Abstract
The topology optimization of computer communication network is studied based on improved genetic algorithm (GA), a network optimization design model based on the establishment of network reliability maximization under given cost constraints, and the corresponding improved GA is proposed. In this method, the corresponding computer communication network cost model and computer communication network reliability model are established through a specific project, and the genetic intelligence algorithm is used to solve the cost model and computer communication network reliability model, respectively. It has been proved that GA can solve the complex problems of computer working environment better, which is 80% higher than the general algorithm, and can select the optimal scheme pertinently.
1 Introduction
With the further strengthening of social informatization, people will rely more and more on all kinds of networks, requiring the network to provide convenient, rapid, accurate, safe, and high-quality services. At the same time, the scale of the network continues to expand, the connection area and the length of the network are also rapidly expanding. Up to now, human beings have developed many new large-scale complex equipment and systems, such as computer communication network system, communication system, automated production line system, banking service system, nuclear power plant, large passenger aircraft, and military system [1]. The common characteristics of these systems are complex structure and powerful function. The system needs the support of complex hardware and software to complete the scheduled function, and sometimes also needs the participation of people. Once the system breaks down, it will cause losses of different degrees to society, economy, and environment. Therefore, system reliability, one of the most important indicators of system efficiency, has become a research direction attracting much attention [2]. Therefore, the study of computer communication network reliability has very important theoretical significance and practical value. To ensure that the system can work safely and reliably, theoretical research needs to mainly focus on the optimization design of network reliability, and other indicators of the optimization system, such as link cost, maintenance cost, delay, blocking rate, response time, etc., should be taken into account on the basis of improving network reliability [3]. In practical engineering applications, designers mainly consider two aspects when constructing network systems: network performance and investment cost. Because of the high cost of network system, cost is often a very important constraint factor in network topology design. For most networks today, a small improvement in their topology design can save a certain amount of money. Through re-optimization, considerable cost savings can be achieved by applying new ideas and technologies without reducing system performance [4].
2 Literature review
Studies have shown that Liu and Wang, taking computer communication network as an example, conducted a detailed study and discussion on the problem of topology optimization design of large-scale network based on full terminal reliability [5]. Sengottuvelan and Prasath conducted exploratory research on the reliability optimization problem of all-terminal network, and applied heuristic methods and GAs to solve this kind of optimization problem for the first time, achieving more effective and satisfactory results than traditional methods [6]. Miao et al. verified that calculating 2-terminal reliability, K-terminal reliability, and all-terminal reliability is NP-hard problem. In general, foreign research works in this field have been carried out in depth, and many valuable research results have emerged [7]. Chang and Yang studied the Si1000-based wireless M-Bus communication system design, as shown in Figure 1 [8]. Abdessamad et al. believed that the optimization design model of route selection and link capacity distribution in computer communication network is a complex nonlinear 0–1 planning if solved by traditional mathematical method, cannot quickly and effectively sum engineering satisfactory solution, based on the basic idea of transmission algorithm, and designed an optimization algorithm which is completely different from the traditional method [9]. Afsharinejad et al. studied its value through the application of contingency algorithms in computers [10]. Osamy et al. proposed a QoS routing algorithm based on improved casting based on delay bandwidth constraints. In this algorithm, a combination of weighted depth priority search and roulette is used to ensure the diversity of the initial population, while improving the basic variation process and proposing methods to guide the variation [11]. Xu et al. have proposed a location information hiding method based on effectively protecting user privacy with improved GAs [12]. Liu et al. extracted the features of location information together with the association rules: the vector quantitative fusion method is used for the data hiding design after information coding [13]. Aizaz and Sinha performed the encryption key construction of location information based on improved GAs, encrypted and quantified location information, and realized the flow chart of location information hiding optimization as shown in Figure 2 [14].

Design of a wireless M-bus communication system based on Si1000.
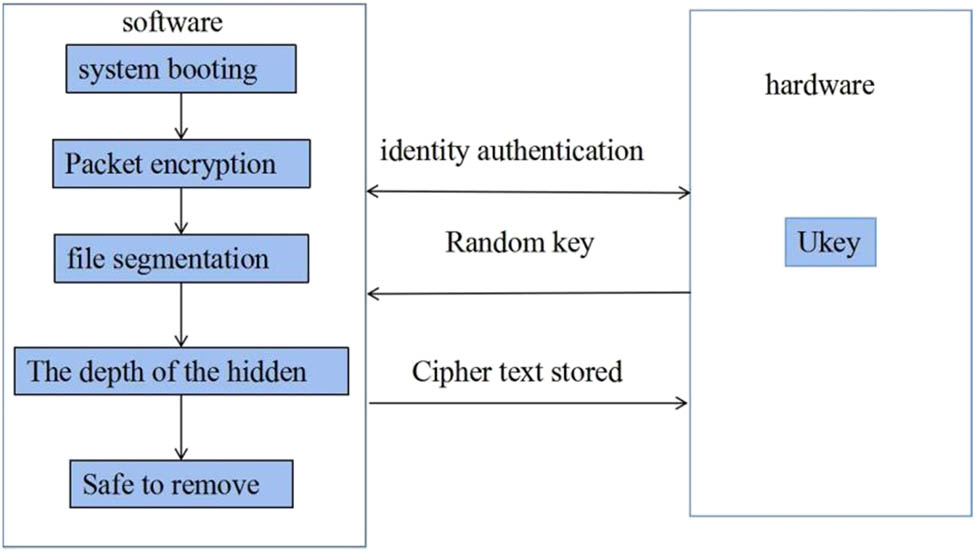
System overall framework diagram.
