction time for improvement of security and access control in web services. Appl Sci. 2021;11(6):2561.10.3390/app11062561Suche in Google Scholar
[10] Park NK, Lee JH. PoC (proof of concept) for performance monitoring platform of container terminals. J Mar Sci Eng. 2020;8(12):971.10.3390/jmse8120971Suche in Google Scholar
[11] Batista E, Solanas A. A uniformization-based approach to preserve individuals’ privacy during process mining analyses. Peer-to-Peer Netw Appl. 2021;14(3):1500–19.10.1007/s12083-020-01059-1Suche in Google Scholar
[12] Jayakumar J, Chacko S, Ajay P. Conceptual implementation of artificial intelligent based e-mobility controller in smart city environment. Wirel Commun Mob Comput. 2021;2021:1–8.10.1155/2021/5325116Suche in Google Scholar
[13] Steadman P, Evans S, Liddiard R, Godoy-Shimizu D, Humphrey D. Building stock energy modelling in the UK: The 3D stock method and the London Building Stock Model. Build Cities. 2020;1(1):100–19.10.5334/bc.52Suche in Google Scholar
[14] Xu C, Mao Y. An improved traffic congestion monitoring system based on federated learning. Information. 2020;11(7):365.10.3390/info11070365Suche in Google Scholar
[15] Alkhelaiwi M, Boulila W, Ahmad J, Koubaa A, Driss M. An efficient approach based on privacy-preserving deep learning for satellite image classification. Remote Sens. 2021;13(11):2221.10.3390/rs13112221Suche in Google Scholar
[16] Li J. Artificial intelligence hospital hardware system and clinical observation of molecular heparin sodium in hemodialysis patients. Microprocess Microsyst. 2021;81(4):103690.10.1016/j.micpro.2020.103690Suche in Google Scholar
[17] Shubnikova EV, Zhuravleva EO, Velts NY, Giulakhmedova PM, Druzhinina AA. Drug safety monitoring information. Saf Risk Pharmacother. 2021;9(2):103–5.10.30895/2312-7821-2021-9-2-103-105Suche in Google Scholar
[18] Fatkieva R, Evnevich E. Control of information security monitoring perimeter of industrial facilities. J Phys Conf Ser. 2021;1864(1):012122(5pp).10.1088/1742-6596/1864/1/012122Suche in Google Scholar
[19] Editorial A. Drug safety monitoring information. Saf Risk Pharmacother. 2020;8(2):104–6.10.30895/2312-7821-2020-8-2-104-106Suche in Google Scholar
[20] Editorial A. Monitoring drug safety information – recommendations of foreign regulatory authorities. Saf Risk Pharmacother. 2020;8(1):52–4.10.30895/2312-7821-2020-8-1-52-54Suche in Google Scholar
[21] Wenceslao J. Public market price monitoring information system with SMS notification: A decision support system. Int J Adv Trends Comput Sci Eng. 2020;9(4):4302–7.10.30534/ijatcse/2020/19942020Suche in Google Scholar
[22] Jiang X, Chen X. Predicting method of monitoring information for telemonitoring system. IOP Conf Ser Mater Sci Eng. 2019;490(6):062030(6pp).10.1088/1757-899X/490/6/062030Suche in Google Scholar
[23] Suta I, Prabandari I, Ni L. Disclosure of information on environmental documents in supporting the role of public monitoring. Yuridika. 2021;36(2):313.10.20473/ydk.v36i2.24724Suche in Google Scholar
[24] Storozhenko NR, Goleva AI, Potapov VI, Pastuhova EI, Tunkov DA, Ralovec ML, et al. The mathematical model of monitoring information system with failure prediction. J Phys Conf Ser. 2019;1260(2):022010(7pp).10.1088/1742-6596/1260/2/022010Suche in Google Scholar
[25] Basri A, Gunawan AH. Information of system monitoring by network operation center. Tech-E. 2021;4(2):36.10.31253/te.v4i2.533Suche in Google Scholar
[26] Liu Y, Guo L, Gao H, You Z, Zhang B. Machine vision based condition monitoring and fault diagnosis of machine tools using information from machined surface texture: A review. Mech Syst Signal Process. 2022;164(1):108068.10.1016/j.ymssp.2021.108068Suche in Google Scholar
© 2023 the author(s), published by De Gruyter
This work is licensed under the Creative Commons Attribution 4.0 International License.
