Abstract
Due to the precise and continuous regulation of phase, holographic encryption based on metasurfaces and liquid crystals (LCs) has been proposed to encrypt the information by manipulating the wavelength, polarization, etc. However, the security cannot be fully guaranteed since the requirements of decoding methods for these schemes are generally not very strict and vulnerable for exhaustive attack. Furthermore, any part of the hologram stolen may lead to the disclosure of the hidden information regardless of the generation mode of phase delay or the selection of media material, so the security needs to be further improved. Here, inspired by Tiger Amulet, embodying the encryption consciousness of ancient China, we propose a simple but effective encryption method and design a “four-in-one” hologram based on photopatterned LCs. Specifically, the most important encrypted image can only be displayed when the four LC holograms in the same group are spliced into a whole according to the designed order. On the contrary, the camouflage information would be displayed if the holograms are placed in the optical path separately or spliced in wrong order. It is even more interesting that with the LC directors tilted with applied external voltages, the holographic efficiency of the LC hologram will change accordingly. This sets further demanding requirement on the decryption condition and thus increases the encryption security. With the advantages of simple design, high security, and low crosstalk, our encryption scheme has great potential in the fields of information hiding and image encryption.
1 Introduction
With the development of information technology, people are exchanging information more and more frequently. In this context, the issue of information security has received more attention than ever before, and amounts of efforts are put in exploring new encryption technology to enhance the information security. Among numerous technical methods, optical holographic encryption, as a new encryption approach, has become one of the most important research contents of modern encryption technology due to its unique technical characteristics [1, 2]. In optical holographic encryption, information can be hidden in a variety of parameters, such as phase, spatial frequency, polarization or wavelength, which empowers the optical encryption excellent coding capacity and flexible key design.
In recent years, the research of metasurfaces based on Pancharatnam–Berry (PB) phase has attracted a lot of attention. Due to its precise and continuous phase regulation without increasing the processing complexity, it enables the reconstruction of high-quality holographic images [3–7]. Thus, meta-holograms are increasingly used in the field of optical encryption [8–12]. Many feasible methods are to encrypt the information by manipulating the wavelength [13, 14], polarization [15–18], incidence angle [19], topological charge [20, 21], observation spaces [22–24] or spatial frequency range [25] and so on. Meanwhile, liquid crystals (LCs) have also been widely used in spatial light modulations owing to the unique optical characteristics of polarization control and sensitivity to external stimuli response. Designed LCs and meta-holograms can be combined to realize stimuli-responsive dynamic displays [26–28]. Thus, LC-integrated metasurfaces can also work as a candidate for information encryption, which can be implemented by changing the applied voltages [29, 30] or environmental temperature [31]. Recently, researchers have found that LC can control the PB phase of light waves like metasurface, and holographic encryption based on LCs has been proposed [32–34]. Compared to meta-hologram, LC holographic encryption has the advantages of adjustable spectral response, large-area manufacturing, high efficiency, low cost, dynamic switching ability, easy cutting and splicing, and compatibility with existing commercial LCD devices [35–37]. However, the security cannot be fully guaranteed since the requirements of decoding methods for these schemes are generally not very strict to some extent. It is still possible to get the hidden information in the case of wavelength offset in a certain range, polarization state with an error and less accurate incidence angle, etc. Even if the information may not be as clear and accurate, it is not far from complete decryption. Furthermore, because any part of the hologram designed by the traditional algorithms contains the hidden information, any part stolen may lead to the disclosure of the hidden information regardless of the generation mode of phase delay (geometric phase, transmission phase, etc.) or the selection of media material (metasurfaces, LCs). Thus, the security needs to be further improved.
Inspired by Tiger Amulet, a tiger-shaped tally issued to generals as imperial authorization for troop movement in ancient China, we propose a high-security encryption method based on “four-in-one” LC hologram to address the problem of information disclosure in holographic encryption. The basic idea of how the Tiger Amulet works is schematically demonstrated in Figure 1(a). It could be seen that only the Tiger Amulet in the same group can be combined to form a complete pattern and plays the role of conveying orders, while the forged Tiger Amulet cannot be closely matched with the real one to show the real meaningful information. Our encryption method works in a similar logic: as shown in Figure 1(c), the most important encrypted image can only be displayed when the four LC holograms in the same group are spliced into a whole according to the designed order; when they are spliced in the wrong order or placed in the optical path respectively, camouflage information instead of actually encrypted information would be decoded, as seen in Figure 1(b). With many advantages such as large-area manufacturing and low cost, LC is chosen as the media material to implement our new encryption method. Moreover, by applying external voltages, the out-of-plane orientation angles of LC director will vary [38], leading to different holographic efficiency and more demanding decryption condition. Therefore, our method provides an encryption scheme with simple design, high security, and low crosstalk, which has great potential in the fields of information hiding and image encryption.