Based on the synthesis of the existing research, this article proposes the reliability analysis and optimization research based on improved GA, aiming to discuss the process of reliability model establishment and reliability analysis, to provide necessary security service strategy for engineering application, and study the multi-objective optimization of network reliability, so as to establish a construction method based on reliability purpose, and give a specific implementation case through intelligent optimization algorithm.
3 Case analysis
This section gives two examples of topology optimization design of computer communication networks. Example 1 maximizes the reliability of a given ARPA network with 5 nodes and 7 links, constrained by given cost. The mathematical description is as follows:
Let X = (x 1, x 2, …x 7) make maximize.
The computer network diagram of 4 nodes and their gene expressions are shown in Table 1.
Gene expression table of computer network nodes
| N1 | 0101 |
| N2 | 1010 |
| N3 | 0101 |
| N4 | 1010 |
Choice of fitness function: Effectively prevent the occurrence of deception in the GA, the cost values of individuals in the population are arranged according to their numerical size. The ordering code of the individuals with the smallest cost value is set as 1, and the ordering code of the individuals with the largest cost value is set as pop-size, so the fitness function is designed as follows:
According to the algorithm flow of GA and the adjustment algorithm flow of GA, the simulation solution is carried out step by step. When the number of genetic operation iterations is 100, the simulation process terminates. The simulation results show that the minimum cost of computer network link is 45, and the maximum reliability of computer network is 0.875. The simulation curves of computer network link cost and computer network reliability are shown in Figure 3, respectively.

Computer network link cost simulation curve.
The reliability of nodes is considered. The reliability of service centers is 0.95, that of workstations is 0.9, that of links between service centers is 0.9, that of links between service centers and workstations is 0.85, and RMIN = 0.9. The GA proposed in this article is run in the Matlab environment, the GA parameters are: population size POPXZE = 100, maximum iteration times MAXGEN = 500, crossover rate P c = 0.3, mutation rate P m = 0.7, the number of iterations of the program is 32, each run randomly generates different populations. And then the best results of those 32 times are taken and compared. Its topological structure is shown in Figure 4. In the figure, the thick line represents the link of the backbone network, and the thin line represents the link between the center and the client, as follows.

Network structure in W e = W r = W d = 1/3 mode.
Many experiments show that under the same condition (there is no expected optimal solution in the initial population), the optimal solution appears in about 50 generations by using the traditional GA, and the algebras are relatively scattered. However, using the GA presented, the optimal solution appears in about 15 generations, and occurs most frequently in less than 50 generations. Moreover, the general algorithm is targeted and the proposed algorithm is universal.
4 Discussion
4.1 Basic principles of GA
The basic principle is that GA is a group iterative process. That is to say, the application of GA is randomly selected in the initial population, in accordance with the laws of the natural selection of the fittest, through generations of change and continuous competition, line selection, breeding, hybridization, and mutation, thus constantly getting better next generation group, and so the cycle of evolution finally get a good group most suited to the current environment. In using GA to obtain the optimal solution, not only the basic structure is relatively simple, but also does not have any restrictions and requirements on the nature of the objective function. In the search, genetic characteristics will be used to constantly find the search direction of the optimal solution, and the optimal solution can be obtained quickly and accurately from the whole function value [15,16].
Component of GA: GA includes five parts: Gene expression, initial population determination, gene fitness calculation, genetic operation (crossover and variation), and evolutionary operation (selection).
GA process: GA provides a general framework for solving complex system optimization problems, which does not depend on the domain and type of the problem. For a practical application problem requiring optimization calculation, the following steps can be generally used to construct a GA to solve the problem.
