Abstract
Separation is the primary consideration in cloud computing security. A series of security and safety problems would arise if a separation mechanism is not deployed appropriately, thus affecting the confidence of cloud end-users. In this paper, together with characteristics of cloud computing, the separation issue in cloud computing has been analyzed from the perspective of information flow. The process of information flow in cloud computing systems is formalized to propose corresponding separation rules. These rules have been verified in this paper and it is shown that the rules conform to non-interference security, thus ensuring the security and practicability of the proposed rules.
1 Introduction
Cloud computing is an emerging computing model based on separation and sharing. Sharing is one of the characteristics of cloud computing, while separation is a cornerstone of cloud computing security. If effective separation in a cloud computing environment failed to be implemented, a series of problems would arise, such as virtual machine escape, virtual machine stealing, and covert channels. Therefore, the issue of separation should be one of the primary security issues for a CSP (Cloud Service Provider). By ensuring reliable separation in a cloud computing environment, the confidence of users for the CSP can be enhanced and the acceptance of a CSP by users can be improved.
The study of separation can be discussed from two aspects: technologies and theories. For the technology part, the study of separation includes traditional network isolation, access control, encryption technology, isolation of virtualization level, as well as covert channels and side channels in cloud computing environments, etc. [4, 5, 6]. For the theory part, some studies have formalized description, analysis and verification on partial components in cloud computing. However, the cloud computing system is too large and too complex, thus making an overall formalized description and analysis difficult.
Rushby [1] and Kelem [2] have proposed proof conditions for secure separation for raw virtual machine systems. Rushby pointed out that the separation between virtual machines can be considered as “when a virtual machine performs an operation, there should be no perception in other virtual machines”. Meanwhile, Kelem described the separation requirements of virtual machine systems as “an internal operation of the virtual machine will not produce systematic state variation visible to other virtual machines”. However, with today’s point of view, these two conditions are more like achievable results of successful separation, rather than of proof conditions for separation.
The “perception” and “influence” between virtual machines fit the semantic of information flow provided by non-interference. Non-interference theory is an important method in the study of information flow. It provides a semantic to describe information flow within a system. In addition, it can also be applied to analyze the security of information flow in a system. Since the interaction process of the system can be effectively described by information flow, information flow has been widely applied to demonstrate the security of complex systems. In information flow analysis of cloud computing, there exists a series of related work, including critical information flow based on the Xen virtualization system discussed with DFL (Data Flow Logic), the issue of “conflict-of-interests” among different tenants analyzed in [3], with the application of a Chinese wall model. Meanwhile, there is also literature [4] describing a non-deterministic system with noninterference theory, indicating that non-interference theory is able to provide modeling and analysis for more complex systems (such as cloud computing systems). Thus, in this study, from the perspective of information flow based on the semantic theory of the separation concept and noninterference theory, we have proposed a separation relationship and requirements for a cloud computing system from a global point of view. The main contributions of this paper are as follows: the formal description of information flow in cloud computing system is given; a separation model of cloud computing system level has been proposed based on information flow; and it is proved that the security of a cloud computing system constructed based on the above separation model can be assured.
The organization of this paper is as follows. After a general introduction to separation issues and related work in cloud computing, background of cloud computing service architecture and non-interference theory are briefly discussed in Section II. The formal description of information flow in cloud computing is discussed in Section III, including the corresponding separation rules. In Section IV, security of the separation rules is proved with non-interference theory. Section V offers additional discussion. And finally, the paper is concluded in Section VI.
2 Background
2.1 Cloud computing service architecture
A typical architecture of cloud computing services has been described (Figure 1). Based on virtualization technology, the hardware resources (including CPU, memory, network and storage, etc.) will be encapsulated by a management center within the CSP and allocated to different virtual machines. Through the cloud computing services interface, the resources will provide service to end users in the form of virtual machines. At the same time, there are corresponding regulatory organizations in the CSP, managing and controlling the users, virtual machines and virtual machine interface, as well as virtualization layer.
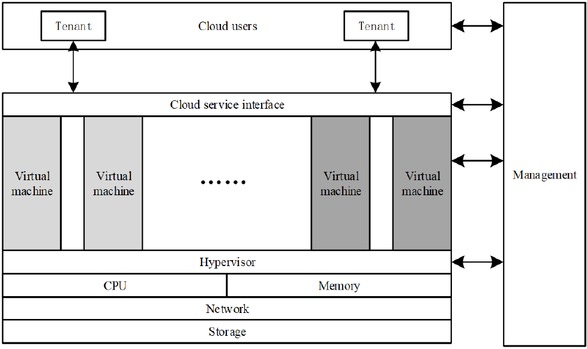
A typical cloud computing system
Three types of information flow in a cloud computing environment are presented here (Figure 1):
(i) Information flow between virtual machines. Since a lot of hardware resources are shared between virtual machines, there is a certain information flow between virtual machines, i.e., information flow at the virtual machine level. For this part of information flow, the information is mainly exchanged through the hypervisor; (ii) Information flow between users and CSP. Users send operating instructions to the infrastructure they have rented through the cloud services interface and receive corresponding feedback. Thus the information flow between user and CSP is formed, which is information flow at the cloud computing level; (iii) Management information flow. The management center of the cloud computing system responds to management instructions of the cloud computing system, thus generating the management information flow. This type of information flow is similar to that between virtual machines, while there are also great differences.