Artikel in diesem Heft
- Research Articles
- The regularization of spectral methods for hyperbolic Volterra integrodifferential equations with fractional power elliptic operator
- Analytical and numerical study for the generalized q-deformed sinh-Gordon equation
- Dynamics and attitude control of space-based synthetic aperture radar
- A new optimal multistep optimal homotopy asymptotic method to solve nonlinear system of two biological species
- Dynamical aspects of transient electro-osmotic flow of Burgers' fluid with zeta potential in cylindrical tube
- Self-optimization examination system based on improved particle swarm optimization
- Overlapping grid SQLM for third-grade modified nanofluid flow deformed by porous stretchable/shrinkable Riga plate
- Research on indoor localization algorithm based on time unsynchronization
- Performance evaluation and optimization of fixture adapter for oil drilling top drives
- Nonlinear adaptive sliding mode control with application to quadcopters
- Numerical simulation of Burgers’ equations via quartic HB-spline DQM
- Bond performance between recycled concrete and steel bar after high temperature
- Deformable Laplace transform and its applications
- A comparative study for the numerical approximation of 1D and 2D hyperbolic telegraph equations with UAT and UAH tension B-spline DQM
- Numerical approximations of CNLS equations via UAH tension B-spline DQM
- Nonlinear numerical simulation of bond performance between recycled concrete and corroded steel bars
- An iterative approach using Sawi transform for fractional telegraph equation in diversified dimensions
- Investigation of magnetized convection for second-grade nanofluids via Prabhakar differentiation
- Influence of the blade size on the dynamic characteristic damage identification of wind turbine blades
- Cilia and electroosmosis induced double diffusive transport of hybrid nanofluids through microchannel and entropy analysis
- Semi-analytical approximation of time-fractional telegraph equation via natural transform in Caputo derivative
- Analytical solutions of fractional couple stress fluid flow for an engineering problem
- Simulations of fractional time-derivative against proportional time-delay for solving and investigating the generalized perturbed-KdV equation
- Pricing weather derivatives in an uncertain environment
- Variational principles for a double Rayleigh beam system undergoing vibrations and connected by a nonlinear Winkler–Pasternak elastic layer
- Novel soliton structures of truncated M-fractional (4+1)-dim Fokas wave model
- Safety decision analysis of collapse accident based on “accident tree–analytic hierarchy process”
- Derivation of septic B-spline function in n-dimensional to solve n-dimensional partial differential equations
- Development of a gray box system identification model to estimate the parameters affecting traffic accidents
- Homotopy analysis method for discrete quasi-reversibility mollification method of nonhomogeneous backward heat conduction problem
- New kink-periodic and convex–concave-periodic solutions to the modified regularized long wave equation by means of modified rational trigonometric–hyperbolic functions
- Explicit Chebyshev Petrov–Galerkin scheme for time-fractional fourth-order uniform Euler–Bernoulli pinned–pinned beam equation
- NASA DART mission: A preliminary mathematical dynamical model and its nonlinear circuit emulation
- Nonlinear dynamic responses of ballasted railway tracks using concrete sleepers incorporated with reinforced fibres and pre-treated crumb rubber
- Two-component excitation governance of giant wave clusters with the partially nonlocal nonlinearity
- Bifurcation analysis and control of the valve-controlled hydraulic cylinder system
- Engineering fault intelligent monitoring system based on Internet of Things and GIS
- Traveling wave solutions of the generalized scale-invariant analog of the KdV equation by tanh–coth method
- Electric vehicle wireless charging system for the foreign object detection with the inducted coil with magnetic field variation
- Dynamical structures of wave front to the fractional generalized equal width-Burgers model via two analytic schemes: Effects of parameters and fractionality
- Theoretical and numerical analysis of nonlinear Boussinesq equation under fractal fractional derivative
- Research on the artificial control method of the gas nuclei spectrum in the small-scale experimental pool under atmospheric pressure
- Mathematical analysis of the transmission dynamics of viral infection with effective control policies via fractional derivative
- On duality principles and related convex dual formulations suitable for local and global non-convex variational optimization
- Study on the breaking characteristics of glass-like brittle materials
- The construction and development of economic education model in universities based on the spatial Durbin model