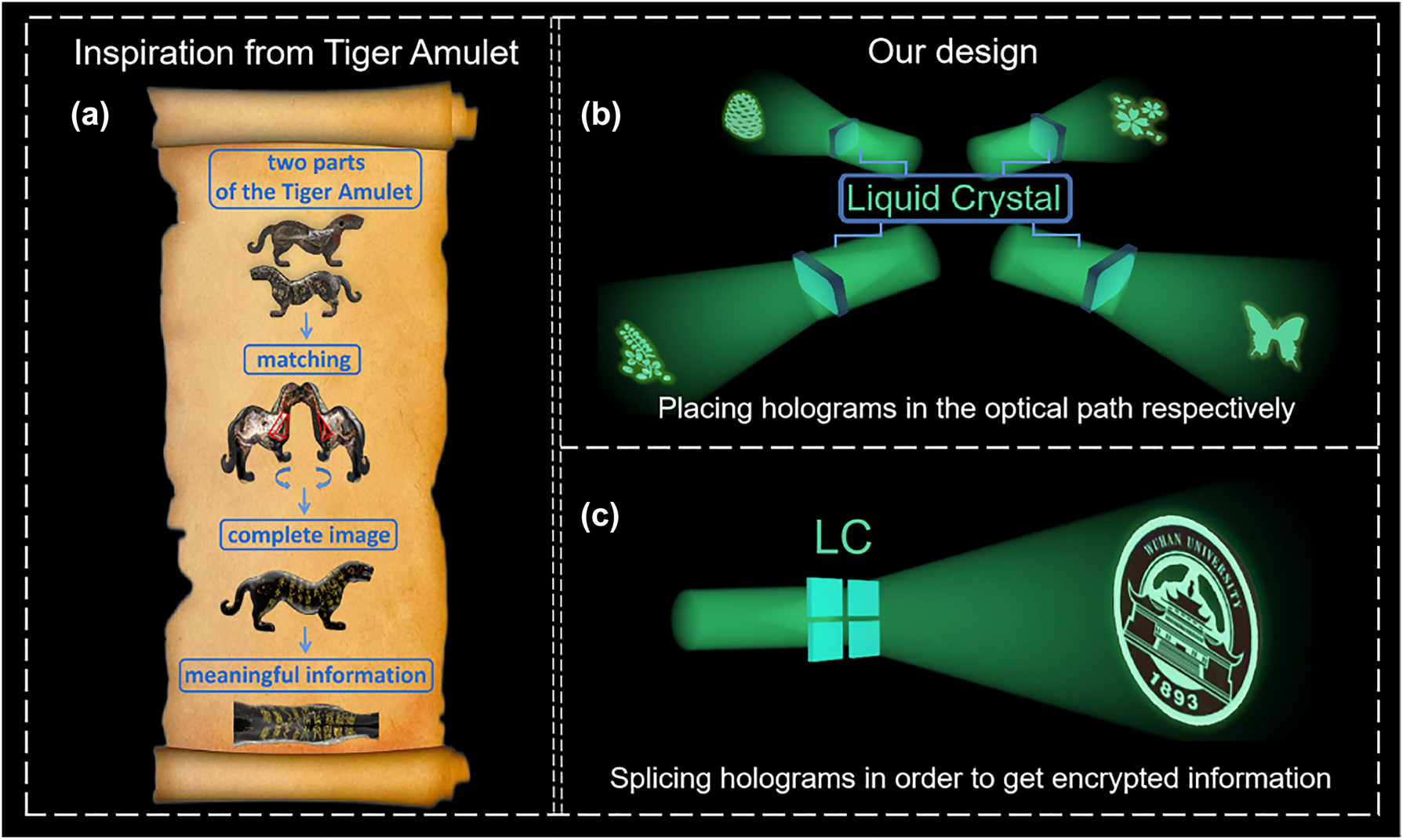
Inspiration and operation schematics of the “four-in-one” LC hologram. (a) The inspiration from Tiger Amulet. (b) Schematic illustration of the reconstruction result when four small holograms are placed in the optical path to work separately. (c) Schematic illustration of the reconstruction result when four small holograms are spliced into a whole.
2 Design of the LC-based four-in-one holograms
LC is an anisotropic medium. It is possible to modulate phase continuously in LCs through PB phase due to the spin orbit interaction of light in heterogeneous anisotropic media [39–41]. An LC director has two orientation angles: an in-plane orientation angle θ and an out-of-plane orientation angle α. We design all working unit-cells of LC device with the same size, but different in-plane orientation angles θ (−90°–90°). Here, we control the PB phase by varying the in-plane orientation angles unit by unit, and the PB phase is exactly twice the in-plane orientation angle.
It is known that separate small holograms can be designed to display different holographic images. Benefiting from the degree of freedom in the holographic design, it is possible to display another holographic image when the phase matrices of separate small holograms are combined into the phase matrix of a large hologram according to a designed order. Based on this general idea, we propose a hologram encryption iterative algorithm (HEIA) to calculate the phase distribution of LC hologram to realize the “four-in-one” holographic encryption. In our design, the overall iterative optimization of five images is carried out, and the correlation coefficient is used to evaluate the quality of the reconstructed image. In each iteration, we also introduce different weight information to different images to adjust the reconstruction quality of images with different sizes. By carefully designing the weighted value of the amplitude of the desired output light field and that in the calculated result, high reconstruction quality of all the five images can be achieved. For the optimization of each separate holograms, an improved angular spectrum method (IASM) is utilized, and the flow chart is shown in Figure 2. Different from its traditional counterpart, in this method the amplitude of the updated output light field is made up of the weighted value of the desired and calculated light field amplitude, which replaces the preceding one obtained by angular spectrum diffraction. By following this process, the diffraction result of each iteration will be superimposed on the output light field information. After inverse diffraction, it will return to the input light field as feedback, so as to accelerate the iteration speed [42].
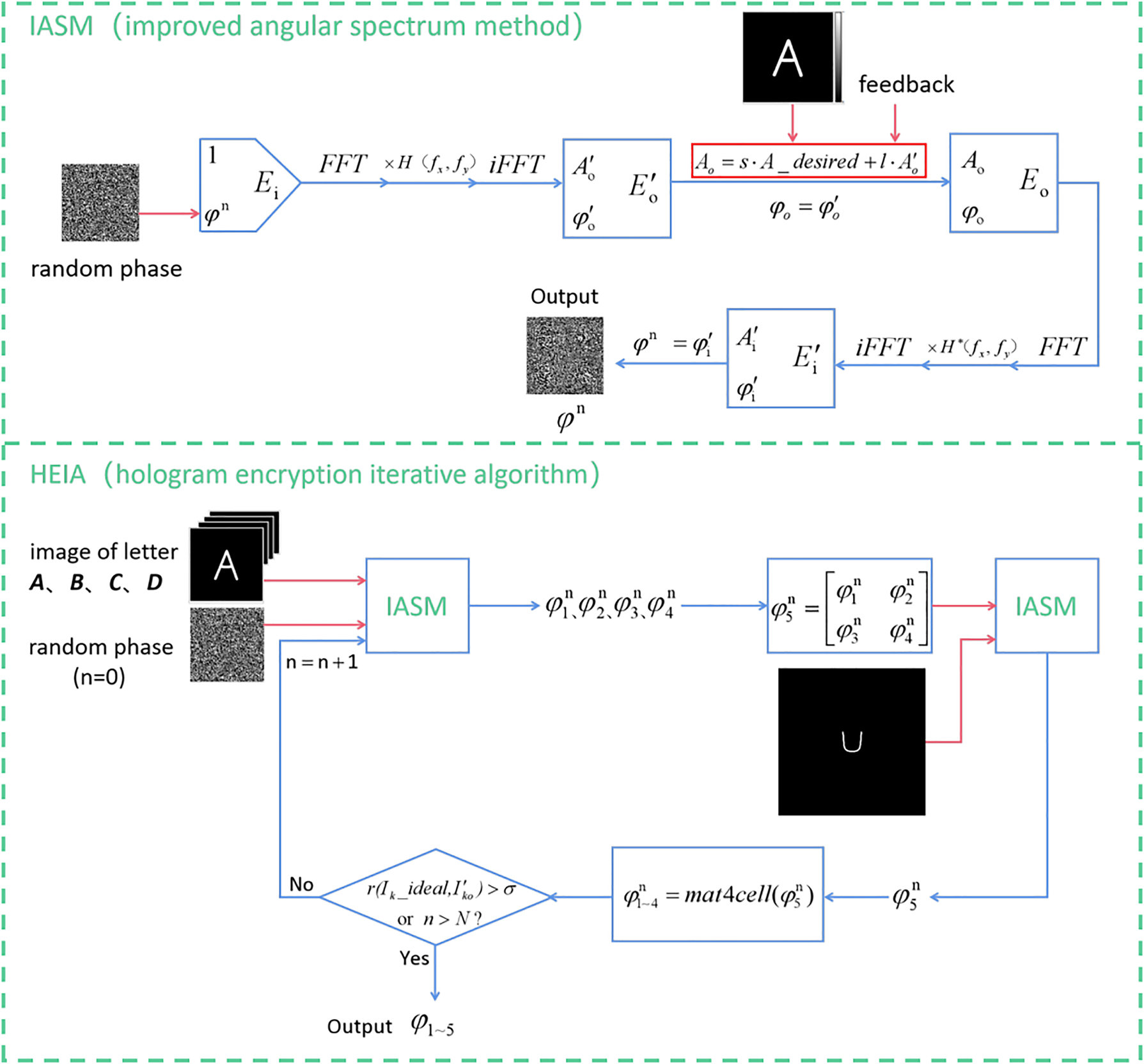
Flowchart of the improved angular spectrum method and hologram encryption iterative algorithm. “FFT” and “iFFT” represent fast Fourier transformation and inverse fast Fourier transformation, respectively. “H” represents angular spectrum propagation function and “H*” represents its conjugate.