For the three types of information flow, different levels of separation are required. The information flow between virtual machines brings separation requirements for the virtual machine level. Separation for the virtual machine level is mainly reflected in the “interference” relationship between virtual machines, namely whether the state of a virtual machine would have observable effects on other virtual machines. For example, after the end of the life cycle of a virtual machine, the sharing resource may be released and there may be residual information in the released resources. Another example is whether the preemption of resources in one virtual machine would have effects on response speed of other virtual machines running in the same physical host. Furthermore, the information flow between users and the CSP bring separation requirements on the cloud computing level. Compared with the virtual machine level, the cloud computing level is more dynamic and there should be an independent centralized resource management mechanism. Therefore, separation on the cloud computing level is mainly reflected in the process of uniformly dynamical allocation and retrieving of resources for users, such as whether different tenants access the same resources and how communications are performed between different tenants.
2.2 Non-interference theory
Non-interference theory is a formal semantic for describing the relationship of information flow policies. It was originally applied to describe transitive information flow policies in a deterministic system, such as H ↣M and M ↣ L, and then H ↣ L, which makes information able to flow from H to L transitively. Later, Rushby [4] extended non-interference theory to intransitive policies, such as H ↣ D, D ↣ L, but
Rushby [4] also indicated that the “unwinding relation” in non-interference theory can not only be applied to prove the security of a system, but also be applied to construct a secure system by designing access control rules based on this theory. In recent years, Meyden [5] has pointed out and treated some deficiencies in Rushby’s intransitive non-interference theory. The “unwind theorem” in non-interference theory has been further improved and applied to prove system security. In this study, the semantic of non-interference defined by Meyden has been followed to make formalized description of a cloud computing system. Here are some basic definitions from Meyden.
A deterministic state machine M = {S, s_0, A, D, O, step, dom, obs} is applied to describe one system in which S is the set of states; represents the initial state of the system; A is the action set of system, a ∈ A represents that a is a single action, while α ∈ A* indicates α is a series of action sequences; D represents domains in the system; O represents the set of observed values observable to the domain; the function step: S × A → S represents the system in one state performing an action and then going forward to the next state; dom: A → D represents the domain which performs a specified action; and obs: S ×D → O represents the observed value of one domain in one state. In addition,↣ is applied to represent information flow policy between domains; thus we can simply use M (D,↣ ) to represent a system composed with D and↣ . The theorem has been expanded with the relationship family ∼u in a single D by Meyden:
If s∼ut, then obs(s, u)=obs(t, u) (the consistency of output, referred to as OC;
If s∼ut and s∼dom(a)t, then s • a∼dom(a)t • a (weak single-step consistency, referred to as WSC);
If dom
3 Description of cloud computing separation model
3.1 Formal description of information flow in cloud computing
On the basis of the definitions from non-interference theory introduced in Section 2, some supplementary definitions are required. The resources in cloud computing systems are represented by D = {PM, R, T1, T2, . . . , T}, in which PM indicates the resource address space retained by the management organizations, R represents the resource address space which can be allocated (remaining) in the system, and Ti represents the resource address space of tenant i, which is the address space of the virtual machine owned by tenant i. H is applied to represent the entire address space of cloud computing systems so clearly H = {PM ∪ R ∪ T1 ∪ . . . ∪ Tn}. V denotes the set of values of the address space, with A as the set of actions of the system, and S as the set of states of the system. We define the relevant functions as follows:
The address space mapping function addr: S × D → H represents an actual address space which a virtual machine corresponds to in a specific system state;
The tenant resource (virtual machine) membership function host: S × H → 2D represents the tenant resource (virtual machine) which an address space belongs to in a specific state;
The address space value function value: S × H → V represents the value of an address in a specific state in the system. Specifically, value(s,h)=0 means that the address h in state s is filled with 0, which is also the initialization and emptying operation of address h; when address space can be allocated, it must be initialized, namely ∀h ∈ R, s ∈ S, value (s, h) = 0;
The tenant resource (virtual machine) observation function ∀d ∈ D, obs (s, d) = {(t, value(s, t))|t ∈ D}represents that the observable content of d in state s is a two-tuple composed of one address space and the value in this address space.
With these definitions, a series of actions can be described by the access of address space from corresponding subject to object, such as the access of tenant to their leased infrastructure, management actions from management organization, as well as resources allocation and retrieving. In another words, the operation of an entire cloud computing system can be described with information flow. Follow the definition of non-interference theory,↣ is applied to represent information flow in a cloud computing system, such as T1 ↣ T2 indicating address space T1 of Tenant 1 flowing to address space T2 of Tenant 2, and
In addition, the management operations from a cloud computing management center on a cloud computing system resource constitute special information flow. Some special rules are required to describe this type of information flow. Intuitively, if a configuration change happened to a virtual machine in a cloud computing system (according to a tenant’s request or administrator adjustment), it would mean the resource it processed would vary. It is apparent that the new resources could be obtained only from idle resources, or a portion of the resources would be returned to the resource pool. Therefore, the following rules can be defined to accommodate the special management information flow.