- Homoclinic breather, periodic wave, lump solution, and M-shaped rational solutions for cold bosonic atoms in a zig-zag optical lattice
- Fractional insights into Zika virus transmission: Exploring preventive measures from a dynamical perspective
- Rapid Communication
- Influence of joint flexibility on buckling analysis of free–free beams
- Special Issue: Recent trends and emergence of technology in nonlinear engineering and its applications - Part II
- Research on optimization of crane fault predictive control system based on data mining
- Nonlinear computer image scene and target information extraction based on big data technology
- Nonlinear analysis and processing of software development data under Internet of things monitoring system
- Nonlinear remote monitoring system of manipulator based on network communication technology
- Nonlinear bridge deflection monitoring and prediction system based on network communication
- Cross-modal multi-label image classification modeling and recognition based on nonlinear
- Application of nonlinear clustering optimization algorithm in web data mining of cloud computing
- Optimization of information acquisition security of broadband carrier communication based on linear equation
- A review of tiger conservation studies using nonlinear trajectory: A telemetry data approach
- Multiwireless sensors for electrical measurement based on nonlinear improved data fusion algorithm
- Realization of optimization design of electromechanical integration PLC program system based on 3D model
- Research on nonlinear tracking and evaluation of sports 3D vision action
- Analysis of bridge vibration response for identification of bridge damage using BP neural network
- Numerical analysis of vibration response of elastic tube bundle of heat exchanger based on fluid structure coupling analysis
- Establishment of nonlinear network security situational awareness model based on random forest under the background of big data
- Research and implementation of non-linear management and monitoring system for classified information network
- Study of time-fractional delayed differential equations via new integral transform-based variation iteration technique
- Exhaustive study on post effect processing of 3D image based on nonlinear digital watermarking algorithm
- A versatile dynamic noise control framework based on computer simulation and modeling
- A novel hybrid ensemble convolutional neural network for face recognition by optimizing hyperparameters
- Numerical analysis of uneven settlement of highway subgrade based on nonlinear algorithm
- Experimental design and data analysis and optimization of mechanical condition diagnosis for transformer sets
- Special Issue: Reliable and Robust Fuzzy Logic Control System for Industry 4.0
- Framework for identifying network attacks through packet inspection using machine learning
- Convolutional neural network for UAV image processing and navigation in tree plantations based on deep learning
- Analysis of multimedia technology and mobile learning in English teaching in colleges and universities
- A deep learning-based mathematical modeling strategy for classifying musical genres in musical industry
- An effective framework to improve the managerial activities in global software development
- Simulation of three-dimensional temperature field in high-frequency welding based on nonlinear finite element method
- Multi-objective optimization model of transmission error of nonlinear dynamic load of double helical gears
- Fault diagnosis of electrical equipment based on virtual simulation technology
- Application of fractional-order nonlinear equations in coordinated control of multi-agent systems
- Research on railroad locomotive driving safety assistance technology based on electromechanical coupling analysis
- Risk assessment of computer network information using a proposed approach: Fuzzy hierarchical reasoning model based on scientific inversion parallel programming
- Special Issue: Dynamic Engineering and Control Methods for the Nonlinear Systems - Part I
- The application of iterative hard threshold algorithm based on nonlinear optimal compression sensing and electronic information technology in the field of automatic control
- Equilibrium stability of dynamic duopoly Cournot game under heterogeneous strategies, asymmetric information, and one-way R&D spillovers
- Mathematical prediction model construction of network packet loss rate and nonlinear mapping user experience under the Internet of Things
- Target recognition and detection system based on sensor and nonlinear machine vision fusion
- Risk analysis of bridge ship collision based on AIS data model and nonlinear finite element
- Video face target detection and tracking algorithm based on nonlinear sequence Monte Carlo filtering technique
- Adaptive fuzzy extended state observer for a class of nonlinear systems with output constraint