After four holographic images (A, B, C, D) and random phase are put into the IASM in turn, we will get the four matrices of phase information for the current iteration. After that we combine four small phase matrices into the phase matrix of the large hologram. When putting it and the encrypted holographic image (U) into IASM and then getting the new large phase matrix, the phase matrix of the large hologram is decomposed into four small phase matrices and one iteration process is completed. Finally, the iterative process for the whole is repeated until the correlation coefficient between the desired light intensity distribution and that calculated by diffraction theory is greater than the preset threshold σ or the number of iterations n reaches N (the maximum number of iterations). In the end, we get the phases of the designed hologram.
3 Experimental demonstration of the LC-based holographic encryption
Based on the hologram encryption iterative algorithm, we design an LC device to realize the display of different patterns of four small LC holograms separately and combined. The four small LC holograms are composed of 124 × 124 pixels, and four different letter images (“A”, “B”, “C”, and “D”) are selected as the target images. Another letter image (“U”) is selected as the target image for the large hologram.
The fabrication process of the LC sample can be mainly divided into two parts: one is the preparation of the LC empty cell, and the other is the photopatterning technology to realize the designed in-plane LC orientations. First, ITO glass substrates were spin-coated with the UV-polarization-sensitive azo-dye SD1 layer, and then covered with the other substrate to form the empty cell with 8 μm spacers. Second, the DMD-based dynamic photopatterning system is used to implement the multistep partly overlapping exposure process [37, 43]. The designed in-plane director distributions can be obtained in nematic LCs, forming the LC hologram.
To characterize its performance, the sample is placed in an optical path as shown in Figure 3(a). A super-continuum laser (YSL SC-pro) is used to illuminate the sample. The incident laser beam is converted into circularly polarized (CP) light after passing through the circular polarizer. And a circular analyzer is introduced as an optical filter to make sure all the light that can pass through is cross-polarized CP light. All holographic images were captured by a charge coupled device (CCD).
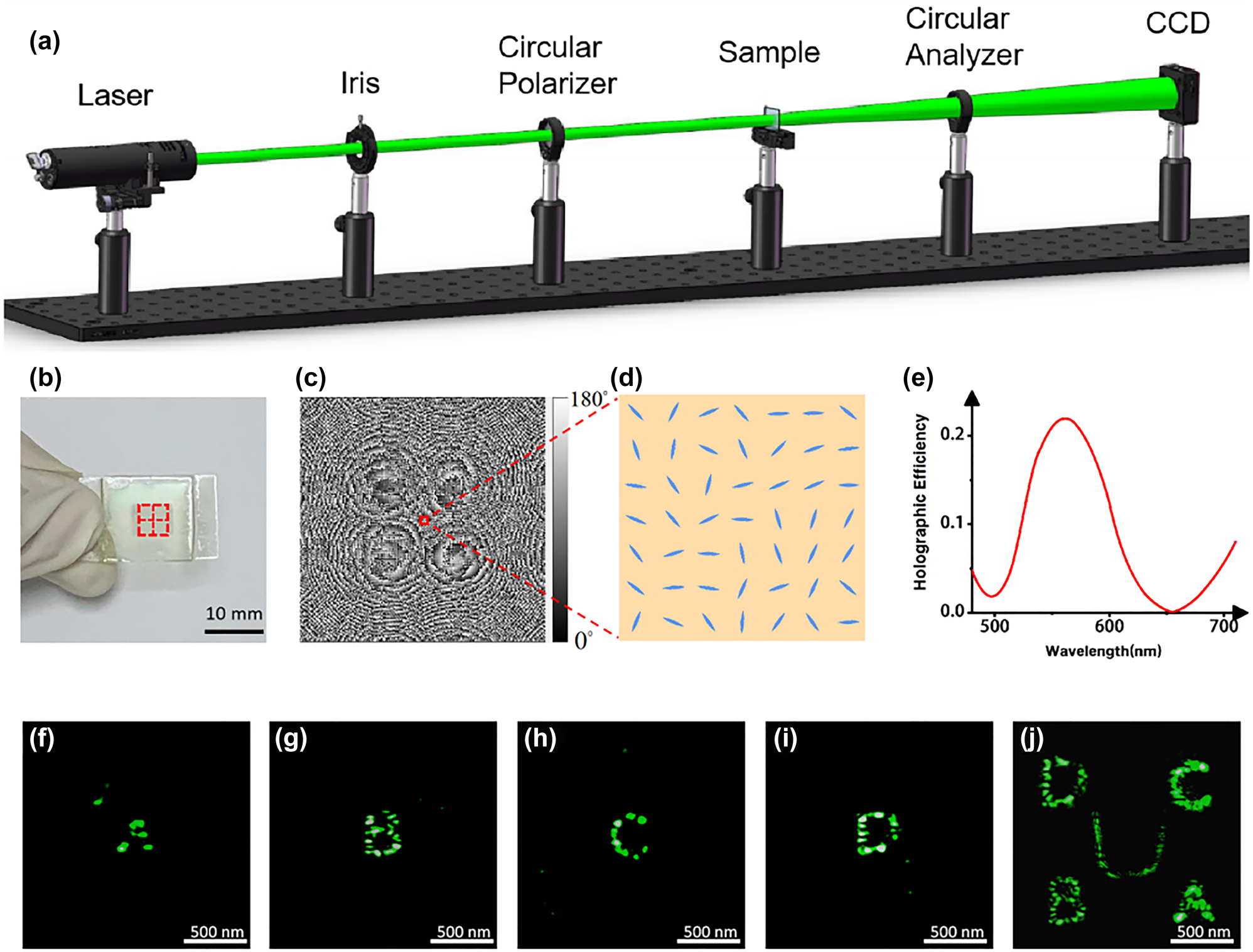
Experimental results of the “four-in-one” LC hologram without applied voltage. (a) Optical setup for observing holographic image. (b) The photo of the “four-in-one” LC hologram and the marked red box indicates the working area. (c) The final in-plane orientation angle distribution. (d) Schematic of zoom-in view of the in-plane orientation angle distribution. (e) Holographic efficiency of the LC device for different wavelengths without applied external voltage. (f)–(j) The captured holographic images of 4 small holographic images and the combined big one at the wavelength of 560 nm.