Rule 1 (Resource management rule): In a cloud computing system M (D,↣ ), ∀t ∈ {Ti|i = 1, 2, . . . , n} , ∀h ∈ H, ∀a ∈ A, there are:
addr (s, h) t ∧ addr (step (s, a) , h) ⊂ t ⇒ addr (s, h) ⊂ R
addr (s, h) ⊆ t ∧ addr (step (s, a) , h) t ⇒ addr
(step (s, a) , h) ⊂ R
The two rules indicate that there is no direct overlap between the resources of different tenants; the resources cannot be directly transited from one tenant to another tenant, while there will always be a process of retrieving and re-allocation. Based on the resource management rule, we can make an independent description of management information flow:
In a cloud computing system M (D,↣ ), ∀t ∈ {Ti|i = 1, 2, . . . , n}, ∀h ∈ H, ∀a ∈ A, dom(a)⊪ t is applied to indicate that dom(a) produces a management information flow on t, if one of following conditions is met:
t ∉ addr (s, h) ∧ t ∈ addr(step (s, a) , h)
t ∈ addr (s, h) ∧ t ∉ addr(step (s, a) , h)
Although resources between tenants cannot be directly exchanged, there is still need for communication or sharing. Therefore, an appropriate pipe should be defined to describe the information exchange between tenants. For information exchange through a pipe, the fact is that a tenant reads data from one address and then writes data to another address space. Thus, a pipe can be considered as a passage of space address for which the tenant of the sender has read permission, while the tenant of the receiver has write permission. P represents the pipe in M (D,↣ ), the occupied address space is expressed with a pipe address function rs: P→ 2D, a pipe beginning function begin: P → D and a pipe terminating function ter: P → D which are all applied to describe the address space connected by the pipe. Obviously, begin(p)≠ter(p). In this paper, for simplicity, the following rules are defined to normalize the pipes:
Rule 2 (Pipe creation rule): In a cloud computing system M (D,↣), for ∀u, t ∈ {Ti|i = 1, 2, . . . , n}, and u ≠t:
u ∩ t ≠∅ ⇒ ∃p ∈ P ∧ s (p) = u ∩ t
∀p1,p2 ∈ P, p1 ∩ p2 = ∅
This rule describes a pipe between two tenants. Meanwhile, it also points out that there exists only zero or one pipe between different tenants, and in addition, no overlap is allowed between two pipes [11, 12, 13, 14].
Based on the definitions of management information flow and pipe, we can make further description on↣, that is:
∀u, t ∈ {Ti|i = 1, 2, . . . , n} , then ut ⇔ u ∩ t ≠∅ ∨ u |||= t.
3.2 Separation rules for cloud computing system
On the basis of the above formalized description on the information flow of a cloud computing system, we propose the required separation conditions in the cloud computing system:
Rule 3 (Separation rule for cloud computing system):
Rule 3-1: Resource separation
∀r ∈ R, value (S0, r) = 0
The first rule, Rule 3-1, indicates that the address space of different tenants should not be overlapped. The second rule indicates that allocatable resources in the system (including initial remaining resources and retrieved resources) should be in the emptied state in the resource pool. That is, a new resource obtained by tenants must be initialized, without residual data.
Rule 3-2: Pipe separation
∀r ∈ R, s ∈ S, a ∈ A, addr (step (s, a) , r)
≠addr (s, r) iff dom (a) = PM
∀p, begin (p) ⊆ PM ∨ ter (p) ⊆ PM
This set of rules reflects the separation rules for creating a pipe. Specifically, the pipe must be created between management organizations and tenants. In addition, resource management can only be performed by management organizations.
Rule 3-3: Tenant separation
∀ t ∈ {Ti|i = 1, 2, . . . , n} , then∃p, begin (p) = t ∨ ter (p) = t
Rule 3-3 indicates that each tenant must be controlled by management organizations.
Rule 3-4: Single step consistency in separation
∀s1, s2 ∈ S, h ∈ H, a ∈ A, value (s1, h) = value (s2, h)
⇒ value (step (s1, a) , h) = vaule(step (s2, a) , h)
Rule 3-4 indicates that single step consistency should be reached in a cloud computing system. If the values of one address space are the same in two states, when the system sends the same action, the value in this address space should remain the same.
These four sets of rules indicate the separation ruleswhich should be followed in a cloud computing environment. They are closely related to information flow in the cloud computing system, covering the information flow control between virtual machines, information flow control between tenants, as well as the separation roles played by management information flow [15, 16, 17, 18].
4 Security analysis
Rule 3 guarantees secure separation in a cloud computing system, and also provides material for implementing separation in a cloud computing system. In this section, based on non-interference theory, the security embodied in Rule 3 will be analyzed.
Lemma 1 (Observation of single-step consistency): If the cloud computing system M (D, ↣ ) can satisfy the rules in Rule 3, then
∀a ∈ A, ∀s1, s2 ∈ S, t ∈ {Ti|i = 1, 2, . . . , n}
obs (s1, t) = obs (s2, t) ⇒ obs (step (s1, a) , t)
= obs(step (s2, a) , t)
Proof: According to the definition of the obs function, the observed result should be a two-tuple composed of address space and value in this address space; thus, action a should be discussed in two cases.
CASE: a is a simple operation of address writing. For such an action, a can only change the value in the address space, while the range of address space will not be changed. Therefore, simply according to Rule 3-4,
vaule (s1, h) = value (s2, h)
⇒ value (step (s1, a) , h) = value(step (s2, a) , h),
we have obs (step (s1, a) , t) = obs(step (s2, a) , t).
CASE: a is a management operation. For such an action, a can change the range of address space, while the value in the original address space will not be changed. When the action a is to compress the address space, obviously, the observed value within the address space will not be changed; when the action is to expand the address space, because the newly allocated address space h’ is the address space after initialization, there will be
value (s1, h′) = value (s2, h′) =
value (step (s1, a) , h′) = value (step (s2, a) , h′) = 0.