Determine the decision variables and various constraints, that is, determine the individual phenotype X and the solution space of the problem;
Establish an optimization model, that is, to determine the type of objective function (whether to seek the maximum value of the objective function or the minimum value of the objective function) and its mathematical description or quantitative method;
Determine the chromosome coding method representing the feasible solution, that is, determine the individual genotype X and the search space of GA;
Determine the decoding method, and determine the corresponding relationship or conversion method from individual genotype X to individual phenotype x;
Determine the quantitative evaluation method of individual fitness, that is, determine the target function value f(x) to individual fitness F(X).
Design genetic operators, that is, determine the specific operation methods of selection operation, crossover operation, mutation operation, and other genetic operators;
Determine the relevant operating parameters of GA, that is, determine the initial population pop-size and evolution of GA.
The coding method of feasible solution and the design of genetic operator are two main problems which need to be considered in the construction of GA, and also two key steps in the design of specific GA. Different optimization problems need to use different coding methods and different genetic operators, which are closely related to the specific problem to be solved, so the understanding of the problem to be solved is the key to the success of GA application.
4.1.1 Coding
Topology design of computer communication network is concerned with the representation of the connection between two nodes, so this kind of problem and the encoding and decoding between chromosomes is very convenient that is to use the binary strategy. The specific approach is: first, each link to be selected is naturally sorted according to the node numbers of its two ends, and then each link to be selected is regarded as a gene in the chromosome in this order. When the gene value is 1, the corresponding link is selected to join the network. Otherwise, vice versa. Therefore, the length of chromosomes should be equal to the number of links to be selected, and each chromosome represents a topological design scheme.
4.1.2 Chromosomes meet the connectivity process
The primary condition for topological design of computer communication network is connectivity, so when we construct chromosomes, we carry out connectivity check for each chromosome obtained in the process of GA, and the process is as follows:
Return true if the obtained chromosome satisfies
4.1.3 Fitness function
The fitness function should reflect optimization objectives and constraints. Therefore, the fitness function is defined as:
where λ is the penalty factor.
4.1.4 Select operation
The crossover operation of GA requires two individuals to be selected for combined operation. Individuals are selected according to the following probabilities:
4.1.5 Adaptive adjustment of control parameters
To prevent the premature convergence of GA and to speed up the search speed, the strategy of M. Strinvas was adopted, that is to dynamically adjust the crossover probability P according to the evolution of population and the probability of variation P m . The specific determination process is as follows: F max is set as the fitness value of the best individual in a generation population, F w is the average fitness value of this generation population, denoted by δ = F max − F avg, so it can be believed that the smaller δ is, the smaller the difference between individuals in this generation population is, and the population tends to converge. The larger δ is, the greater the difference between individuals in this generation is, and the degree of convergence is small [7–17]. Therefore, in order to prevent premature population convergence, when δ is small, P c and P m should be increased. When δ is large, P c and P m should be reduced. It can be expressed as follows:
The above formula shows that in the process of evolution, P c and P m can be adjusted at any time according to the actual situation to make the GA have stronger search ability. However, the above equation also leads to a high probability of destruction of the optimal individual when evolution has converged to the global optimum. To overcome this phenomenon, it is necessary not only to prevent premature convergence but also to protect the superior individuals. Therefore, P c and P m are correspondingly different for different individuals in the same generation. Individuals with high fitness should be protected to reduce P c and P m . For individuals with low fitness, P c and P m were increased accordingly. The above two formulae can be modified as follows:
where F c is the maximum fitness of the two crossover individuals, F m is the fitness of the mutant individuals, and k 1, k 2, k 3, and k 4 are constants.
4.2 Requirements for optimal design of computer communication network
Reliability: Computer network in the specified conditions (operation mode, maintenance mode, load conditions, temperature, humidity, radiation, etc.) under the specified time (1,000 h, a quarter, etc.) to maintain connectivity and meet the communication requirements of the ability is called computer network reliability. The reliability of computer network is the probability that the network will complete the specified function within the specified time (1,000 h, a quarter, etc.) under the specified conditions (operation mode, maintenance mode, load condition, temperature, humidity, radiation, etc.). Computer network reliability has three types: (1) 2-terminal reliability, that is, in the probability graph, the probability that there is at least one normal link between the specified source point S and the terminal point T. (2) γ terminal reliability, that is, in the probability graph, the probability that there is a link in normal operation between any two pairs of nodes in the set composed of γ nodes is specified. (3) Full terminal reliability, that is, in the probability graph, the probability that there is a link in normal operation between any two nodes is specified [18,19].
