Abstract
Timetabling problems are specific types of scheduling problems that deal with assigning certain events to the timeslots. This assigning is subject to certain hard constraints that should be achieved to get a feasible timetable and soft constraints that must meet as many as possible during forming a feasible schedule. This paper introduces an adaptive tabu search. Eleven benchmark datasets of the year 2002 are applied to show the effectiveness of the introduced algorithm. These datasets consist of 5-small, 5-medium, and 1-large dataset. As compared to other methods from previous works, the proposed algorithm produces excellent timetables, in comparison with the algorithms as well as the current results, the mathematical results showed the high effectiveness of the suggested algorithm. It has a minor deficit on the medium or the small problem adaptive Tabu, and the tabu search relies on the tabu list and penalty cost when the change in the penalty cost is checked; if it is still unchanged for the period of iterations (1,000 iterations), the tabu list reduces automatically by (−2); furthermore, the tabu list remains constant.
1 Introduction
In reality, the timetabling problem is a challenging task in constructing a well-behaved solution [1]. The problem’s size represents the main difficulty. This difficulty includes a sizeable volume of rooms, courses, teachers, and students that are correlated in several ways throughout conditions and objectives. Thus, a huge amount of variables and constraints should be taken into consideration during the procedure of each solution [2]. In the problem of course timetabling, a heuristic algorithm is applied to obtain a feasible starting solution. It begins by assigning a course to time slots. Scheduling the course is the first step in the strategy of starting. Since the course involves a sizeable number of students, it is very hard to reschedule. To place a course in the best appropriate time slots, it is recommended to construct a schedule based on a blank timetable [3]. This technique is known as least saturation degree. The academic institution faces the problem of scheduling appointments of the courses and examinations in every semester. This problem raises due to the increasing number of students, courses, exams, rooms, and the invigilator constraints. An automated timetabling system can produce functional and accurate schedules; the types of timetabling at educational institutions (schools and universities) are manual, semi-automated, and fully automated timetabling. A survey conducted by Iyad Abu Doush et al. (2008) in 56 universities in the UK discovered that only 58% (32 universities) uses the computer for preparing their examination timetable while 21% (11 universities) has a scheduling system [4]. Hard requirements must be firmly adhered to, and they take precedence over soft constraints. If a timetable meets all hard restrictions, it is said to be feasible. Event clash limitations are likely to be prevalent hard constraints in educational scheduling issues. These constraints typically occur when a single resource is requested by two events at the same time, which is impossible to do. Almost every educational institution has this constraint [5].
This paper presents the problem of university course timetabling examined using an adaptive tabu search algorithm to enhance the initial feasible solution. Eleven benchmark datasets presented by Socha et al. are employed for testing this approach. The findings appear that our method can produce excellent solutions in comparison with other methods in the literature.
This paper contributes to developing a tabu search algorithm, an adaptive tabu list to be compatible resulting in a solution for the scheduling a timetable problem.
The structure of this paper is logically organized where the next section portrays the related works. A brief explanation of the course-timetabling problem is given in Section 3.
The meta-heuristic algorithm and its application to the course-timetabling problem are described in Section 4. Section 5 presents experimental results and a comparison between techniques from the related work, and Section 6 reports brief concluding comments.
2 Related works
Solving problems of course timetabling and specifically enrolment-based have been proposed in the last three decades. Four categories of automatic timetabling procedures can be extracted from wide-ranging literature reviews. The first category deals the timetabling as graph problems and is known as sequential methods. The second category models the timetabling as a group of events (variables) and assigns their values (resources such as rooms and teachers) to achieve several soft and hard constraints. It is known as the constraint-based method [6]. In the third category, which is called the cluster method, the problem is partitioned into several event sets. The last category is called the meta-heuristic method, which includes different algorithms such as Ant Colony Optimization (ACO), neural networks, tabu search, simulated annealing, and genetic algorithms [7].
Besides, many innovative approaches were recently developed for solving timetabling problems, which involve hyper-heuristics, fuzzy, and case-based reasoning approaches [8].
In course timetabling, the enrolment-based problem is focused, which can be partitioned into six approaches: hyper-heuristic, population-based, hybridization meta-heuristic, meta-heuristic, graph-based, and constraint-based approaches.
In practice, meta-heuristics have recently achieved great usefulness in almost solving timetabling problems. The capability of escaping from local optima and handling a wide range of constraints is the key benefit of such methods [3].