Figure 3(b) exhibits the LC device composed of 248 × 248 effective working units, which corresponds to the in-plane orientation angles distribution shown in Figure 3(c). In our experiment, the LC cell is 8 μm thick with each working unit-cell measuring 20.7 × 20.7 μm2. We choose 560 nm as the design wavelength. Figure 3(f)–(i) shows the holographic images obtained when the four small holograms are illuminated, respectively, from which it could be seen that all the letters are reconstructed clearly. And the encrypted information, i.e., pattern “U”, could be obtained when the four small holograms are illuminated simultaneously in the right order, which demonstrates the effectiveness of our encryption method. We also measure holographic efficiency, the ratio of the transmitted energy reconstructing the holographic image to the incident light energy, without applied external voltage. Figure 3(e) shows the variant holographic efficiency in the wavelength range from 480 to 710 nm. At the operation wavelength of 560 nm, holographic efficiency reaches its maximum of 22.7%. Moreover, to judge the quality of the holographic images in this work, we use a more intuitive parameter, correlation coefficient [12], to compare the similarity between the experimentally captured images and the target images. The correlations between the captured holographic images (Figure 3(f)–(j)) and the corresponding target images are 0.6978, 0.6863, 0.6802, 0.6776, and 0.6722 respectively. The correlation coefficients for 5 holographic images are higher than 0.67, indicating that the experimental results are in good agreement with the design.
To investigate the broadband response of our sample with different applied voltages, we alter the wavelength of the super-continuum laser source from 470 nm to 620 nm and employ a commercial signal generator to provide an external electric field. Figure 4(a), (e), and (i) shows the experimental results of the holographic efficiency at respective wavelength under the applied voltage ranging from 0 to 5 V. We can see that there is a threshold voltage which means when the voltage does not reach the threshold, the holographic efficiency will not change. Then, the increasing voltage leads to the change of holographic efficiency, which indicates the latent capacity of tunable spectral response. As shown in Figure 4(b)–(d), (f)–(h), and (j)–(l), when choosing wavelengths of 470, 560, and 620 nm, holographic images with different brightness could be obtained under different applied voltages. Moreover, as for a certain operating wavelength, the holographic efficiency would decrease from the maximum to almost zero within a specific applied voltage range, which suggests that we could apply this property to the encryption process.
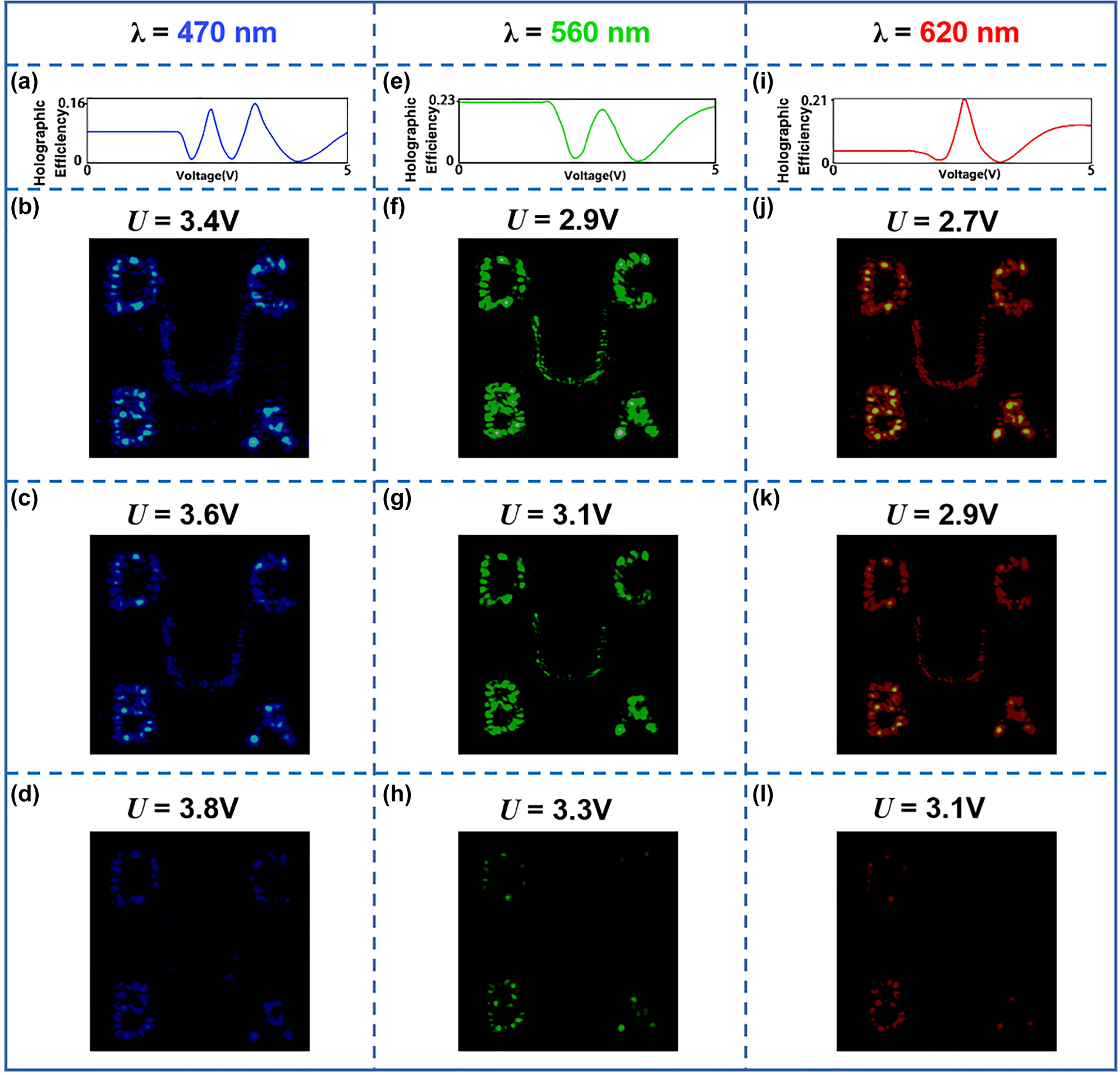
Spectral response of the “four-in-one” LC hologram with different external electric field. (a), (e), and (i) Holographic efficiency for different applied voltages. The operating wavelength is (a) 470 nm, (e) 560 nm, (i) 620 nm. (b)–(d), (f)–(h), and (j)–(l) Holographic images under different applied voltages at the wavelength of (b)–(d) 470 nm, (f)–(h) 560 nm, and (j)–(l) 620 nm.