Artikel in diesem Heft
- Research Articles
- The regularization of spectral methods for hyperbolic Volterra integrodifferential equations with fractional power elliptic operator
- Analytical and numerical study for the generalized q-deformed sinh-Gordon equation
- Dynamics and attitude control of space-based synthetic aperture radar
- A new optimal multistep optimal homotopy asymptotic method to solve nonlinear system of two biological species
- Dynamical aspects of transient electro-osmotic flow of Burgers' fluid with zeta potential in cylindrical tube
- Self-optimization examination system based on improved particle swarm optimization
- Overlapping grid SQLM for third-grade modified nanofluid flow deformed by porous stretchable/shrinkable Riga plate
- Research on indoor localization algorithm based on time unsynchronization
- Performance evaluation and optimization of fixture adapter for oil drilling top drives
- Nonlinear adaptive sliding mode control with application to quadcopters
- Numerical simulation of Burgers’ equations via quartic HB-spline DQM
- Bond performance between recycled concrete and steel bar after high temperature
- Deformable Laplace transform and its applications
- A comparative study for the numerical approximation of 1D and 2D hyperbolic telegraph equations with UAT and UAH tension B-spline DQM
- Numerical approximations of CNLS equations via UAH tension B-spline DQM
- Nonlinear numerical simulation of bond performance between recycled concrete and corroded steel bars
- An iterative approach using Sawi transform for fractional telegraph equation in diversified dimensions
- Investigation of magnetized convection for second-grade nanofluids via Prabhakar differentiation
- Influence of the blade size on the dynamic characteristic damage identification of wind turbine blades
- Cilia and electroosmosis induced double diffusive transport of hybrid nanofluids through microchannel and entropy analysis
- Semi-analytical approximation of time-fractional telegraph equation via natural transform in Caputo derivative
- Analytical solutions of fractional couple stress fluid flow for an engineering problem
- Simulations of fractional time-derivative against proportional time-delay for solving and investigating the generalized perturbed-KdV equation
- Pricing weather derivatives in an uncertain environment
- Variational principles for a double Rayleigh beam system undergoing vibrations and connected by a nonlinear Winkler–Pasternak elastic layer
- Novel soliton structures of truncated M-fractional (4+1)-dim Fokas wave model
- Safety decision analysis of collapse accident based on “accident tree–analytic hierarchy process”
- Derivation of septic B-spline function in n-dimensional to solve n-dimensional partial differential equations
- Development of a gray box system identification model to estimate the parameters affecting traffic accidents
- Homotopy analysis method for discrete quasi-reversibility mollification method of nonhomogeneous backward heat conduction problem
- New kink-periodic and convex–concave-periodic solutions to the modified regularized long wave equation by means of modified rational trigonometric–hyperbolic functions
- Explicit Chebyshev Petrov–Galerkin scheme for time-fractional fourth-order uniform Euler–Bernoulli pinned–pinned beam equation
- NASA DART mission: A preliminary mathematical dynamical model and its nonlinear circuit emulation
- Nonlinear dynamic responses of ballasted railway tracks using concrete sleepers incorporated with reinforced fibres and pre-treated crumb rubber
- Two-component excitation governance of giant wave clusters with the partially nonlocal nonlinearity
- Bifurcation analysis and control of the valve-controlled hydraulic cylinder system
- Engineering fault intelligent monitoring system based on Internet of Things and GIS
- Traveling wave solutions of the generalized scale-invariant analog of the KdV equation by tanh–coth method
- Electric vehicle wireless charging system for the foreign object detection with the inducted coil with magnetic field variation
- Dynamical structures of wave front to the fractional generalized equal width-Burgers model via two analytic schemes: Effects of parameters and fractionality
- Theoretical and numerical analysis of nonlinear Boussinesq equation under fractal fractional derivative
- Research on the artificial control method of the gas nuclei spectrum in the small-scale experimental pool under atmospheric pressure
- Mathematical analysis of the transmission dynamics of viral infection with effective control policies via fractional derivative
- On duality principles and related convex dual formulations suitable for local and global non-convex variational optimization
- Study on the breaking characteristics of glass-like brittle materials
- The construction and development of economic education model in universities based on the spatial Durbin model
