Abstract
The paper presents an approach to encrypt the color images using bit-level permutation and alternate logistic map. The proposed method initially segregates the color image into red, green, and blue channels, transposes the segregated channels from the pixel-plane to bit-plane, and scrambles the bit-plane matrix using Arnold cat map (ACM). Finally, the red, blue, and green channels of the scrambled image are confused and diffused by applying alternate logistic map that uses a four-dimensional Lorenz system to generate a pseudorandom number sequence for the three channels. The parameters of ACM are generated with the help of Logistic-Sine map and Logistic-Tent map. The intensity values of scrambled pixels are altered by Tent-Sine map. One-dimensional and two-dimensional logistic maps are used for alternate logistic map implementation. The performance and security parameters histogram, correlation distribution, correlation coefficient, entropy, number of pixel change rate, and unified averaged changed intensity are computed to show the potential of the proposed encryption technique.
1 Introduction
In this information age, with the advent of technology, it becomes easier for an individual to send processed data. The processed data are classified into different categories as digital images, text, audio, videos, etc. Digital images are also one of the types of processed data, which are often sent through the various media like networking sites, electronic media, and social media. These are used in many application areas like video conversation, medical science, online albums, and military images database. The color images draw more attention as these incorporate more data than grayscale images [12], [38], [39], [42]. Hence, their security and authenticity is the major issue of research interest [30]. A number of image encryption algorithms are being developed for the security and safety of digital image data while transferring them through the networking medium. The classical algorithms like Data Encryption Standard [10], Advanced Encryption Standard [32], International Data Encryption Algorithm [16], etc. are incapable of encrypting digital images as there is strong correlation among adjacent pixels and redundant data and bulk capacity of data is present in digital images. Also, the classical algorithms require higher processing time and power [3], [24], [30], [46], [47]. The chaotic encryption techniques acquired the consideration of researchers because of their ubiquitous nature like sensitivity to seed value and control parameters, ergodic state, quasi-randomness, complex dynamics, etc. [1], [18], [24], [27], [30], [46].
The chaotic map is an integral part of the chaotic cryptosystem. It helps in implementing the chaotic behavior within the cryptosystem. By using seed value and control parameters, chaotic maps produce fractals of pseudorandom numbers. Chaotic maps are also used as key streams generator for the various encrypted systems [6], [23], [26]. In [23], [26], the Chebyshev polynomial and one-dimensional piecewise monotonic maps are used for the same. In [13], [28], the seed value of implemented logistic map (LM) and control parameters of Arnold map are used as the encryption key. The chaotic maps are categorized into one-dimensional [14], [26], [27] and multi-dimensional [5], [7], [11], [22], [27], [28], [41], [43], [48] as described in the research works of [11], [17]. The one-dimensional chaos has basic architecture, is easy to implement, and has low processing cost, but their chaotic orbit is quite smooth and one can predict it effortlessly [2]. The multi-dimensional chaos map has multiple parameters, sophisticated architecture, and higher processing cost [2], [17], [28]. Hence, a number of new chaos maps have been proposed by combining established chaotic maps. These provide a wider chaotic range, better chaotic behavior, and uniform distribution of density function as compared to traditional chaotic maps. Techniques that use new chaos maps are described in the research works of [2], [17], [36].
The confusion and diffusion process is an essential part of the chaotic cryptosystem [40], [46]. In confusion phase, there is the position interchanging between the pixels of an image while keeping values of all pixels same. In diffusion phase, the pixels’ values of the image are changed by employing any chaotic map. Hua and Zhou [15] integrated the confusion-diffusion to one step to make the algorithm more efficient. In [28] Patidar et al. described the new shuffling-diffusion technique. The work in [21] is enhanced by applying a modified shuffling-diffusion technique which gave better results [45]. Until now, the substitution-diffusion is applied at pixel level, but it can also be applied at the bit level. The bit-level permutation changes the pixel value of the image as well as modifies its intensity value. So it is preferred over pixel level. To make the statistical characteristics of confusion and diffusion process more robust, the bit-level permutation techniques are employed in the algorithms [8], [20], [46]. In [48], Zhao et al. uses Arnold cat map (ACM) for bit-level permutation which illustrates the high security and efficiency of the technique. The ACM is also used to reduce the relationship between the pixels of an image via shuffling [13], [33]. Inspired by the these observations, the proposed scheme of this paper uses the ACM for bit-level permutation. The bit-level permutation is followed by the XOR operation which is used to change the intensity values of the image pixels. In [35], for encrypting partially an image, the XOR operations and wavelet transform was applied. The XOR operator is used in encryption process due to its efficient nature in diffusing the image pixels which changes the intensity values of the pixel [25], [31].
The high-dimensional chaotic maps are used for secure communication and image encryption technique [29], [41]. The security of an algorithm is directly proportional to its key space. To provide a larger key space, the high-dimensional differential equation is used. To increase the encryption speed and security of a system, the four-dimensional Lorenz system is developed by classical three-dimensional Lorenz system [9], [19], [49]. Inspired by the work, in the proposed scheme, the four-dimensional chaotic Lorenz system is employed as a key generator for the encryption algorithm.
The paper presents a novel approach to encrypt a color image using bit-level permutation and alternate LM. The proposed method initially segregates the color image into red, green, and blue channels, transposes the segregated channels from the pixel plane to the bit plane, and scrambles the bit-plane matrix using ACM. Finally, the red, green, and blue channels of the scrambled image are confused and diffused by applying an alternate LM that uses a four-dimensional Lorenz system to generate a pseudorandom number sequence for the three channels. The parameters of ACM are generated with the help of Logistic-Sine map (LSM) and Logistic-Tent map (LTM). The intensity values of scrambled pixels are altered by the Tent-Sine map (TSM). One-dimensional and two-dimensional LMs are used for alternate LM implementation.
The structure of the paper is as follows: Section 2 describes the chaotic maps used in the proposed technique, Sections 3 and 4 explain the working behind the proposed scheme and the experimental results obtained from it, respectively, and Section 5 concludes the paper.
2 Chaotic Maps
Chaotic maps play an important role in a chaotic cryptosystem. The initial and control parameter can be used as the encryption key and also for generating the pseudorandom number series. The chaotic maps used in this paper are described as follows.
2.1 Logistic Map
This is one of the oldest, simple, and extensively used chaotic maps that have been used in many chaos-based cryptography systems.
2.1.1 One-Dimensional LM
It can be easily implemented through hardware and software because of its simplicity. It has less processing overhead and is more balanced. Hence, it is a candidate for characterizing the sophisticated dynamic behavior. Equation (1) gives the mathematical expression of the one-dimensional LM.
where pj lies in the range between 0 and 1 for n number of iterations. The dynamic nature of the function p depends on the control parameter
2.1.2 Two-Dimensional LM
The two-dimensional LM is the extension of one-dimensional LM. Chaotic cryptosystems usually employ the chaotic maps of more than one dimension to provide better key space and dependency on the control parameter. Hence, two-dimensional LM has a more complicated structure [28]. It shows more chaotic behavior than the one-dimensional LM. So it becomes harder for an attacker to breach the cryptosystem [42]. It can be mathematically expressed by Eq. (2).
where
2.2 Four-Dimensional Chaotic Map (Lorenz System)
The Lorenz system is the four-dimensional differential chaotic equation, an extended version of the three-dimensional differential equations. Equation (3) represents the mathematical expression of the four-dimensional Lorenz system [45].