The value in the original address space will not be influenced, so that.
Lemma 1 has been proved.↣
Lemma 2 (secure separation theorem): If the cloud computing system M (D, ↣ ) satisfies the rules in Rule 3, then M is non-interference secure with respect to “↣”.
Proof: To prove M is non-interference secure with respect to “↣ ”, we need to respectively prove that, for “↣ ”, M satisfies OC, WSC and LR according to Theorem 1.
In M (D,↣), the relation of M on D is defined ∼ t, s1 ∼ s2 if obs(s1, t) = obs(s2, t). Obviously OC can be satisfied.
According to Lemma 1, we can see
That is, WSC can be satisfied;
Since dom(a)
Lemma 2 has been proved.
Lemma 2 proves that the separation can be effectively ensured in a cloud computing system constructed based on Rule 3.
5 Discussion
Resources in a cloud computing system, such as computing resources of CPU time slice, storage resources of memory, disk and network etc., can be described with address space. The information flow in a cloud computing system can also be described by writing operations on different address spaces. Therefore, when discussing separation based on information flow, the focus should mainly be on the separation of resources, which is the separation of address space. Based on the separation rules proposed in this study, a separation model has been constructed in a cloud computing system. The role of PM has been emphasized in this model: the actions of retrieving, allocation and scheduling of any resources (address space) must be completed by PM. In this model, PM has been placed in the central position of the entire cloud computing system. As shown in Figure 2, the different tenants T1, T2, T3, communicate with PM through pipes P1, P2, P3, respectively. Through pipe P4, the appropriate resources will be scheduled (allocating or retrieving) to different tenants (dashed arrows in Figure 2) by PM.

The cloud computing system based on Rule 3 and the allocation of resources scheduled through pipes
Actually, the cloud computing system constructed based on Rule 3 is more suitable to construct a cloud computing system requiring strict separation. In addition, the separation security between this system and an existing actual system can also be analyzed to a certain extent. For example, in the architecture of Xen [19], each virtual machine communicates with VMM through an event channel, while there is no channel between virtual machines. VMM provides corresponding CPU resources for virtual machines, as well as physical memory mapping (or dynamic adjustment such as a balloon driver) and I/O operations. However, in some other actual systems, the collaborative tenants should and must perform job division and collaboration through the network. In this case, besides the rules proposed in this study, some new sharing management rules to accommodate a wider range of application scenes are required.
6 Conclusion
Security is the core issue of cloud computing, while separation is one of the most important security measures. In this paper, separation in a cloud computing system has been analyzed from the perspective of information flow, and a series of security rules have been proposed which can be proved in theory. Secure separation can be ensured in a cloud computing system constructed based on this security rule. Our study provides guidance for the construction of cloud computing systems and it also provides reference for the consistency between actual systems and strategy. Learning from the assessment and validation method in TCSEC and CC, the rules proposed in this study can also provide a method and guidance for verifying the separation in existing cloud computing systems. Therefore, it also provides references for analyzing security of existing cloud computing systems, as well as designing and constructing future trusted and secure cloud computing systems.
Acknowledgement
The research is supported by Henan Programs for Science and Technology Development (No. 182102210329).
References
[1] Rushby J.M., Proof of separability a verification technique for a class of security kernels, Int. Symp. Program.. Spring. Berlin Heidelberg, 1982, 352-357.10.1007/3-540-11494-7_23Search in Google Scholar
[2] Kelem N.L., Feiertag R.J., A separation model for virtual machine monitors, Res. Security Priv., 1991. Proc. 1991 IEEE Comput. Soc. Sym. IEEE, 1991.Search in Google Scholar
[3] Wu R.Y., Information flow control in cloud computing. Collaborative computing: networking, applications and worksharing (CollaborateCom), 2010 6th Int. Conf. on. IEEE.10.4108/icst.trustcol.2010.1Search in Google Scholar
[4] Rushby J., Noninterference, transitivity, and channel-control security policies, SRI Int., Comput. Sci. Lab., 1992.Search in Google Scholar
[5] Van D.M.R., What, indeed, is intransitive noninterference?, Computer security–ESORICS 2007, Spring. Berlin Heidelberg, 2007, 235-250.10.1007/978-3-540-74835-9_16Search in Google Scholar
[6] Seshadri A., Luk M., Qu N., Perrig A. SecVisor: A tiny hypervisor to provide lifetime kernel code integrity for commodity oses, ACM SIGOPS Operating Syst. Rev, 2007, 41(6), 335-350.10.1145/1294261.1294294Search in Google Scholar
[7] Dai Y.H., Design and verification of a lightweight reliable virtual machine monitor for a many-core architecture. Front. Comput. Sci., 2013, 7(1), 34-43.10.1007/s11704-012-2084-0Search in Google Scholar
[8] Sierra L.A., Yepes V., Garcia-Segura T., Pellicer E., Bayesian network method for decision-making about the social sustainability of infrastructure projects, J. Clean. Prod., 2018, 176, 521-534.10.1016/j.jclepro.2017.12.140Search in Google Scholar
[9] Hoang T.S., Abstractions of non-interference security: probabilistic versus possibilistic, Form. Aspects Comput., 2014, 26(1), 169-194.10.1007/s00165-012-0237-4Search in Google Scholar