To work out timetable problems of a Spanish secondary school [9], an approach of two stages is introduced. In the first stage, a heuristic algorithm is employed to produce the early answer. Improving this answer is done in the next stage using a tabu search algorithm. The Hyper-heuristic approach is applied in another work [10] to move up the generalization level of the computerized timetabling systems using a tabu search algorithm. The system was established to solve the problems of nurse scheduling and to achieve the course timetabling instances. Moreover, the course timetabling problem of enrollment-based was also solved using the tabu-based memetic algorithm, as introduced in ref. [11]. Incorporating a tabu list enhanced the effectiveness of the solutions and controlling the selections of neighborhood structures using the memetic algorithm [12] presented the tabu Search algorithm as a solution to a practical problem of university timetabling. Nine practical cases have been tested in that work. Further work focused on the lecture lengths at the University of Kebangsaan Malaysia, Faculty of Engineering, to resolve the university course timetable, using multi-neighborhood structures and tabu search [13]. In contrast, the winner of the 2004 International Timetabling Competition applied an approach of three stages to solve problems of course timetabling. Out of 20 examples in the competition, the approach has achieved 13 best results. Feasible solutions, as an enhancement stage for the problem of course timetabling, were obtained [14], using a simulated annealing algorithm. Two types of neighborhood structures were the basis of this enhancement. In another work [15], to answer the post-enrollment course timetabling (PE-CTT), a simulated annealing algorithm was also applied within a metaheuristic approach. As compared to previous works, this work showed improved results regardless of the fact of using a somewhat straightforward single-step algorithm, against using complicated multi-step algorithms of most of the previous solvers. For complicated cases of university course timetabling, [16] introduced a non-linear great deluge algorithm. It is an extended version of the traditional great deluge algorithm. In contrast, a hybrid of Kempe-chain neighborhood structure with a great delug algorithm [17] was introduced to resolve the timetabling problem. This approach can compete with other available approaches. Afterwards, the great deluge algorithm is combined with an electromagnetic-like mechanism to obtain a new meta-heuristic [18]. The most important goal of the hyper-heuristic approach is to build up a general optimization approach that can be reused in diverse problem cases as well as a range of various problems. Lastly, a novel method was introduced for answering the problems of university course timetabling, which consists of two ant colony systems with hybrids. The first system combined the ant colony system and a simulated annealing algorithm, while the second system combined the ant colony system with a tabu search algorithm [19]. In the literature, Exact algorithms and approximation algorithms are the two types of algorithms that are utilized to solve the timetabling problem. In truth, precise algorithms can uncover the best answers; on the other hand, in the scheduling problem, the exact algorithms frame brute-force style. All these issues resulted in an exponential growth rate in the search space; therefore, these kinds of algorithms could only apply for the small in size issues. However, approximation algorithms are based on optimal solutions or not; nevertheless, they can make a good practical solution. As a result of all these factors, we proposed algorithms to solve the educational institution timetabling issue [20].
3 Describing the problem
Timetabling problem can be described by assigning course materials to a collection of rooms and timeslots, taking into account a group of soft constraints and hard constraints. The problem involves two stages to obtain the final solution. The first stage is to attain a feasible solution depending upon satisfying the hard constraints. The second stage is to obtain a better solution by improving the primary solution through a reduction in the soft constraints as much as possible. Thus, the final solution can compete with other relevant solutions in the literature [5].
We introduced a set of problem cases, which are used in this paper to test our algorithm. First, the hard constraints are listed in the following:
At any time, assigning only one course to the student.
The room should achieve the course feature requirements.
No more students can attend the course greater than the room capacity.
For each room, assigning only one course is to the same timeslot.
Second, the soft constraints are listed as follows:
The last day-timeslot should have a course scheduled for the student.
At least two consecutive courses should assign to the student.
On a day, only one course should the student have.
Lastly, the problem includes the following:
No. of courses = N, e = {e 1,…,e n }.
No. of timeslots = 45.
No. of rooms = R.
No. of room features = F.
No. of students = M.
The final solution (the aim of the problem) is to achieve a feasible timetable (the hard constraints) with minimizing the soft-constraints infringement.
This study is based on an instance of PE-CTT difficulties that was presented. Large, medium, and small datasets are divided into three categories based on their size. Eleven case studies are also taken into account: 5 mediums, 1 large, and 5 small (see Section 5).
4 The algorithm
The work is partitioned into constructing and improving algorithms. The constructing algorithm is performed using the least saturation degree algorithm to get an early solution. Next, in the improving algorithm, the tabu search algorithm is employed to decrease the soft-constraints infringement (improvement).
The following four neighborhood structures are utilized:
Nb1: Randomly choose a particular course and progress to a feasible timeslot, which can produce the smallest cost.
Nb2: Randomly select a room. Also, randomly select two courses for that room. Next, swap timeslots.
Nb3: Randomly select two times. Next, swap timeslots.
Nb4: Randomly select a particular time and swap it with another time, in the range between 0 and 44, which can produce the smallest penalty cost.
4.1 Constructing algorithm
The first stage of the work includes the production of the early solution, which can achieve the hard constraints without any accounting for the soft constraints infringement. A least saturation degree algorithm is employed in this stage. First, the events beside smaller number of available rooms that seems hardly scheduled are selected. The algorithm is terminated if a feasible solution is obtained. Else, the neighborhood moves (N1 and/or N2) are performed to achieve feasibility. N1 is employed for a specific number of repetitions. Next, the algorithm is terminated if a feasible solution is achieved. Else, the algorithm continues using the N2 neighborhood structure for a specific number of repetitions. Note that all case studies are examined before the improvement algorithm is employed since the solutions must be made feasible first (see in Figure 1).