Here z1, z2, z3, and z4 are state variables and a, b, c, d, e, f, and g are the constant parameters of the system. In [19] and [9], two Lorenz systems have been combined, and the performance analysis of new four-dimensional chaotic systems has been done. The developed differential equation system provides a set of dynamic solutions.
2.3 ACM
The ACM is performing the permutation within the pixels of an image. It is used to decrease the interrelationship between the pixels of the color image. Equation (4) gives the mathematical expression for the iterative form of ACM [24].
Here, a′ and b′ become the new coordinate positions of the pixel for the original positions of a and
2.4 LSM
This chaotic map is a combination of one-dimensional logistic and one-dimensional sine map. It provides greater chaotic range as compared to individual logistic and sine map. Equation (5) gives the mathematical expression for the LSM [6].
where
2.5 LTM
This chaotic map is the combination of the one-dimensional LM and one-dimensional tent map. Equation (6) gives the mathematical expression for the LTM [6].
where
2.6 TSM
This map is also the combination of one-dimensional tent map and one-dimensional sine map. Equation (7) gives the mathematical expression for the TSM [6].
3 Proposed Scheme
This section of the paper describes the color image encryption technique. The proposed scheme comprises bit-level permutation and alternate one-dimensional, two-dimensional LM. Firstly, the color image of

Block Diagram for Encyrption-Decryption Mechanism.
3.1 Bit-Level Permutation
A color image of size
Next, the TSM is used to generate pseudorandom number series (C) to diffuse the intensity value of the scrambled image by XORing with random numbers. The following expression is used to diffuse the intensity value of image pixel.
3.2 Encryption Technique
The scrambled image is encrypted using one-dimensional and two-dimensional LMs one after another employing the four-dimensional Lorenz system as pseudorandom key generator.
3.2.1 Pseudorandom Key Generator
The Algorithm 1 below describes the steps for generating the encryption key using Lorenz system.
Pseudorandom Key Generator Using Lorenz System
| Input: For generating keys for red, green, and blue channel, the initial values of constant parameters a, b, c, d, e, f, and g of the Lorenz system are taken as 16, 45, −2, 45, 16, −4, and 16. |
|---|
| Step 1: Create a four-dimensional chaotic sequence by taking the root values as z01, z02, z03, and z04 of chaotic system to iterate Eq. (3) (( |
| Step 2: Quantize four-dimensional chaotic sequence by taking all the values of
(11)
The decimal part of the chaotic sequence is quantized, and the integer sequence values
(12)
Step 3: Generate key sequence where
(13)
The following order reduces the correlation between three random bit sequences, and crosswise different bits of every sequence are taken. |
| Key 1 obtained from the first to eighth bits of
(14)
Key 2 obtained from the fifth to twelfth bits of
(15)
Key 3 obtained from the ninth to sixteenth bits of
(16)
Output: k1, k2, and k3 are the encryption keys for red, green, and blue channels obtained as output of this algorithm. |
The time taken to generate different lengths of multi-dimensional chaotic sequence is 5.181768 by this technique. A good pseudorandom key generator efficiently minimizes the length of chaotic sequence and hence largely reduce the time for encrypting the image.
3.2.2 Alternate LMs
The scrambled color image (h) of size
Alternate Logistic Maps
| Input: The scrambled image of size [M * N * 3] after bit-level permutation is performed is given as input. |
|---|
| Step1: Divide the scrambled image into R, G, and B channels matrix |
| Step 2:
(17)
(18)
(19)
Step 3: Repeat Eqs. (5) and (6) using Bk, Bk 1, Bk 2, Ly 1, and Ly 2 as the initial values of the p0, q0, and r0 are used. In each repetition the new values pj, qj, and rj are obtained. |
| Step 4: Assign the value of keys k 1, k 2, and k 3 should be to pi, qi, and ri, and continue repeating two-dimensional equations and one-dimensional equation of logistic map alternately. |
| Step 5: Diffuse the values of red, green, and blue channels to obtain the final encrypted image A.
(20)
where A(p, r − 1) is the previous value of the channels and (D(p,r)) is the current value of the channels which are being processed. |
| Output: The final encrypted image with its red, green, and blue channels is obtained by the algorithm. |
4 Experimental Setup and Security Analysis
This section of the paper discusses the tool used for implementing the color image encryption technique and results obtained after applying the technique. To implement the technique, MATLAB R2013a simulation tool, Operating System Windows 10 Pro, and processor intel core i-5 were used. The seed values for LSM, LTM, and TSM are set to 0.19235188279821, 0.73457891876543, and 0.56399882091176, respectively. The value of bifurcation parameter is 3.9999 for all the three maps. The implementation of the alternate LM with Lorenz system as the key generator is done by using the parameters, and initial values are v = 3.99, v1 = 3.39, v2 = 3.4489, L1 = 0.21, L2 = 0.15, x0 = 0.345, y0 = 0.365, and z0 = 0.537. Figure 2A shows the input “Aerial” image of size 170 × 170 taken for testing the proposed work. Figure 2B–D show its red, green, and blue channels. Figure 3A–D show the final encrypted color image with the red, green, and blue channels, respectively. Figure 4A–D show the final decrypted image with red, green, and blue channels, respectively.
Figure 2A–D show a final encrypted color image with the red, green, and blue channels, respectively.
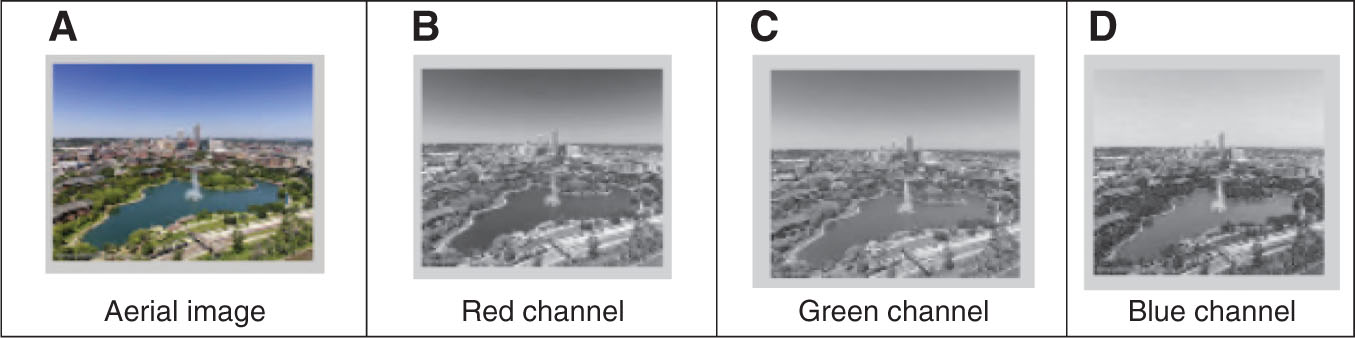
(A–D) Original “Aerial” Image with R, G, and B channels.