[10] Bacon J., Information flow control for secure cloud computing, IEEE Trans, Network Serv. Manage., 2014, 11(1), 76-89.10.1109/TNSM.2013.122313.130423Search in Google Scholar
[11] Jean B., David E., Thomas P., Jat S., Ioannis P., Peter P., Computer system evaluation criteria, IEEE Trans. Network Serv. Manage., 11(1), 76-89.Search in Google Scholar
[12] Xu L.Q., Active and personalized services in an information security engineering cloud based on ISO/IEC 15408. Intelligence and security informatics, Spring. Int. Publishing, 2014, 35-48.10.1007/978-3-319-06677-6_4Search in Google Scholar
[13] Common criteria for information technology security evaluation (CC), Version 3.1, revision 4, September, 2012.Search in Google Scholar
[14] Sharip Z., Yusoff F.M., Plankton community characteristics of natural and man-made tropical lakes, J. Environ. Biol., 2017, 38(6), 1365-1374.10.22438/jeb/38/6/MRN-356Search in Google Scholar
[15] Costamagna A., Drigo M., Martini M., Sona B., Venturino E., A model for the operations to render epidemic-free a hog farm infected by the aujeszky disease, Appl. Math. Nonlinear Sci., 2016, 1(1), 207-228.10.21042/AMNS.2016.1.00016Search in Google Scholar
[16] Peng W., Ge S., Ebadi A.G., Hisoriev H., Esfahani M.J., Syngas production by catalytic co-gasification of coal-biomass blends in a circulating fluidized bed gasifier. J. Clean. Prod., 2017, 168, 1513-1517.10.1016/j.jclepro.2017.06.233Search in Google Scholar
[17] Gao W., Wang Y., Wang W., Shi L., The first multiplication atom-bond connectivity index of molecular structures in drugs, Saudi Pharm. J., 2017, 25(4), 548-555.10.1016/j.jsps.2017.04.021Search in Google Scholar PubMed PubMed Central
[18] Dewasurendra M., Vajravelu K., On the method of inverse mapping for solutions of coupled systems of nonlinear differential equations arising in nanofluid flow, heat and mass transfer, Appl. Math. Nonlinear Sci., 2018, 3(1), 1-14.10.21042/AMNS.2018.1.00001Search in Google Scholar
[19] Barham P., Xen and the art of virtualization, ACM SIGOPS Operating Syst. Rev., 2003, 37(5), 164-177.10.1145/945445.945462Search in Google Scholar
© 2019 W. Ma et al., published by De Gruyter
This work is licensed under the Creative Commons Attribution 4.0 International License.
Articles in the same Issue
- Regular Articles
- Non-equilibrium Phase Transitions in 2D Small-World Networks: Competing Dynamics
- Harmonic waves solution in dual-phase-lag magneto-thermoelasticity
- Multiplicative topological indices of honeycomb derived networks
- Zagreb Polynomials and redefined Zagreb indices of nanostar dendrimers
- Solar concentrators manufacture and automation
- Idea of multi cohesive areas - foundation, current status and perspective
- Derivation method of numerous dynamics in the Special Theory of Relativity
- An application of Nwogu’s Boussinesq model to analyze the head-on collision process between hydroelastic solitary waves
- Competing Risks Model with Partially Step-Stress Accelerate Life Tests in Analyses Lifetime Chen Data under Type-II Censoring Scheme
- Group velocity mismatch at ultrashort electromagnetic pulse propagation in nonlinear metamaterials
- Investigating the impact of dissolved natural gas on the flow characteristics of multicomponent fluid in pipelines
- Analysis of impact load on tubing and shock absorption during perforating
- Energy characteristics of a nonlinear layer at resonant frequencies of wave scattering and generation
- Ion charge separation with new generation of nuclear emulsion films
- On the influence of water on fragmentation of the amino acid L-threonine
- Formulation of heat conduction and thermal conductivity of metals
- Displacement Reliability Analysis of Submerged Multi-body Structure’s Floating Body for Connection Gaps
- Deposits of iron oxides in the human globus pallidus
- Integrability, exact solutions and nonlinear dynamics of a nonisospectral integral-differential system
- Bounds for partition dimension of M-wheels
- Visual Analysis of Cylindrically Polarized Light Beams’ Focal Characteristics by Path Integral
- Analysis of repulsive central universal force field on solar and galactic dynamics
- Solitary Wave Solution of Nonlinear PDEs Arising in Mathematical Physics
- Understanding quantum mechanics: a review and synthesis in precise language
- Plane Wave Reflection in a Compressible Half Space with Initial Stress
- Evaluation of the realism of a full-color reflection H2 analog hologram recorded on ultra-fine-grain silver-halide material
- Graph cutting and its application to biological data
- Time fractional modified KdV-type equations: Lie symmetries, exact solutions and conservation laws
- Exact solutions of equal-width equation and its conservation laws
- MHD and Slip Effect on Two-immiscible Third Grade Fluid on Thin Film Flow over a Vertical Moving Belt
- Vibration Analysis of a Three-Layered FGM Cylindrical Shell Including the Effect Of Ring Support
- Hybrid censoring samples in assessment the lifetime performance index of Chen distributed products
- Study on the law of coal resistivity variation in the process of gas adsorption/desorption
- Mapping of Lineament Structures from Aeromagnetic and Landsat Data Over Ankpa Area of Lower Benue Trough, Nigeria
- Beta Generalized Exponentiated Frechet Distribution with Applications
- INS/gravity gradient aided navigation based on gravitation field particle filter
- Electrodynamics in Euclidean Space Time Geometries
- Dynamics and Wear Analysis of Hydraulic Turbines in Solid-liquid Two-phase Flow
- On Numerical Solution Of The Time Fractional Advection-Diffusion Equation Involving Atangana-Baleanu-Caputo Derivative
- New Complex Solutions to the Nonlinear Electrical Transmission Line Model