4.3 Computer communication network optimization design based on GA
The main steps of computer communication network optimization design using GA are as follows:
Establish a coding scheme: The encoded sequence becomes a chromosome, and the coding element called Gene randomly generates a group of initial chromosomes, which become the initial population;
Fitness operation: Each chromosome in the population is decoded into a set of solutions, through which the fitness of each chromosome can be calculated;
Crossover operation: After pairing chromosomes in the population, part of the chromosomes is exchanged according to crossover probability;
Mutation operation: Change the gene value of its chromosome at the mutation point according to the mutation probability. Steps (2)–(10) are repeated until a good individual meets the stop rule is produced [11,21]. After the combination of satisfaction optimization and GA, in the process of optimization with GA, the value of comprehensive satisfaction function is taken as the adaptive value, and the design of backbone network with the highest comprehensive satisfaction is the optimization result.
4.4 Analysis of optimization results
The proposed GA runs in the MATLAB environment, and the parameters of the GA are: population size Popxze = 100, MAXGEN = 500, crossover rate p c = 0.3, mutation rate p m = 0.7, the program has 32 iterations, each run randomly generates small identical populations, and then compares the best results obtained from these 32 times. If network cost, average delay, and reliability are equally important during optimization, the weights of the three performance indicators are W e = W r = W d = 1/3, respectively, in the calculation of integrated media satisfaction, and the optimization results are shown in Table 2. In the process of initialization and variation, the solutions that meet the reliability constraints are removed, so the reliability can be considered little [22,23]. Then, the network cost and average delay are equally important, so the weights of the three performance indicators are respectively W c = W d = 0.5 and W r = 0 when calculating the comprehensive satisfaction. The optimization results are shown in Table 2. It can be seen that better satisfaction can be obtained under the reliability conditions of these small equal weights. It can be said that after adopting GA, satisfactory solution can be found in the shortest time, and the NP-hard problem with high reliability and low cost can be successfully solved, and the topology optimization problem of computer communication network can be realized and solved quickly [24–26].
Performance indexes and GA optimization results under different weights
| A weight | Network fee | Reliability | Cost satisfaction | Reliability satisfaction | Overall satisfaction |
|---|---|---|---|---|---|
| W e = W r = W d = 1/3 | 601 | 1 | 0.895 | 1 | 0.985 |
| W c = W d = 0.5 | 609 | 0.9353 | 0.975 | 0.963 | 0.956 |
| W r = 0 |
5 Conclusion
The general mathematical model of topology optimization design of computer communication network is established first, and then the GA and corresponding strategy are designed to solve this kind of problem. Example results show that the algorithm presented can effectively solve such problems, and can be used to solve general 0–1 programming problems, so it has a strong promotion value.
Acknowledgment
Science and technology research and Development Plan of Langfang in 2021, Research on collaborative innovation development path of Beijing-Tianjin-Hebei Artificial intelligence industry. Project No.: 2021029060.
-
Conflict of interest: The authors declare that they have no competing interests.
References
[1] Cui X, Yang J, Li J, Wu C. Improved genetic algorithm to optimize the Wi-Fi indoor positioning based on artificial neural network. IEEE Access. 2020;PP(99):1.10.1109/ACCESS.2020.2988322Search in Google Scholar
[2] He Q. Model of computer network topology optimization based on pattern recognition technology. Int J Technol Manag. 2017;6:16–8.Search in Google Scholar
[3] Ruo-Qiang F, Feng-Cheng L, Wei-Jia X, Min M, Yang L. Topology optimization method of lattice structures based on a genetic algorithm. Int J Steel Struct. 2016;16(3):743–53.10.1007/s13296-015-0208-8Search in Google Scholar
[4] Seo JH, Yoon Y, Kim YH. An efficient large-scale sensor deployment using a parallel genetic algorithm based on CUDA. Int J Distrib Sens Netw. 2016;2016(1):1–17.10.1155/2016/8612128Search in Google Scholar
[5] Liu S, Wang N. Collaborative optimization scheduling of cloud service resources based on improved genetic algorithm. IEEE Access. 2020;PP(99):1.10.1109/ACCESS.2020.3016762Search in Google Scholar
[6] Sengottuvelan P, Prasath N. BAFSA: breeding artificial fish swarm algorithm for optimal cluster head selection in wireless sensor networks. Wirel Pers Commun. 2016;94(4):1–13.10.1007/s11277-016-3340-7Search in Google Scholar