(A–D) Encrypted “Aerial” Image with R, G, and B channels.

(A–D) Decrypted “Aerial” Image with R, G, and B channels.
4.1 Key Space Analysis
The key space analysis demonstrates the probability of finding an encryption key by applying all the possible keys [29]. The key space of the implemented technique increases exponentially with increase in key size. It also depends upon the initial value of chaotic maps used in the system [45]. In the proposed scheme, the three chaotic maps are used which has 14 digits after the decimal points. The key space for them is equal to
4.2 Statistical Analysis
It demonstrates the nearness between the plaintext image and the cipher image. There must be no similarity between the cipher and the plaintext image. The two measures of statistical analysis are image histogram and correlation between the adjacent pixels [40]. The histogram illustrates the distribution of image pixels by plotting the graph of the intensity level of each pixel present in the image. Usually, for original plaintext, the graph formed is steeper, raised, and fluctuating in nature, while for encrypted images the graph is consistently scattered and much different from the original plaintext. Hence, it shows no statistical similarity between the original and the encrypted images. Figure 5A–C show histograms of R, G, and B channels of the original image, respectively. Figure 6A–C show the histograms of R, G, and B channels of the encrypted image, respectively.

Histogram Distribution of the Original Image.

Histogram Distribution of the Encrypted Image.
The correlation among the adjacent pixels of an original plaintext image is stronger, whereas in the encrypted image the correlation must be weaker such that the original images cannot be easily retrieved from the encrypted images. The correlation distribution of the red, green, and blue channels of the “Aerial” color image in each direction is shown in Figure 7. Figure 7A–C show the correlation distribution of the red channel of the plain color image horizontally, vertically, and diagonally. Figure 7D–F show the correlation distribution of the green channel of the plain color image horizontally, vertically, and diagonally. Figure 7G–I show the correlation distribution of the blue channel of the plain color image horizontally, vertically, and diagonally.

Correlation Distribution of Red, Green, and Blue Channels of the Original Color Image.
The correlation distribution of the red, green, and blue channels of the encrypted color image in each direction is shown in Figure 8. Figure 8A–C show the correlation distribution of the red channel of the encrypted color image horizontally, vertically, and diagonally. Figure 8D–F show the correlation distribution of the green channel of the encrypted image horizontally, vertically, and diagonally. Figure 8G–I show the correlation distribution of the blue channel of the encrypted image horizontally, vertically, and diagonally.

Correlation Distribution of Encrypted Red, Green, and Blue Channel of the Encrypted Image.
4.3 Correlation Coefficient Analysis
The correlation among the pixels of the original plaintext is high in each direction whether it is horizontal, vertical, or diagonal, while for the encrypted image the correlation should be very small in each direction. When the correlation is low, it implies that the algorithm has a better ability to resist statistical attack [40]. In plain image and encrypted image, 3000 pairs of adjacent pixels are selected to calculate the correlation coefficient. It is calculated by using the following equations [5]:
where
Table 1 shows the correlation coefficients between the R, G, and B channels of the encrypted color image.
Correlation Coefficients of R, G, and B Channels of the Encrypted Color Image of “Aerial”.
| Component | Horizontal | Vertical | Diagonal |
|---|---|---|---|
| R component | 0.0043 | −0.0162 | 0.0117 |
| G component | 0.0046 | −0.0067 | 0.0113 |
| B component | −0.0126 | −0.0283 | 0.0213 |
4.4 Information Entropy
Information entropy is used for measuring the robustness of the algorithm. The entropy value of the ciphered image is relatively equivalent to 8; then the algorithm has the capability of resisting against the entropy attack. Equation (42) gives mathematical expression for information entropy [19], [29], [40].
Here
NPCR, UACI, and Entropy Values of Encrypted R, G, and B Channels.
| Channels | NPCR | UACI | Entropy |
|---|---|---|---|
| Red | 99.6955 | 28.9173 | 7.9939 |
| Green | 99.7024 | 27.9796 | 7.9939 |
| Blue | 99.5329 | 31.6502 | 7.9920 |
4.5 Differential Analysis
This differential analysis illustrates the sensitivity of the encryption technique towards the negligible changes [37]. If an intruder does small changes in the original plaintext (for example, 1 pixel) to notice its impact on results, this interruption would result in a major change in the ciphered image. Then, the intruder could not get the connection between the original plaintext and the encrypted image. Thus, the differential attack by an intruder fails. Two measures, NPCR and UACI, are used to test against differential attack. NPCR is an acronym for a number of pixel change rate with respect to a one-pixel change in the original image. UACI is an acronym for unified average changing intensity which demonstrates the average intensity of differences between two encrypted images, corresponding to plain images having only one-pixel difference between them. The NPCR and UACI are expressed as follows:
where
where A and B show the width and height of the image, and C1 and C2 are the encrypted image before and after one pixel of the color plain image is changed. Table 2 shows the NPCR and UACI of R, G, and B components of the original plaintext and encrypted image.
4.6 PSNR and MSE
The parameters used for measuring encryption and decryption efficiency are mean squared error (MSE) and peak signal-to-noise ratio (PSNR) [4], [44]. MSE measures error present in images. The mathematical expression for calculating mean squared error is defined as follows in Eq. (28).
Here, z′ is the original plain image, and z is an encrypted image. N is the size of the image.
PSNR is defined as the ratio between peak signal to MSE. The mathematical formula for calculating the PSNR is as follows, defined in Eq. (29).
4.6.1 Encryption Efficiency
For encryption process efficiency, the PSNR and MSE are calculated for the original image and the encrypted image. Lower PSNR value and higher MSE value demonstrate the more efficient image encryption. The encryption efficiency is shown in Table 3.
Algorithm Efficiency Using PSNR and MSE Parameter for R, G, and B Channels.
| Channels | PSNR |
MSE |
||||
|---|---|---|---|---|---|---|
| R | G | B | R | G | B | |
| Encryption efficiency | 9.1395 | 9.4931 | 8.2573 | 7.9273e + 03 | 7.3076e + 03 | 9.7129e + 03 |
| Decryption efficiency | 38.2513 | 38.9967 | 35.3901 | 9.7264 | 8.1925 | 8.7962 |
4.6.2 Decryption Efficiency
For decryption process efficiency, the value of PSNR should be higher and MSE is lower between the original and the decrypted images. Table 3 shows the decryption efficiency of the algorithm.
4.7 Encryption Time Analysis
Time is the most important parameter in image encryption [40]. The proposed image encryption algorithm has been implemented on a personal computer with operating system Windows 10 Pro, with processor Intel core i-5 and using MATLAB R2013 as a simulation tool. Table 4 represents the time taken for encryption of the red, green, and blue components of the image.