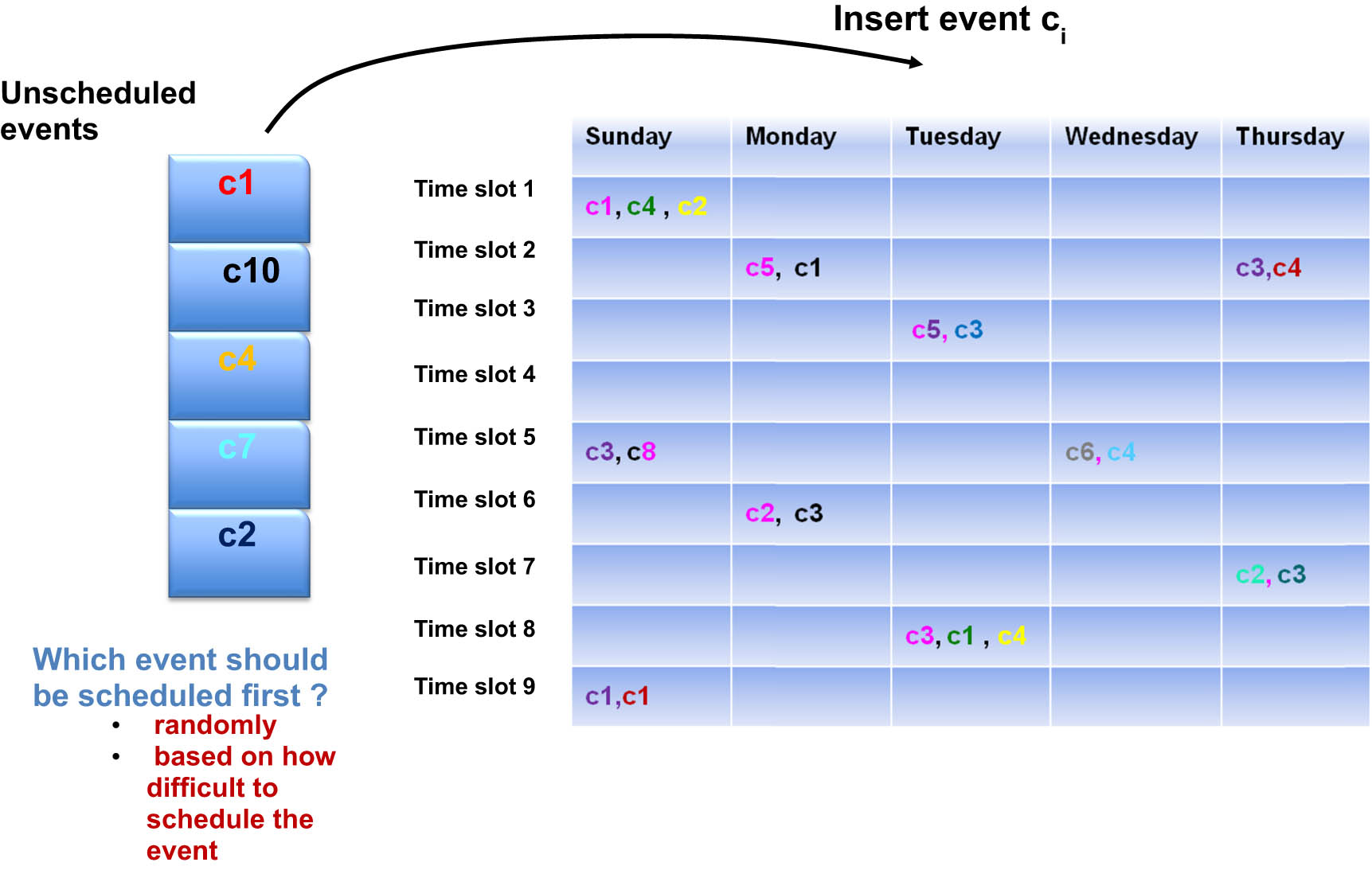
Constructive heuristics (the least saturation degree).
4.2 Improvement algorithm
The second stage includes using a set of neighborhood structures that were previously defined (Nb3, Nb4). During this stage, no hard-constraint infringement is completely allowed. Adaptive Tabu Search algorithm is applied to improve the early solution. Figure 2 shows the pseudocode of the used algorithm.

Pseudocode for the adaptive tabu search algorithm.
Adaptive tabu search depends on the tabu list and the penalty cost, by checking the changing of this penalty cost, if this changing is still invariant for a period of iterations (1,000 iterations), the tabu list is reducing automatically (−2); otherwise, the tabu list remains constant. This procedure will continue until the tabu list equals 2, Figure 3.
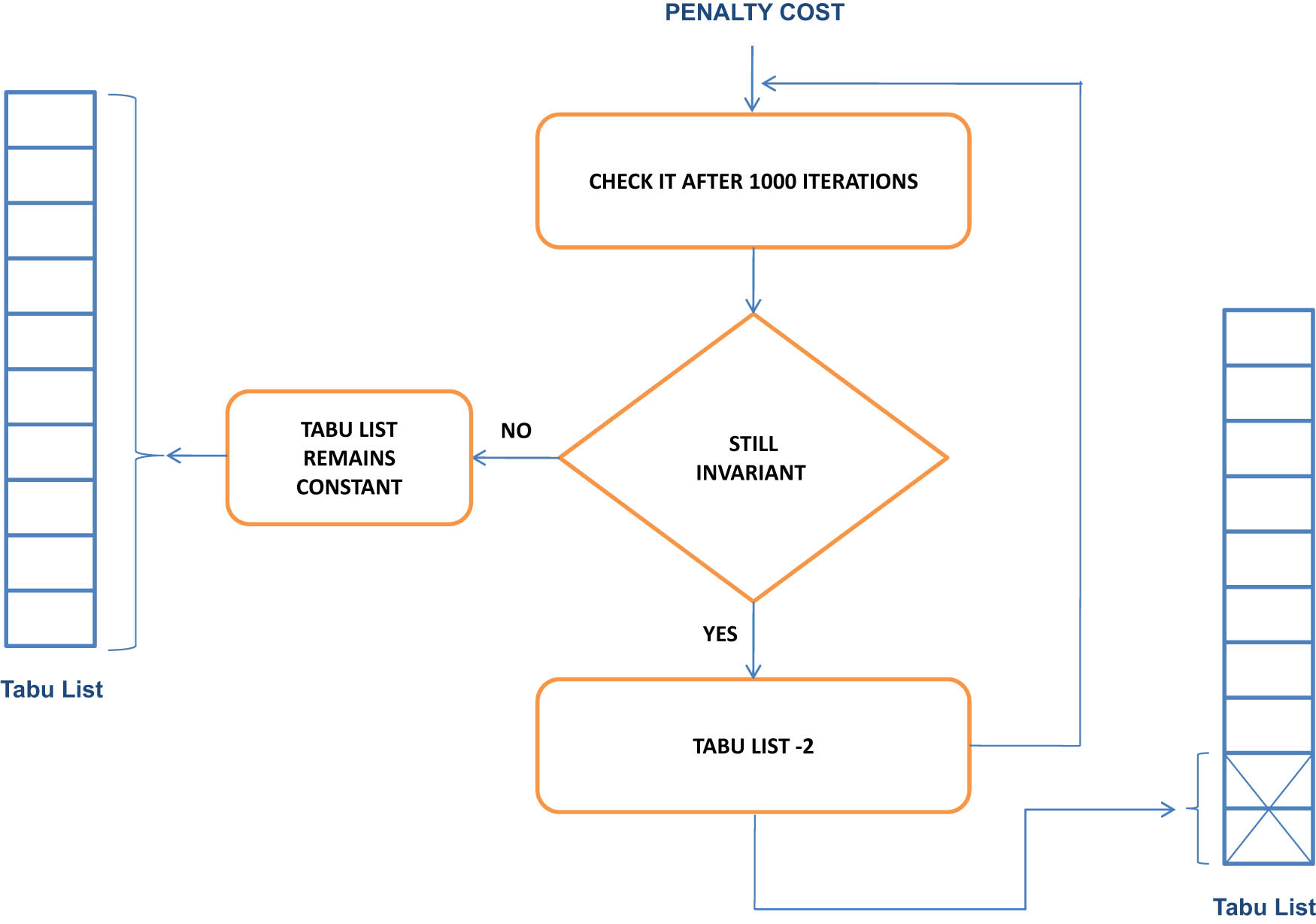
Adaptive tabu list.