4 Discussions
In addition to the above experiments, the security of our proposed encryption method is further verified through splicing holograms in different orders, and the results are shown in Figure 5. When four small holograms are jointly designed and spliced in the right order, we can see the letter “U” in the center of holographic image; but when the arrangement order is inconsistent with the designed one, it could be seen from Figure 5(b) that the letter “U” cannot be obtained. Therefore, our design can be used as an encryption device for authentication just like Tiger Amulet. Higher security performance will be obtained if using 6, 8, or even more LC holograms. However, the computing time of the holographic encryption algorithm will increase greatly at the same time. And the setup alignment requirements will become stricter to obtain encrypted information after splicing all the small holograms and the quality of the reconstructed image will also be affected. There is a trade-off when choosing schemes with different number of the LC holograms.
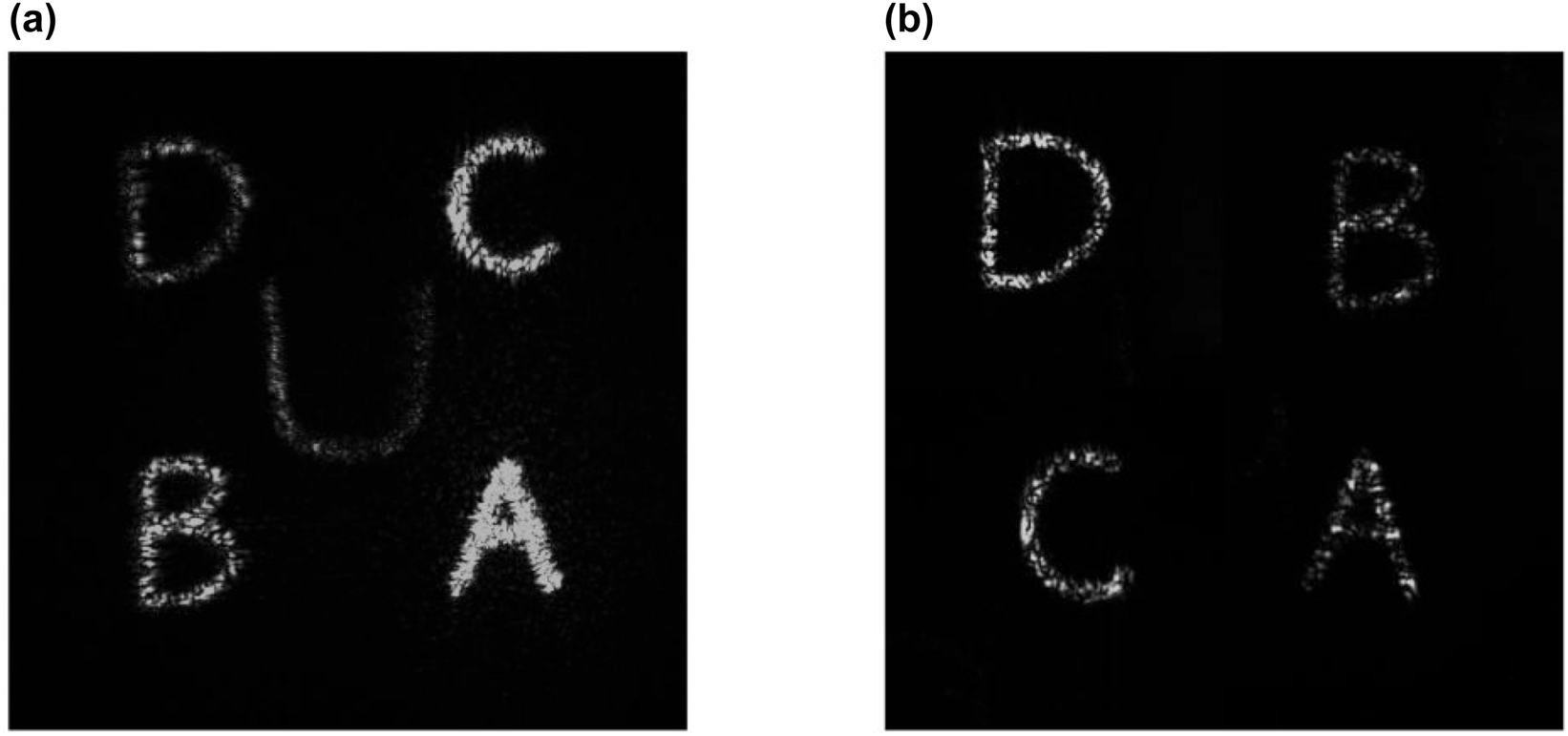
Experimental results of the “four-in-one” LC hologram in different orders. (a) Holographic image of four designed holograms in the right order. (b) Holographic image of four jointly designed holograms in the wrong order.