Encryption Time of R, G, and B Components.
| Plain image component | Time (s) |
|---|---|
| Red component | 34.4616 |
| Green component | 34.4648 |
| Blue component | 34.4616 |
| Total encryption time | 34.4626 |
5 Conclusion
The proposed scheme presents a color image encryption technique using bit-level permutation and four-dimensional Lorenz system. The bit-level permutation is done with help of ACM. The three channels go through the confusion-diffusion process by four-dimensional Lorenz system and ultimately are transformed to an encrypted color image. Also, the tested performance metrics like key space analysis, entropy analysis, and differential analysis reveal that the developed system is highly resistant towards brute-force attack, is more secure, and is highly sensitive towards differential attack, respectively.
The PSNR and MSE are used to calculate efficiency of encryption and decryption process.
Bibliography
[1] A. Akgul, H. Calgan, I. Koyuncu, I. Pehlivan and A. Istanbullu, Chaos-based engineering applications with a 3D chaotic system without equilibrium points, Nonlinear Dyn. 84 (2016), 481–495.10.1007/s11071-015-2501-7Suche in Google Scholar
[2] A. Akgul, I. Moroz, I. Pehlivan and S. Vaidyanathan, A new four-scroll chaotic attractor and its engineering applications, Optik 127 (2016), 5491–5499.10.1016/j.ijleo.2016.02.066Suche in Google Scholar
[3] S. Aljawarneh and M. B. Yassein, A resource-efficient encryption algorithm for multimedia big data, Multimed. Tools Appl. 76 (2017), 22703–22724.10.1007/s11042-016-4333-ySuche in Google Scholar
[4] A. Bisht, M. Dua and S. Dua, A novel approach to encrypt multiple images using multiple chaotic maps and chaotic discrete fractional random transform, J. Amb. Intel. Hum. Comp. (2018), 1–13.10.1007/s12652-018-1072-0Suche in Google Scholar
[5] G. Chen, Y. Chen and X. Liao, An extended method for obtaining S-boxes based on three-dimensional chaotic Baker maps, Chaos Soliton. Fract. 31 (2007), 571–579.10.1016/j.chaos.2005.10.022Suche in Google Scholar
[6] J. X. Chen, Z. L. Zhu, C. Fu, H. Yu and L. B. Zhang, A fast chaos-based image encryption scheme with a dynamic state variables selection mechanism, Commun. Nonlinear Sci. Numer. Simul. 20 (2015), 846–860.10.1016/j.cnsns.2014.06.032Suche in Google Scholar
[7] A. V. Diaconu, Circular inter–intra pixels bit-level permutation and chaos-based image encryption, Inf. Sci. 355 (2016), 314–327.10.1016/j.ins.2015.10.027Suche in Google Scholar
[8] A. V. Diaconu, V. Ionescu, G. Iana and J. M. Lopez-Guede, A new bit-level permutation image encryption algorithm, in: Communications (COMM), 2016 International Conference on (IEEE), pp. 411–416, June 2016.10.1109/ICComm.2016.7528310Suche in Google Scholar
[9] C. Fu, B. B. Lin, Y. S. Miao, X. Liu and J. J. Chen, A novel chaos-based bit-level permutation scheme for digital image encryption, Opt. Commun. 284 (2011), 5415–5423.10.1016/j.optcom.2011.08.013Suche in Google Scholar
[10] A. Gambhir and R. Arya, Performance analysis and implementation of DES algorithm and RSA algorithm with image and audio steganography techniques, in:Computing, Communication and Signal Processing, pp. 1021–1028, Springer, Singapore, 2019.10.1007/978-981-13-1513-8_103Suche in Google Scholar
[11] T. Gao and Z. Chen, A new image encryption algorithm based on hyper-chaos, Phys. Lett. A 372 (2008), 394–400.10.1016/j.physleta.2007.07.040Suche in Google Scholar
[12] Q. Guo, Z. Liu and S. Liu, Color image encryption by using Arnold and discrete fractional random transforms in IHS space, Opt. Laser. Eng. 48 (2010), 1174–1181.10.1016/j.optlaseng.2010.07.005Suche in Google Scholar
[13] Z. Han, W. X. Feng, L. Z. Hui, L. Da Hai and L. Y. Chou, A new image encryption algorithm based on chaos system, in: Robotics, intelligent systems and signal processing, 2003. Proceedings. 2003 IEEE international conference on (IEEE), Vol. 2, pp. 778–782, October 2003.Suche in Google Scholar
[14] F. Han, X. Liao, B. Yang and Y. Zhang, A hybrid scheme for self-adaptive double color-image encryption, Multimed. Tools Appl. 77 (2017), 1–20.10.1007/s11042-017-5029-7Suche in Google Scholar
[15] Z. Hua and Y. Zhou, Image encryption using 2D Logistic-adjusted-Sine map, Inf. Sci. 339 (2016), 237–253.10.1016/j.ins.2016.01.017Suche in Google Scholar
[16] M. Jayashree, I. Poonguzhali and S. S. Agnes, An efficient high throughput implementation of idea encryption algorithm using VLSI, Aust. J. Basic Appl. Sci. 10 (2016), 337–344.Suche in Google Scholar
[17] A. Kanso and M. Ghebleh, A novel image encryption algorithm based on a 3D chaotic map, Commun. Nonlinear Sci. Numer. Simul. 17 (2012), 2943–2959.10.1016/j.cnsns.2011.11.030Suche in Google Scholar
[18] D. Lambić, A novel method of S-box design based on discrete chaotic map, Nonlinear Dyn. 87 (2017), 2407–2413.10.1007/s11071-016-3199-xSuche in Google Scholar
[19] C. Li, T. Xie, Q. Liu and G. Cheng, Cryptanalyzing image encryption using chaotic logistic map, Nonlinear Dyn. 78 (2014), 1545–1551.10.1007/s11071-014-1533-8Suche in Google Scholar
[20] Z. Lin, G. Wang, X. Wang, S. Yu and J. Lü, Security performance analysis of a chaotic stream cipher, Nonlinear Dyn. 94 (2018), 1–15.10.1007/s11071-018-4406-8Suche in Google Scholar
[21] H. Liu and X. Wang, Color image encryption using spatial bit-level permutation and high-dimension chaotic system, Opt. Commun. 284 (2011), 3895–3903.10.1016/j.optcom.2011.04.001Suche in Google Scholar
[22] H. Liu and A. Kadir, Asymmetric color image encryption scheme using 2D discrete-time map, Signal Process. 113 (2015), 104–112.10.1016/j.sigpro.2015.01.016Suche in Google Scholar
[23] B. Muite and G. Tabia, Chaos based cryptography, Tartu University, Tartu, Estonia, 2016.Suche in Google Scholar
[24] M. A. Murillo-Escobar, C. Cruz-Hernández, F. Abundiz-Pérez, R. M. López-Gutiérrez and O. A. Del Campo, A RGB image encryption algorithm based on total plain image characteristics and chaos, Signal Process. 109 (2015), 119–131.10.1016/j.sigpro.2014.10.033Suche in Google Scholar