[7] Miao Y, Wang Y, Cai D, Wang X. A hybrid genetic algorithm for the minimum exposure path problem of wireless sensor networks based on a numerical functional extreme model. IEEE Trans Vehicular Technol. 2016;65(10):8644–57.10.1109/TVT.2015.2508504Search in Google Scholar
[8] Chang H, Yang J. Automated selection of a channel subset based on the genetic algorithm in a motor imagery brain-computer interface system. IEEE Access. 2019;PP(99):1.10.1109/ACCESS.2019.2944938Search in Google Scholar
[9] Abdessamad ER, Saber M, Chehri A, Saadane R, Jeon G. Optimization of spectrum utilization parameters in cognitive radio using genetic algorithm-NC-ND license. Procedia Comput Sci. 2020;176(2020):2466–75.10.1016/j.procs.2020.09.328Search in Google Scholar
[10] Afsharinejad A, Davy A, Jennings B. Dynamic channel allocation in electromagnetic nanonetworks for high resolution monitoring of plants. Nano Commun Netw. 2016;7:2–16.10.1016/j.nancom.2015.01.001Search in Google Scholar
[11] Osamy W, El-Sawy AA, Khedr AM. Effective TDMA scheduling for tree-based data collection using genetic algorithm in wireless sensor networks. Peer-to-Peer Netw Appl. 2020;13(3):796–815.10.1007/s12083-019-00818-zSearch in Google Scholar
[12] Xu L, Tan GZ, Xia Z. Probabilistic inference-based service level objective-sensitive virtual network reconfiguration. Comput Commun. 2015;57:25–36.10.1016/j.comcom.2014.10.005Search in Google Scholar
[13] Liu G, Wei X, Zhang S, Cai J, Liu S. Analysis of epileptic seizure detection method based on improved genetic algorithm optimization back propagation neural network. Sheng wu yi xue gong cheng xue za zhi = J Biomed Eng = Shengwu yixue gongchengxue zazhi. 2019;36(1):24–32.Search in Google Scholar
[14] Aizaz Z, Sinha P. A survey of cognitive radio reconfigurable antenna design and proposed design using genetic algorithm. Int J Comput Appl. 2016;137(3):11–6.10.1109/SCEECS.2016.7509263Search in Google Scholar
[15] Jiang W, Fu X, Chang J, Qin R. An improved de-interleaving algorithm of radar pulses based on SOFM with self-adaptive network topology. J Syst Eng Electron. 2020;31(4):712–21.10.23919/JSEE.2020.000046Search in Google Scholar
[16] Zheng W, Qiao J, Feng L, Fu P. Optimal cooperative virtual multi-input and multi-output network communication by double improved ant colony system and genetic algorithm. IAENG Int J Comput Sci. 2018;45(1):89–96.Search in Google Scholar
[17] Barekatain B, Dehghani S, Pourzaferani M. An energy-aware routing protocol for wireless sensor networks based on new combination of genetic algorithm and k-means. Procedia Comput Sci. 2015;72(12):552–60.10.1016/j.procs.2015.12.163Search in Google Scholar
[18] Zahedi A, Rajamand S, Jafari S, Rajati MR. A novel multiuser detector based on restricted search space and depth-first tree search method in DS/CDMA communication systems. Wirel Pers Commun. 2015;82(3):1531–45.10.1007/s11277-015-2297-2Search in Google Scholar
[19] Bui LT, Huynh TTB. A survivable design of last mile communication networks using multi-objective genetic algorithms. Memetic Comput. 2016;8(2):1–12.10.1007/s12293-015-0177-7Search in Google Scholar
[20] Ouamri MA, Azni M. New optimisation method to minimise overshooting problem in LTE using genetic algorithms based on laplace crossover. Int J Ultra Wideb Commun Syst. 2020;4(2):49.10.1504/IJUWBCS.2020.110544Search in Google Scholar
[21] Hussain W. Optimization of construction resource allocation and levelling using genetic algorithm. Int J Innov Res Computer Commun Eng. 2015;4(6):4573–8.Search in Google Scholar
[22] Shanthi DL. Energy efficient intelligent routing in WSN using dominant genetic algorithm. Int J Electr Comput Eng. 2020;10(1):500.10.11591/ijece.v10i1.pp500-511Search in Google Scholar
[23] Demir MS, Sait SM, Uysal M. Unified resource allocation and mobility management technique using particle swarm optimization for VLC networks. Photonics J. 2018;10(6):1–9.10.1109/JPHOT.2018.2864139Search in Google Scholar
[24] Lu C. Research on optimization of computer network quality of service based on improved RED algorithm. Rev Fac de Ing. 2017;32(4):321–8.Search in Google Scholar
[25] Li Z, Chen K. Research on timing optimization of reginal traffic signals based on improved genetic algorithm. IOP Conf Ser Mater Sci Eng. 2018;423(1):012191.10.1088/1757-899X/423/1/012191Search in Google Scholar
[26] Miao SC, Yang JH, Wang XH, Ji-Cheng LI, Tai-Long LI. Blade pattern optimization of the hydraulic turbine based on neural network and genetic algorithm. J Aerosp Power. 2015;30(8):1918–25.Search in Google Scholar
© 2022 Hua Ai et al., published by De Gruyter
This work is licensed under the Creative Commons Attribution 4.0 International License.