5 Experimental results
Our algorithm is programmed in VB.NET using a PC of Win. 7, 1.7 GHz CPU, and 2G RAM.
Datasets are used for evaluating our algorithm efficiency. This collection of data was composed of different real-world course timetabling issues at different universities. We measured the quality of the timetable in the same way that did, by assigning a “1” to each violation of the soft or hard limits for each student involved. The hard constraint violations hvc (total penalty of hvc) of S* for all pupils, as well as the soft constraint violations svc (total penalty of svc) of S* for all students, make up the nature of the candidate solution S*, f(S*) (S equal total number of students), The datasets include 1 large, 5 mediums, 5 small instances that are available at http://iridia.ulb.ac.be/∼msampels/tt.data/.
The experiments for the course timetabling problem discussed in this paper were tested on the benchmark course timetabling problems that need to schedule (100–400) courses into a timetable with (45) timeslots corresponding to (5) days of (9) hours each, while the room features satisfying and room capacity constraints also satisfying. Table 1 lists the parameter values that define the types.
The parameter values for the different types of course scheduling problems
| Type | Small | Medium | Large |
|---|---|---|---|
| No. of courses | 100 | 400 | 400 |
| No. of rooms | 5 | 10 | 10 |
| No. of features | 5 | 5 | 10 |
| No. of students | 80 | 200 | 400 |
On the eleven timetabling instances, we compare our technique to other algorithms in two parts: first, comparing with other literatures that used tabu search even if it hybrid with another algorithm (Table 2), and second, comparing with other works that used another algorithm (Table 3).
| Data set | Our | Alg1 | Alg2 | Alg3 | Alg4 | Alg5 | Alg6 | Alg7 | Alg8 |
|---|---|---|---|---|---|---|---|---|---|
| S1 | — | — | — | — | — | — | — | — | — |
| S2 | — | — | — | — | — | — | — | — | — |
| S3 | — | — | — | — | — | — | — | — | — |
| S4 | — | — | — | — | — | — | — | — | — |
| S5 | — | — | — | — | — | — | — | — | — |
| M1 | 97 | 175 | 78 | 55 | 146 | 242 | 317 | 372 | 150 |
| M2 | 91 | 197 | 92 | 70 | 173 | 161 | 313 | 419 | 179 |
| M3 | 65 | 216 | 135 | 102 | 267 | 265 | 357 | 359 | 183 |
| M4 | 95 | 149 | 75 | 32 | 169 | 181 | 247 | 348 | 140 |
| M5 | 50 | 190 | 68 | 61 | 303 | 151 | 292 | 171 | 152 |
| L | 347 | 912 | 556 | 653 | 1166 | — | — | 1068 | 720 |
Compare our results with the results of other tabu search
| Data set | Our | Alg1 | Alg2 | Alg3 | Alg4 | Alg5 | Alg6 | Alg7 |
|---|---|---|---|---|---|---|---|---|
| S1 | — | — | — | — | — | — | — | — |
| S2 | — | — | — | — | — | — | — | — |
| S3 | — | — | — | — | — | — | — | — |
| S4 | — | — | — | — | — | — | — | — |
| S5 | — | — | — | — | — | — | — | — |
| M1 | 97 | 254 | 174 | 227 | 139 | 175 | 143 | 124 |
| M2 | 91 | 258 | 184 | 180 | 92 | 197 | 130 | 117 |
| M3 | 65 | 251 | 188 | 235 | 122 | 216 | 183 | 190 |
| M4 | 95 | 321 | 180 | 142 | 98 | 149 | 133 | 132 |
| M5 | 50 | 276 | 132 | 200 | 116 | 190 | 169 | 73 |
| L | 347 | 1072 | 994 | — | 615 | 912 | 825 | 424 |
Comparing our results with other approaches in the literature
| Data set | Alg8 | Alg9 | Alg10 | Alg11 | Alg12 | Alg13 | Alg14 |
|---|---|---|---|---|---|---|---|
| S1 | — | — | — | — | — | — | — |
| S2 | — | — | — | — | — | — | — |
| S3 | — | — | — | — | — | — | — |
| S4 | — | — | — | — | — | — | — |
| S5 | — | — | — | — | — | — | — |
| M1 | 180 | 140 | 117 | 9 | 338 | 236 | 243 |
| M2 | 176 | 130 | 121 | 15 | 326 | 158 | 325 |
| M3 | 219 | 189 | 158 | 36 | 384 | 261 | 249 |
| M4 | 150 | 112 | 124 | 12 | 299 | 176 | 285 |
| M5 | 196 | 141 | 134 | 3 | 307 | 147 | 132 |
| L | — | 876 | 645 | 208 | 100% Inf | 296 | 1138 |
Alg1: Abdullah et al. (2012) combine an electromagnetic-like mechanism (EM) and the great deluge algorithm (GD).