- Homoclinic breather, periodic wave, lump solution, and M-shaped rational solutions for cold bosonic atoms in a zig-zag optical lattice
- Fractional insights into Zika virus transmission: Exploring preventive measures from a dynamical perspective
- Rapid Communication
- Influence of joint flexibility on buckling analysis of free–free beams
- Special Issue: Recent trends and emergence of technology in nonlinear engineering and its applications - Part II
- Research on optimization of crane fault predictive control system based on data mining
- Nonlinear computer image scene and target information extraction based on big data technology
- Nonlinear analysis and processing of software development data under Internet of things monitoring system
- Nonlinear remote monitoring system of manipulator based on network communication technology
- Nonlinear bridge deflection monitoring and prediction system based on network communication
- Cross-modal multi-label image classification modeling and recognition based on nonlinear
- Application of nonlinear clustering optimization algorithm in web data mining of cloud computing
- Optimization of information acquisition security of broadband carrier communication based on linear equation
- A review of tiger conservation studies using nonlinear trajectory: A telemetry data approach
- Multiwireless sensors for electrical measurement based on nonlinear improved data fusion algorithm
- Realization of optimization design of electromechanical integration PLC program system based on 3D model
- Research on nonlinear tracking and evaluation of sports 3D vision action
- Analysis of bridge vibration response for identification of bridge damage using BP neural network
- Numerical analysis of vibration response of elastic tube bundle of heat exchanger based on fluid structure coupling analysis
- Establishment of nonlinear network security situational awareness model based on random forest under the background of big data
- Research and implementation of non-linear management and monitoring system for classified information network
- Study of time-fractional delayed differential equations via new integral transform-based variation iteration technique
- Exhaustive study on post effect processing of 3D image based on nonlinear digital watermarking algorithm
- A versatile dynamic noise control framework based on computer simulation and modeling
- A novel hybrid ensemble convolutional neural network for face recognition by optimizing hyperparameters
- Numerical analysis of uneven settlement of highway subgrade based on nonlinear algorithm
- Experimental design and data analysis and optimization of mechanical condition diagnosis for transformer sets
- Special Issue: Reliable and Robust Fuzzy Logic Control System for Industry 4.0
- Framework for identifying network attacks through packet inspection using machine learning
- Convolutional neural network for UAV image processing and navigation in tree plantations based on deep learning
- Analysis of multimedia technology and mobile learning in English teaching in colleges and universities
- A deep learning-based mathematical modeling strategy for classifying musical genres in musical industry
- An effective framework to improve the managerial activities in global software development
- Simulation of three-dimensional temperature field in high-frequency welding based on nonlinear finite element method
- Multi-objective optimization model of transmission error of nonlinear dynamic load of double helical gears
- Fault diagnosis of electrical equipment based on virtual simulation technology
- Application of fractional-order nonlinear equations in coordinated control of multi-agent systems
- Research on railroad locomotive driving safety assistance technology based on electromechanical coupling analysis
- Risk assessment of computer network information using a proposed approach: Fuzzy hierarchical reasoning model based on scientific inversion parallel programming
- Special Issue: Dynamic Engineering and Control Methods for the Nonlinear Systems - Part I
- The application of iterative hard threshold algorithm based on nonlinear optimal compression sensing and electronic information technology in the field of automatic control
- Equilibrium stability of dynamic duopoly Cournot game under heterogeneous strategies, asymmetric information, and one-way R&D spillovers
- Mathematical prediction model construction of network packet loss rate and nonlinear mapping user experience under the Internet of Things
- Target recognition and detection system based on sensor and nonlinear machine vision fusion
- Risk analysis of bridge ship collision based on AIS data model and nonlinear finite element
- Video face target detection and tracking algorithm based on nonlinear sequence Monte Carlo filtering technique
- Adaptive fuzzy extended state observer for a class of nonlinear systems with output constraint