- The effects of quantum spectrum of 4 + n-dimensional water around a DNA on pure water in four dimensional universe
- Quantum Phase Estimation Algorithm for Finding Polynomial Roots
- Vibration Equation of Fractional Order Describing Viscoelasticity and Viscous Inertia
- The Errors Recognition and Compensation for the Numerical Control Machine Tools Based on Laser Testing Technology
- Evaluation and Decision Making of Organization Quality Specific Immunity Based on MGDM-IPLAO Method
- Key Frame Extraction of Multi-Resolution Remote Sensing Images Under Quality Constraint
- Influences of Contact Force towards Dressing Contiguous Sense of Linen Clothing
- Modeling and optimization of urban rail transit scheduling with adaptive fruit fly optimization algorithm
- The pseudo-limit problem existing in electromagnetic radiation transmission and its mathematical physics principle analysis
- Chaos synchronization of fractional–order discrete–time systems with different dimensions using two scaling matrices
- Stress Characteristics and Overload Failure Analysis of Cemented Sand and Gravel Dam in Naheng Reservoir
- A Big Data Analysis Method Based on Modified Collaborative Filtering Recommendation Algorithms
- Semi-supervised Classification Based Mixed Sampling for Imbalanced Data
- The Influence of Trading Volume, Market Trend, and Monetary Policy on Characteristics of the Chinese Stock Exchange: An Econophysics Perspective
- Estimation of sand water content using GPR combined time-frequency analysis in the Ordos Basin, China
- Special Issue Applications of Nonlinear Dynamics
- Discrete approximate iterative method for fuzzy investment portfolio based on transaction cost threshold constraint
- Multi-objective performance optimization of ORC cycle based on improved ant colony algorithm
- Information retrieval algorithm of industrial cluster based on vector space
- Parametric model updating with frequency and MAC combined objective function of port crane structure based on operational modal analysis
- Evacuation simulation of different flow ratios in low-density state
- A pointer location algorithm for computer visionbased automatic reading recognition of pointer gauges
- A cloud computing separation model based on information flow
- Optimizing model and algorithm for railway freight loading problem
- Denoising data acquisition algorithm for array pixelated CdZnTe nuclear detector
- Radiation effects of nuclear physics rays on hepatoma cells
- Special issue: XXVth Symposium on Electromagnetic Phenomena in Nonlinear Circuits (EPNC2018)
- A study on numerical integration methods for rendering atmospheric scattering phenomenon
- Wave propagation time optimization for geodesic distances calculation using the Heat Method
- Analysis of electricity generation efficiency in photovoltaic building systems made of HIT-IBC cells for multi-family residential buildings
- A structural quality evaluation model for three-dimensional simulations
- WiFi Electromagnetic Field Modelling for Indoor Localization
- Modeling Human Pupil Dilation to Decouple the Pupillary Light Reflex
- Principal Component Analysis based on data characteristics for dimensionality reduction of ECG recordings in arrhythmia classification
- Blinking Extraction in Eye gaze System for Stereoscopy Movies
- Optimization of screen-space directional occlusion algorithms
- Heuristic based real-time hybrid rendering with the use of rasterization and ray tracing method
- Review of muscle modelling methods from the point of view of motion biomechanics with particular emphasis on the shoulder
- The use of segmented-shifted grain-oriented sheets in magnetic circuits of small AC motors
- High Temperature Permanent Magnet Synchronous Machine Analysis of Thermal Field
- Inverse approach for concentrated winding surface permanent magnet synchronous machines noiseless design
- An enameled wire with a semi-conductive layer: A solution for a better distibution of the voltage stresses in motor windings
- High temperature machines: topologies and preliminary design
- Aging monitoring of electrical machines using winding high frequency equivalent circuits
- Design of inorganic coils for high temperature electrical machines
- A New Concept for Deeper Integration of Converters and Drives in Electrical Machines: Simulation and Experimental Investigations
- Special Issue on Energetic Materials and Processes
- Investigations into the mechanisms of electrohydrodynamic instability in free surface electrospinning
- Effect of Pressure Distribution on the Energy Dissipation of Lap Joints under Equal Pre-tension Force
- Research on microstructure and forming mechanism of TiC/1Cr12Ni3Mo2V composite based on laser solid forming
- Crystallization of Nano-TiO2 Films based on Glass Fiber Fabric Substrate and Its Impact on Catalytic Performance
- Effect of Adding Rare Earth Elements Er and Gd on the Corrosion Residual Strength of Magnesium Alloy
- Closed-die Forging Technology and Numerical Simulation of Aluminum Alloy Connecting Rod
- Numerical Simulation and Experimental Research on Material Parameters Solution and Shape Control of Sandwich Panels with Aluminum Honeycomb
- Research and Analysis of the Effect of Heat Treatment on Damping Properties of Ductile Iron
- Effect of austenitising heat treatment on microstructure and properties of a nitrogen bearing martensitic stainless steel
- Special Issue on Fundamental Physics of Thermal Transports and Energy Conversions
- Numerical simulation of welding distortions in large structures with a simplified engineering approach
- Investigation on the effect of electrode tip on formation of metal droplets and temperature profile in a vibrating electrode electroslag remelting process