[25] A. Nag, J. P. Singh, S. Khan, S. Biswas, D. Sarkar and P. P. Sarkar, Image encryption using affine transform and XOR operation. in: Signal Processing, Communication, Computing and Networking Technologies (ICSCCN), 2011 International Conference on (IEEE), pp. 309–312, July 2011.10.1109/ICSCCN.2011.6024565Suche in Google Scholar
[26] C. Pak and L. Huang, A new color image encryption using combination of the 1D chaotic map, Signal Process. 138 (2017), 129–137.10.1016/j.sigpro.2017.03.011Suche in Google Scholar
[27] N. K. Pareek, V. Patidar and K. K. Sud, Cryptography using multiple one-dimensional chaotic maps, Commun. Nonlinear Sci. Numer. Simul. 10 (2005), 715–723.10.1016/j.cnsns.2004.03.006Suche in Google Scholar
[28] V. Patidar, N. K. Pareek and K. K. Sud, A new substitution–diffusion based image cipher using chaotic standard and logistic maps, Commun. Nonlinear Sci. Numer. Simul. 14 (2009), 3056–3075.10.1016/j.cnsns.2008.11.005Suche in Google Scholar
[29] V. Patidar, N. K. Pareek, G. Purohit and K. K. Sud, Modified substitution–diffusion image cipher using chaotic standard and logistic maps, Commun. Nonlinear Sci. Numer. Simul. 15 (2010), 2755–2765.10.1016/j.cnsns.2009.11.010Suche in Google Scholar
[30] N. Prasad, V. M. Ravi and L. Chandrasekhar, Image encryption with an encrypted QR, random phase encoding, and logistic map, in: 2018 IEEE International Conference on Computer Communication and Informatics (ICCCI), pp. 1–4, January 2018.10.1109/ICCCI.2018.8441219Suche in Google Scholar
[31] R. M. Rad, A. Attar and R. E. Atani, A new fast and simple image encryption algorithm using scan patterns and XOR, IJSIP 6 (2013), 275–290.10.14257/ijsip.2013.6.5.25Suche in Google Scholar
[32] M. I. S. Reddy and A. S. Kumar, Secured data transmission using wavelet based steganography and cryptography by using AES algorithm, Procedia Comput. Sci. 85 (2016), 62–69.10.1016/j.procs.2016.05.177Suche in Google Scholar
[33] P. R. Sankpal and P. A. Vijaya, Image encryption using chaotic maps: a survey, in: Signal and Image Processing (ICSIP), 2014 Fifth International Conference on (IEEE), pp. 102–107, January 2014.10.1109/ICSIP.2014.80Suche in Google Scholar
[34] S. M. Seyedzadeh and S. Mirzakuchaki, A fast color image encryption algorithm based on coupled two-dimensional piecewise chaotic map, Signal Process. 92 (2012), 1202–1215.10.1016/j.sigpro.2011.11.004Suche in Google Scholar
[35] P. K. Singh, R. S. Singh and K. N. Rai, An image encryption algorithm based on XOR operation with approximation component in wavelet transform, in: Computer Vision, Pattern Recognition, Image Processing and Graphics (NCVPRIPG), 2015 Fifth National Conference on (IEEE), pp. 1–4, December 2015.10.1109/NCVPRIPG.2015.7490013Suche in Google Scholar
[36] L. Sui, H. Lu, Z. Wang and Q. Sun, Double-image encryption using discrete fractional random transform and logistic maps, Opt. Laser. Eng. 56 (2014), 1–12.10.1016/j.optlaseng.2013.12.001Suche in Google Scholar
[37] S. Suri and R. Vijay, A synchronous intertwining logistic map-DNA approach for color image encryption, J. Amb. Intel. Hum. Comp. (2018), 1–14.10.1007/s12652-018-0825-0Suche in Google Scholar
[38] C. J. Tay, C. Quan, W. Chen and Y. Fu, Color image encryption based on interference and virtual optics, Opt. Laser Technol. 42 (2010), 409–415.10.1016/j.optlastec.2009.08.016Suche in Google Scholar
[39] L. Teng, X. Wang and J. Meng, A chaotic color image encryption using integrated bit-level permutation, Multimed. Tools Appl. 77 (2018), 6883–6896.10.1007/s11042-017-4605-1Suche in Google Scholar
[40] X. J. Tong, M. Zhang, Z. Wang, Y. Liu, H. Xu and J. Ma, A fast encryption algorithm of color image based on four-dimensional chaotic system, J. Vis. Commun. Image R. 33 (2015), 219–234.10.1016/j.jvcir.2015.09.014Suche in Google Scholar
[41] A. Tsuneda, Design of binary sequences with tunable exponential autocorrelations and run statistics based on one-dimensional chaotic maps, IEEE Trans. Circuits Syst.-I 52 (2005), 454–462.10.1109/TCSI.2004.841597Suche in Google Scholar
[42] X. Wang, Y. Zhao, H. Zhang and K. Guo, A novel color image encryption scheme using alternate chaotic mapping structure, Opt. Laser. Eng. 82 (2016), 79–86.10.1016/j.optlaseng.2015.12.006Suche in Google Scholar
[43] J. Wei, X. Liao, K. W. Wong and T. Zhou, Cryptanalysis of a cryptosystem using multiple one-dimensional chaotic maps, Commun. Nonlinear Sci. Numer. Simul. 12 (2007), 814–822.10.1016/j.cnsns.2005.06.001Suche in Google Scholar
[44] Y. Xing, Q. H. Wang, Z. L. Xiong and H. Deng, Encrypting three-dimensional information system based on integral imaging and multiple chaotic maps, Opt. Eng. 55 (2016), 023107.10.1117/1.OE.55.2.023107Suche in Google Scholar
[45] F. Yu, L. Gao, K. Gu, B. Yin, Q. Wan and Z. Zhou, A fully qualified four-wing four-dimensional autonomous chaotic system and its synchronization, Optik 131 (2017), 79–88.10.1016/j.ijleo.2016.11.067Suche in Google Scholar
[46] Y. Q. Zhang and X. Y. Wang, A new image encryption algorithm based on non-adjacent coupled map lattices, Appl. Soft Comput. 26 (2015), 10–20.10.1016/j.asoc.2014.09.039Suche in Google Scholar
[47] Y. Zhou, L. Bao and C. P. Chen, Image encryption using a new parametric switching chaotic system, Signal Process. 93 (2013), 3039–3052.10.1016/j.sigpro.2013.04.021Suche in Google Scholar
[48] Y. Zhou, L. Bao and C. P. Chen, A new 1D chaotic system for image encryption, Signal Process. 97 (2014), 172–182.10.1016/j.sigpro.2013.10.034Suche in Google Scholar
[49] Z. L. Zhu, W. Zhang, K. W. Wong and H. Yu, A chaos-based symmetric image encryption scheme using a bit-level permutation, Inf. Sci. 181 (2011), 1171–1186.10.1016/j.ins.2010.11.009Suche in Google Scholar
©2020 Walter de Gruyter GmbH, Berlin/Boston
This work is licensed under the Creative Commons Attribution 4.0 Public License.