Alg2: Shaker (2010) Great Deluge and Tabu Search.
Alg3: Hamza & Salwani (2009) Incorporating Tabu Search into Memetic Approach.
Alg4: Burke et al. (2003a) a hyper-heuristic used tabu search.
Alg5: Abdullah, Burke and McCollum composite neighborhood structure with a randomized iterative improvement algorithm.
Alg6: Abdullah et al. (2007b) Variable neighborhood search with tabu.
Alg7: Burke et al. (2007).
Alg8: Ayob and Jaradat (2009) hybrids Ant Colony Systems with the tabu search (ACS-TS).
Alg1: Salwani and Hamza (2008) Genetic Algorithms and Local Search.
Alg2: AI-Betar et al. (2012) A MultiSwap Algorithm.
Alg3: Jat and Yang (2008) a memetic with genetic algorithm.
Alg4: Yang and Jat (2011) Genetic Algorithms With Guided and Local Search Strategies.
Alg5: Abdullah et al. (2010a) Hybridization algorithm. Electromagnetic-like mechanism with a great deluge.
Alg6: Abuhamdah and Ayob (2010) Round Robin (RR) Algorithm.
Alg7: Al-Betar et al. (2010) harmony search algorithm.
Alg8: Karami and Hasanzadeh (2012) hybrid genetic algorithm (HGA).
Alg9: Obit and Silva (2010) the non-linear great deluge Algorithm.
Alg10: Ayob and Jaradat (2009) hybrids Ant Colony Systems with the Simulated Annealing (ACS-SA).
Alg11: Sara et al. (2012) Simulated Annealing.
Alg12: Abdullah et al. Variable Neighborhood Search.
Alg13: Abdullah Hamdan (2008): A Hybrid Approach.
Alg14: Asmuni et al. Fuzzy Multiple Heuristic.
6 Conclusion
The aim of this paper was to develop a tabu search algorithm to contain an adaptive tabu list to be compatible with the state of solution for the course timetabling problem. This has been accomplished, demonstrating that tabu search is a viable solution to the course scheduling problem. In most cases, tabu search outperforms the traditional method. In addition, the usage of aspiration and stopping criteria are critical to the algorithm’s effectiveness. Tabu search has been proved to be effective in solving scheduling issues, experimental results also showed that the most accurate timetables can be produced when hard and soft constraints are distinguished. Tabu search heuristics are also known to be sensitive to parameter selection. As a result, fine-tuning the parameters may yield even better outcomes. Future work includes further analysis of individual components of the contribution to develop a tabu search algorithm. Hence, future researchers can believe in limitations such as pre-requisite relations and the variation between the Compulsory and optional modules and solve this issue by promoting innovative algorithms, rather than the deep educational algorithm. In the same method, researchers are capable of compiling with other constraints to the model, or they can set heuristic algorithms. In future studies, the intended constraints are advised.
-
Conflict of interest: Authors state no conflict of interest.
References
[1] Osorio A, Esquivel M. A solution to the university course timetabling problem using a hybrid method based on genetic algorithms. Dyna. 2020;87(215):47–56.10.15446/dyna.v87n215.85933Suche in Google Scholar
[2] Amin R, Abshirini Z, Boshkani Zade M. Solving University course timetabling problem using parallel genetic algorithm. Int J Sci Res Comput Sci Eng. 2019;7.5:5–13.10.26438/ijsrcse/v7i5.513Suche in Google Scholar
[3] Khiarak NJ, Zamani-Harghalani Y, Derakhshi M-RF. Combined multi-agent method to control inter-department common events collision for university courses timetabling. J Intell Syst. 2020;29(1):110–26. 10.1515/jisys-2017-0249.Suche in Google Scholar
[4] Abu Doush I, Al-Betar MA, Awadallah MA, Hammouri AI, Al-Khatib RM, ElMustafa S, et al. Harmony search algorithm for patient admission scheduling problem. J Intell Syst. 2020;29(1):540–53. 10.1515/jisys-2018-0094.Suche in Google Scholar
[5] Wei M, Yang Y, Su J, Li Q, Liang Z. Task reallocating for responding to design change in complex product design. J Intell Syst. 2019;28(1):57–76. 10.1515/jisys-2016-0262.Suche in Google Scholar
[6] Abdullah S, Turabieh H, McCollum B, McMullan P. A hybrid metaheuristic approach to the university course timetabling problem. J Heuristics. 2012;18:1–23. 10.1007/s10732-010-9154-y.Suche in Google Scholar
[7] Bolaji AL, Okwonu FZ, Shola PB, Balogun BS, Adubisi OD. A modified binary pigeon-inspired algorithm for solving the multi-dimensional knapsack problem. J Intell Syst. 2021;30(1):90–103. 10.1515/jisys-2018-0450.Suche in Google Scholar
[8] Turabieh H, Abdullah S. Incorporating tabu search into memetic approach for enrolment-based course timetabling problems. 2009 2nd Conference on Data Mining and Optimization. Selangor, Malaysia: IEEE; 27–28 October 2009. p. 115–9.10.1109/DMO.2009.5341901Suche in Google Scholar
[9] Ayob M, Jaradat GH. Hybrid ant colony systems for course timetabling problems. 2nd Conference on Data Mining and Optimization. Selangor, Malaysia: IEEE; 27–28 October 2009. p. 120–6.10.1109/DMO.2009.5341898Suche in Google Scholar
[10] Sadaf Jat N, Yang SH. A memetic algorithm for the university course timetabling problem. 20th IEEE International Conference on Tools with Artificial Intelligence; 2008. p. 427–33.10.1109/ICTAI.2008.126Suche in Google Scholar
[11] Yang SH, Naseem Jat S. Genetic algorithms with guided and local search strategies for university course timetabling. IEEE Trans Systems, Man, Cybernetics-Part C: Appl Rev. January 2011;41(1):93–106.10.1109/TSMCC.2010.2049200Suche in Google Scholar
[12] Jyoti M, Monga H, Baghla S. Reduction of inter-symbol interference using artifical neural network system in multicarrier OFDM system. Int J Wirel Microw Technol. 2018;8:10–8.10.5815/ijwmt.2018.05.02Suche in Google Scholar