- Effect of North Wall Materials on the Thermal Environment in Chinese Solar Greenhouse (Part A: Experimental Researches)
- Three-dimensional optimal design of a cooled turbine considering the coolant-requirement change
- Theoretical analysis of particle size re-distribution due to Ostwald ripening in the fuel cell catalyst layer
- Effect of phase change materials on heat dissipation of a multiple heat source system
- Wetting properties and performance of modified composite collectors in a membrane-based wet electrostatic precipitator
- Implementation of the Semi Empirical Kinetic Soot Model Within Chemistry Tabulation Framework for Efficient Emissions Predictions in Diesel Engines
- Comparison and analyses of two thermal performance evaluation models for a public building
- A Novel Evaluation Method For Particle Deposition Measurement
- Effect of the two-phase hybrid mode of effervescent atomizer on the atomization characteristics
- Erratum
- Integrability analysis of the partial differential equation describing the classical bond-pricing model of mathematical finance
- Erratum to: Energy converting layers for thin-film flexible photovoltaic structures
Articles in the same Issue
- Regular Articles
- Non-equilibrium Phase Transitions in 2D Small-World Networks: Competing Dynamics
- Harmonic waves solution in dual-phase-lag magneto-thermoelasticity
- Multiplicative topological indices of honeycomb derived networks
- Zagreb Polynomials and redefined Zagreb indices of nanostar dendrimers
- Solar concentrators manufacture and automation
- Idea of multi cohesive areas - foundation, current status and perspective
- Derivation method of numerous dynamics in the Special Theory of Relativity
- An application of Nwogu’s Boussinesq model to analyze the head-on collision process between hydroelastic solitary waves
- Competing Risks Model with Partially Step-Stress Accelerate Life Tests in Analyses Lifetime Chen Data under Type-II Censoring Scheme
- Group velocity mismatch at ultrashort electromagnetic pulse propagation in nonlinear metamaterials
- Investigating the impact of dissolved natural gas on the flow characteristics of multicomponent fluid in pipelines
- Analysis of impact load on tubing and shock absorption during perforating
- Energy characteristics of a nonlinear layer at resonant frequencies of wave scattering and generation
- Ion charge separation with new generation of nuclear emulsion films
- On the influence of water on fragmentation of the amino acid L-threonine
- Formulation of heat conduction and thermal conductivity of metals
- Displacement Reliability Analysis of Submerged Multi-body Structure’s Floating Body for Connection Gaps
- Deposits of iron oxides in the human globus pallidus
- Integrability, exact solutions and nonlinear dynamics of a nonisospectral integral-differential system
- Bounds for partition dimension of M-wheels
- Visual Analysis of Cylindrically Polarized Light Beams’ Focal Characteristics by Path Integral
- Analysis of repulsive central universal force field on solar and galactic dynamics
- Solitary Wave Solution of Nonlinear PDEs Arising in Mathematical Physics
- Understanding quantum mechanics: a review and synthesis in precise language
- Plane Wave Reflection in a Compressible Half Space with Initial Stress
- Evaluation of the realism of a full-color reflection H2 analog hologram recorded on ultra-fine-grain silver-halide material
- Graph cutting and its application to biological data
- Time fractional modified KdV-type equations: Lie symmetries, exact solutions and conservation laws
- Exact solutions of equal-width equation and its conservation laws
- MHD and Slip Effect on Two-immiscible Third Grade Fluid on Thin Film Flow over a Vertical Moving Belt
- Vibration Analysis of a Three-Layered FGM Cylindrical Shell Including the Effect Of Ring Support
- Hybrid censoring samples in assessment the lifetime performance index of Chen distributed products
- Study on the law of coal resistivity variation in the process of gas adsorption/desorption
- Mapping of Lineament Structures from Aeromagnetic and Landsat Data Over Ankpa Area of Lower Benue Trough, Nigeria
- Beta Generalized Exponentiated Frechet Distribution with Applications
- INS/gravity gradient aided navigation based on gravitation field particle filter
- Electrodynamics in Euclidean Space Time Geometries
- Dynamics and Wear Analysis of Hydraulic Turbines in Solid-liquid Two-phase Flow
- On Numerical Solution Of The Time Fractional Advection-Diffusion Equation Involving Atangana-Baleanu-Caputo Derivative
- New Complex Solutions to the Nonlinear Electrical Transmission Line Model
- The effects of quantum spectrum of 4 + n-dimensional water around a DNA on pure water in four dimensional universe
- Quantum Phase Estimation Algorithm for Finding Polynomial Roots
- Vibration Equation of Fractional Order Describing Viscoelasticity and Viscous Inertia
- The Errors Recognition and Compensation for the Numerical Control Machine Tools Based on Laser Testing Technology
- Evaluation and Decision Making of Organization Quality Specific Immunity Based on MGDM-IPLAO Method
- Key Frame Extraction of Multi-Resolution Remote Sensing Images Under Quality Constraint
- Influences of Contact Force towards Dressing Contiguous Sense of Linen Clothing
- Modeling and optimization of urban rail transit scheduling with adaptive fruit fly optimization algorithm
- The pseudo-limit problem existing in electromagnetic radiation transmission and its mathematical physics principle analysis
- Chaos synchronization of fractional–order discrete–time systems with different dimensions using two scaling matrices
- Stress Characteristics and Overload Failure Analysis of Cemented Sand and Gravel Dam in Naheng Reservoir