Our core idea in this work is “multiple in one” correct matching to display correct information, which is inspired by Tiger Amulet. Using this idea and the optimization algorithm proposed in the paper, our design has a further demanding requirement on the decryption condition and thus increases the encryption security regardless of the generation mode of phase delay (geometric phase, transmission phase, etc.) or the selection of media material (metasurfaces, LCs). As a result, the scheme used in our work is free from the problem in previous holographic encryption methods, i.e., any part of the hologram stolen may lead to the disclosure of the hidden information. In a word, the Tiger Amulet technique is used to address the problem of information disclosure in holographic encryption. Overall, the proposed LC hologram encryption scheme has many technical advantages compared to previous solutions. First, in our design, the encrypted image is hidden when the four small holograms work separately in the optical path. But when they are correctly combined, the encrypted image could be decoded and displayed. This breaks through the property that any part of the traditional hologram contains whole object light wave information. So even if a single small hologram is stolen here, the encrypted information cannot be recovered, and only the wrong information as camouflage would be decoded, which increases the information security and mitigate the problem of information disclosure in holographic encryption. Second, benefitting from the electrical tunability of LC materials, i.e., each LC director can tilt from the state of in-plane to out-of-plane when applied external voltages, the encryption safety based on the proposed “four-in-one” LC hologram can be further enhanced. The applied external voltage of the four small holograms can be designed with different value independently, which allows the setting of more demanding conditions to get the encrypted message and reduces the risk of information disclosure. Last but not least, compared with holograms based on metasurfaces, our LC hologram is more practical in terms of large-area manufacturing. Considering current mature technology in LC display industry, our design is simple to implement and it is possible to realize the mass production of the proposed encryption device for practical applications.
5 Conclusions
In this paper, we propose and experimentally demonstrate an encryption method based on the LC hologram. Only when the four holograms in the same group are placed in the optical path at the same time and in the designed order, can the most important encrypted images be displayed. As a contrast, other camouflage images would be displayed when the small holograms work separately in the optical path. Due to the introduction of iterative optimization and the weighted value of the amplitude based on the traditional angular spectrum theory, a new encryption method based on hologram splicing is proposed and demonstrated. Since the observed holographic image would vary as the applied external voltages of the LC hologram changes, the applied electrical signal can also be considered in the encryption process, leading to enhanced security of the encrypted information. And the mature LC display technology makes our design more practical and adaptable. Overall, with these unique characteristics of simple design, high security, low crosstalk, and large-area manufacturing, our proposed LC device has great potential in various applications such as information hiding, image encryption, and so on.
Funding source: Natural Science Foundation of Jiangsu Province
Award Identifier / Grant number: BK20212004
Funding source: Innovation Program for Quantum Science and Technology
Award Identifier / Grant number: 2021ZD0301500
Funding source: National Natural Science Foundation of China
Award Identifier / Grant number: 12174292, 62222507, 62175101, 11904267, 91950110
Funding source: Fundamental Research Funds for the Central Universities
Award Identifier / Grant number: 2042021kf0018
Funding source: Natural Science Foundation of Hubei Province
Award Identifier / Grant number: ZRMS2021000211
Funding source: National Key R&D Program of China
Award Identifier / Grant number: 2021YFE0205800, 2021YFA1202000
-
Author contributions: All the authors have accepted responsibility for the entire content of this submitted manuscript and approved submission.
-
Research funding: National Key R&D Program of China (Grant Nos. 2021YFE0205800, and 2021YFA1202000); National Natural Science Foundation of China (Grant Nos. 12174292, 62222507, 62175101, 11904267 and 91950110); Natural Science Foundation of Hubei Province (Grant Nos. ZRMS2021000211); Innovation Program for Quantum Science and Technology (Grant No. 2021ZD0301500); Natural Science Foundation of Jiangsu Province, Major Project (Grant No. BK20212004), Fundamental Research Funds for the Central Universities (Grant Nos. 2042021kf0018).
-
Conflict of interest statement: The authors declare no conflicts of interest regarding this article.
References
[1] B. Javidi and T. Nomura, “Securing information by use of digital holography,” Opt. Lett., vol. 25, pp. 28–30, 2000. https://doi.org/10.1364/ol.25.000028.Search in Google Scholar PubMed
[2] X. Fang, H. Ren, and M. Gu, “Orbital angular momentum holography for high-security encryption,” Nat. Photonics, vol. 14, pp. 102–108, 2020. https://doi.org/10.1038/s41566-019-0560-x.Search in Google Scholar
[3] M. Khorasaninejad and K. B. Crozier, “Silicon nanofin grating as a miniature chirality-distinguishing beam-splitter,” Nat. Commun., vol. 5, p. 5386, 2014. https://doi.org/10.1038/ncomms6386.Search in Google Scholar PubMed
[4] G. Zheng, H. Mühlenbernd, M. Kenney, G. Li, T. Zentgraf, and S. Zhang, “Metasurface holograms reaching 80% efficiency,” Nat. Nanotechnol., vol. 10, pp. 308–312, 2015. https://doi.org/10.1038/nnano.2015.2.Search in Google Scholar PubMed