Articles in the same Issue
- Research Articles
- Construction of 3D model of knee joint motion based on MRI image registration
- Evaluation of several initialization methods on arithmetic optimization algorithm performance
- Application of visual elements in product paper packaging design: An example of the “squirrel” pattern
- Deep learning approach to text analysis for human emotion detection from big data
- Cognitive prediction of obstacle's movement for reinforcement learning pedestrian interacting model
- The application of neural network algorithm and embedded system in computer distance teach system
- Machine translation of English speech: Comparison of multiple algorithms
- Automatic control of computer application data processing system based on artificial intelligence
- A secure framework for IoT-based smart climate agriculture system: Toward blockchain and edge computing
- Application of mining algorithm in personalized Internet marketing strategy in massive data environment
- On the correction of errors in English grammar by deep learning
- Research on intelligent interactive music information based on visualization technology
- Extractive summarization of Malayalam documents using latent Dirichlet allocation: An experience
- Conception and realization of an IoT-enabled deep CNN decision support system for automated arrhythmia classification
- Masking and noise reduction processing of music signals in reverberant music
- Cat swarm optimization algorithm based on the information interaction of subgroup and the top-N learning strategy
- State feedback based on grey wolf optimizer controller for two-wheeled self-balancing robot
- Research on an English translation method based on an improved transformer model
- Short-term prediction of parking availability in an open parking lot
- PUC: parallel mining of high-utility itemsets with load balancing on spark
- Image retrieval based on weighted nearest neighbor tag prediction
- A comparative study of different neural networks in predicting gross domestic product
- A study of an intelligent algorithm combining semantic environments for the translation of complex English sentences
- IoT-enabled edge computing model for smart irrigation system
- A study on automatic correction of English grammar errors based on deep learning
- A novel fingerprint recognition method based on a Siamese neural network
- A hidden Markov optimization model for processing and recognition of English speech feature signals
- Crime reporting and police controlling: Mobile and web-based approach for information-sharing in Iraq
- Convex optimization for additive noise reduction in quantitative complex object wave retrieval using compressive off-axis digital holographic imaging
- CRNet: Context feature and refined network for multi-person pose estimation
- Improving the efficiency of intrusion detection in information systems
- Research on reform and breakthrough of news, film, and television media based on artificial intelligence
- An optimized solution to the course scheduling problem in universities under an improved genetic algorithm
- An adaptive RNN algorithm to detect shilling attacks for online products in hybrid recommender system
- Computing the inverse of cardinal direction relations between regions
- Human-centered artificial intelligence-based ice hockey sports classification system with web 4.0
- Construction of an IoT customer operation analysis system based on big data analysis and human-centered artificial intelligence for web 4.0
- An improved Jaya optimization algorithm with ring topology and population size reduction
- Review Articles
- A review on voice pathology: Taxonomy, diagnosis, medical procedures and detection techniques, open challenges, limitations, and recommendations for future directions
- An extensive review of state-of-the-art transfer learning techniques used in medical imaging: Open issues and challenges
- Special Issue: Explainable Artificial Intelligence and Intelligent Systems in Analysis For Complex Problems and Systems
- Tree-based machine learning algorithms in the Internet of Things environment for multivariate flood status prediction
- Evaluating OADM network simulation and an overview based metropolitan application
- Radiography image analysis using cat swarm optimized deep belief networks
- Comparative analysis of blockchain technology to support digital transformation in ports and shipping
- IoT network security using autoencoder deep neural network and channel access algorithm
- Large-scale timetabling problems with adaptive tabu search
- Eurasian oystercatcher optimiser: New meta-heuristic algorithm
- Trip generation modeling for a selected sector in Baghdad city using the artificial neural network
- Trainable watershed-based model for cornea endothelial cell segmentation
- Hessenberg factorization and firework algorithms for optimized data hiding in digital images
- The application of an artificial neural network for 2D coordinate transformation
- A novel method to find the best path in SDN using firefly algorithm
- Systematic review for lung cancer detection and lung nodule classification: Taxonomy, challenges, and recommendation future works
- Special Issue on International Conference on Computing Communication & Informatics
- Edge detail enhancement algorithm for high-dynamic range images
- Suitability evaluation method of urban and rural spatial planning based on artificial intelligence
- Writing assistant scoring system for English second language learners based on machine learning
- Dynamic evaluation of college English writing ability based on AI technology
- Image denoising algorithm of social network based on multifeature fusion
- Automatic recognition method of installation errors of metallurgical machinery parts based on neural network
- An FCM clustering algorithm based on the identification of accounting statement whitewashing behavior in universities
- Emotional information transmission of color in image oil painting
- College music teaching and ideological and political education integration mode based on deep learning
- Behavior feature extraction method of college students’ social network in sports field based on clustering algorithm