- A Big Data Analysis Method Based on Modified Collaborative Filtering Recommendation Algorithms
- Semi-supervised Classification Based Mixed Sampling for Imbalanced Data
- The Influence of Trading Volume, Market Trend, and Monetary Policy on Characteristics of the Chinese Stock Exchange: An Econophysics Perspective
- Estimation of sand water content using GPR combined time-frequency analysis in the Ordos Basin, China
- Special Issue Applications of Nonlinear Dynamics
- Discrete approximate iterative method for fuzzy investment portfolio based on transaction cost threshold constraint
- Multi-objective performance optimization of ORC cycle based on improved ant colony algorithm
- Information retrieval algorithm of industrial cluster based on vector space
- Parametric model updating with frequency and MAC combined objective function of port crane structure based on operational modal analysis
- Evacuation simulation of different flow ratios in low-density state
- A pointer location algorithm for computer visionbased automatic reading recognition of pointer gauges
- A cloud computing separation model based on information flow
- Optimizing model and algorithm for railway freight loading problem
- Denoising data acquisition algorithm for array pixelated CdZnTe nuclear detector
- Radiation effects of nuclear physics rays on hepatoma cells
- Special issue: XXVth Symposium on Electromagnetic Phenomena in Nonlinear Circuits (EPNC2018)
- A study on numerical integration methods for rendering atmospheric scattering phenomenon
- Wave propagation time optimization for geodesic distances calculation using the Heat Method
- Analysis of electricity generation efficiency in photovoltaic building systems made of HIT-IBC cells for multi-family residential buildings
- A structural quality evaluation model for three-dimensional simulations
- WiFi Electromagnetic Field Modelling for Indoor Localization
- Modeling Human Pupil Dilation to Decouple the Pupillary Light Reflex
- Principal Component Analysis based on data characteristics for dimensionality reduction of ECG recordings in arrhythmia classification
- Blinking Extraction in Eye gaze System for Stereoscopy Movies
- Optimization of screen-space directional occlusion algorithms
- Heuristic based real-time hybrid rendering with the use of rasterization and ray tracing method
- Review of muscle modelling methods from the point of view of motion biomechanics with particular emphasis on the shoulder
- The use of segmented-shifted grain-oriented sheets in magnetic circuits of small AC motors
- High Temperature Permanent Magnet Synchronous Machine Analysis of Thermal Field
- Inverse approach for concentrated winding surface permanent magnet synchronous machines noiseless design
- An enameled wire with a semi-conductive layer: A solution for a better distibution of the voltage stresses in motor windings
- High temperature machines: topologies and preliminary design
- Aging monitoring of electrical machines using winding high frequency equivalent circuits
- Design of inorganic coils for high temperature electrical machines
- A New Concept for Deeper Integration of Converters and Drives in Electrical Machines: Simulation and Experimental Investigations
- Special Issue on Energetic Materials and Processes
- Investigations into the mechanisms of electrohydrodynamic instability in free surface electrospinning
- Effect of Pressure Distribution on the Energy Dissipation of Lap Joints under Equal Pre-tension Force
- Research on microstructure and forming mechanism of TiC/1Cr12Ni3Mo2V composite based on laser solid forming
- Crystallization of Nano-TiO2 Films based on Glass Fiber Fabric Substrate and Its Impact on Catalytic Performance
- Effect of Adding Rare Earth Elements Er and Gd on the Corrosion Residual Strength of Magnesium Alloy
- Closed-die Forging Technology and Numerical Simulation of Aluminum Alloy Connecting Rod
- Numerical Simulation and Experimental Research on Material Parameters Solution and Shape Control of Sandwich Panels with Aluminum Honeycomb
- Research and Analysis of the Effect of Heat Treatment on Damping Properties of Ductile Iron
- Effect of austenitising heat treatment on microstructure and properties of a nitrogen bearing martensitic stainless steel
- Special Issue on Fundamental Physics of Thermal Transports and Energy Conversions
- Numerical simulation of welding distortions in large structures with a simplified engineering approach
- Investigation on the effect of electrode tip on formation of metal droplets and temperature profile in a vibrating electrode electroslag remelting process
- Effect of North Wall Materials on the Thermal Environment in Chinese Solar Greenhouse (Part A: Experimental Researches)
- Three-dimensional optimal design of a cooled turbine considering the coolant-requirement change
- Theoretical analysis of particle size re-distribution due to Ostwald ripening in the fuel cell catalyst layer
- Effect of phase change materials on heat dissipation of a multiple heat source system
- Wetting properties and performance of modified composite collectors in a membrane-based wet electrostatic precipitator
- Implementation of the Semi Empirical Kinetic Soot Model Within Chemistry Tabulation Framework for Efficient Emissions Predictions in Diesel Engines
- Comparison and analyses of two thermal performance evaluation models for a public building
- A Novel Evaluation Method For Particle Deposition Measurement
- Effect of the two-phase hybrid mode of effervescent atomizer on the atomization characteristics
- Erratum
- Integrability analysis of the partial differential equation describing the classical bond-pricing model of mathematical finance
- Erratum to: Energy converting layers for thin-film flexible photovoltaic structures