[13] Abuhamdah A, Ayob M. Adaptive randomized descent algorithm using round robin for solving course timetabling problems. 10th International Conference on Intelligent Systems Design and Applications, IEEE; 2010. p. 1201–6.10.1109/ISDA.2010.5687021Suche in Google Scholar
[14] Azmi Al-Betar M, Tajudin Khader A, Yi Liao I. A harmony search with multi-pitch adjusting rate for the university course timetabling. Berlin Heidelberg: Springer-Verlag; 2010. p. 147–61.10.1007/978-3-642-04317-8_13Suche in Google Scholar
[15] Hossein Karami A, Hasanzadeh M. University course timetabling using a new hybrid genetic algorithm. 2nd International Conference on Computer and Knowledge Engineering (ICCKE); October 18–19 2012. p. 144–9.10.1109/ICCKE.2012.6395368Suche in Google Scholar
[16] Henry Obit J, Landa-Silva D. Computational study of non-linear great deluge for university course timetabling. Berlin Heidelberg: Springer-Verlag; 2010. p. 309–28.10.1007/978-3-642-13428-9_14Suche in Google Scholar
[17] Ghaith Jaradat M, Ayob M. Big bang-big crunch optimization algorithm to solve the course timetabling problem. 10th International Conference on Intelligent Systems Design and Applications. Selangor, Malaysia: Data Mining and Optimization Research Group The National University of Malaysia B.B.Bangi; p. 1448–52.10.1109/ISDA.2010.5687114Suche in Google Scholar
[18] Zheng N, Chen T, Lin F, Xu H. A hybrid heuristic algorithm for the intelligent transportation scheduling problem of the BRT system. J Intell Syst. 2015;24(4):437–48. 10.1515/jisys-pp.2014-0134.Suche in Google Scholar
[19] Ceschia S, Di Gaspero L, Schaerf A. Design, engineering, and experimental analysis of a simulated annealing approach to the post-enrolment course timetabling problem. Comput Oper Res. 2012;39:1615–24.10.1016/j.cor.2011.09.014Suche in Google Scholar
[20] Alirezaei E, Vahedi Z, Ghaznavi-Ghoushchi M. Parallel hybrid meta heuristic algorithm for university course timetabling problem. 20th Iranian Conference on Electrical Engineering, (ICEE2012). Tehran, Iran: IEEE; May 15–17 2012. p. 673–8.10.1109/IranianCEE.2012.6292439Suche in Google Scholar
© 2022 Fouad H. Awad et al., published by De Gruyter
This work is licensed under the Creative Commons Attribution 4.0 International License.
Artikel in diesem Heft
- Research Articles
- Construction of 3D model of knee joint motion based on MRI image registration
- Evaluation of several initialization methods on arithmetic optimization algorithm performance
- Application of visual elements in product paper packaging design: An example of the “squirrel” pattern
- Deep learning approach to text analysis for human emotion detection from big data
- Cognitive prediction of obstacle's movement for reinforcement learning pedestrian interacting model
- The application of neural network algorithm and embedded system in computer distance teach system
- Machine translation of English speech: Comparison of multiple algorithms
- Automatic control of computer application data processing system based on artificial intelligence
- A secure framework for IoT-based smart climate agriculture system: Toward blockchain and edge computing
- Application of mining algorithm in personalized Internet marketing strategy in massive data environment
- On the correction of errors in English grammar by deep learning
- Research on intelligent interactive music information based on visualization technology
- Extractive summarization of Malayalam documents using latent Dirichlet allocation: An experience
- Conception and realization of an IoT-enabled deep CNN decision support system for automated arrhythmia classification
- Masking and noise reduction processing of music signals in reverberant music
- Cat swarm optimization algorithm based on the information interaction of subgroup and the top-N learning strategy
- State feedback based on grey wolf optimizer controller for two-wheeled self-balancing robot
- Research on an English translation method based on an improved transformer model
- Short-term prediction of parking availability in an open parking lot
- PUC: parallel mining of high-utility itemsets with load balancing on spark
- Image retrieval based on weighted nearest neighbor tag prediction
- A comparative study of different neural networks in predicting gross domestic product
- A study of an intelligent algorithm combining semantic environments for the translation of complex English sentences
- IoT-enabled edge computing model for smart irrigation system
- A study on automatic correction of English grammar errors based on deep learning
- A novel fingerprint recognition method based on a Siamese neural network
- A hidden Markov optimization model for processing and recognition of English speech feature signals
- Crime reporting and police controlling: Mobile and web-based approach for information-sharing in Iraq
- Convex optimization for additive noise reduction in quantitative complex object wave retrieval using compressive off-axis digital holographic imaging
- CRNet: Context feature and refined network for multi-person pose estimation
- Improving the efficiency of intrusion detection in information systems
- Research on reform and breakthrough of news, film, and television media based on artificial intelligence
- An optimized solution to the course scheduling problem in universities under an improved genetic algorithm
- An adaptive RNN algorithm to detect shilling attacks for online products in hybrid recommender system
- Computing the inverse of cardinal direction relations between regions