[5] Z. Li, G. Zheng, P. He, et al.., “All-silicon nanorod-based Dammann gratings,” Opt. Lett., vol. 40, pp. 4285–4288, 2015. https://doi.org/10.1364/ol.40.004285.Search in Google Scholar
[6] M. Khorasaninejad, W. Chen, R. C. Devlin, J. Oh, A. Zhu, and F. Capasso, “Metalenses at visible wavelengths: diffraction-limited focusing and subwavelength resolution imaging,” Science, vol. 352, pp. 1190–1194, 2016. https://doi.org/10.1126/science.aaf6644.Search in Google Scholar PubMed
[7] Z. Mou, C. Zhou, P. Lu, Q. Yue, S. Wang, and S. Teng, “Structured vortices generated by metasurface holography,” Photon. Res., vol. 9, pp. 2125–2131, 2021. https://doi.org/10.1364/prj.427745.Search in Google Scholar
[8] Q. Dai, Z. Guan, S. Chang, et al.., “A single-celled tri-functional metasurface enabled with triple manipulations of light,” Adv. Funct. Mater., vol. 30, p. 2003990, 2020. https://doi.org/10.1002/adfm.202003990.Search in Google Scholar
[9] L. Deng, J. Deng, Z. Guan, et al.., “Malus-metasurface-assisted polarization multiplexing,” Light Sci. Appl., vol. 9, p. 101, 2020. https://doi.org/10.1038/s41377-020-0327-7.Search in Google Scholar PubMed PubMed Central
[10] C. Liang, L. Deng, Q. Dai, et al.., “Single-celled multifunctional metasurfaces merging structural-color nanoprinting and holography,” Opt. Express, vol. 29, pp. 10737–10748, 2021. https://doi.org/10.1364/oe.420831.Search in Google Scholar
[11] R. Fu, X. Shan, L. Deng, et al.., “Multiplexing meta-hologram with separate control of amplitude and phase,” Opt. Express, vol. 29, pp. 27696–27707, 2021. https://doi.org/10.1364/oe.435986.Search in Google Scholar
[12] Z. Zhou, Y. Wang, C. Chen, et al.., “Holographic meta-image displays enabled by dual-degeneracy,” Small, vol. 18, p. 2106148, 2022. https://doi.org/10.1002/smll.202106148.Search in Google Scholar PubMed
[13] W. Ye, F. Zeuner, X. Li, et al.., “Spin and wavelength multiplexed nonlinear metasurface holography,” Nat. Commun., vol. 7, p. 11930, 2016. https://doi.org/10.1038/ncomms11930.Search in Google Scholar PubMed PubMed Central
[14] L. Jin, Z. Dong, S. Mei, et al.., “Noninterleaved metasurface for (26-1) spin-and wavelength-encoded holograms,” Nano Lett., vol. 18, pp. 8016–8024, 2018. https://doi.org/10.1021/acs.nanolett.8b04246.Search in Google Scholar PubMed
[15] H. C. Liu, B. Yang, Q. Guo, et al.., “Single-pixel computational ghost imaging with helicity-dependent metasurface hologram,” Sci. Adv., vol. 3, p. 1701477, 2017. https://doi.org/10.1126/sciadv.1701477.Search in Google Scholar PubMed PubMed Central
[16] Z. Li, C. Chen, Z. Guan, et al.., “Three-channel metasurfaces for simultaneous meta-holography and meta-nanoprinting: a single-cell design approach,” Laser Photonics Rev., vol. 14, p. 2000032, 2020. https://doi.org/10.1002/lpor.202000032.Search in Google Scholar
[17] X. Shan, Z. Li, Q. Dai, et al.., “Metasurfaces with single-sized antennas for reconstructing full-color holographic images without cross talk,” Opt. Lett., vol. 46, pp. 5417–5420, 2021. https://doi.org/10.1364/ol.442477.Search in Google Scholar
[18] S. Zhang, L. Huang, G. Geng, J. Li, X. Li, and Y. Wang, “Full-Stokes polarization transformations and time sequence metasurface holographic display,” Photon. Res., vol. 10, pp. 1031–1038, 2022. https://doi.org/10.1364/prj.450354.Search in Google Scholar
[19] X. Li, L. Chen, Y. Li, et al.., “Multicolor 3D meta-holography by broadband plasmonic modulation,” Sci. Adv., vol. 2, p. 1601102, 2016. https://doi.org/10.1126/sciadv.1601102.Search in Google Scholar PubMed PubMed Central
[20] L. Jin, Y. W. Huang, Z. Jin, et al.., “Dielectric multi-momentum meta-transformer in the visible,” Nat. Commun., vol. 10, p. 4789, 2019. https://doi.org/10.1038/s41467-019-12637-0.Search in Google Scholar PubMed PubMed Central
[21] H. Ren, X. Fang, J. Jang, J. Bürger, J. Rho, and S. A. Maier, “Complex-amplitude metasurface-based orbital angular momentum holography in momentum space,” Nat. Nanotechnol., vol. 15, pp. 948–955, 2020. https://doi.org/10.1038/s41565-020-0768-4.Search in Google Scholar PubMed
[22] K. Huang, Z. Dong, S. Mei, et al.., “Silicon multi-meta-holograms for the broadband visible light,” Laser Photonics Rev., vol. 10, pp. 500–509, 2016. https://doi.org/10.1002/adom.201700434.Search in Google Scholar
[23] Q. Wei, L. Huang, X. Li, J. Liu, and Y. Wang, “Broadband multiplane holography based on plasmonic metasurface,” Adv. Opt. Mater., vol. 5, p. 1700434, 2017.10.1002/adom.201700434Search in Google Scholar
[24] X. Liang, L. Deng, X. Shan, et al.., “Asymmetric hologram with a single-size nanostructured metasurface,” Opt. Express, vol. 29, pp. 19964–19974, 2021. https://doi.org/10.1364/oe.430217.Search in Google Scholar PubMed
[25] J. Deng, Y. Yang, J. Tao, et al.., “Spatial frequency multiplexed meta-holography and meta-nanoprinting,” ACS Nano, vol. 13, pp. 9237–9246, 2019. https://doi.org/10.1021/acsnano.9b03738.Search in Google Scholar PubMed
[26] M. A. Naveed, J. Kim, I. Javed, et al.., “Novel spin-decoupling strategy in liquid crystal-integrated metasurfaces for interactive metadisplays,” Adv. Opt. Mater., vol. 10, p. 2200196, 2022. https://doi.org/10.1002/adom.202200196.Search in Google Scholar
[27] I. Kim, M. A. Ansari, M. Q. Mehmood, et al.., “Stimuli-responsive dynamic metaholographic displays with designer liquid crystal modulators,” Adv. Mater., vol. 32, p. 2004664, 2020. https://doi.org/10.1002/adma.202004664.Search in Google Scholar PubMed
[28] Y. Ni, C. Chen, S. Wen, X. Xue, L. Sun, and Y. Yang, “Computational spectropolarimetry with a tunable liquid crystal metasurface,” eLight, vol. 2, p. 23, 2022. https://doi.org/10.1186/s43593-022-00032-0.Search in Google Scholar
[29] J. Li, P. Yu, S. Zhang, and N. Liu, “Electrically-controlled digital metasurface device for light projection displays,” Nat. Commun., vol. 11, p. 3574, 2020. https://doi.org/10.1038/s41467-020-17390-3.Search in Google Scholar PubMed PubMed Central