Artikel in diesem Heft
- An Optimized K-Harmonic Means Algorithm Combined with Modified Particle Swarm Optimization and Cuckoo Search Algorithm
- Texture Feature Extraction Using Intuitionistic Fuzzy Local Binary Pattern
- Leaf Disease Segmentation From Agricultural Images via Hybridization of Active Contour Model and OFA
- Deadline Constrained Task Scheduling Method Using a Combination of Center-Based Genetic Algorithm and Group Search Optimization
- Efficient Classification of DDoS Attacks Using an Ensemble Feature Selection Algorithm
- Distributed Multi-agent Bidding-Based Approach for the Collaborative Mapping of Unknown Indoor Environments by a Homogeneous Mobile Robot Team
- An Efficient Technique for Three-Dimensional Image Visualization Through Two-Dimensional Images for Medical Data
- Combined Multi-Agent Method to Control Inter-Department Common Events Collision for University Courses Timetabling
- An Improved Particle Swarm Optimization Algorithm for Global Multidimensional Optimization
- A Kernel Probabilistic Model for Semi-supervised Co-clustering Ensemble
- Pythagorean Hesitant Fuzzy Information Aggregation and Their Application to Multi-Attribute Group Decision-Making Problems
- Using an Efficient Optimal Classifier for Soil Classification in Spatial Data Mining Over Big Data
- A Bayesian Multiresolution Approach for Noise Removal in Medical Magnetic Resonance Images
- Gbest-Guided Artificial Bee Colony Optimization Algorithm-Based Optimal Incorporation of Shunt Capacitors in Distribution Networks under Load Growth
- Graded Soft Expert Set as a Generalization of Hesitant Fuzzy Set
- Universal Liver Extraction Algorithm: An Improved Chan–Vese Model
- Software Effort Estimation Using Modified Fuzzy C Means Clustering and Hybrid ABC-MCS Optimization in Neural Network
- Handwritten Indic Script Recognition Based on the Dempster–Shafer Theory of Evidence
- An Integrated Intuitionistic Fuzzy AHP and TOPSIS Approach to Evaluation of Outsource Manufacturers
- Automatically Assess Day Similarity Using Visual Lifelogs
- A Novel Bio-Inspired Algorithm Based on Social Spiders for Improving Performance and Efficiency of Data Clustering
- Discriminative Training Using Noise Robust Integrated Features and Refined HMM Modeling
- Self-Adaptive Mussels Wandering Optimization Algorithm with Application for Artificial Neural Network Training
- A Framework for Image Alignment of TerraSAR-X Images Using Fractional Derivatives and View Synthesis Approach
- Intelligent Systems for Structural Damage Assessment
- Some Interval-Valued Pythagorean Fuzzy Einstein Weighted Averaging Aggregation Operators and Their Application to Group Decision Making
- Fuzzy Adaptive Genetic Algorithm for Improving the Solution of Industrial Optimization Problems
- Approach to Multiple Attribute Group Decision Making Based on Hesitant Fuzzy Linguistic Aggregation Operators
- Cubic Ordered Weighted Distance Operator and Application in Group Decision-Making
- Fault Signal Recognition in Power Distribution System using Deep Belief Network
- Selector: PSO as Model Selector for Dual-Stage Diabetes Network
- Oppositional Gravitational Search Algorithm and Artificial Neural Network-based Classification of Kidney Images
- Improving Image Search through MKFCM Clustering Strategy-Based Re-ranking Measure
- Sparse Decomposition Technique for Segmentation and Compression of Compound Images
- Automatic Genetic Fuzzy c-Means
- Harmony Search Algorithm for Patient Admission Scheduling Problem
- Speech Signal Compression Algorithm Based on the JPEG Technique
- i-Vector-Based Speaker Verification on Limited Data Using Fusion Techniques
- Prediction of User Future Request Utilizing the Combination of Both ANN and FCM in Web Page Recommendation
- Presentation of ACT/R-RBF Hybrid Architecture to Develop Decision Making in Continuous and Non-continuous Data
- An Overview of Segmentation Algorithms for the Analysis of Anomalies on Medical Images
- Blind Restoration Algorithm Using Residual Measures for Motion-Blurred Noisy Images
- Extreme Learning Machine for Credit Risk Analysis
- A Genetic Algorithm Approach for Group Recommender System Based on Partial Rankings
- Improvements in Spoken Query System to Access the Agricultural Commodity Prices and Weather Information in Kannada Language/Dialects
- A One-Pass Approach for Slope and Slant Estimation of Tri-Script Handwritten Words
- Secure Communication through MultiAgent System-Based Diabetes Diagnosing and Classification
- Development of a Two-Stage Segmentation-Based Word Searching Method for Handwritten Document Images
- Pythagorean Fuzzy Einstein Hybrid Averaging Aggregation Operator and its Application to Multiple-Attribute Group Decision Making
- Ensembles of Text and Time-Series Models for Automatic Generation of Financial Trading Signals from Social Media Content
- A Flame Detection Method Based on Novel Gradient Features
- Modeling and Optimization of a Liquid Flow Process using an Artificial Neural Network-Based Flower Pollination Algorithm
- Spectral Graph-based Features for Recognition of Handwritten Characters: A Case Study on Handwritten Devanagari Numerals
- A Grey Wolf Optimizer for Text Document Clustering
- Classification of Masses in Digital Mammograms Using the Genetic Ensemble Method
- A Hybrid Grey Wolf Optimiser Algorithm for Solving Time Series Classification Problems
- Gray Method for Multiple Attribute Decision Making with Incomplete Weight Information under the Pythagorean Fuzzy Setting
- Multi-Agent System Based on the Extreme Learning Machine and Fuzzy Control for Intelligent Energy Management in Microgrid
- Deep CNN Combined With Relevance Feedback for Trademark Image Retrieval
- Cognitively Motivated Query Abstraction Model Based on Associative Root-Pattern Networks
- Improved Adaptive Neuro-Fuzzy Inference System Using Gray Wolf Optimization: A Case Study in Predicting Biochar Yield
- Predict Forex Trend via Convolutional Neural Networks
- Optimizing Integrated Features for Hindi Automatic Speech Recognition System
- A Novel Weakest t-norm based Fuzzy Fault Tree Analysis Through Qualitative Data Processing and Its Application in System Reliability Evaluation
- FCNB: Fuzzy Correlative Naive Bayes Classifier with MapReduce Framework for Big Data Classification
- A Modified Jaya Algorithm for Mixed-Variable Optimization Problems
- An Improved Robust Fuzzy Algorithm for Unsupervised Learning
- Hybridizing the Cuckoo Search Algorithm with Different Mutation Operators for Numerical Optimization Problems
- An Efficient Lossless ROI Image Compression Using Wavelet-Based Modified Region Growing Algorithm
- Predicting Automatic Trigger Speed for Vehicle-Activated Signs
- Group Recommender Systems – An Evolutionary Approach Based on Multi-expert System for Consensus
- Enriching Documents by Linking Salient Entities and Lexical-Semantic Expansion
- A New Feature Selection Method for Sentiment Analysis in Short Text