- Evaluation model of multimedia-aided teaching effect of physical education course based on random forest algorithm
- Venture financing risk assessment and risk control algorithm for small and medium-sized enterprises in the era of big data
- Interactive 3D reconstruction method of fuzzy static images in social media
- The impact of public health emergency governance based on artificial intelligence
- Optimal loading method of multi type railway flatcars based on improved genetic algorithm
- Special Issue: Evolution of Smart Cities and Societies using Emerging Technologies
- Data mining applications in university information management system development
- Implementation of network information security monitoring system based on adaptive deep detection
- Face recognition algorithm based on stack denoising and self-encoding LBP
- Research on data mining method of network security situation awareness based on cloud computing
- Topology optimization of computer communication network based on improved genetic algorithm
- Implementation of the Spark technique in a matrix distributed computing algorithm
- Construction of a financial default risk prediction model based on the LightGBM algorithm
- Application of embedded Linux in the design of Internet of Things gateway
- Research on computer static software defect detection system based on big data technology
- Study on data mining method of network security situation perception based on cloud computing
- Modeling and PID control of quadrotor UAV based on machine learning
- Simulation design of automobile automatic clutch based on mechatronics
- Research on the application of search algorithm in computer communication network
- Special Issue: Artificial Intelligence based Techniques and Applications for Intelligent IoT Systems
- Personalized recommendation system based on social tags in the era of Internet of Things
- Supervision method of indoor construction engineering quality acceptance based on cloud computing
- Intelligent terminal security technology of power grid sensing layer based upon information entropy data mining
- Deep learning technology of Internet of Things Blockchain in distribution network faults
- Optimization of shared bike paths considering faulty vehicle recovery during dispatch
- The application of graphic language in animation visual guidance system under intelligent environment
- Iot-based power detection equipment management and control system
- Estimation and application of matrix eigenvalues based on deep neural network
- Brand image innovation design based on the era of 5G internet of things
- Special Issue: Cognitive Cyber-Physical System with Artificial Intelligence for Healthcare 4.0.
- Auxiliary diagnosis study of integrated electronic medical record text and CT images
- A hybrid particle swarm optimization with multi-objective clustering for dermatologic diseases diagnosis
- An efficient recurrent neural network with ensemble classifier-based weighted model for disease prediction
- Design of metaheuristic rough set-based feature selection and rule-based medical data classification model on MapReduce framework
Articles in the same Issue
- Research Articles
- Construction of 3D model of knee joint motion based on MRI image registration
- Evaluation of several initialization methods on arithmetic optimization algorithm performance
- Application of visual elements in product paper packaging design: An example of the “squirrel” pattern
- Deep learning approach to text analysis for human emotion detection from big data
- Cognitive prediction of obstacle's movement for reinforcement learning pedestrian interacting model
- The application of neural network algorithm and embedded system in computer distance teach system
- Machine translation of English speech: Comparison of multiple algorithms
- Automatic control of computer application data processing system based on artificial intelligence
- A secure framework for IoT-based smart climate agriculture system: Toward blockchain and edge computing
- Application of mining algorithm in personalized Internet marketing strategy in massive data environment
- On the correction of errors in English grammar by deep learning
- Research on intelligent interactive music information based on visualization technology
- Extractive summarization of Malayalam documents using latent Dirichlet allocation: An experience
- Conception and realization of an IoT-enabled deep CNN decision support system for automated arrhythmia classification
- Masking and noise reduction processing of music signals in reverberant music
- Cat swarm optimization algorithm based on the information interaction of subgroup and the top-N learning strategy
- State feedback based on grey wolf optimizer controller for two-wheeled self-balancing robot
- Research on an English translation method based on an improved transformer model
- Short-term prediction of parking availability in an open parking lot
- PUC: parallel mining of high-utility itemsets with load balancing on spark
- Image retrieval based on weighted nearest neighbor tag prediction
- A comparative study of different neural networks in predicting gross domestic product
- A study of an intelligent algorithm combining semantic environments for the translation of complex English sentences
- IoT-enabled edge computing model for smart irrigation system
- A study on automatic correction of English grammar errors based on deep learning
- A novel fingerprint recognition method based on a Siamese neural network
- A hidden Markov optimization model for processing and recognition of English speech feature signals
- Crime reporting and police controlling: Mobile and web-based approach for information-sharing in Iraq
- Convex optimization for additive noise reduction in quantitative complex object wave retrieval using compressive off-axis digital holographic imaging
- CRNet: Context feature and refined network for multi-person pose estimation
- Improving the efficiency of intrusion detection in information systems
- Research on reform and breakthrough of news, film, and television media based on artificial intelligence
- An optimized solution to the course scheduling problem in universities under an improved genetic algorithm