[30] I. Kim, J. Jang, G. Kim, et al.., “Pixelated bifunctional metasurface-driven dynamic vectorial holographic color prints for photonic security platform,” Nat. Commun., vol. 12, p. 3614, 2021. https://doi.org/10.1038/s41467-021-23814-5.Search in Google Scholar PubMed PubMed Central
[31] C. Choi, S. E. Mun, J. Sung, K. Choi, S. Y. Lee, and B. Lee, “Hybrid state engineering of phase-change metasurface for all-optical cryptography,” Adv. Funct. Mater., vol. 31, p. 2007210, 2021. https://doi.org/10.1002/adfm.202007210.Search in Google Scholar
[32] P. Chen, B. Y. Wei, W. Hu, and Y. Q. Lu, “Liquid-crystal-mediated geometric phase: from transmissive to broadband reflective planar optics,” Adv. Mater., vol. 32, p. 1903665, 2020. https://doi.org/10.1002/adma.201903665.Search in Google Scholar PubMed
[33] P. Chen, L. L. Ma, W. Hu, et al.., “Chirality invertible superstructure mediated active planar optics,” Nat. Commun., vol. 10, p. 2518, 2019. https://doi.org/10.1038/s41467-019-10538-w.Search in Google Scholar PubMed PubMed Central
[34] Z. X. Li, Y. P. Ruan, P. Chen, et al.., “Liquid crystal devices for vector vortex beams manipulation and quantum information applications,” Chin. Opt. Lett., vol. 19, p. 112601, 2021. https://doi.org/10.3788/col202119.112601.Search in Google Scholar
[35] J. Xiong and S. T. Wu, “Planar liquid crystal polarization optics for augmented reality and virtual reality: from fundamentals to applications,” eLight, vol. 1, p. 3, 2021. https://doi.org/10.1186/s43593-021-00003-x.Search in Google Scholar
[36] K. Chen, C. Xu, Z. Zhou, et al.., “Multifunctional liquid crystal device for grayscale pattern display and holography with tunable spectral-response,” Laser Photonics Rev., vol. 16, p. 2100591, 2022. https://doi.org/10.1002/lpor.202100591.Search in Google Scholar
[37] P. Chen, Z. X. Shen, C. T. Xu, et al.., “Simultaneous realization of dynamic and hybrid multiplexed holography via light-activated chiral superstructures,” Laser Photonics Rev., vol. 16, p. 2200011, 2022. https://doi.org/10.1002/lpor.202200011.Search in Google Scholar
[38] C. T. Wang, A. Tam, C. Meng, M. C. Tseng, G. Li, and H. S. Kwok, “Voltage-controlled liquid crystal Pancharatnam-Berry phase lens with broadband operation and high photo-stability,” Opt. Lett., vol. 45, pp. 5323–5326, 2020. https://doi.org/10.1364/ol.395342.Search in Google Scholar PubMed
[39] Z. Li, S. Yu, and G. Zheng, “Advances in exploiting the degrees of freedom in nanostructured metasurface design: from 1 to 3 to more,” Nanophotonics, vol. 9, pp. 3699–3731, 2020. https://doi.org/10.1515/nanoph-2020-0127.Search in Google Scholar
[40] M. Berry, “Quantal phase factors accompanying adiabatic changes,” Proc. Roy. Soc. Lond. Math. Phys. Sci., vol. 392, pp. 45–57, 1984.10.1098/rspa.1984.0023Search in Google Scholar
[41] L. Zhu, C. T. Xu, P. Chen, et al.., “Pancharatnam-Berry phase reversal via opposite-chirality-coexisted superstructures,” Light Sci. Appl., vol. 11, p. 135, 2022. https://doi.org/10.1038/s41377-022-00835-3.Search in Google Scholar PubMed PubMed Central
[42] H. Liu and Y. Ji, “An ameliorated fast phase retrieval iterative algorithm based on the angular spectrum theory,” Acta Phys. Sin., vol. 62, pp. 263–269, 2013.10.7498/aps.62.114203Search in Google Scholar
[43] P. Chen, L. L. Ma, W. Duan, et al.., “Digitalizing self-assembled chiral superstructures for optical vortex processing,” Adv. Mater., vol. 30, p. 1705865, 2018. https://doi.org/10.1002/adma.201705865.Search in Google Scholar PubMed
© 2023 the author(s), published by De Gruyter, Berlin/Boston
This work is licensed under the Creative Commons Attribution 4.0 International License.
Articles in the same Issue
- Frontmatter
- Review
- Two-dimensional metal halide perovskites and their heterostructures: from synthesis to applications
- Research Articles
- Hot carrier generation in a strongly coupled molecule–plasmonic nanoparticle system
- Nanowire dimer optical antenna brightens the surface defects of silicon
- Time-varying gradient metasurface with applications in all-optical beam steering
- A chiral microchip laser using anisotropic grating mirrors for single mode emission
- Cylindrical vector beams demultiplexing communication based on a vectorial diffractive optical element
- Super-gain nanostructure with self-assembled well-wire complex energy-band engineering for high performance of tunable laser diodes
- Narrowband photoblinking InP/ZnSe/ZnS quantum dots for super-resolution multifocal structured illumination microscopy enhanced by optical fluctuation
- Tiger Amulet inspired high-security holographic encryption via liquid crystals
- Electrically switchable and tunable infrared light modulator based on functional graphene metasurface
- On-chip mode-selective manipulation based on the modal-field redistribution assisted with subwavelength grating structures
Articles in the same Issue
- Frontmatter
- Review
- Two-dimensional metal halide perovskites and their heterostructures: from synthesis to applications
- Research Articles
- Hot carrier generation in a strongly coupled molecule–plasmonic nanoparticle system
- Nanowire dimer optical antenna brightens the surface defects of silicon
- Time-varying gradient metasurface with applications in all-optical beam steering
- A chiral microchip laser using anisotropic grating mirrors for single mode emission
- Cylindrical vector beams demultiplexing communication based on a vectorial diffractive optical element
- Super-gain nanostructure with self-assembled well-wire complex energy-band engineering for high performance of tunable laser diodes
- Narrowband photoblinking InP/ZnSe/ZnS quantum dots for super-resolution multifocal structured illumination microscopy enhanced by optical fluctuation
- Tiger Amulet inspired high-security holographic encryption via liquid crystals
- Electrically switchable and tunable infrared light modulator based on functional graphene metasurface
- On-chip mode-selective manipulation based on the modal-field redistribution assisted with subwavelength grating structures