- Human-centered artificial intelligence-based ice hockey sports classification system with web 4.0
- Construction of an IoT customer operation analysis system based on big data analysis and human-centered artificial intelligence for web 4.0
- An improved Jaya optimization algorithm with ring topology and population size reduction
- Review Articles
- A review on voice pathology: Taxonomy, diagnosis, medical procedures and detection techniques, open challenges, limitations, and recommendations for future directions
- An extensive review of state-of-the-art transfer learning techniques used in medical imaging: Open issues and challenges
- Special Issue: Explainable Artificial Intelligence and Intelligent Systems in Analysis For Complex Problems and Systems
- Tree-based machine learning algorithms in the Internet of Things environment for multivariate flood status prediction
- Evaluating OADM network simulation and an overview based metropolitan application
- Radiography image analysis using cat swarm optimized deep belief networks
- Comparative analysis of blockchain technology to support digital transformation in ports and shipping
- IoT network security using autoencoder deep neural network and channel access algorithm
- Large-scale timetabling problems with adaptive tabu search
- Eurasian oystercatcher optimiser: New meta-heuristic algorithm
- Trip generation modeling for a selected sector in Baghdad city using the artificial neural network
- Trainable watershed-based model for cornea endothelial cell segmentation
- Hessenberg factorization and firework algorithms for optimized data hiding in digital images
- The application of an artificial neural network for 2D coordinate transformation
- A novel method to find the best path in SDN using firefly algorithm
- Systematic review for lung cancer detection and lung nodule classification: Taxonomy, challenges, and recommendation future works
- Special Issue on International Conference on Computing Communication & Informatics
- Edge detail enhancement algorithm for high-dynamic range images
- Suitability evaluation method of urban and rural spatial planning based on artificial intelligence
- Writing assistant scoring system for English second language learners based on machine learning
- Dynamic evaluation of college English writing ability based on AI technology
- Image denoising algorithm of social network based on multifeature fusion
- Automatic recognition method of installation errors of metallurgical machinery parts based on neural network
- An FCM clustering algorithm based on the identification of accounting statement whitewashing behavior in universities
- Emotional information transmission of color in image oil painting
- College music teaching and ideological and political education integration mode based on deep learning
- Behavior feature extraction method of college students’ social network in sports field based on clustering algorithm
- Evaluation model of multimedia-aided teaching effect of physical education course based on random forest algorithm
- Venture financing risk assessment and risk control algorithm for small and medium-sized enterprises in the era of big data
- Interactive 3D reconstruction method of fuzzy static images in social media
- The impact of public health emergency governance based on artificial intelligence
- Optimal loading method of multi type railway flatcars based on improved genetic algorithm
- Special Issue: Evolution of Smart Cities and Societies using Emerging Technologies
- Data mining applications in university information management system development
- Implementation of network information security monitoring system based on adaptive deep detection
- Face recognition algorithm based on stack denoising and self-encoding LBP
- Research on data mining method of network security situation awareness based on cloud computing
- Topology optimization of computer communication network based on improved genetic algorithm
- Implementation of the Spark technique in a matrix distributed computing algorithm
- Construction of a financial default risk prediction model based on the LightGBM algorithm
- Application of embedded Linux in the design of Internet of Things gateway
- Research on computer static software defect detection system based on big data technology
- Study on data mining method of network security situation perception based on cloud computing
- Modeling and PID control of quadrotor UAV based on machine learning
- Simulation design of automobile automatic clutch based on mechatronics
- Research on the application of search algorithm in computer communication network
- Special Issue: Artificial Intelligence based Techniques and Applications for Intelligent IoT Systems
- Personalized recommendation system based on social tags in the era of Internet of Things
- Supervision method of indoor construction engineering quality acceptance based on cloud computing
- Intelligent terminal security technology of power grid sensing layer based upon information entropy data mining
- Deep learning technology of Internet of Things Blockchain in distribution network faults
- Optimization of shared bike paths considering faulty vehicle recovery during dispatch
- The application of graphic language in animation visual guidance system under intelligent environment
- Iot-based power detection equipment management and control system
- Estimation and application of matrix eigenvalues based on deep neural network
- Brand image innovation design based on the era of 5G internet of things
- Special Issue: Cognitive Cyber-Physical System with Artificial Intelligence for Healthcare 4.0.