- Optimizing Software Modularity with Minimum Possible Variations
- Optimizing the Self-Organizing Team Size Using a Genetic Algorithm in Agile Practices
- Aspect-Oriented Sentiment Analysis: A Topic Modeling-Powered Approach
- Feature Pair Index Graph for Clustering
- Tangramob: An Agent-Based Simulation Framework for Validating Urban Smart Mobility Solutions
- A New Algorithm Based on Magic Square and a Novel Chaotic System for Image Encryption
- Video Steganography Using Knight Tour Algorithm and LSB Method for Encrypted Data
- Clay-Based Brick Porosity Estimation Using Image Processing Techniques
- AGCS Technique to Improve the Performance of Neural Networks
- A Color Image Encryption Technique Based on Bit-Level Permutation and Alternate Logistic Maps
- A Hybrid of Deep CNN and Bidirectional LSTM for Automatic Speech Recognition
- Database Creation and Dialect-Wise Comparative Analysis of Prosodic Features for Punjabi Language
- Trapezoidal Linguistic Cubic Fuzzy TOPSIS Method and Application in a Group Decision Making Program
- Histopathological Image Segmentation Using Modified Kernel-Based Fuzzy C-Means and Edge Bridge and Fill Technique
- Proximal Support Vector Machine-Based Hybrid Approach for Edge Detection in Noisy Images
- Early Detection of Parkinson’s Disease by Using SPECT Imaging and Biomarkers
- Image Compression Based on Block SVD Power Method
- Noise Reduction Using Modified Wiener Filter in Digital Hearing Aid for Speech Signal Enhancement
- Secure Fingerprint Authentication Using Deep Learning and Minutiae Verification
- The Use of Natural Language Processing Approach for Converting Pseudo Code to C# Code
- Non-word Attributes’ Efficiency in Text Mining Authorship Prediction
- Design and Evaluation of Outlier Detection Based on Semantic Condensed Nearest Neighbor
- An Efficient Quality Inspection of Food Products Using Neural Network Classification
- Opposition Intensity-Based Cuckoo Search Algorithm for Data Privacy Preservation
- M-HMOGA: A New Multi-Objective Feature Selection Algorithm for Handwritten Numeral Classification
- Analogy-Based Approaches to Improve Software Project Effort Estimation Accuracy
- Linear Regression Supporting Vector Machine and Hybrid LOG Filter-Based Image Restoration
- Fractional Fuzzy Clustering and Particle Whale Optimization-Based MapReduce Framework for Big Data Clustering
- Implementation of Improved Ship-Iceberg Classifier Using Deep Learning
- Hybrid Approach for Face Recognition from a Single Sample per Person by Combining VLC and GOM
- Polarity Analysis of Customer Reviews Based on Part-of-Speech Subcategory
- A 4D Trajectory Prediction Model Based on the BP Neural Network
- A Blind Medical Image Watermarking for Secure E-Healthcare Application Using Crypto-Watermarking System
- Discriminating Healthy Wheat Grains from Grains Infected with Fusarium graminearum Using Texture Characteristics of Image-Processing Technique, Discriminant Analysis, and Support Vector Machine Methods
- License Plate Recognition in Urban Road Based on Vehicle Tracking and Result Integration
- Binary Genetic Swarm Optimization: A Combination of GA and PSO for Feature Selection
- Enhanced Twitter Sentiment Analysis Using Hybrid Approach and by Accounting Local Contextual Semantic
- Cloud Security: LKM and Optimal Fuzzy System for Intrusion Detection in Cloud Environment
- Power Average Operators of Trapezoidal Cubic Fuzzy Numbers and Application to Multi-attribute Group Decision Making
Artikel in diesem Heft
- An Optimized K-Harmonic Means Algorithm Combined with Modified Particle Swarm Optimization and Cuckoo Search Algorithm
- Texture Feature Extraction Using Intuitionistic Fuzzy Local Binary Pattern
- Leaf Disease Segmentation From Agricultural Images via Hybridization of Active Contour Model and OFA
- Deadline Constrained Task Scheduling Method Using a Combination of Center-Based Genetic Algorithm and Group Search Optimization
- Efficient Classification of DDoS Attacks Using an Ensemble Feature Selection Algorithm
- Distributed Multi-agent Bidding-Based Approach for the Collaborative Mapping of Unknown Indoor Environments by a Homogeneous Mobile Robot Team
- An Efficient Technique for Three-Dimensional Image Visualization Through Two-Dimensional Images for Medical Data
- Combined Multi-Agent Method to Control Inter-Department Common Events Collision for University Courses Timetabling
- An Improved Particle Swarm Optimization Algorithm for Global Multidimensional Optimization
- A Kernel Probabilistic Model for Semi-supervised Co-clustering Ensemble
- Pythagorean Hesitant Fuzzy Information Aggregation and Their Application to Multi-Attribute Group Decision-Making Problems
- Using an Efficient Optimal Classifier for Soil Classification in Spatial Data Mining Over Big Data
- A Bayesian Multiresolution Approach for Noise Removal in Medical Magnetic Resonance Images
- Gbest-Guided Artificial Bee Colony Optimization Algorithm-Based Optimal Incorporation of Shunt Capacitors in Distribution Networks under Load Growth
- Graded Soft Expert Set as a Generalization of Hesitant Fuzzy Set
- Universal Liver Extraction Algorithm: An Improved Chan–Vese Model
- Software Effort Estimation Using Modified Fuzzy C Means Clustering and Hybrid ABC-MCS Optimization in Neural Network
- Handwritten Indic Script Recognition Based on the Dempster–Shafer Theory of Evidence
- An Integrated Intuitionistic Fuzzy AHP and TOPSIS Approach to Evaluation of Outsource Manufacturers
- Automatically Assess Day Similarity Using Visual Lifelogs
- A Novel Bio-Inspired Algorithm Based on Social Spiders for Improving Performance and Efficiency of Data Clustering
- Discriminative Training Using Noise Robust Integrated Features and Refined HMM Modeling
- Self-Adaptive Mussels Wandering Optimization Algorithm with Application for Artificial Neural Network Training
- A Framework for Image Alignment of TerraSAR-X Images Using Fractional Derivatives and View Synthesis Approach
- Intelligent Systems for Structural Damage Assessment
- Some Interval-Valued Pythagorean Fuzzy Einstein Weighted Averaging Aggregation Operators and Their Application to Group Decision Making
- Fuzzy Adaptive Genetic Algorithm for Improving the Solution of Industrial Optimization Problems
- Approach to Multiple Attribute Group Decision Making Based on Hesitant Fuzzy Linguistic Aggregation Operators
- Cubic Ordered Weighted Distance Operator and Application in Group Decision-Making
- Fault Signal Recognition in Power Distribution System using Deep Belief Network
- Selector: PSO as Model Selector for Dual-Stage Diabetes Network
- Oppositional Gravitational Search Algorithm and Artificial Neural Network-based Classification of Kidney Images
- Improving Image Search through MKFCM Clustering Strategy-Based Re-ranking Measure
- Sparse Decomposition Technique for Segmentation and Compression of Compound Images
- Automatic Genetic Fuzzy c-Means
- Harmony Search Algorithm for Patient Admission Scheduling Problem