- An adaptive RNN algorithm to detect shilling attacks for online products in hybrid recommender system
- Computing the inverse of cardinal direction relations between regions
- Human-centered artificial intelligence-based ice hockey sports classification system with web 4.0
- Construction of an IoT customer operation analysis system based on big data analysis and human-centered artificial intelligence for web 4.0
- An improved Jaya optimization algorithm with ring topology and population size reduction
- Review Articles
- A review on voice pathology: Taxonomy, diagnosis, medical procedures and detection techniques, open challenges, limitations, and recommendations for future directions
- An extensive review of state-of-the-art transfer learning techniques used in medical imaging: Open issues and challenges
- Special Issue: Explainable Artificial Intelligence and Intelligent Systems in Analysis For Complex Problems and Systems
- Tree-based machine learning algorithms in the Internet of Things environment for multivariate flood status prediction
- Evaluating OADM network simulation and an overview based metropolitan application
- Radiography image analysis using cat swarm optimized deep belief networks
- Comparative analysis of blockchain technology to support digital transformation in ports and shipping
- IoT network security using autoencoder deep neural network and channel access algorithm
- Large-scale timetabling problems with adaptive tabu search
- Eurasian oystercatcher optimiser: New meta-heuristic algorithm
- Trip generation modeling for a selected sector in Baghdad city using the artificial neural network
- Trainable watershed-based model for cornea endothelial cell segmentation
- Hessenberg factorization and firework algorithms for optimized data hiding in digital images
- The application of an artificial neural network for 2D coordinate transformation
- A novel method to find the best path in SDN using firefly algorithm
- Systematic review for lung cancer detection and lung nodule classification: Taxonomy, challenges, and recommendation future works
- Special Issue on International Conference on Computing Communication & Informatics
- Edge detail enhancement algorithm for high-dynamic range images
- Suitability evaluation method of urban and rural spatial planning based on artificial intelligence
- Writing assistant scoring system for English second language learners based on machine learning
- Dynamic evaluation of college English writing ability based on AI technology
- Image denoising algorithm of social network based on multifeature fusion
- Automatic recognition method of installation errors of metallurgical machinery parts based on neural network
- An FCM clustering algorithm based on the identification of accounting statement whitewashing behavior in universities
- Emotional information transmission of color in image oil painting
- College music teaching and ideological and political education integration mode based on deep learning
- Behavior feature extraction method of college students’ social network in sports field based on clustering algorithm
- Evaluation model of multimedia-aided teaching effect of physical education course based on random forest algorithm
- Venture financing risk assessment and risk control algorithm for small and medium-sized enterprises in the era of big data
- Interactive 3D reconstruction method of fuzzy static images in social media
- The impact of public health emergency governance based on artificial intelligence
- Optimal loading method of multi type railway flatcars based on improved genetic algorithm
- Special Issue: Evolution of Smart Cities and Societies using Emerging Technologies
- Data mining applications in university information management system development
- Implementation of network information security monitoring system based on adaptive deep detection
- Face recognition algorithm based on stack denoising and self-encoding LBP
- Research on data mining method of network security situation awareness based on cloud computing
- Topology optimization of computer communication network based on improved genetic algorithm
- Implementation of the Spark technique in a matrix distributed computing algorithm
- Construction of a financial default risk prediction model based on the LightGBM algorithm
- Application of embedded Linux in the design of Internet of Things gateway
- Research on computer static software defect detection system based on big data technology
- Study on data mining method of network security situation perception based on cloud computing
- Modeling and PID control of quadrotor UAV based on machine learning
- Simulation design of automobile automatic clutch based on mechatronics
- Research on the application of search algorithm in computer communication network
- Special Issue: Artificial Intelligence based Techniques and Applications for Intelligent IoT Systems
- Personalized recommendation system based on social tags in the era of Internet of Things
- Supervision method of indoor construction engineering quality acceptance based on cloud computing
- Intelligent terminal security technology of power grid sensing layer based upon information entropy data mining
- Deep learning technology of Internet of Things Blockchain in distribution network faults
- Optimization of shared bike paths considering faulty vehicle recovery during dispatch
- The application of graphic language in animation visual guidance system under intelligent environment
- Iot-based power detection equipment management and control system
- Estimation and application of matrix eigenvalues based on deep neural network
- Brand image innovation design based on the era of 5G internet of things
- Special Issue: Cognitive Cyber-Physical System with Artificial Intelligence for Healthcare 4.0.
- Auxiliary diagnosis study of integrated electronic medical record text and CT images
- A hybrid particle swarm optimization with multi-objective clustering for dermatologic diseases diagnosis
- An efficient recurrent neural network with ensemble classifier-based weighted model for disease prediction
- Design of metaheuristic rough set-based feature selection and rule-based medical data classification model on MapReduce framework