- Auxiliary diagnosis study of integrated electronic medical record text and CT images
- A hybrid particle swarm optimization with multi-objective clustering for dermatologic diseases diagnosis
- An efficient recurrent neural network with ensemble classifier-based weighted model for disease prediction
- Design of metaheuristic rough set-based feature selection and rule-based medical data classification model on MapReduce framework
Artikel in diesem Heft
- Research Articles
- Construction of 3D model of knee joint motion based on MRI image registration
- Evaluation of several initialization methods on arithmetic optimization algorithm performance
- Application of visual elements in product paper packaging design: An example of the “squirrel” pattern
- Deep learning approach to text analysis for human emotion detection from big data
- Cognitive prediction of obstacle's movement for reinforcement learning pedestrian interacting model
- The application of neural network algorithm and embedded system in computer distance teach system
- Machine translation of English speech: Comparison of multiple algorithms
- Automatic control of computer application data processing system based on artificial intelligence
- A secure framework for IoT-based smart climate agriculture system: Toward blockchain and edge computing
- Application of mining algorithm in personalized Internet marketing strategy in massive data environment
- On the correction of errors in English grammar by deep learning
- Research on intelligent interactive music information based on visualization technology
- Extractive summarization of Malayalam documents using latent Dirichlet allocation: An experience
- Conception and realization of an IoT-enabled deep CNN decision support system for automated arrhythmia classification
- Masking and noise reduction processing of music signals in reverberant music
- Cat swarm optimization algorithm based on the information interaction of subgroup and the top-N learning strategy
- State feedback based on grey wolf optimizer controller for two-wheeled self-balancing robot
- Research on an English translation method based on an improved transformer model
- Short-term prediction of parking availability in an open parking lot
- PUC: parallel mining of high-utility itemsets with load balancing on spark
- Image retrieval based on weighted nearest neighbor tag prediction
- A comparative study of different neural networks in predicting gross domestic product
- A study of an intelligent algorithm combining semantic environments for the translation of complex English sentences
- IoT-enabled edge computing model for smart irrigation system
- A study on automatic correction of English grammar errors based on deep learning
- A novel fingerprint recognition method based on a Siamese neural network
- A hidden Markov optimization model for processing and recognition of English speech feature signals
- Crime reporting and police controlling: Mobile and web-based approach for information-sharing in Iraq
- Convex optimization for additive noise reduction in quantitative complex object wave retrieval using compressive off-axis digital holographic imaging
- CRNet: Context feature and refined network for multi-person pose estimation
- Improving the efficiency of intrusion detection in information systems
- Research on reform and breakthrough of news, film, and television media based on artificial intelligence
- An optimized solution to the course scheduling problem in universities under an improved genetic algorithm
- An adaptive RNN algorithm to detect shilling attacks for online products in hybrid recommender system
- Computing the inverse of cardinal direction relations between regions
- Human-centered artificial intelligence-based ice hockey sports classification system with web 4.0
- Construction of an IoT customer operation analysis system based on big data analysis and human-centered artificial intelligence for web 4.0
- An improved Jaya optimization algorithm with ring topology and population size reduction
- Review Articles
- A review on voice pathology: Taxonomy, diagnosis, medical procedures and detection techniques, open challenges, limitations, and recommendations for future directions
- An extensive review of state-of-the-art transfer learning techniques used in medical imaging: Open issues and challenges
- Special Issue: Explainable Artificial Intelligence and Intelligent Systems in Analysis For Complex Problems and Systems
- Tree-based machine learning algorithms in the Internet of Things environment for multivariate flood status prediction
- Evaluating OADM network simulation and an overview based metropolitan application
- Radiography image analysis using cat swarm optimized deep belief networks
- Comparative analysis of blockchain technology to support digital transformation in ports and shipping
- IoT network security using autoencoder deep neural network and channel access algorithm
- Large-scale timetabling problems with adaptive tabu search
- Eurasian oystercatcher optimiser: New meta-heuristic algorithm
- Trip generation modeling for a selected sector in Baghdad city using the artificial neural network
- Trainable watershed-based model for cornea endothelial cell segmentation
- Hessenberg factorization and firework algorithms for optimized data hiding in digital images
- The application of an artificial neural network for 2D coordinate transformation
- A novel method to find the best path in SDN using firefly algorithm
- Systematic review for lung cancer detection and lung nodule classification: Taxonomy, challenges, and recommendation future works
- Special Issue on International Conference on Computing Communication & Informatics
- Edge detail enhancement algorithm for high-dynamic range images
- Suitability evaluation method of urban and rural spatial planning based on artificial intelligence
- Writing assistant scoring system for English second language learners based on machine learning
- Dynamic evaluation of college English writing ability based on AI technology
- Image denoising algorithm of social network based on multifeature fusion
- Automatic recognition method of installation errors of metallurgical machinery parts based on neural network
- An FCM clustering algorithm based on the identification of accounting statement whitewashing behavior in universities
- Emotional information transmission of color in image oil painting
- College music teaching and ideological and political education integration mode based on deep learning
- Behavior feature extraction method of college students’ social network in sports field based on clustering algorithm
- Evaluation model of multimedia-aided teaching effect of physical education course based on random forest algorithm
- Venture financing risk assessment and risk control algorithm for small and medium-sized enterprises in the era of big data
- Interactive 3D reconstruction method of fuzzy static images in social media
- The impact of public health emergency governance based on artificial intelligence
- Optimal loading method of multi type railway flatcars based on improved genetic algorithm
- Special Issue: Evolution of Smart Cities and Societies using Emerging Technologies
- Data mining applications in university information management system development
- Implementation of network information security monitoring system based on adaptive deep detection
- Face recognition algorithm based on stack denoising and self-encoding LBP
- Research on data mining method of network security situation awareness based on cloud computing
- Topology optimization of computer communication network based on improved genetic algorithm
- Implementation of the Spark technique in a matrix distributed computing algorithm
- Construction of a financial default risk prediction model based on the LightGBM algorithm
- Application of embedded Linux in the design of Internet of Things gateway
- Research on computer static software defect detection system based on big data technology
- Study on data mining method of network security situation perception based on cloud computing
- Modeling and PID control of quadrotor UAV based on machine learning
- Simulation design of automobile automatic clutch based on mechatronics
- Research on the application of search algorithm in computer communication network
- Special Issue: Artificial Intelligence based Techniques and Applications for Intelligent IoT Systems
- Personalized recommendation system based on social tags in the era of Internet of Things
- Supervision method of indoor construction engineering quality acceptance based on cloud computing
- Intelligent terminal security technology of power grid sensing layer based upon information entropy data mining
- Deep learning technology of Internet of Things Blockchain in distribution network faults
- Optimization of shared bike paths considering faulty vehicle recovery during dispatch
- The application of graphic language in animation visual guidance system under intelligent environment
- Iot-based power detection equipment management and control system
- Estimation and application of matrix eigenvalues based on deep neural network
- Brand image innovation design based on the era of 5G internet of things
- Special Issue: Cognitive Cyber-Physical System with Artificial Intelligence for Healthcare 4.0.
- Auxiliary diagnosis study of integrated electronic medical record text and CT images
- A hybrid particle swarm optimization with multi-objective clustering for dermatologic diseases diagnosis
- An efficient recurrent neural network with ensemble classifier-based weighted model for disease prediction
- Design of metaheuristic rough set-based feature selection and rule-based medical data classification model on MapReduce framework