- Speech Signal Compression Algorithm Based on the JPEG Technique
- i-Vector-Based Speaker Verification on Limited Data Using Fusion Techniques
- Prediction of User Future Request Utilizing the Combination of Both ANN and FCM in Web Page Recommendation
- Presentation of ACT/R-RBF Hybrid Architecture to Develop Decision Making in Continuous and Non-continuous Data
- An Overview of Segmentation Algorithms for the Analysis of Anomalies on Medical Images
- Blind Restoration Algorithm Using Residual Measures for Motion-Blurred Noisy Images
- Extreme Learning Machine for Credit Risk Analysis
- A Genetic Algorithm Approach for Group Recommender System Based on Partial Rankings
- Improvements in Spoken Query System to Access the Agricultural Commodity Prices and Weather Information in Kannada Language/Dialects
- A One-Pass Approach for Slope and Slant Estimation of Tri-Script Handwritten Words
- Secure Communication through MultiAgent System-Based Diabetes Diagnosing and Classification
- Development of a Two-Stage Segmentation-Based Word Searching Method for Handwritten Document Images
- Pythagorean Fuzzy Einstein Hybrid Averaging Aggregation Operator and its Application to Multiple-Attribute Group Decision Making
- Ensembles of Text and Time-Series Models for Automatic Generation of Financial Trading Signals from Social Media Content
- A Flame Detection Method Based on Novel Gradient Features
- Modeling and Optimization of a Liquid Flow Process using an Artificial Neural Network-Based Flower Pollination Algorithm
- Spectral Graph-based Features for Recognition of Handwritten Characters: A Case Study on Handwritten Devanagari Numerals
- A Grey Wolf Optimizer for Text Document Clustering
- Classification of Masses in Digital Mammograms Using the Genetic Ensemble Method
- A Hybrid Grey Wolf Optimiser Algorithm for Solving Time Series Classification Problems
- Gray Method for Multiple Attribute Decision Making with Incomplete Weight Information under the Pythagorean Fuzzy Setting
- Multi-Agent System Based on the Extreme Learning Machine and Fuzzy Control for Intelligent Energy Management in Microgrid
- Deep CNN Combined With Relevance Feedback for Trademark Image Retrieval
- Cognitively Motivated Query Abstraction Model Based on Associative Root-Pattern Networks
- Improved Adaptive Neuro-Fuzzy Inference System Using Gray Wolf Optimization: A Case Study in Predicting Biochar Yield
- Predict Forex Trend via Convolutional Neural Networks
- Optimizing Integrated Features for Hindi Automatic Speech Recognition System
- A Novel Weakest t-norm based Fuzzy Fault Tree Analysis Through Qualitative Data Processing and Its Application in System Reliability Evaluation
- FCNB: Fuzzy Correlative Naive Bayes Classifier with MapReduce Framework for Big Data Classification
- A Modified Jaya Algorithm for Mixed-Variable Optimization Problems
- An Improved Robust Fuzzy Algorithm for Unsupervised Learning
- Hybridizing the Cuckoo Search Algorithm with Different Mutation Operators for Numerical Optimization Problems
- An Efficient Lossless ROI Image Compression Using Wavelet-Based Modified Region Growing Algorithm
- Predicting Automatic Trigger Speed for Vehicle-Activated Signs
- Group Recommender Systems – An Evolutionary Approach Based on Multi-expert System for Consensus
- Enriching Documents by Linking Salient Entities and Lexical-Semantic Expansion
- A New Feature Selection Method for Sentiment Analysis in Short Text
- Optimizing Software Modularity with Minimum Possible Variations
- Optimizing the Self-Organizing Team Size Using a Genetic Algorithm in Agile Practices
- Aspect-Oriented Sentiment Analysis: A Topic Modeling-Powered Approach
- Feature Pair Index Graph for Clustering
- Tangramob: An Agent-Based Simulation Framework for Validating Urban Smart Mobility Solutions
- A New Algorithm Based on Magic Square and a Novel Chaotic System for Image Encryption
- Video Steganography Using Knight Tour Algorithm and LSB Method for Encrypted Data
- Clay-Based Brick Porosity Estimation Using Image Processing Techniques
- AGCS Technique to Improve the Performance of Neural Networks
- A Color Image Encryption Technique Based on Bit-Level Permutation and Alternate Logistic Maps
- A Hybrid of Deep CNN and Bidirectional LSTM for Automatic Speech Recognition
- Database Creation and Dialect-Wise Comparative Analysis of Prosodic Features for Punjabi Language
- Trapezoidal Linguistic Cubic Fuzzy TOPSIS Method and Application in a Group Decision Making Program
- Histopathological Image Segmentation Using Modified Kernel-Based Fuzzy C-Means and Edge Bridge and Fill Technique
- Proximal Support Vector Machine-Based Hybrid Approach for Edge Detection in Noisy Images
- Early Detection of Parkinson’s Disease by Using SPECT Imaging and Biomarkers
- Image Compression Based on Block SVD Power Method
- Noise Reduction Using Modified Wiener Filter in Digital Hearing Aid for Speech Signal Enhancement
- Secure Fingerprint Authentication Using Deep Learning and Minutiae Verification
- The Use of Natural Language Processing Approach for Converting Pseudo Code to C# Code
- Non-word Attributes’ Efficiency in Text Mining Authorship Prediction
- Design and Evaluation of Outlier Detection Based on Semantic Condensed Nearest Neighbor
- An Efficient Quality Inspection of Food Products Using Neural Network Classification
- Opposition Intensity-Based Cuckoo Search Algorithm for Data Privacy Preservation
- M-HMOGA: A New Multi-Objective Feature Selection Algorithm for Handwritten Numeral Classification
- Analogy-Based Approaches to Improve Software Project Effort Estimation Accuracy
- Linear Regression Supporting Vector Machine and Hybrid LOG Filter-Based Image Restoration
- Fractional Fuzzy Clustering and Particle Whale Optimization-Based MapReduce Framework for Big Data Clustering
- Implementation of Improved Ship-Iceberg Classifier Using Deep Learning
- Hybrid Approach for Face Recognition from a Single Sample per Person by Combining VLC and GOM
- Polarity Analysis of Customer Reviews Based on Part-of-Speech Subcategory
- A 4D Trajectory Prediction Model Based on the BP Neural Network
- A Blind Medical Image Watermarking for Secure E-Healthcare Application Using Crypto-Watermarking System
- Discriminating Healthy Wheat Grains from Grains Infected with Fusarium graminearum Using Texture Characteristics of Image-Processing Technique, Discriminant Analysis, and Support Vector Machine Methods
- License Plate Recognition in Urban Road Based on Vehicle Tracking and Result Integration
- Binary Genetic Swarm Optimization: A Combination of GA and PSO for Feature Selection
- Enhanced Twitter Sentiment Analysis Using Hybrid Approach and by Accounting Local Contextual Semantic
- Cloud Security: LKM and Optimal Fuzzy System for Intrusion Detection in Cloud Environment
- Power Average Operators of Trapezoidal Cubic Fuzzy Numbers and Application to Multi-attribute Group Decision Making

